Ransomware Gangs Actively Exploiting PaperCut Server Vulnerabilities
In March 2023, two vulnerabilities were patched in the PaperCut Application Server, both of which would allow a threat actor, if exploited, to perform unauthenticated remote code execution and information disclosure.
In an advisory published by PaperCut, both vulnerabilities were described as follows,
- CVE-2023–27350 / ZDI-CAN-18987 / PO-1216: Unauthenticated remote code execution flaw impacting all PaperCut MF or NG versions 8.0 or later on all OS platforms for both application and site servers. (CVSS v3.1 score: 9.8 – critical)
- CVE-2023–27351 / ZDI-CAN-19226 / PO-1219: Unauthenticated information disclosure flaw impacting all PaperCut MF or NG versions 15.0 or later on all OS platforms for application servers. (CVSS v3.1 score: 8.2 – high)
For some background information, PaperCut is a printing management software compatible with all major printer brands and platforms. It is used by large companies, government organizations, and education institutes, with the company's website claiming it is used by hundreds of millions of people from over 100 countries.
PaperCut went on to state that both flaws were being exploited in the wild at the time of being patched and advised network admins to download and install the security updates as a priority.
A few days after PapaerCut published their advisory, Bleeping Computer reported that proof of concept code had been released, effectively lowering the bar so less skilled threat actors could exploit the flaws.
For admins who cannot promptly patch servers, security researcher Huntress advised that all traffic to the web management port (default port 9191) from external IP addresses on an edge device should be blocked.
Further, blocking all traffic to the same port on the server's firewall to restrict management access will help prevent potential network breaches.
On April 26, Microsoft tweeted a bombshell, with the Redmond tech giant saying,
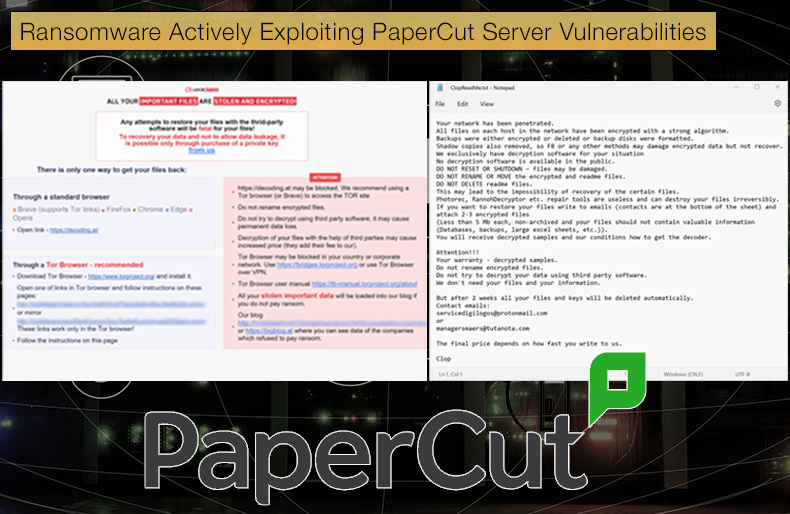
Microsoft is attributing the recently reported attacks exploiting the CVE-2023-27350 and CVE-2023-27351 vulnerabilities in print management software PaperCut to deliver Clop ransomware to the threat actor tracked as Lace Tempest (overlaps with FIN11 and TA505)...Lace Tempest (DEV-0950) is a Clop ransomware affiliate that has been observed using GoAnywhere exploits and Raspberry Robin infection hand-offs in past ransomware campaigns. The threat actor incorporated the PaperCut exploits into their attacks as early as April 13.
It was not only Clop but also those behind the LockBit ransomware strain that was actively targeting vulnerable PaperCut servers.
In observed attacks involving threat actor Lace Tempest, Microsoft security researchers noted that In observed attacks, the threat actor ran multiple PowerShell commands to deliver a TrueBot DLL, which then connected to a command and control server.
TrueBot has been previously linked to Clop, with ransomware operators using the malware to gain initial access to networks. This was done in an attempt to steal credentials and inject the TrueBot payload into the conhost.exe service.
Lace Tempest would then deliver a Cobalt Strike Beacon, a typical tactic ransomware operators use to facilitate the delivery of encryption malware payloads. Lace Tempest then conducted surveillance on connected systems and moved laterally using them.
The actor then identified and exfiltrated files of interest using the file-sharing app MegaSync; if successfully done, these exfiltrated files could be used as part of the now infamous double extortion tactic.
As for attacks seen by Microsoft involving LockBit, it is unclear if these attacks began after the exploits were publicly released.
PaperCut Flaws are a Prime Target for Clop
The exploitation of vulnerabilities found in PaperCut servers matches previously seen Clop tactics. While those deploying Clop will encrypt data, it seems that there has been a shift in how the gang operates, preferring to steal data to extort companies rather than relying on data encryption. This can be seen in the above example of Lace Tempest prioritizing data theft and files.
This shift in operations was first seen in 2020 when Clop operatives successfully hacked Global Accellion to steal data from approximately 100 companies to be used in extortion operations.
To do this, ransomware operators used several disclosed vulnerabilities that were subsequently patched in the company's File Transfer Appliance application.
As for exactly who was responsible, Mandiant determined,
...that a common threat actor we now track as UNC2546 was responsible for this activity. While complete details of the vulnerabilities leveraged to install DEWMODE [malware used to facilitate the theft of data] are still being analyzed, evidence from multiple client investigations has shown multiple commonalities in UNC2546's activities,
The Clop gang recently utilized zero-day vulnerabilities in the GoAnywhere MFT secure file-sharing platform to steal data from 130 companies. Here again, a zero-day vulnerability was used to enable the theft of data to be used in extortion operations.
Security researcher Brian Krebs noted,
A Zero-Day Remote Code Injection exploit was identified in GoAnywhere MFT…The attack vector of this exploit requires access to the administrative console of the application, which in most cases is accessible only from within a private company network, through VPN, or by allow-listed IP addresses (when running in cloud environments, such as Azure or AWS).
As for PaperCut, the software has an archiving feature that saves all print jobs and documents sent through the server, making it a good candidate for data exfiltration attacks Clop is becoming increasingly known for.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion