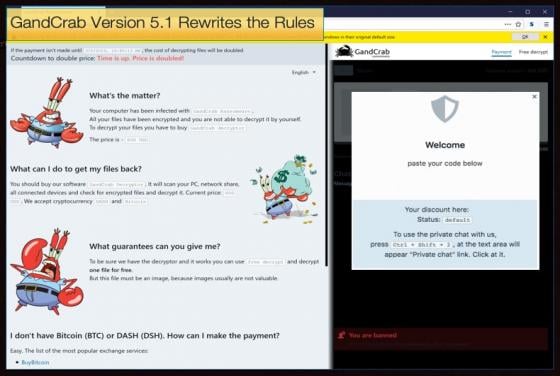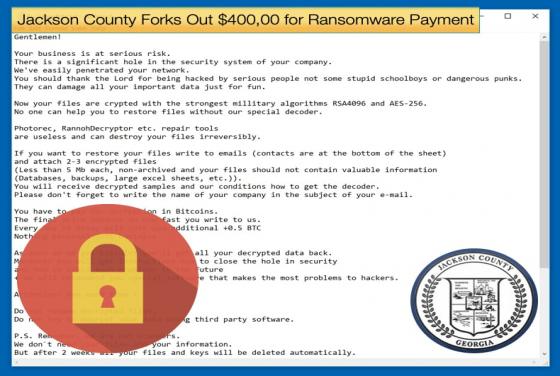

Jackson County Forks Out $400,00 for Ransomware Payment
It was a commonly held belief that hackers using ransomware would only go after private individuals. When WannaCry struck this belief was well and truly shattered. Increasingly hacker groups are seeing the value of attacking government organizations, hospitals, and companies. One of the reasons for