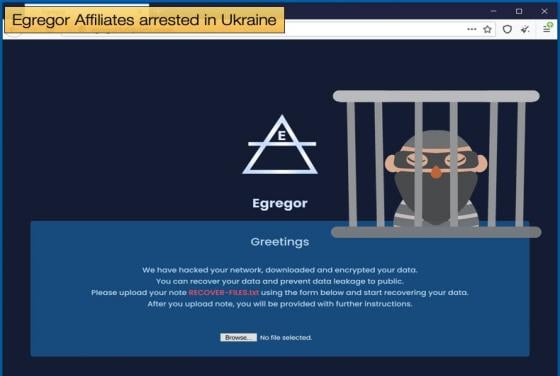
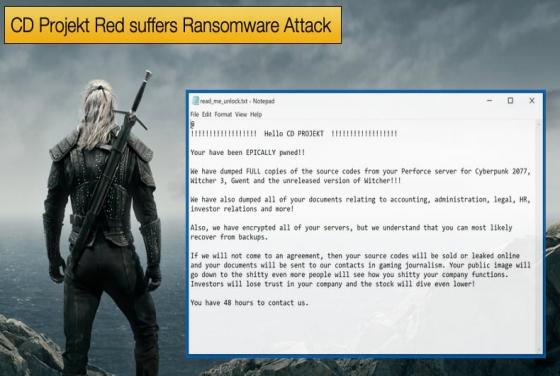
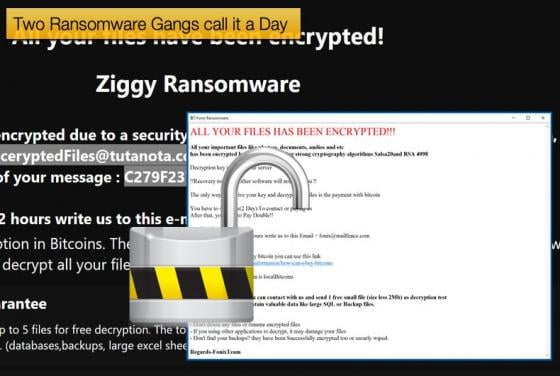
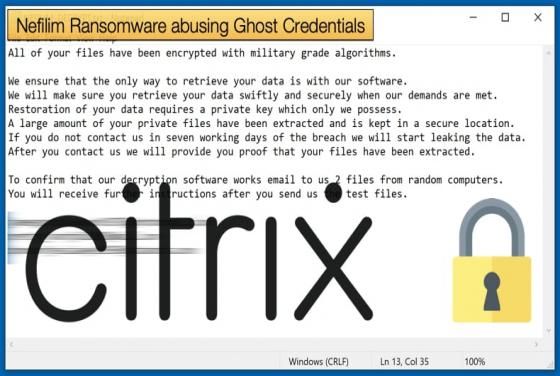
Silver Sparrow infects nearly 30,000 Macs
Details of a new malware designed to target Macs, called Silver Sparrow, has already infected close on 30,000 separate machines. The malware was discovered by researchers from Red Canary who subsequently analyzed the malware along with Malwarebytes and VMWare Carbon Black. In a subsequent report pub