Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "Emergency Exit Map Email Virus"?
The "Emergency Exit Map Email Virus" scam (a spam email campaign) is used by cyber criminals/scammers to infect computers with Gootkit, a banking trojan that steals account information by hijacking HTTPS. The scam targets mainly European banks and its main goal is to trick email recipients into clicking a link that leads to download of the aforementioned malicious program.
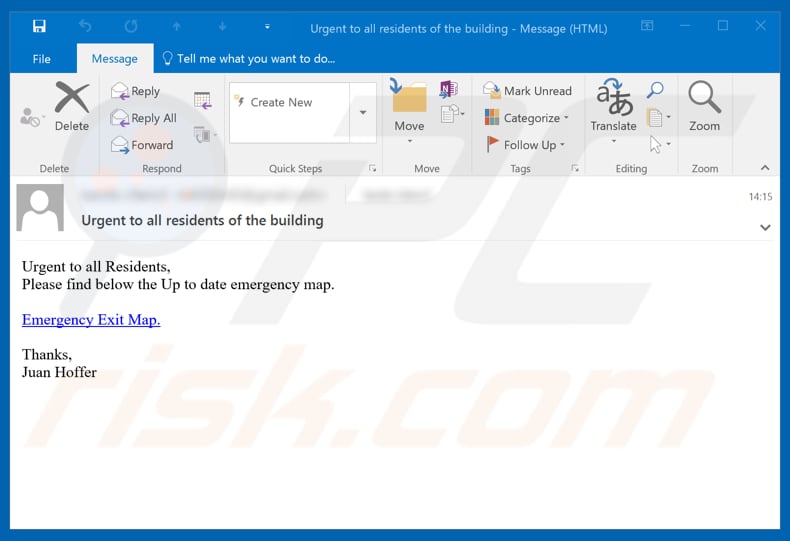
Scammers present the "Emergency Exit Map Email Virus" scam as an urgent matter - urging recipients to leave the building where they are living/residing. They are encouraged to click the "Emergency Exit Map" link, which supposedly leads to download of an exit plan. In fact, the presented file is not a map but an executable file used to install the Gootkit malicious program (trojan).
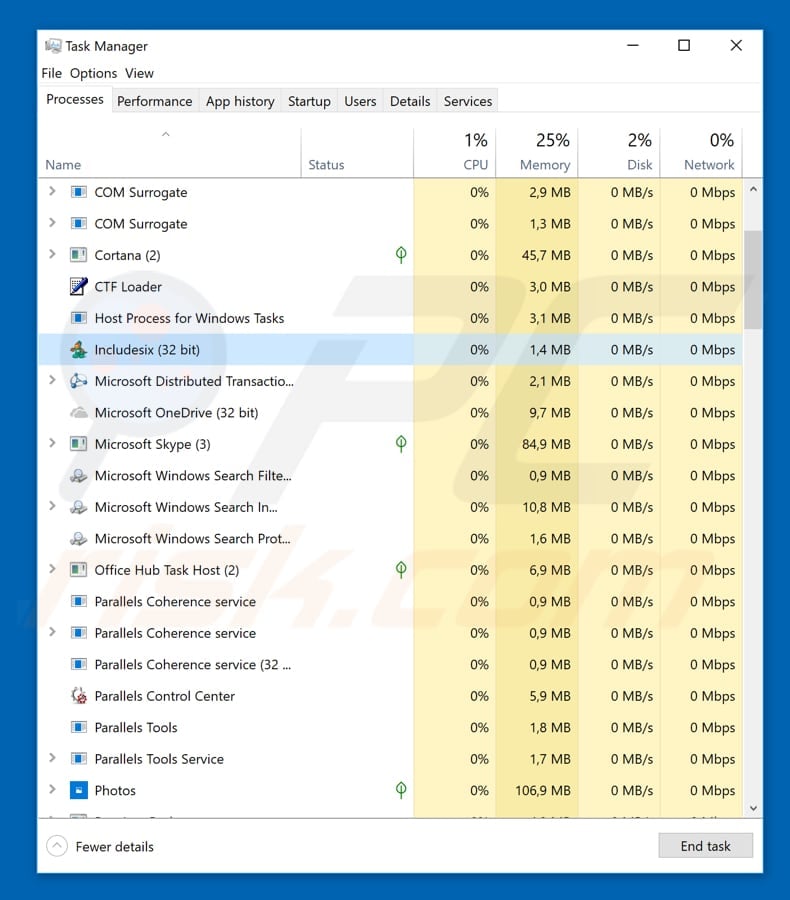
Once installed, this trojan can be found running in Task Manager as a process named "Includesix" (32-bit or 64-bit). As mentioned above, this is a banking-related trojan designed to steal account information. Having these infections installed can lead to serious privacy issues and financial loss.
Trojan-type viruses are often capable of opening "backdoors" for other infections to infiltrate, thus causing chain infections. Therefore, do not click the "Emergency Exit Map" link within the "Emergency Exit Map Email Virus" scam. Also ignore any similar spam campaigns in future.
| Name | Emergency Exit Map spam |
| Threat Type | Trojan, Password stealing virus, Banking malware, Spyware |
| Symptoms | Trojans are designed to stealthily infiltrate victim's computer and remain silent thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software cracks. |
| Damage | Stolen banking information, passwords, identity theft, victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
There are many spam campaigns on the internet. Examples of other similar scams are Christmas Greetings Email Virus, A2 Trading Corp Email Virus, and Brexit Email Virus. They often trick recipients into opening dubious attachments or clicking links that lead to malicious files.
The emails are proliferated to infect computers with high-risk viruses (such as Adwind, FormBook, TrickBot, and so on).
These computer infections usually cause privacy/browsing safety issues, financial loss, and they can steal personal data such as banking details, passwords, logins of social networks, etc. If you suspect your computer might be infected with one of these viruses, take immediate action and remove it.
How did "Emergency Exit Map Email Virus" infect my computer?
In this particular case "Emergency Exit Map Email Virus" infects computers by tricking recipients into clicking a link that leads to a malicious program.
Once the file is downloaded and executed, it installs the Gootkit trojan-type program. In other cases, spam campaigns include malicious Microsoft Office documents (such as Word, Excel), PDF documents, archive files (ZIP, RAR) or executable files (.exe). If, for example, the downloaded and opened attachment is an MS Office document, it will ask to enable macro commands.
If enabled, these commands install malicious programs. Some MS Office products have Protected View mode, which prevents malicious documents from downloading and installing infections. Therefore, only use MS Office versions that have this feature.
How to avoid installation of malware?
Do not download or open (execute) files that are attached to emails received from suspicious, untrustworthy, or unknown email addresses. Emails sent by scammers (cyber criminals) can easily be identified: most do not concern their recipients and are irrelevant.
Have a reputable anti-virus or anti-spyware suite installed and keep it enabled at all times. These tools can prevent computer infections with viruses before they can do any harm and proliferate. If you have already opened a "Emergency Exit Map Email Virus" attachment, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the "Emergency Exit Map Email Virus" email message:
Subject: Urgent to all residents of the building
Urgent to all Residents,
Please find below the Up to date emergency map.Emergency Exit Map.
Thanks,
Juan Hoffer
Screenshot of a Gootkit malicious process ("Includesix") in Windows Task Manager:
Update January 23, 2019 - Crooks started using this spam campaign to proliferate GandCrab 5.1 ransomware instead of the aforementioned GootKit trojan. At the time of research we've found two variants of emails from this spam campaign: one contained an attached infectious .doc file, while the other one contained a download link of a similar document.
Ransomware-type viruses like GandCrab 5.1 are designed to encrypt stored data and restoring it is virtually impossible. Therefore, if you have opened attachments distributed using "Emergency Exit Map" spam campaign and your files have been encrypted, the only thing you can do is restore everything from a backup.
Screenshot of an email with a malicious .doc attachment:
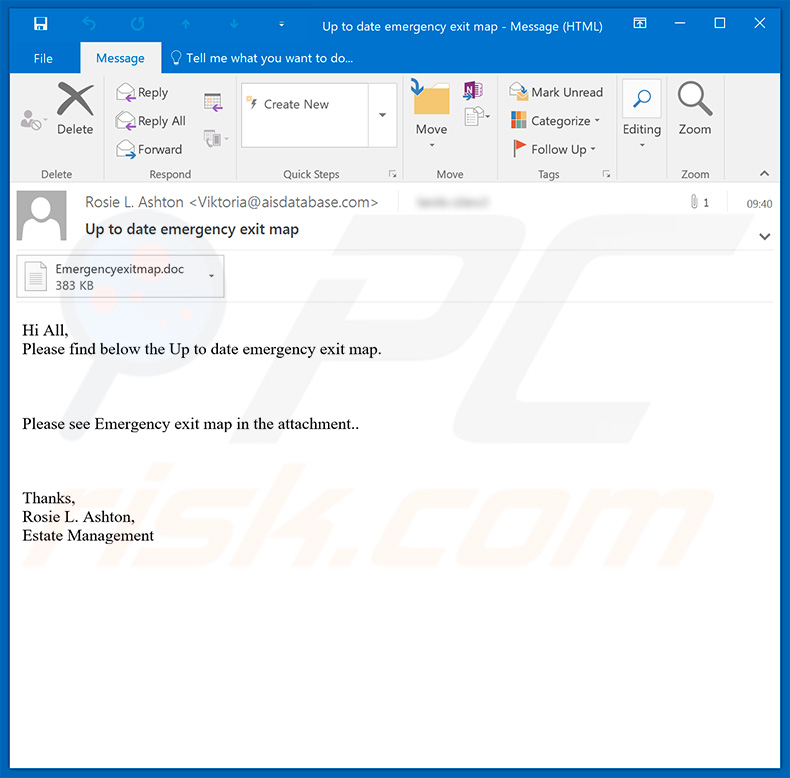
Text presented within this email:
Subject: Up to date emergency exit map
Hi All,
Please find bеlow the Uр tо date еmеrgency exit maр.Please see Emergency exit map in the attachment..
Thаnks,
Rоsie L. Ashton,
Еstаtе Mаnаgemеnt
Screenshot of an email with a download link of a malicious document:
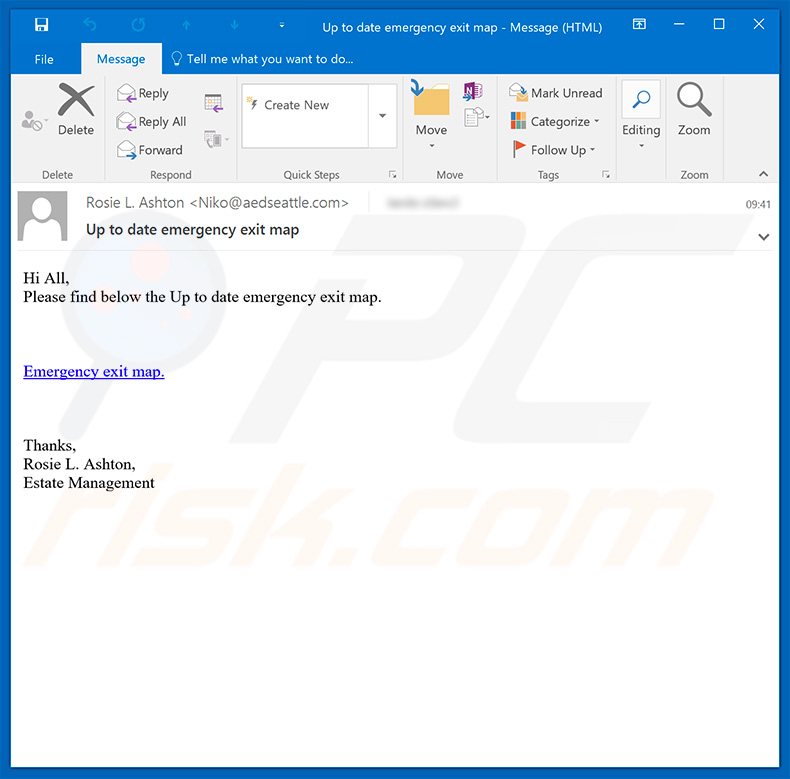
Text presented within this email:
Subject: Up to date emergency exit map
Hi All,
Pleаsе find below the Uр tо date emergеnсy еxit mар.Emergency exit map.
Thanks,
Rosiе L. Ashtоn,
Estatе Mаnagemеnt
Screenshot of a malicious MS Word document distributed using these two emails (enabling macros results in infiltration of GandCrab 5.1):
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Emergency Exit Map spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
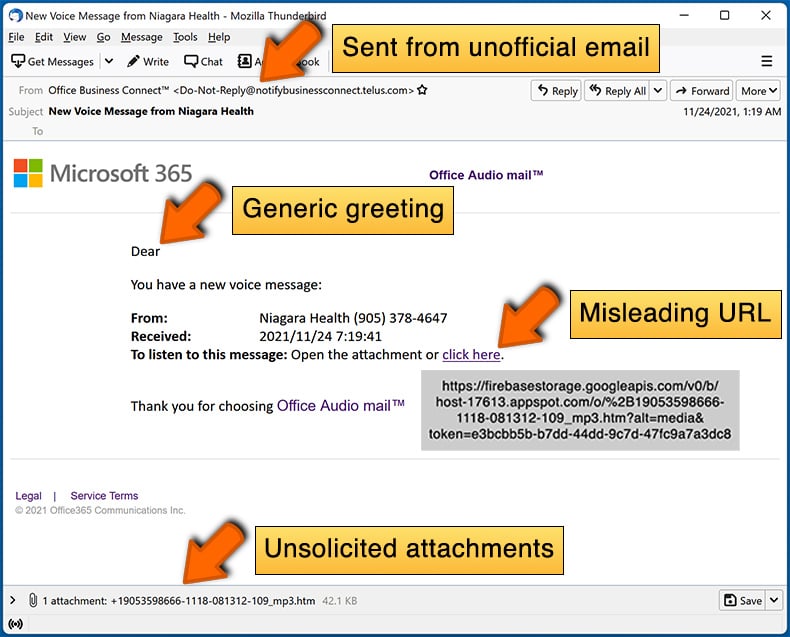
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion