New Ransomware Targets Chinese Mining Rigs
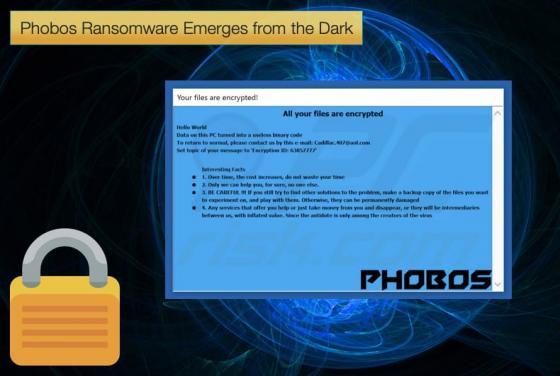
It has been a busy week in the news for ransomware. First, it emerged a new family called Phobos was discovered and been used by the group behind the Crysis and Dharma families of ransomware. Then reports emerged of another new ransomware called Anatova. Then finally, although the week has not ended