How to remove Tofsee trojan-type malware from the operating system
TrojanAlso Known As: Tofsee malware
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is Tofsee?
Tofsee (also known as Gheg) is a malicious Trojan-type program that is capable of performing DDoS attacks, mining cryptocurrency, sending emails, stealing various account credentials, updating itself, and more.
Cyber criminals mainly use this program as an email-oriented tool (they target users' email accounts), however, having Tofsee installed can also lead to many other problems.
Tofsee Trojan overview
Cyber criminals employ this program to hijack (steal) email accounts, which they use to proliferate spam emails that might contain malicious attachments, change the content of received emails (but leaving the original "From" and "To" headers, timestamps, subject etc.), steal email addresses from users' inboxes, and so on.
Tofsee can also be used to hijack e-mail client software (i.e. Microsoft Outlook). Note that, by having access to users' email accounts, cyber criminals can also gain access to other accounts. This affects users who use identical passwords and email addresses for several accounts.
Furthermore, the password recovery service could be used for the same purpose. Unfortunately, there are many other malicious operations capable with this malicious program.
Tofsee can use the hijacked system for DDoS attacks, stealing POP3 credentials and FTP, downloading and installing malicious services (opening backdoors for other threats), removing other malware (that is already installed) to prevent interference, and communicating with a Command & Control (C&C) server.
It can also block access to certain IP addresses. It might be used to prevent users from accessing cyber security websites and other web pages.
Additionally, it is capable of installing cryptocurrency mining software. Therefore, users' computers could be used for mining purposes, thus causing higher electricity bills, diminished computer performance, and even hardware overheating. Furthermore, Tofsee is capable of updating and proliferating itself via Twitter, Facebook, Skype and/or USB drives.
It can proliferate through Facebook using cookies and sending malicious attachments/links leading them to a number of users' Facebook friends. To proliferate through Twitter, it uses cookies and can then download a list of followers and send private messages with malicious links.
To proliferate through Skype, it simply sends malicious messages to users' contacts. It can also place a malicious executable on the USB drive and replace its AutoRun file, thereby forcing the infected USB drive to run a malicious executable when the USB drive is opened.
| Name | Tofsee malware |
| Threat Type | Trojan, Password stealing virus, Banking malware, Spyware, Remote access trojan. |
| Detection Names (zgttwhzu.exe_) |
Avast (Win32:BankerX-gen [Trj]), AVG (Win32:BankerX-gen [Trj]), BitDefender (Gen:Variant.Ulise.34872), ESET-NOD32 (a variant of Win32/Kryptik.GRUQ), Kaspersky (), Full List (VirusTotal). |
| Malicious Process Name(s) | The analyzed sample ran a process with a blank name. |
| Symptoms | Trojans are designed to stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software cracks. |
| Damage | Stolen banking information, passwords, identity theft, victim's computer added to a botnet, additional system infections. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Trojan-type malware examples
Tofsee is a powerful malicious program that can cause serious damage, including financial loss and computer infections. Cyber criminals use it to generate as much revenue as possible. The program is likely to install unintentionally and cause a number of problems for the system in question and other people too.
The internet is full of Trojan-type malicious programs. Some other examples include Emotet, Adwind, Pony, and Trickbot. The main purpose of these programs is to steal personal data and cause additional computer infections.
How did Tofsee infiltrate my computer?
Typically, cyber criminals proliferate malicious programs using spam campaigns, Trojans, fake software updaters, software cracking tools, and untrustworthy software download sources. They use spam campaigns by sending emails that contain infected attachments or links that lead to them.
These attachments are usually Microsoft Office or PDF documents, executables (.exe) files, archives (ZIP, RAR), JavaScript files and so on. To infect systems, these attachments must first be opened. They then download and install malicious programs.
Another way to proliferate malware is through Trojans (malicious programs that cause chain infections), however, to cause any damage, they must be installed. Fake software updaters proliferate computer infections by downloading and installing dubious software rather than updates (fixes and so on) or by exploiting outdated software bugs/flaws.
People use software cracking tools to bypass activation of software that is licensed (not free), however, they are often used by cyber criminals to install malware rather than activating any paid software or operating systems.
Untrustworthy software download sources such as freeware download websites, free file hosting websites, Peer-to-Peer networks (i.e. torrent clients, eMule), third party downloaders, etc. can be used by cyber criminals - they present malicious software/files as legitimate and harmless, thereby tricking people into downloading and installing malicious programs.
How to avoid installation of malware?
Attachments or links that are presented in emails received from unknown, suspicious addresses should not be opened. Furthermore, they are usually included in irrelevant emails and presented as official and important. Emails of this type should be ignored.
Download software using official, trustworthy sources/websites (and direct download links) rather than the other sources mentioned above. Update software or operating systems using tools or implemented functions that are provided by official developers only.
Do not use software cracking tools to activate installed programs. They are illegal (using them is classed as a cyber crime) and often infect computers. Have reputable anti-spyware or anti-virus software installed and enabled. These tools can prevent computer infection with viruses.
If you believe that your computer is already infected, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Screenshot of the Tofsee using CPU resources:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
How to remove malware manually?
Manual malware removal is a complicated task - usually it is best to allow antivirus or anti-malware programs to do this automatically. To remove this malware we recommend using Combo Cleaner Antivirus for Windows.
If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here is an example of a suspicious program running on a user's computer:
If you checked the list of programs running on your computer, for example, using task manager, and identified a program that looks suspicious, you should continue with these steps:
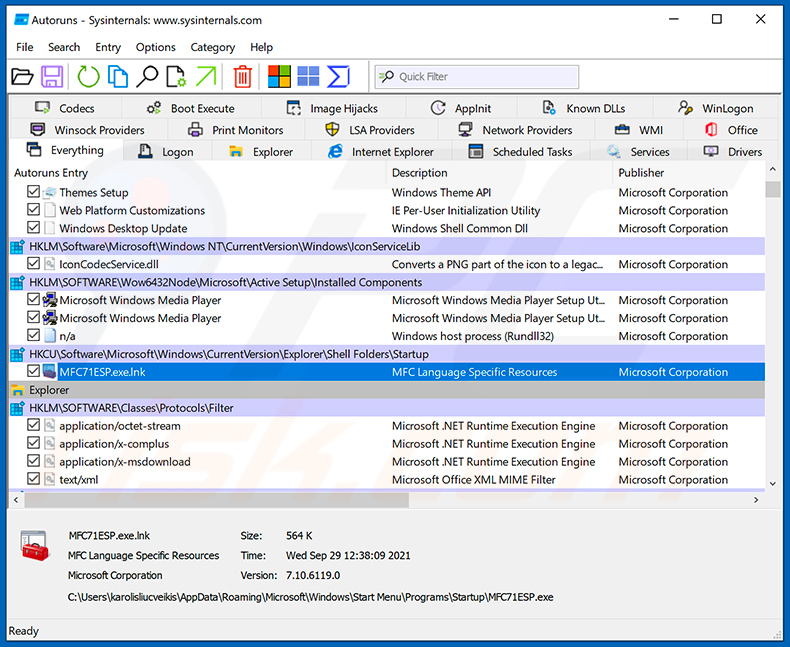
 Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
 Restart your computer into Safe Mode:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
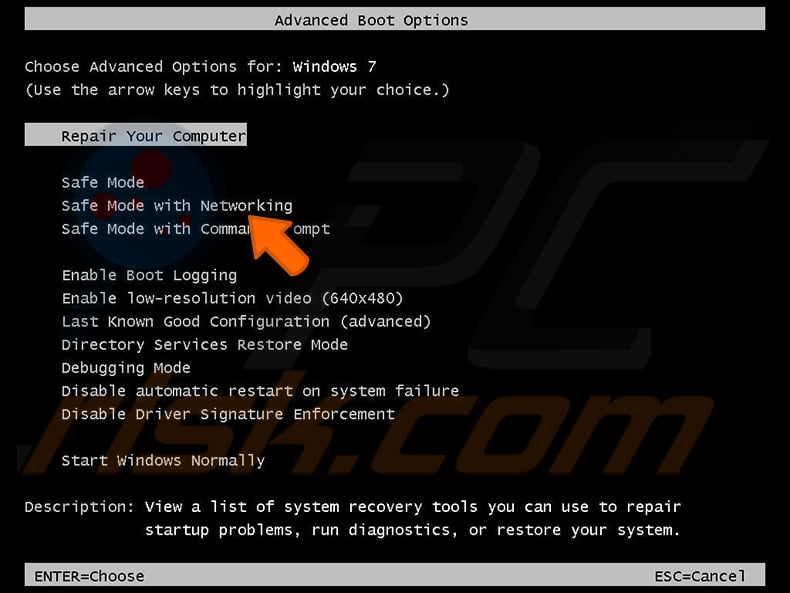
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Advanced startup.
Click the "Restart now" button. Your computer will now restart into the "Advanced Startup options menu". Click the "Troubleshoot" button, and then click the "Advanced options" button. In the advanced option screen, click "Startup settings".
Click the "Restart" button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in "Safe Mode with Networking":
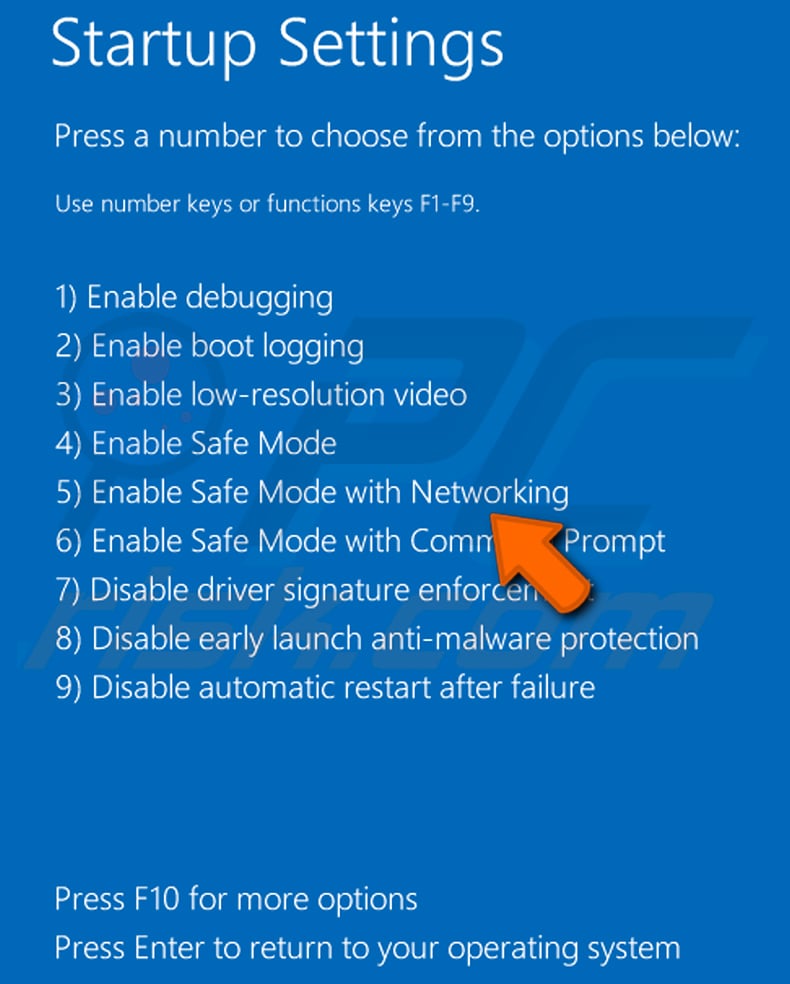
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options".
In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
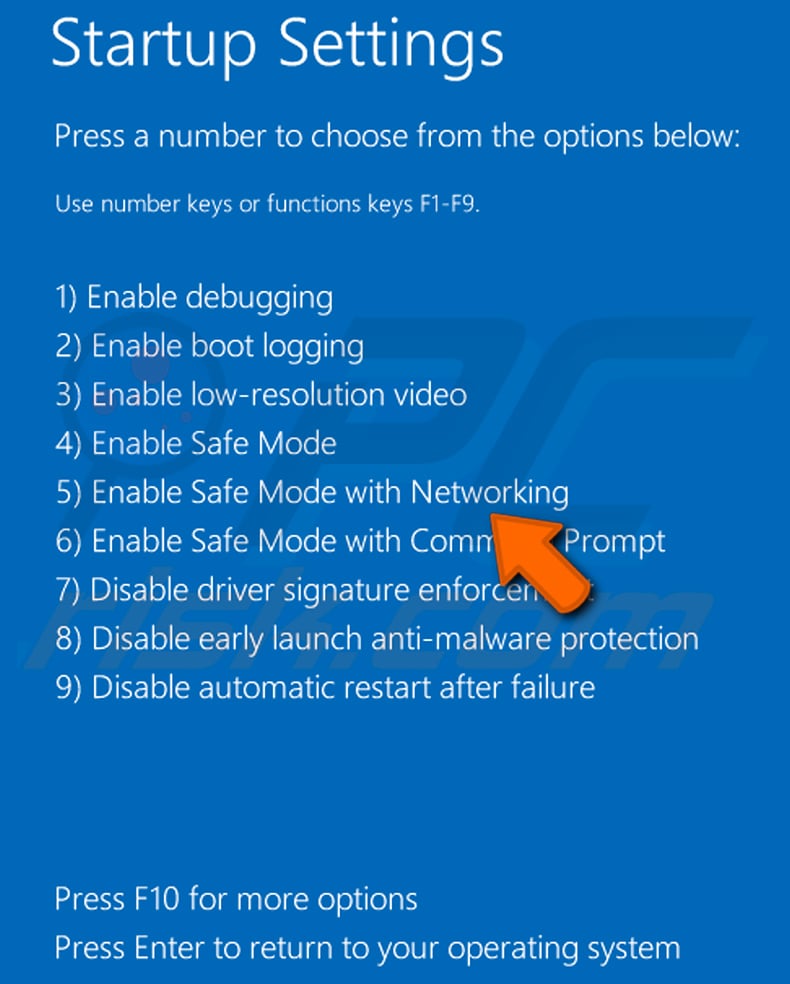
Video showing how to start Windows 10 in "Safe Mode with Networking":
 Extract the downloaded archive and run the Autoruns.exe file.
Extract the downloaded archive and run the Autoruns.exe file.
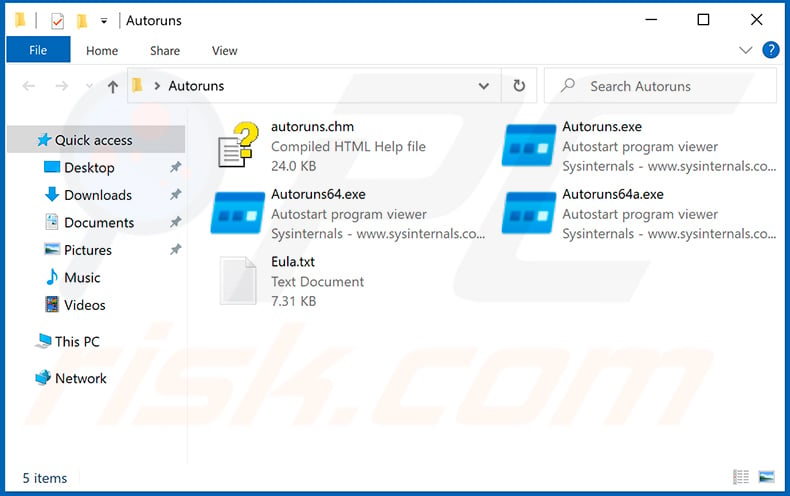
 In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
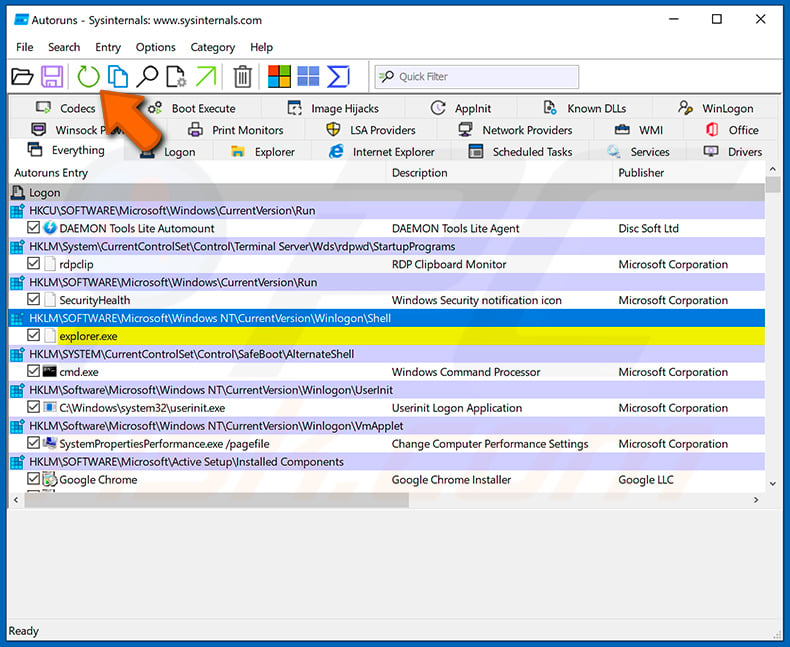
 Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files. After you locate the suspicious program you wish to remove, right click your mouse over its name and choose "Delete".
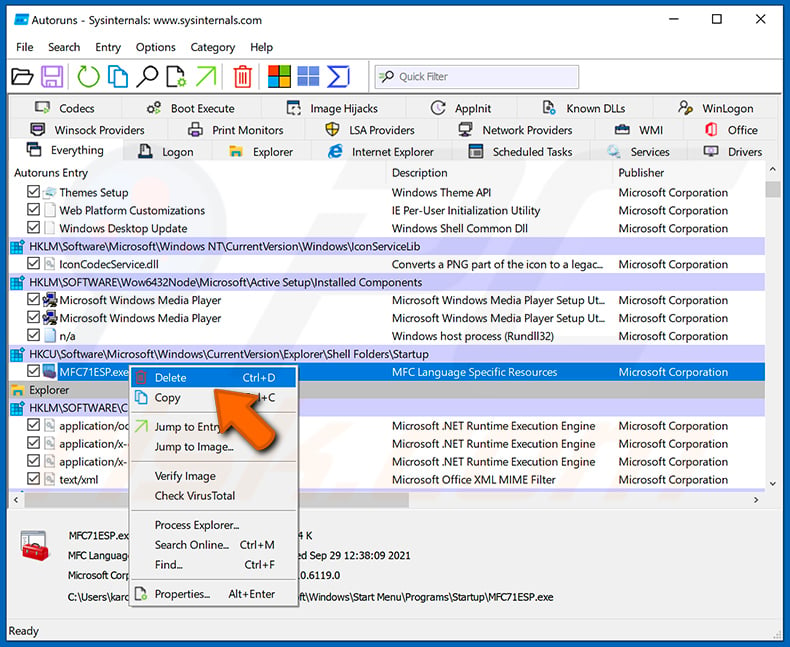
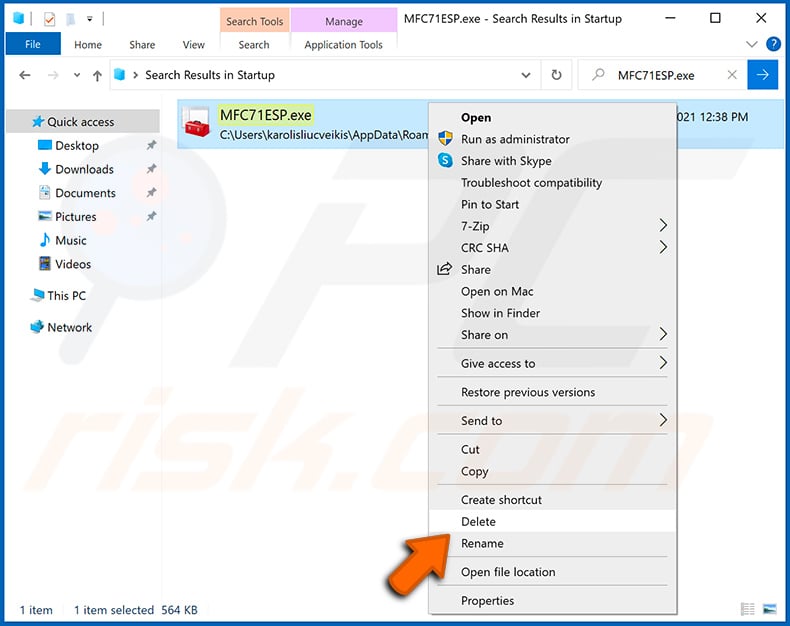
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills. If you do not have these skills, leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it is best to prevent infection than try to remove malware later. To keep your computer safe, install the latest operating system updates and use antivirus software. To be sure your computer is free of malware infections, we recommend scanning it with Combo Cleaner Antivirus for Windows.
Frequently Asked Questions (FAQ)
My computer is infected with Tofsee malware, should I format my storage device to get rid of it?
No, Tofsee trojan's removal does not require such drastic measures.
What are the biggest issues that Tofsee malware can cause?
The Tofsee trojan has a wide variety of abilities. It can seriously diminish system performance by abusing its resources to mine cryptocurrency, launching DDoS attacks, or spamming itself through hijacked emails, social networking accounts, and messengers.
This malware can extract vulnerable data from devices and installed applications. It is also capable of causing chain infections (i.e., download/install trojans, ransomware, and other malware). To summarize, Tofsee can cause multiple system infections, data loss, hardware damage, severe privacy issues, financial losses, and identity theft.
What is the purpose of Tofsee malware?
In most cases, malware is used to generate revenue. However, cyber criminals can also employ malicious software for their own amusement or to carry out personal grudges, disrupt processes (e.g., websites, processes, etc.), or even launch politically/geopolitically motivated attacks.
How did Tofsee malware infiltrate my computer?
Malware is mainly distributed through malicious attachments and links in spam emails/messages, online scams, drive-by downloads, dubious download channels (e.g., unofficial and freeware sites, P2P sharing networks, etc.), illegal software activation tools ("cracks"), and fake updates. Furthermore, some malicious programs can self-proliferate via local networks and removable storage devices (e.g., external hard drives, USB flash drives, etc.).
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner is designed to detect and eliminate threats. It is capable of removing most of the known malware infections. However, it must be stressed that running a complete system scan is paramount - since sophisticated malicious software typically hides deep within systems.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion