Avoid installation of the Kryptik trojan via "WeTransfer" emails
Phishing/ScamAlso Known As: WeTransfer spam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "WeTransfer" email virus?
"WeTransfer" is the title of a deceptive email designed to spread the Kryptik trojan. The email might also be used to spread other malicious programs. You are strongly advised against opening this message, and especially the links it contains, since this will trigger installation of the aforementioned malware infection.
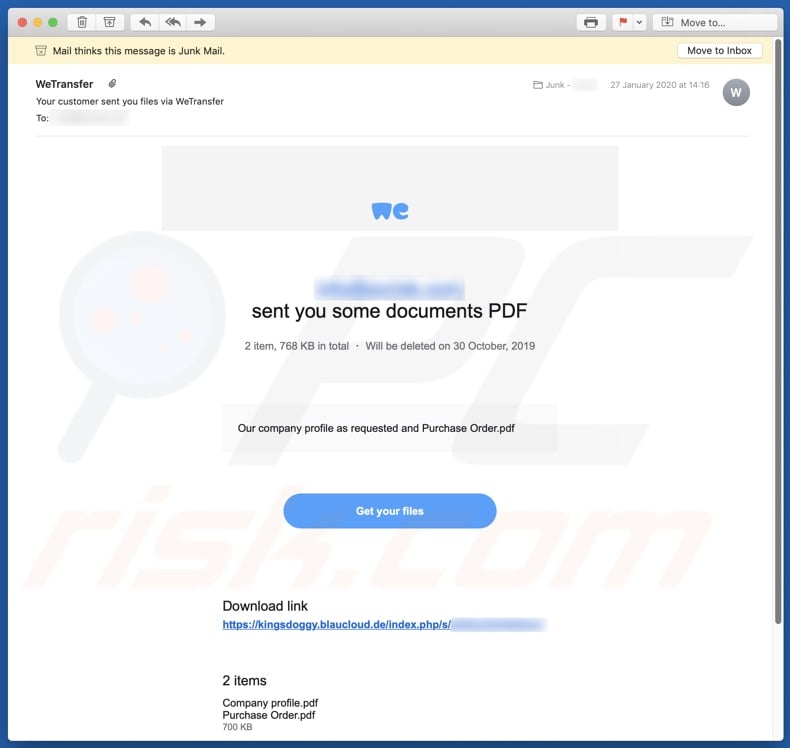
"WeTransfer" malicious email in detail
The text presented in the "WeTransfer" email is brief and simply informs recipients that they have been sent a document concerning the unspecified company's profile and purchase/order details ("Our company profile as requested and Purchase Order.pdf").
The message has few details and does not play on people's emotions (e.g. using scare tactics), however, they risk being tricked into downloading the archived file within the message through confusion or curiosity. Cyber criminals often mention or use legitimate services for their malicious purposes.
Both WeTransfer and ownCloud are genuine services (file transfer and hosting respectively), which are abused by the individuals behind this spam campaign. At the time of research, the link in the "WeTransfer" email opened an ownCloud web page, from which the file containing Kryptik trojan could be downloaded.
This is high-risk malware with a wide range of capabilities, including (but not limited to) system and browser modification, control over connected hardware and data exfiltration. To summarize, Kryptik is likely to cause serious privacy issues, significant financial loss and even identity theft.
To protect device and user safety, it is crucial to eliminate all malicious programs without delay.
| Name | WeTransfer spam |
| Threat Type | Trojan, password-stealing virus, banking malware, spyware. |
| Hoax | Email claims recipients have been sent company and purchase details as per their request. |
| Attachment(s) | Download link of "Our company profile as requested and Purchase Order_PDF.cab" (malicious executable inside) |
| Detection Names |
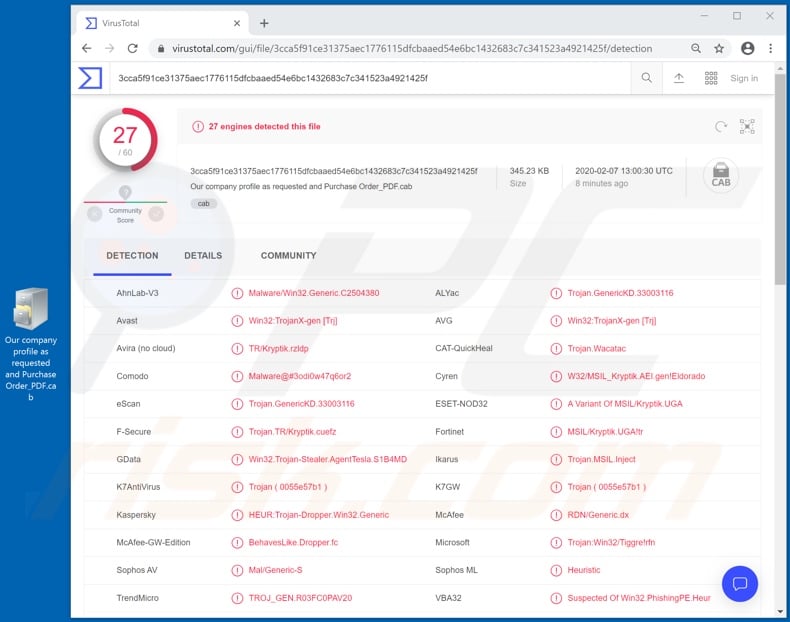
Avast (Win32:TrojanX-gen [Trj]), Fortinet (MSIL/Kryptik.UGA!tr), ESET-NOD32 (A Variant Of MSIL/Kryptik.UGA), Kaspersky (HEUR:Trojan-Dropper.Win32.Generic), Full List Of Detections (VirusTotal) |
| Symptoms | Trojans are designed to stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Payload | Kryptik |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software 'cracks'. |
| Damage | Stolen passwords and banking information, identity theft, the victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Similarities with other emails used to deliver malware
Social engineering and scare tactics are usually employed to further deceptive/scam emails. These messages are typically disguised as "official", "important", "priority", "urgent" and so on. The subject matter varies drastically: the written content can be well-researched and detailed, or sloppy and hastily put together.
Therefore, emails riddled with grammatical errors and spelling mistakes, and other inconsistencies, should call the legitimacy of the message immediately into question. The only purpose of this deceptive email is to generate revenue at users' expense.
This is achieved via malware infections, which trick recipients into revealing their personal details (e.g. information relating to identity, banking account or credit card details, etc.) or making monetary transactions (e.g. blackmailing people for existing or nonexistent compromising material, various fake fees or payments, etc.), and via the use of many other scamming techniques.
Systems are infected through attachments or links leading to download of the file. "Your computer hacked!", "Christmas Party Email", and "HARASSMENT COMPLAINT" are some examples of emails used to proliferate malware.
The Kryptik malicious software is spread through the "WeTransfer" email spam campaign and shares similarities with Emotet, TrickBot, Adwind and countless other trojans.
How did "WeTransfer" email virus infect my computer?
Deceptive/Scam mail infects systems via dangerous files, which can be attached to, or linked within, the message. Links are employed for the "WeTransfer" email. Infectious files come in a variety of formats including archive (CAB, ZIP, RAR, etc.) and executable (.exe, .run, .etc.) files, Microsoft Office and PDF documents, JavaScript and others.
When these files are executed, run or otherwise opened, the infection processes is initiated and they begin downloading/installing malware. For example, upon opening, Microsoft Office documents request users to enable macro commands (i.e., to enable editing).
Enabling them can trigger an infection, however, in MS Office versions released prior to 2010, macros are enabled automatically once the document is opened.
How to avoid installation of malware
Suspect and/or irrelevant emails should not be opened, especially if received from unknown senders (addresses). Also do not open any attached files or links found in suspicious messages, as they are the potential origin of an infection. You are strongly advised to use Microsoft Office versions released after 2010.
The newer releases have "Protected View" mode, which prevents malicious macros from immediately initiating the infection process when the document is opened.
Malicious content is often downloaded from untrusted download channels such as unofficial and free file-hosting websites, Peer-to-Peer sharing networks (BitTorrent, eMule, Gnutella, etc.) and other third party downloaders. Therefore, use only official and verified download sources. Illegal activation ("cracking") tools and third party updaters can also cause infections.
Therefore, programs should be activated and updated only with tools/functions provided by legitimate developers. To ensure device integrity and user safety, have reputable anti-virus/anti-spyware software installed and kept up to date. Furthermore, use this software for regular system scans and removal of detected threats/issues.
If you have already opened the file downloaded from the website accessed via "WeTransfer" email, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the "WeTransfer" email message:
Click 'Download images' to view images
********
sent you some documents PDF
2 item, 768 KB in total ・ Will be deleted on 30 October, 2019
Our company profile as requested and Purchase Order.pdfGet your files
Download link
hxxps://kingsdoggy.blaucloud.de/index.php/s/*****
2 items
Company profile.pdf
Purchase Order.pdf
700 KB
To make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
About WeTransfer ・ Help ・ Legal ・ Report this transfer as spam
Screenshot of the website opened via a link in the "WeTransfer" email:
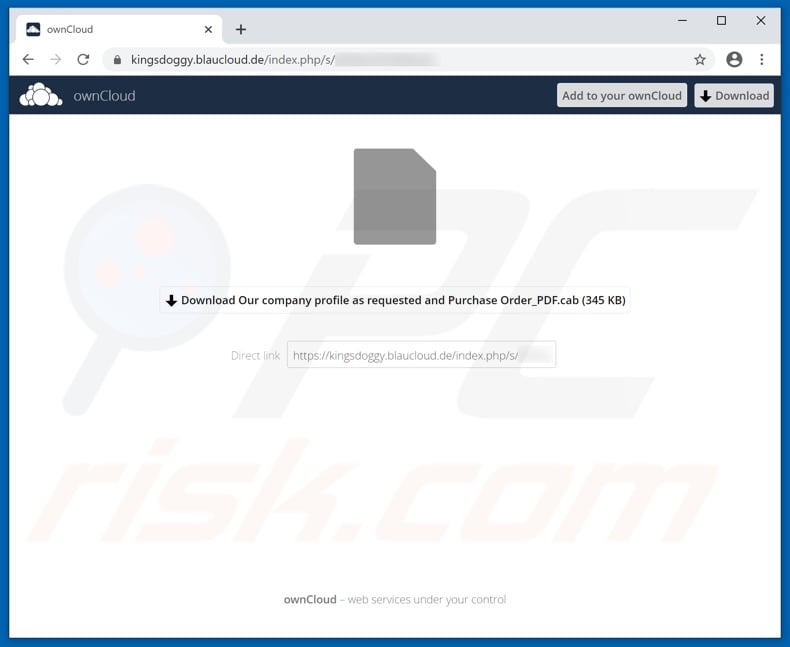
Screenshot of detections on the malware database VirusTotal of "Our company profile as requested and Purchase Order_PDF.cab" (archived file containing the Kryptik's executable):
Another variant of "WeTransfer" spam email:

Text presented within this email:
Subject: You have successfully received files Via Wetransfer
files sent to
*****
6 files, 120 MB in total · Will be deleted on&n=sp;0th Feb, 2020
Download files hereThanks for using WeTransfer. We'll email you a confirmation as soon=as your files have been downloaded.
Download link
hxxps://loxley-th.com/*****Message
Hi - please download files here. Thx.
To make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
Screenshot of the website promoted via this email:
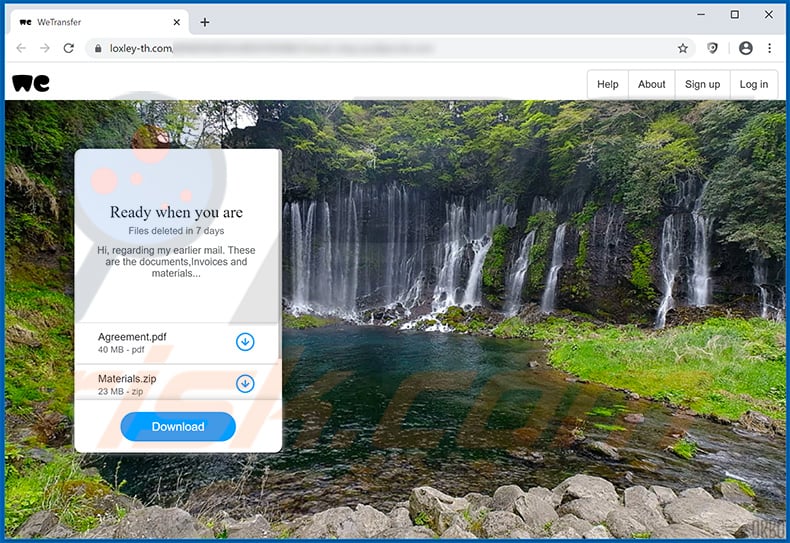
Text presented within this site:
Help About Sign up Log in
Ready when you areFiles deleted in 7 days
Hi, regarding my earlier mail. These are the documents,Invoices and materials...
Agreement.pdf
40 MB - pdf
Materials.zip
23 MB - zip
Mov Intro.mp4
76 MB - mp4
Download
Another example of WeTransfer phishing spam campaign (the text contains "Get your files" text, which is actually a link leading to malicious websites):
Text presented within this email:
Click 'Download images' to view images
****
You have received files via WeTransfer
5 item, 40.5 MB in total · Will be deleted on 19th March, 2020
Get your files1 item
0866_001.pdf
15.5 KB
To make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
About WeTransfer · Help · Legal · Report this transfer as spam
Screenshot of the phishing email:
Yet another variant of WeTransfer spam email:
Text presented within:
Subject: WeTransfer
Click 'Download images' to view images
*******
sent you some files
4 items, 702 KB in total ・ Will be deleted on 7 JUNE, 2020
Get your files
Recipients
*******
Download link
1 File
PAYMENT PLAN INV -2020 JUNE
BL + PL AND TELEX RELEASE
700 kB
To make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
Get more out of WeTransfer, get Pro
About WeTransfer ・ Help ・ Legal ・ Report this transfer as spam
Another WeTransfer-themed spam email promoting a phishing site:
Text presented within:
Click 'Download images' to view images
-
sent you some files
2 file, 803 KB in total · Will be deleted on 24th June, 2020
Get your files
Download link
-
2 file
Documents 23-06-20.Docx
To make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
About WeTransfer · Help · Legal · Report this transfer as spam
Appearance of the promoted site - larkspurandtea[.]com (GIF):
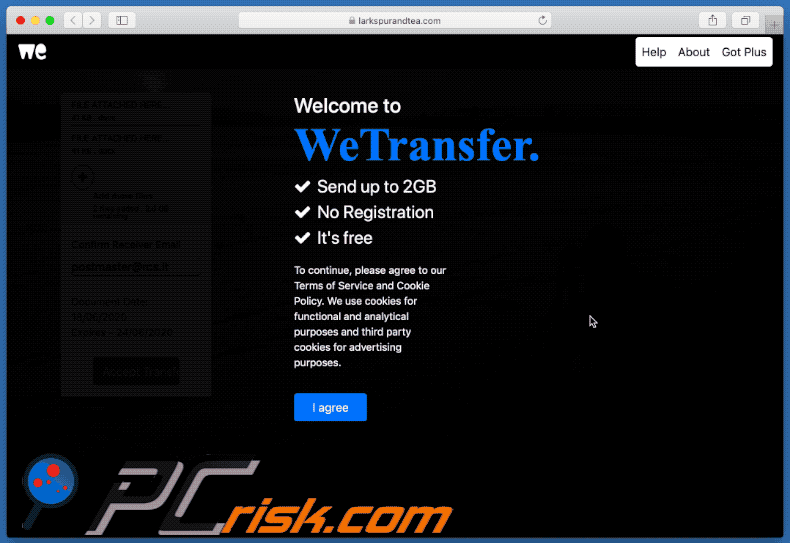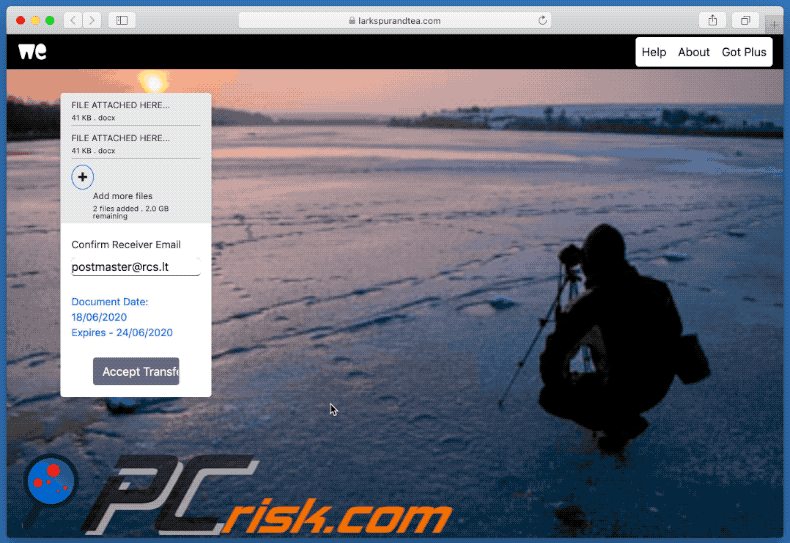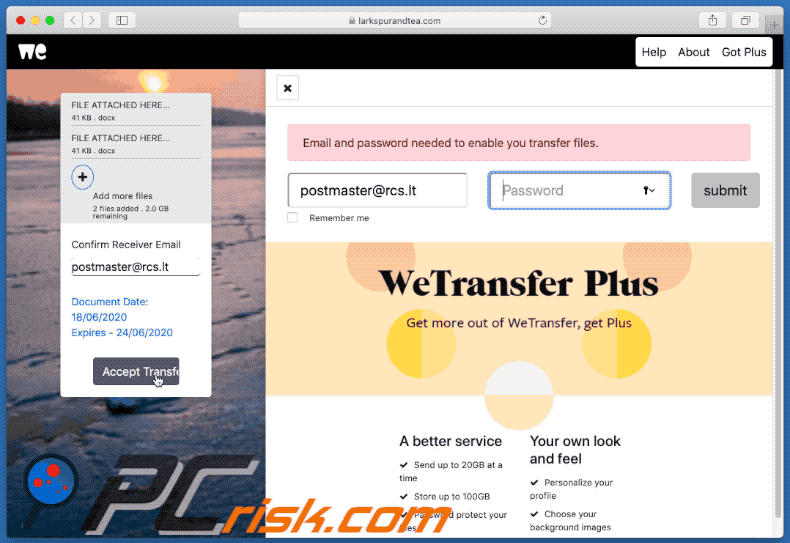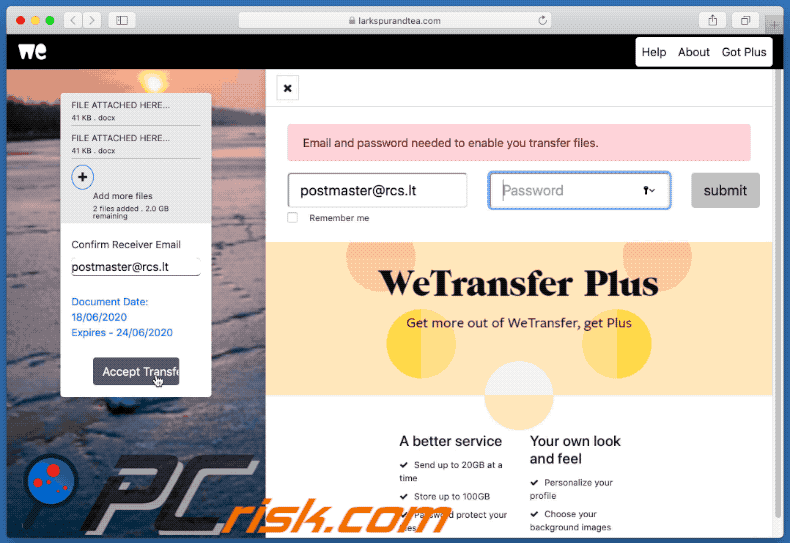
Another example of a WeTransfer-themed spam email used for phishing purposes:

Text presented within:
Subject: sales-dept@mtekmarine.com: sent you files via WeTransfer
Click 'Download images' to view images
sales-dept@mtekmarine.com
sent you some files
2 items, 700 KB in total ・ Will be deleted on 10 JULY, 2020
Get your files
Dear -,We request quotes for the attached requisition from M-TEK MARINE TRADING LTD. give us the best.
Best Regards,
Nyein Su Mon
Sales Department
M-TEK MARINE TRADING LTD.
Tel. +66 038 401309-310
Fax. +66 038 401977
8 Sunview Road
#06-45 Eco-Tech@Sunview
Singapore 628815
Email: sales-dept@mtekmarine.com
Recipients
s.barasheed@rcservice.lt
Download Document
2 Files
RFQ_SMK 001 -2020 JUN & RFQ_SMK 002 -2020 JUN
700 kB
To make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
Get more out of WeTransfer, get Pro
About WeTransfer ・ Help ・ Legal ・ Report this transfer as spam
Phishing website promoted via this email:
Yet another WeTransfer-themed spam email promoting a link to download a .zip archive containing a malicious executable:
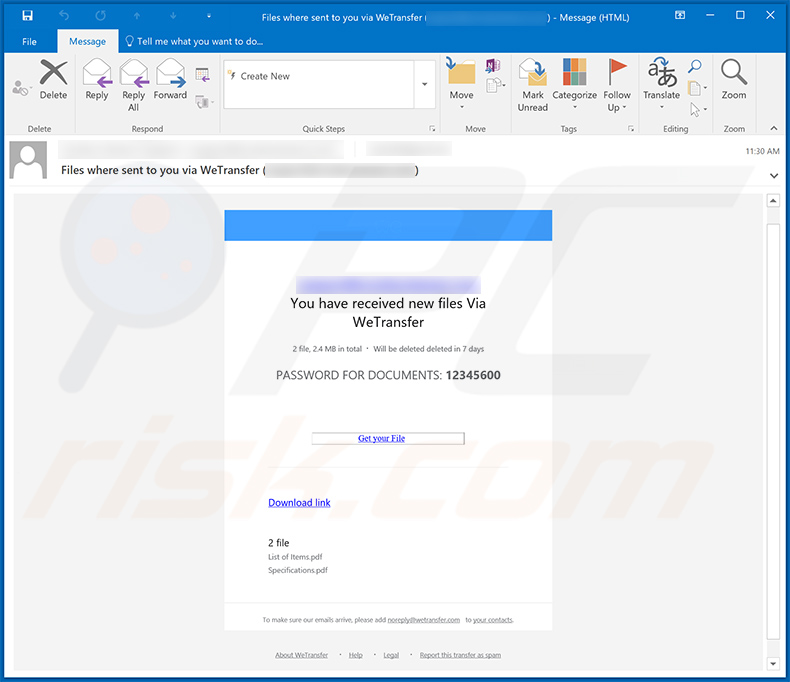
Text presented within:
Subject: Files where sent to you via WeTransfer (**********)
**********
You have received new files Via WeTransfer
2 file, 2.4 MB in total ・ Will be deleted deleted in 7 daysPASSWORD FOR DOCUMENTS: 12345600
Get your File
Download link
2 file
List of Items.pdf
Specifications.pdfTo make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
About WeTransfer ・ Help ・ Legal ・ Report this transfer as spam
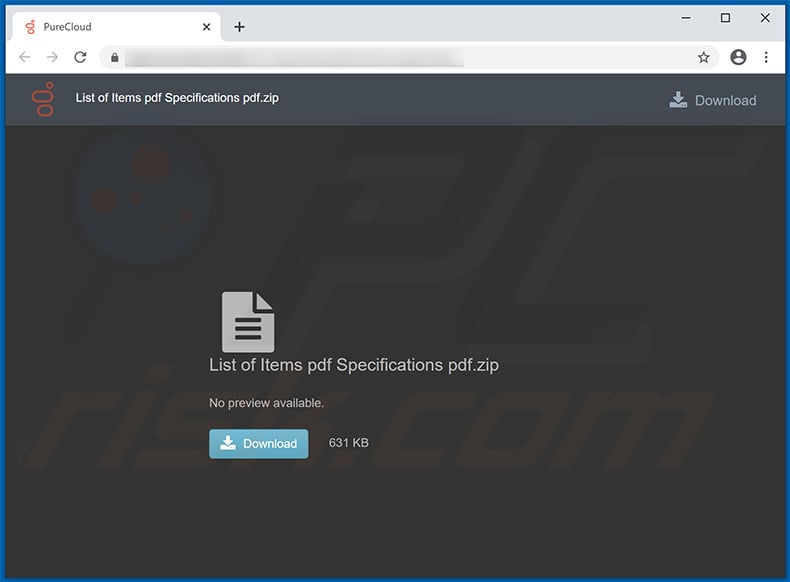
Screenshot of the download website the aforementioned link leads to:
Another WeTransfer-phishing themed spam email used to promote a phishing website:
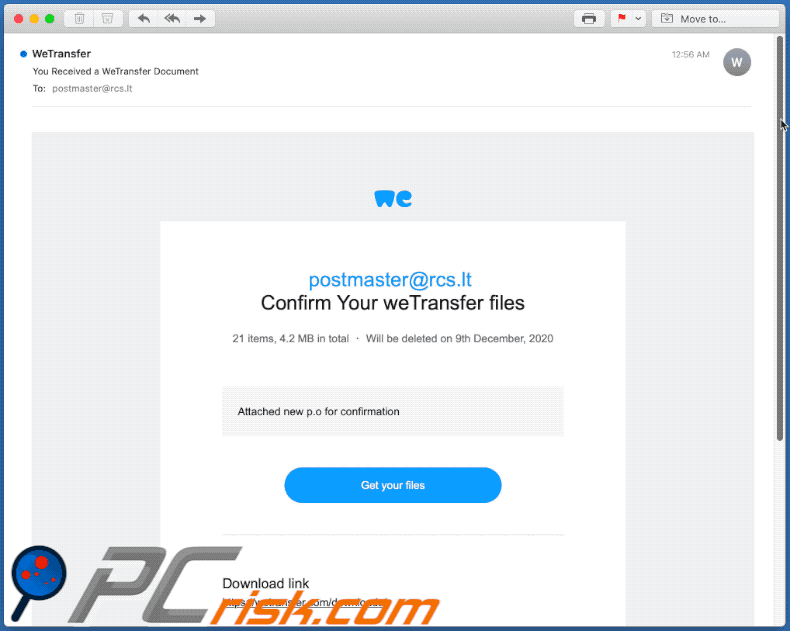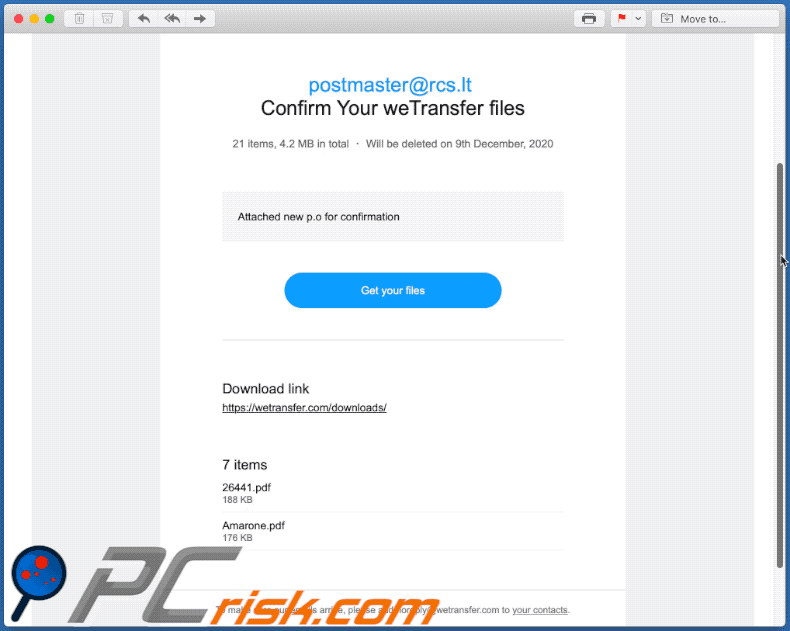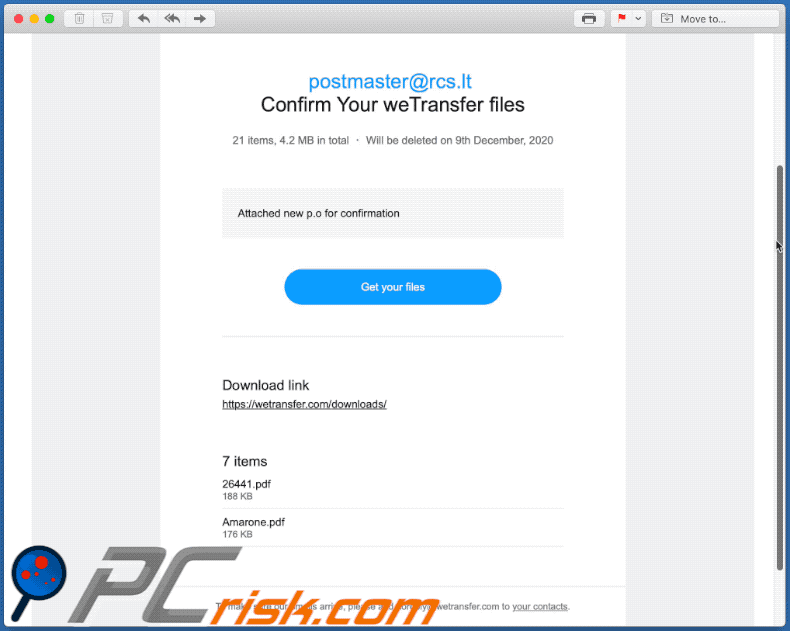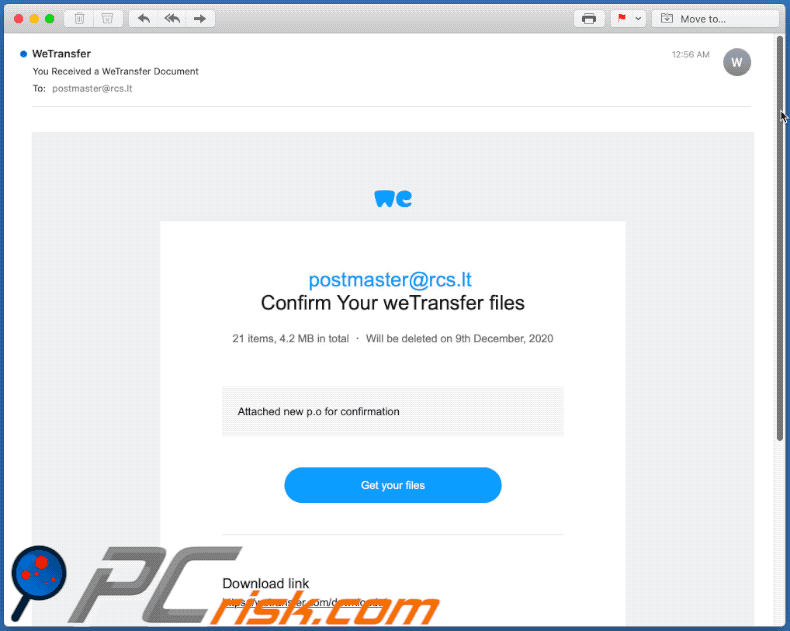
Text presented within:
Subject: You Received a WeTransfer Document
Click 'Download images' to view images
postmaster@rcs.lt
Confirm Your weTransfer files
21 items, 4.2 MB in total ・ Will be deleted on 9th December, 2020
Attached new p.o for confirmationGet your files
Download link
hxxps://wetransfer.com/downloads/
7 items
26441.pdf
188 KB
Amarone.pdf
176 KB
To make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
About WeTransfer ・ Help ・ Legal ・ Report this transfer as spam
Screenshot of the promoted phishing website:
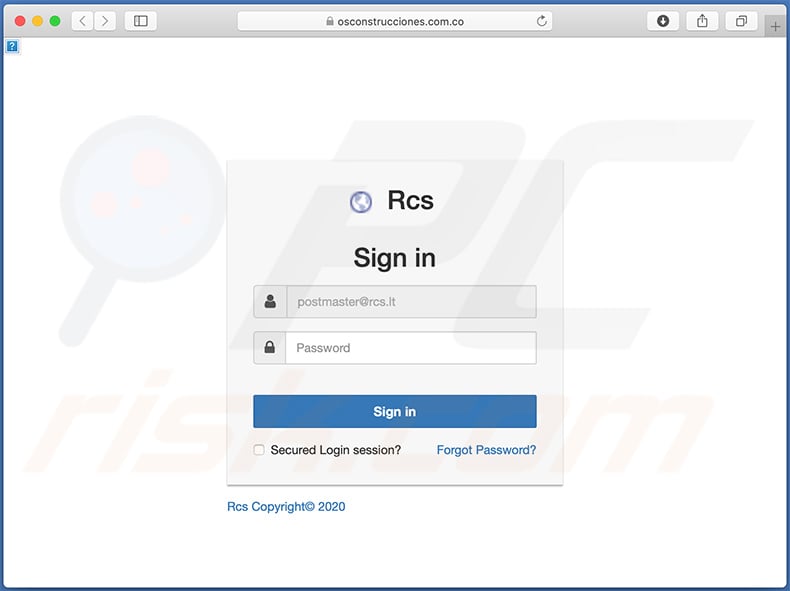
Another example of WeTransfer-themed spam email used to promote a phishing website:
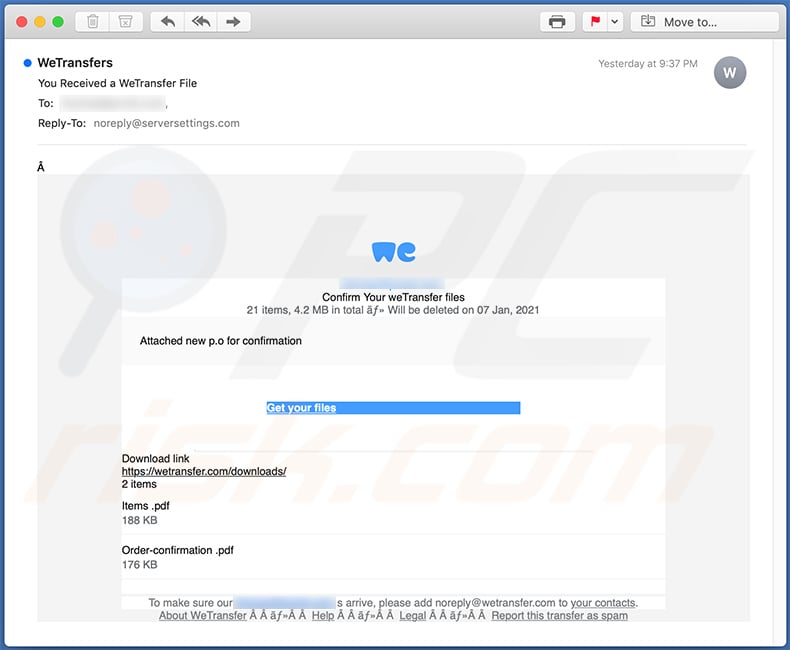
Text presented within:
Subject: You Received a WeTransfer File
-
Confirm Your weTransfer files
21 items, 4.2 MB in total Will be deleted on 07 Jan, 2021
Attached new p.o for confirmationGet your files
Â
Download link
hxxps://wetransfer.com/downloads/
2 items
Items .pdf
188 KB
Order-confirmation .pdf
176 KB
To make sure our - s arrive, please add noreply@wetransfer.com to your contacts.
About WeTransfer Legal Report this transfer as spam
Screenshot of the promoted phishing website:
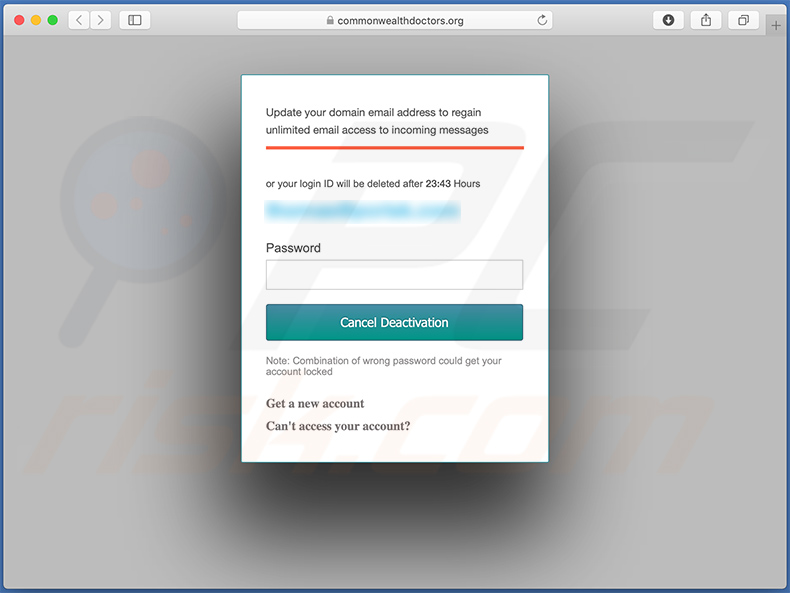
Another example of WeTransfer-themed spam email used to promote a phishing website:
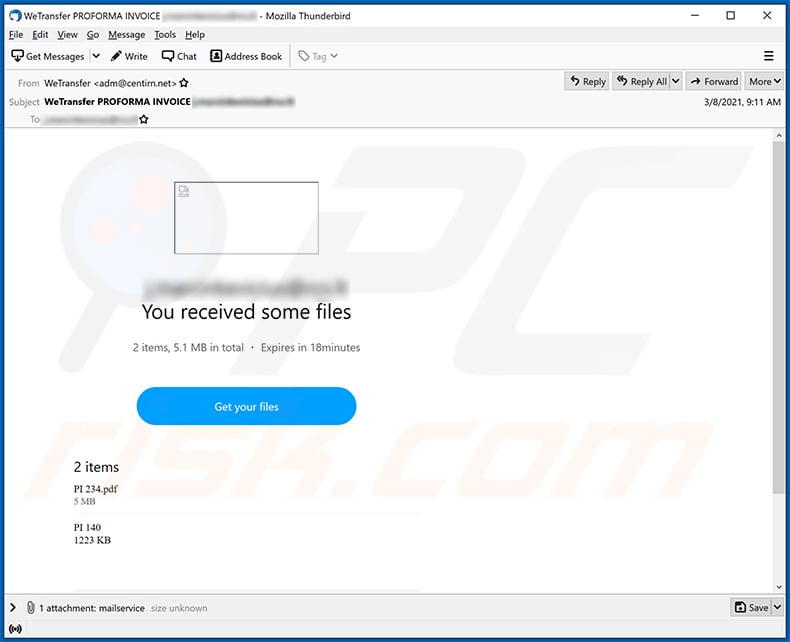
Text presented within:
Subject: WeTransfer PROFORMA INVOICE
********
You received some files
2 items, 5.1 MB in total ・ Expires in 18minutes
Get your files
2 items
PI 234.pdf
5 MB
PI 140
1223 KB
To make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
About WeTransfer ・ Help ・ Legal ・ Report this transfer as spam
Screenshot of the promoted phishing site (instinctive-coal-taurus.glitch.me):
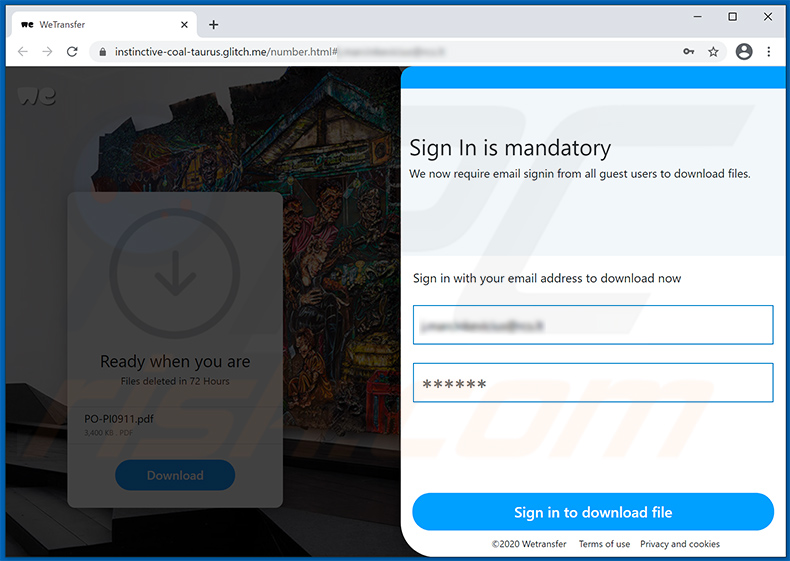
Yet another WeTransfer-themed spam email used to promote a phishing website:
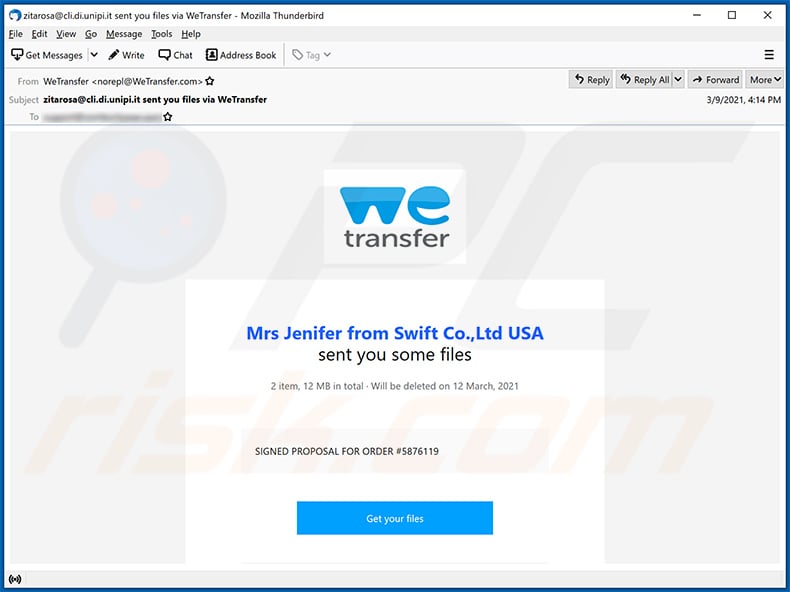
Text presented within:
Subject: ****** sent you files via WeTransfer
Mrs Jenifer from Swift Co.,Ltd USA
sent you some files
2 item, 12 MB in total · Will be deleted on 12 March, 2021SIGNED PROPOSAL FOR ORDER #5876119
Get your files
Screenshot of the promoted phishing website (turbo-arcade[.]gq):
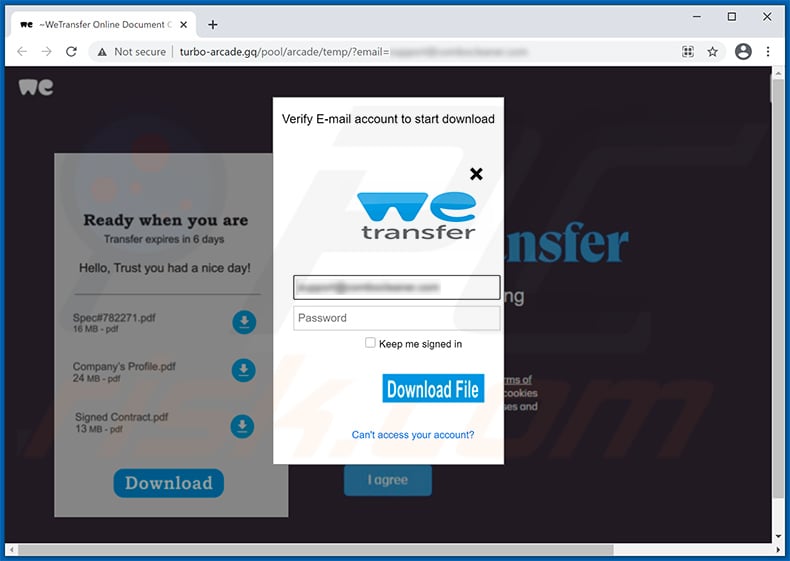
Yet another example of WeTransfer-themed spam email promoting a phishing website:
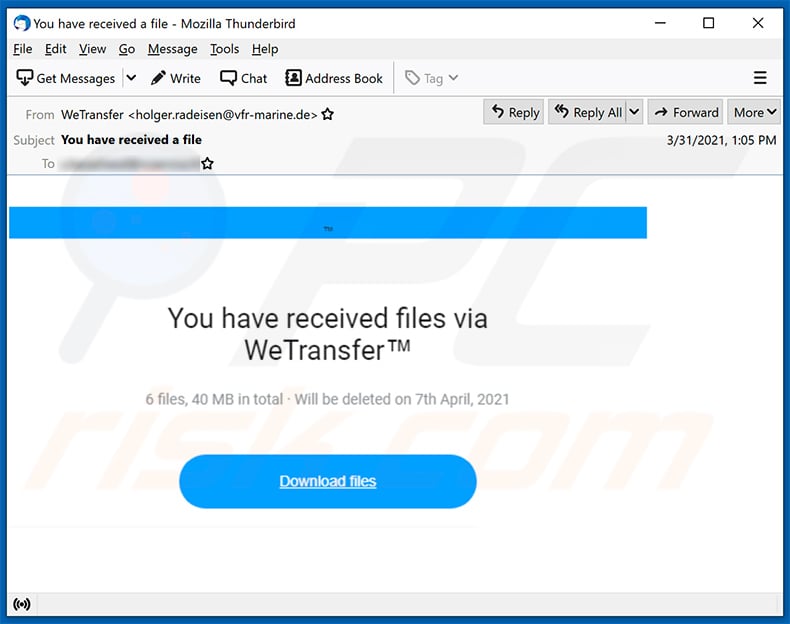
Text presented within:
Subject: You have received a file
You have received files via WeTransfer™
6 files, 40 MB in total
Will be deleted on 7th April, 2021
Download files
Yet another example of WeTransfer-themed spam email used to promote a phishing website:
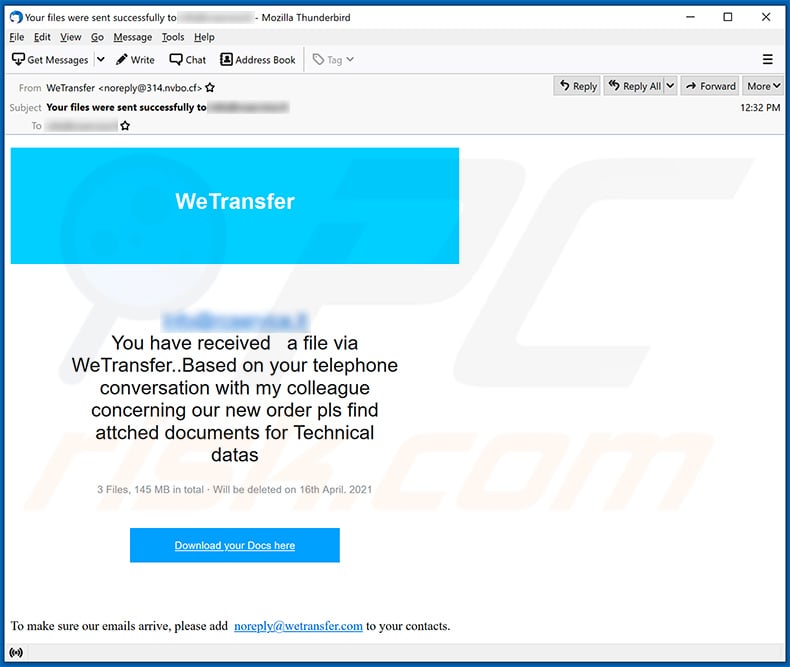
Text presented within:
Subject: Your files were sent successfully to ********
WeTransfer********
You have received a file via WeTransfer..Based on your telephone conversation with my colleague concerning our new order pls find attched documents for Technical datas
3 Files, 145 MB in total · Will be deleted on 16th April. 2021
Download your Docs here
To make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
Screenshot of the promoted phishing website (topchoiceconstructionsroofingservices[.]com[.]au):
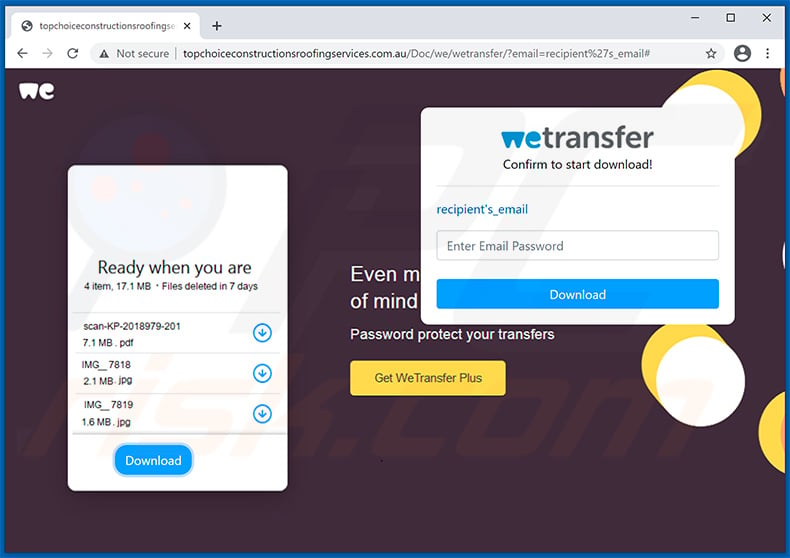
Yet another example of WeTransfer-themed spam email promoting a phishing site:
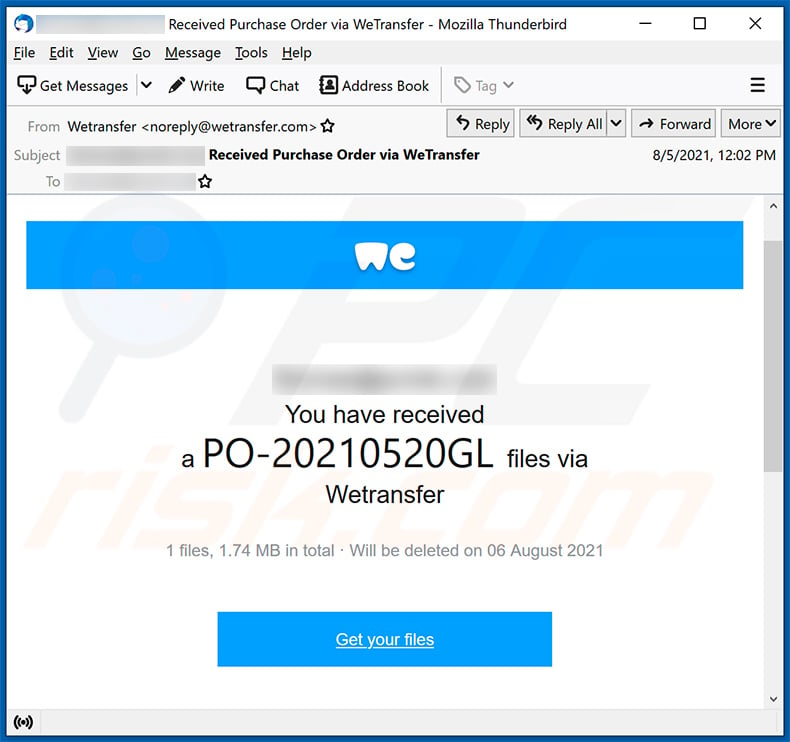
Text presented within:
Subject: ********* Received Purchase Order via WeTransfer
Click 'Download images' to view images
*********
You have received a PO-20210520GL files via Wetransfer
1 files, 1.74 MB in total · Will be deleted on 06 August 2021
Get your filesDownload link
*****1 file
PO-20210520GL.pdf
1.74MBTo make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
sent by wetransfersupport.wetransfer.com
About WeTransfer - Help - Legal - Report this transfer as spam
Screenshot of the promoted phishing website:
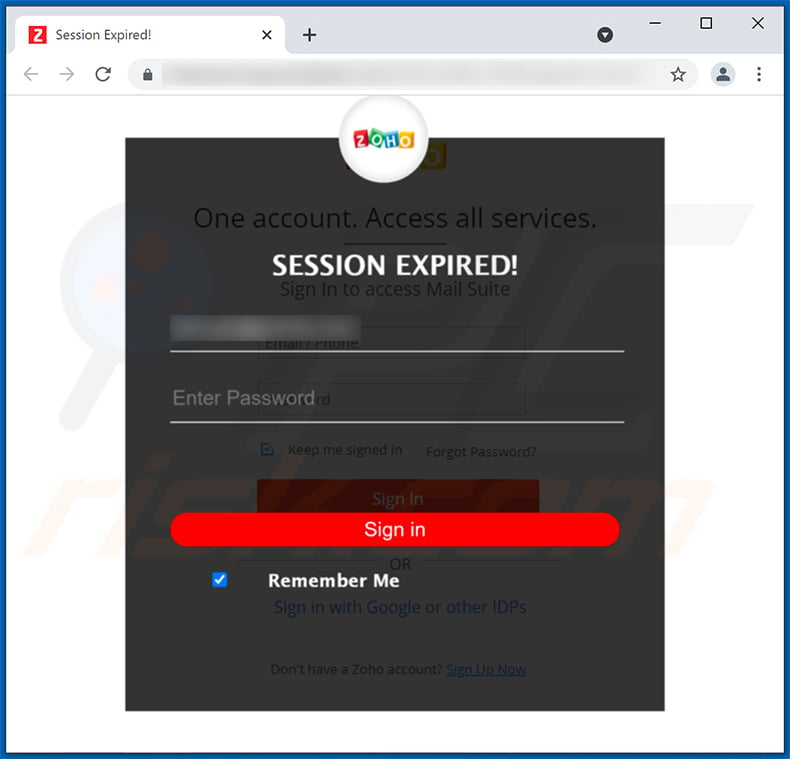
Another example of WeTransfer-themed spam email:
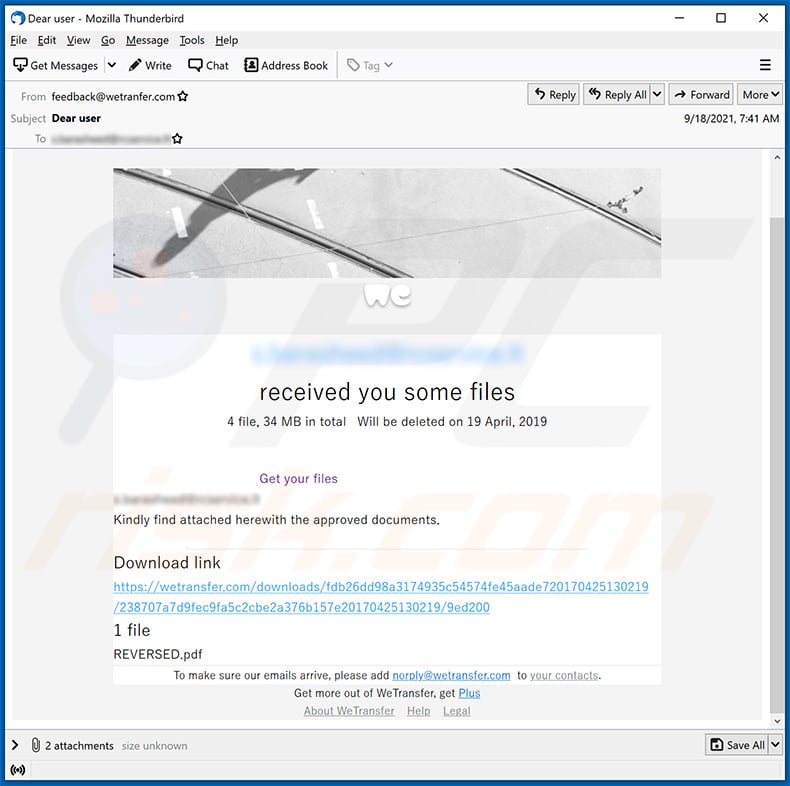
Text presented within:
Subject: Dear user
********
received you some files
4 file, 34 MB in total Will be deleted on 19 April, 2019
Get your files
********
Kindly find attached herewith the approved documents.
Download link
-
1 file
REVERSED.pdfTo make sure our emails arrive, please add norply@wetransfer.com to your contacts.
Get more out of WeTransfer, get Plus
About WeTransfer Help Legal
Screenshot of the promoted phishing site:
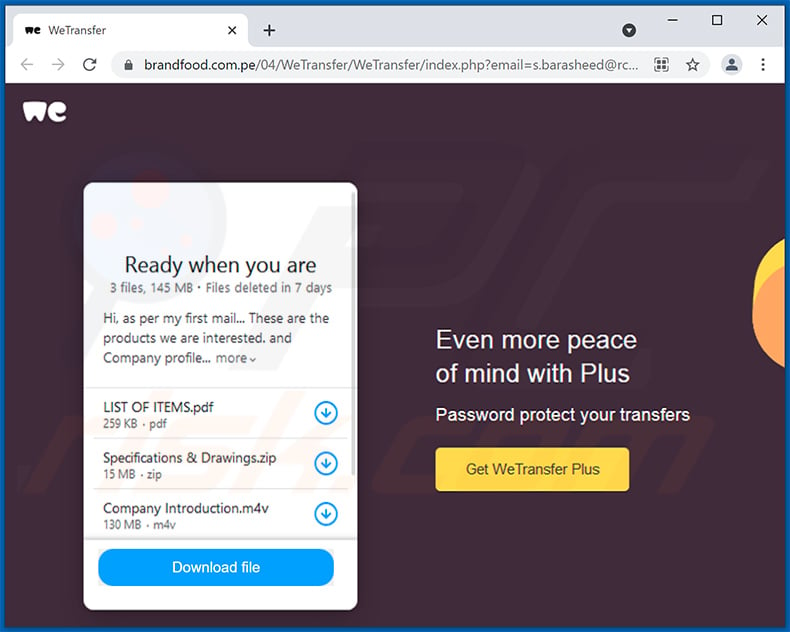
Yet another example of WeTransfer-themed spam email promoting a phishing site:
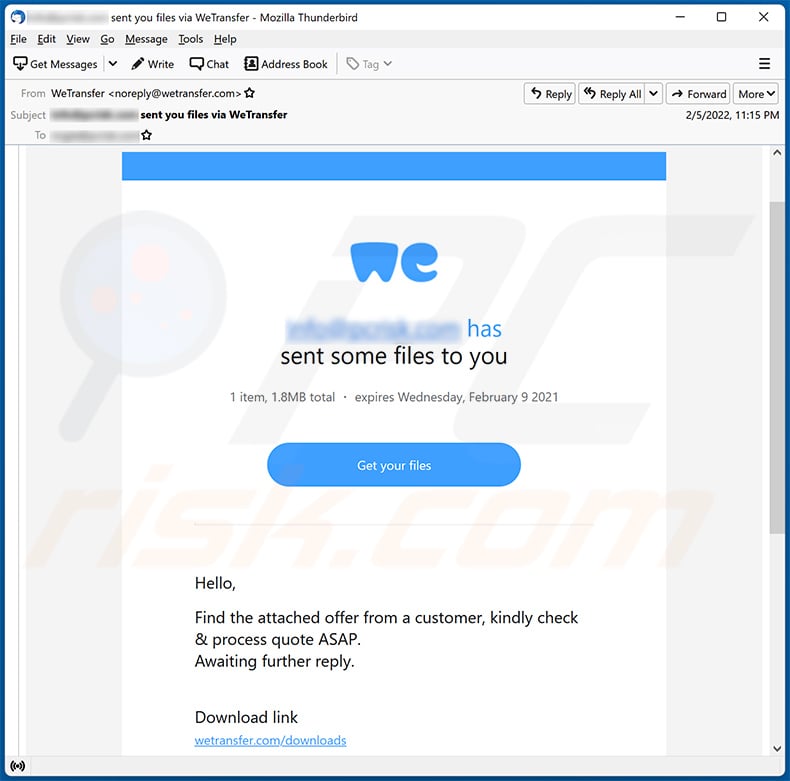
Text presented within:
Subject: - sent you files via WeTransfer
This transfer expires on 2021-01-28
- has
sent some files to you
1 item, 1.8MB total ・ expires Wednesday, February 9 2021
Get your files
Hello,Find the attached offer from a customer, kindly check & process quote ASAP.
Awaiting further reply.Download link
-
1 item
Contract Offer#202283.pdf
1.8 MBTo make sure you receive our emails, please add the email address noreply@wetransfer.com to your contact list.
About WeTransfer ・ Help ・ Legal Notice ・ Report this transfer as spam
Another example of WeTransfer spam email promoting a phishing site:
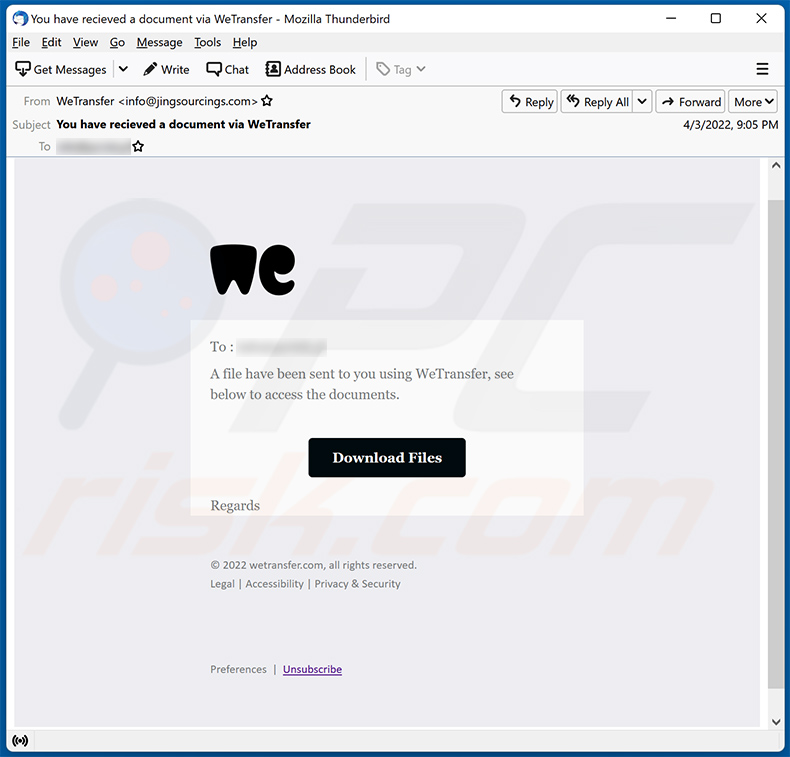
Text presented within:
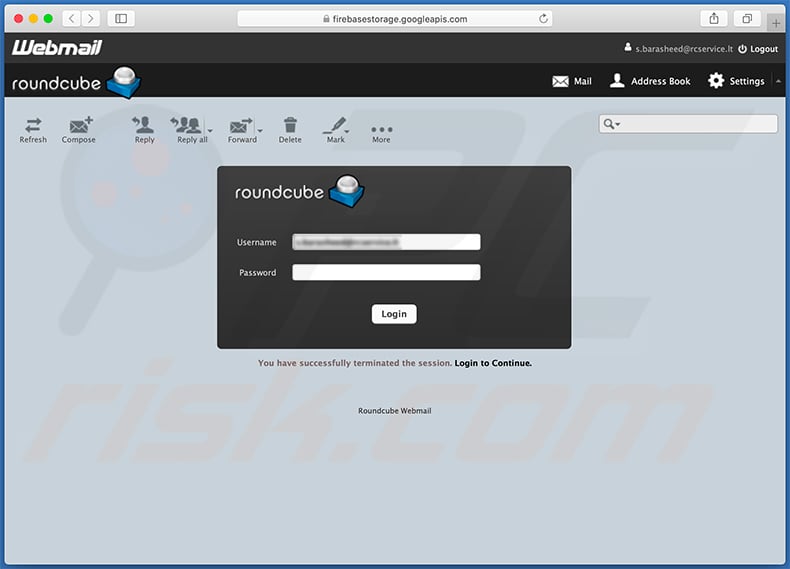
Subject: You have recieved a document via WeTransfer
Roundcube update
To : -
A file have been sent to you using WeTransfer, see below to access the documents.
Download Files
Regards
© 2022 wetransfer.com, all rights reserved.
Legal | Accessibility | Privacy & SecurityPreferences | Unsubscribe
Screenshot of the promoted phishing site (the website's design corresponds to recipient's email provider):
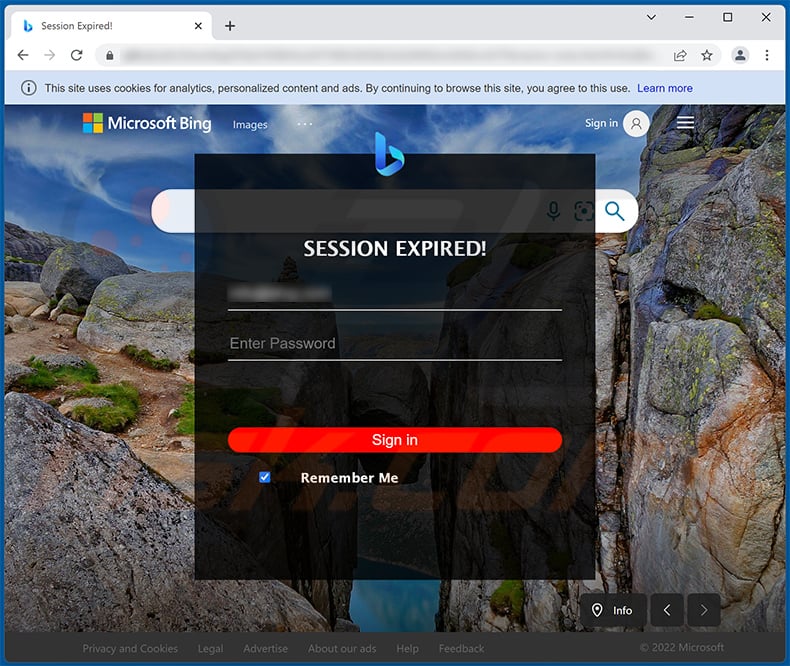
Yet another WeTransfer-themed spam email promoting a phishing site:
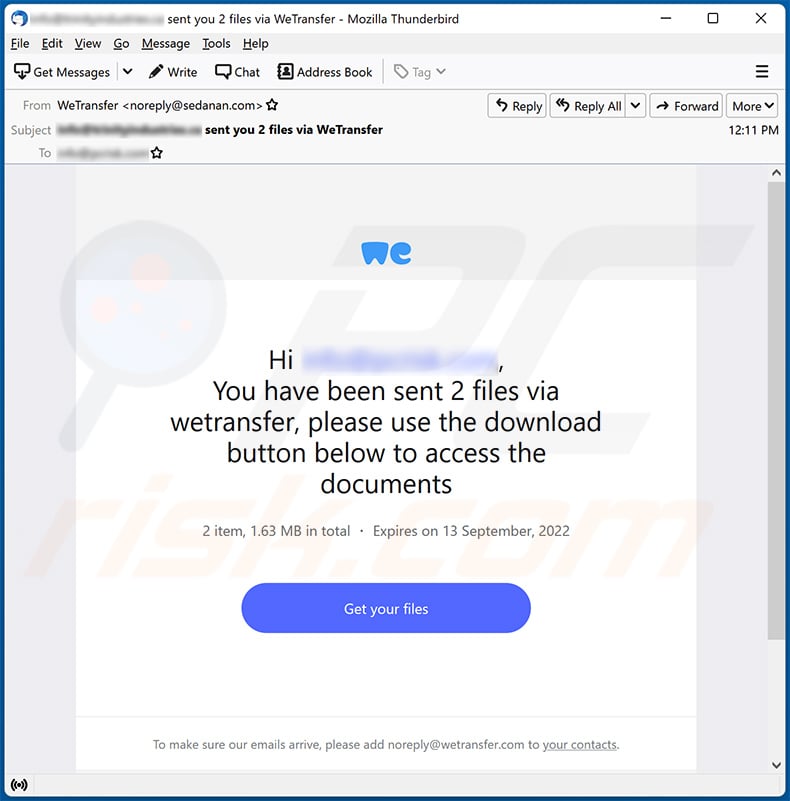
Text presented within:
Subject: ******** sent you 2 files via WeTransfer
Click 'Download images' to view images
Hi ********,
You have been sent 2 files via wetransfer, please use the download button below to access the documents
2 item, 1.63 MB in total ・ Expires on 13 September, 2022
Get your filesTo make sure our emails arrive, please add noreply@wetransfer.com to your contacts.
About WeTransfer ・ Help ・ Legal ・ Report this transfer as spam
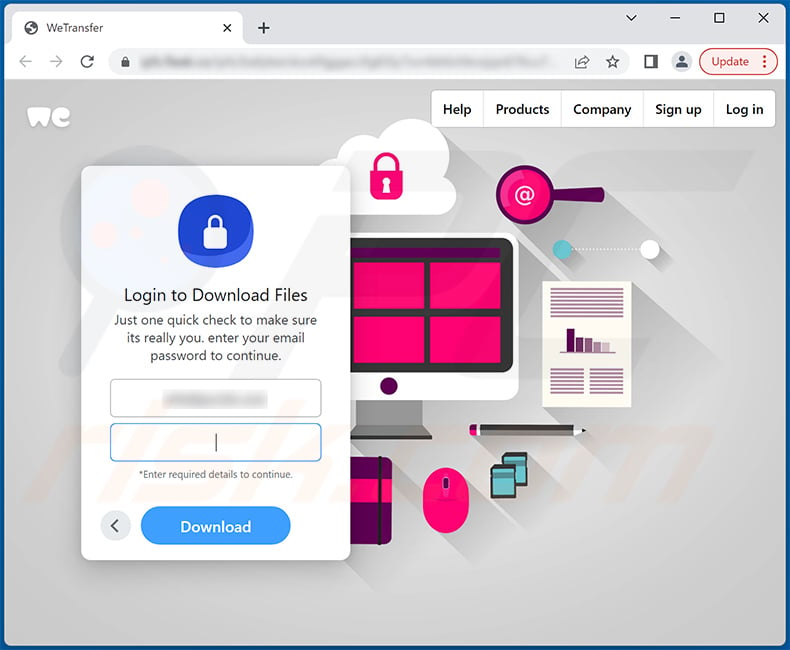
Screenshot of the promoted phishing site:
Yet another example of WeTransfer-themed spam email promoting a phishing site:
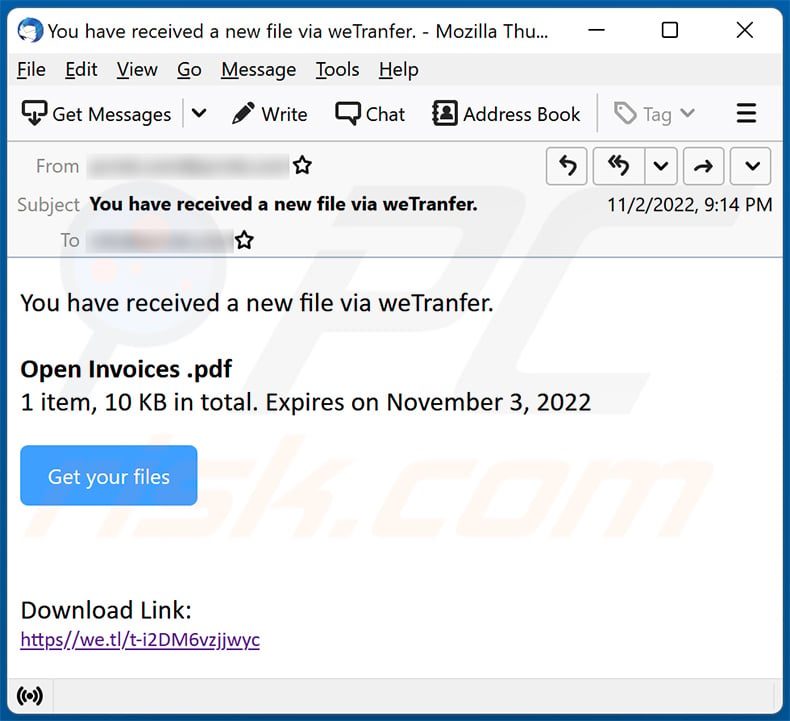
Text presented within:
Subject: You have received a new file via weTranfer.
You have received a new file via weTranfer.
Open Invoices .pdf
1 item, 10 KB in total. Expires on November 3, 2022
Get your filesDownload Link:
-
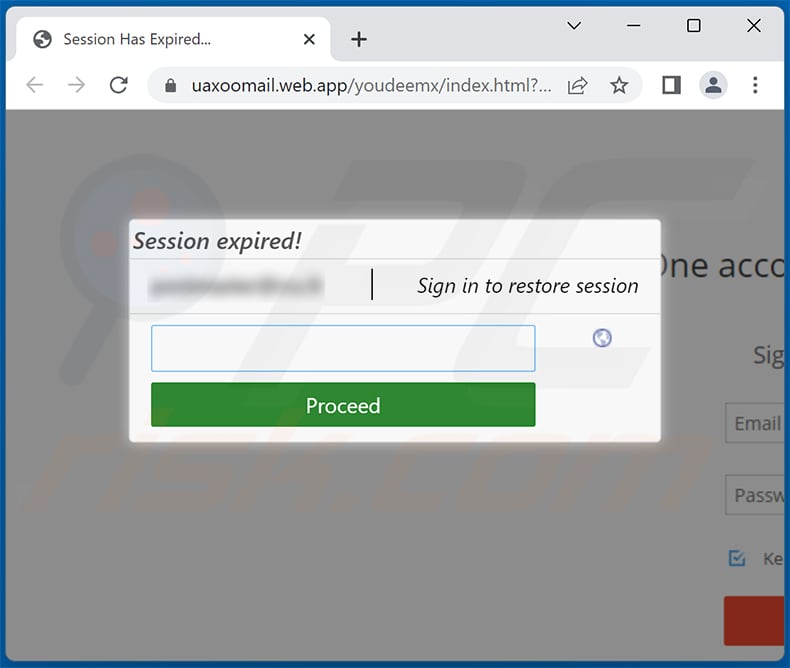
Screenshot of the promoted phishing site:
Yet another example of WeTransfer-themed spam email promoting a phishing site:
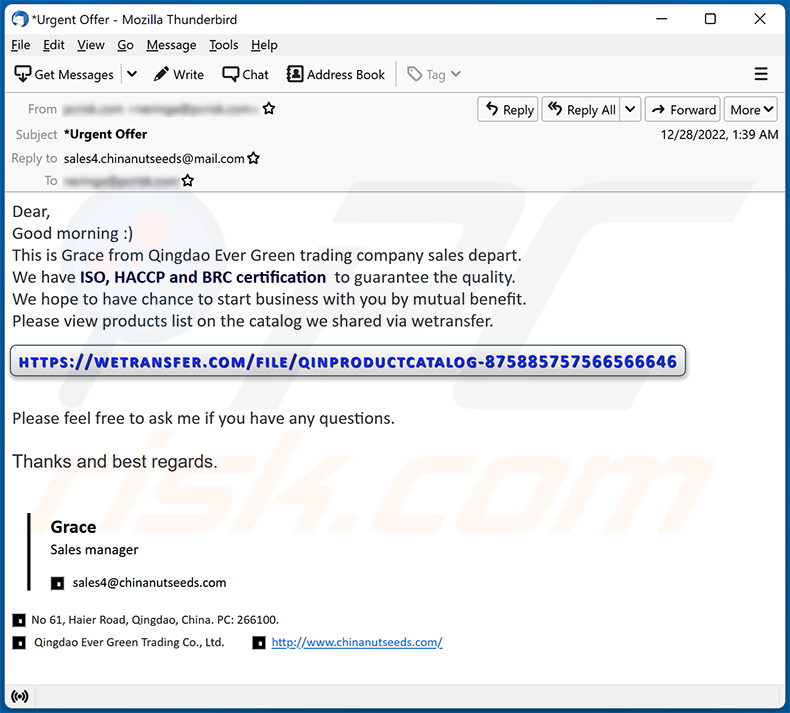
Text presented within:
Subject: *Urgent Offer
Dear,
Good morning :)
This is Grace from Qingdao Ever Green trading company sales depart.
We have ISO, HACCP and BRC certification to guarantee the quality.
We hope to have chance to start business with you by mutual benefit.
Please view products list on the catalog we shared via wetransfer.Please feel free to ask me if you have any questions.
Thanks and best regards.
Grace
Sales managersales4@chinanutseeds.com
No 61, Haier Road, Qingdao, China. PC: 266100.
Qingdao Ever Green Trading Co., Ltd.hxxp://www.chinanutseeds.com/
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is WeTransfer spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
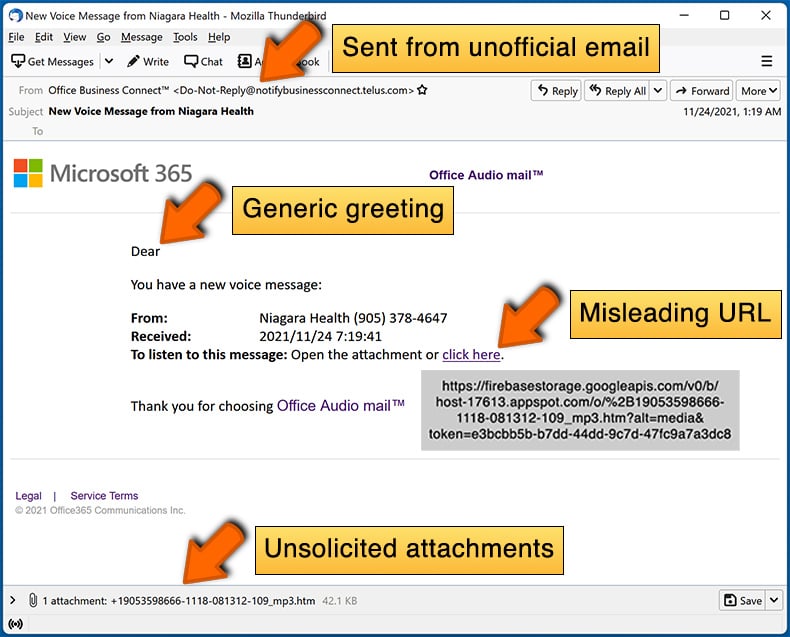
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Frequently Asked Questions (FAQ)
Why did I receive this email?
This email is not personal. Most likely, scammers have obtained your email address from a compromised website or in some other way. When threat actors use email to deliver malware, they send the same letter to all addresses in their database.
I have downloaded and opened a file attached to this email, is my computer infected?
It depends on the type of the file. If the file was an executable file, then there is a high chance that a computer is already infected. Not all files (PDF, MS Office documents, archive files, etc.) can infect computers right away. It is often required to perform additional steps, for instance, to enable macros commands in malicious documents for malware to be executed.
I have read the email but didn't open the attachment, is my computer infected?
No, an email cannot directly infect a computer. Computers get infected only after opening malicious files or links.
Will Combo Cleaner remove malware infections that were present in email attachment?
Yes, Combo Cleaner can detect and eliminate almost all known malware. It is important to scan the operating system using a full scan. Otherwise, the antivirus software may not detect high-risk malware that is hidden deep in the operating system.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion