How to spot scams like Beneficiary/Inheritance phishing email
Phishing/ScamAlso Known As: Beneficiary/Inheritance spam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is Beneficiary/Inheritance email scam?
Generally, scammers behind email scams such as this one attempt to trick recipients into believing that they are beneficiaries of a will, life insurance policy, etc. Scammers ask recipients to contact them and provide various information. At some point, recipients are asked to pay a processing fee or transfer charge.
Note that scammers exploit the names of existing, often well-known organizations and companies to make their emails seem legitimate.
More about the Beneficiary/Inheritance email scam
There are at least two variants of this email scam. One is disguised as a release of funds message claiming that the recipient is a beneficiary of 3,800,000.000 dollars.
Another one is disguised as a message regarding a will (testament) of a person who has died of COVID-19 and claiming that the recipient, who supposedly has an identical surname, is named as the beneficiary of 21,300,000.000 dollars.
In most cases, when recipients contact or reply to scammers behind these emails they are asked to provide personal, sensitive information such as credit card details or to transfer funds (as a processing fee, transfer charge, etc.).
I.e., scammers attempt to extort money or sensitive information, which can be used for malicious purposes (e.g., to make fraudulent purchases and transactions, and steal identities).
| Name | Beneficiary/Inheritance Email Scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud. |
| Fake Claim | Recipient is a eligible to receive distributions from a will or life insurance policy. |
| Disguise | A message from the Dubai Islamic bank. |
| Symptoms | Unauthorized online purchases, changed online account passwords, identity theft, illegal access of the computer. |
| Distribution methods | Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled domains. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Examples of similar scams
"United Nations Online Lotto Email Scam", "USAA Email Scam", and "You Received A Transfer In The Amount Email Scam" are examples of other email scams. Note that cyber criminals can use emails to extort money and sensitive information, and distribute malware (such as Agent Tesla, Urnsif, TrickBot, Adwind, etc.).
How do spam campaigns infect computers?
Ransomware and other malware infections are commonly spread through malspam campaigns, untrusted file/software download sources, fake (third party) software updating tools, Trojans and unofficial software activation tools. Using malspam, criminals send emails that have a malicious file attached, or include a website link designed to download a malicious file.
Their main goal is to trick recipients into executing the file, which then infects the computer with malware. Cyber criminals usually attach a Microsoft Office document, archive file (ZIP, RAR), PDF document, executable file (.exe) or JavaScript file, and wait until recipients open it.
Note that malicious MS Office documents can install malware only when users enable editing/content (macros commands). If the documents are opened with MS Office versions prior to 2010, however, the documents install malicious software automatically, since these older versions do not include "Protected View" mode.
Examples of untrusted file and software download sources are Peer-to-Peer networks (torrent clients), free file hosting websites, freeware download sites, and unofficial web pages. These are used to distribute malicious files by disguising them as legitimate and regular.
When users download and open (execute) the files, however, they inadvertently install malware. Fake software updating tools cause damage by installing malware rather than updates/fixes for installed software, or by exploiting bugs/flaws of outdated software.
Trojans are malicious programs that can cause chain infections by installing other software of this kind. Note that malware can only be distributed in this way if Trojans are already installed on computers.
Unofficial activation ('cracking') tools are illegal programs that supposedly activate licensed software free of charge and bypass activation, however, they often install other malicious programs instead.
How to avoid installation of malware
You are advised to research all software before download/installation. Use only official and verified download channels. Unofficial and free file-hosting websites, Peer-to-Peer sharing networks (BitTorrent, Gnutella, eMule), and other third party downloaders commonly offer harmful and bundled content, and are therefore untrusted and should be avoided.
When downloading/installing, read the terms, study all possible options, use the "Custom/Advanced" settings and opt-out of additional apps, tools, features, and so on. Intrusive advertisements typically seem legitimate, however, they can redirect to dubious and malicious sites (e.g. gambling, pornography, adult-dating, and many others).
If you encounter ads or redirects of this kind, inspect the system and remove all dubious applications and browser extensions/plug-ins immediately. If you have already opened malicious attachments, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the Beneficiary/Inheritance email scam:
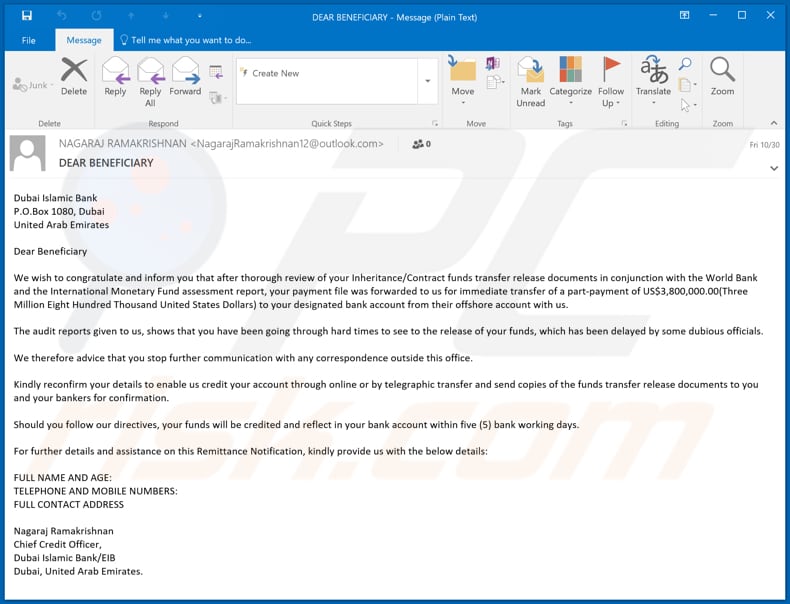
Subject: DEAR BENEFICIARY
Dubai Islamic Bank
P.O.Box 1080, Dubai
United Arab EmiratesDear Beneficiary
We wish to congratulate and inform you that after thorough review of your Inheritance/Contract funds transfer release documents in conjunction with the World Bank and the International Monetary Fund assessment report, your payment file was forwarded to us for immediate transfer of a part-payment of US$3,800,000.00(Three Million Eight Hundred Thousand United States Dollars) to your designated bank account from their offshore account with us.
The audit reports given to us, shows that you have been going through hard times to see to the release of your funds, which has been delayed by some dubious officials.
We therefore advice that you stop further communication with any correspondence outside this office.
Kindly reconfirm your details to enable us credit your account through online or by telegraphic transfer and send copies of the funds transfer release documents to you and your bankers for confirmation.
Should you follow our directives, your funds will be credited and reflect in your bank account within five (5) bank working days.
For further details and assistance on this Remittance Notification, kindly provide us with the below details:
FULL NAME AND AGE:
TELEPHONE AND MOBILE NUMBERS:
FULL CONTACT ADDRESSNagaraj Ramakrishnan
Chief Credit Officer,
Dubai Islamic Bank/EIB
Dubai, United Arab Emirates.
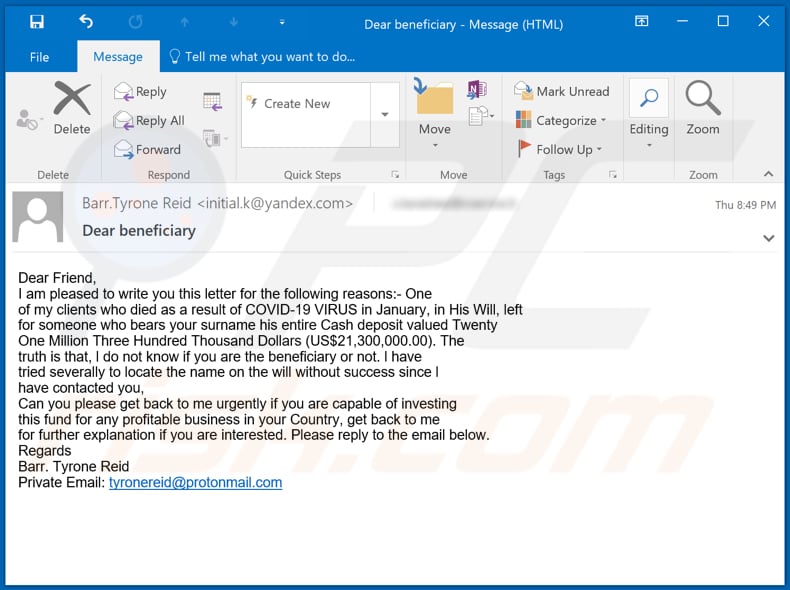
Screenshot of the Coronavirus-themed variant:
Text in this variant:
Subject: Dear beneficiary
Dear Friend,
I am pleased to write you this letter for the following reasons:- One
of my clients who died as a result of COVID-19 VIRUS in January, in His Will, left
for someone who bears your surname his entire Cash deposit valued Twenty
One Million Three Hundred Thousand Dollars (US$21,300,000.00). The
truth is that, l do not know if you are the beneficiary or not. l have
tried severally to locate the name on the will without success since l
have contacted you,
Can you please get back to me urgently if you are capable of investing
this fund for any profitable business in your Country, get back to me
for further explanation if you are interested. Please reply to the email below.
Regards
Barr. Tyrone Reid
Private Email: tyronereid@protonmail.com
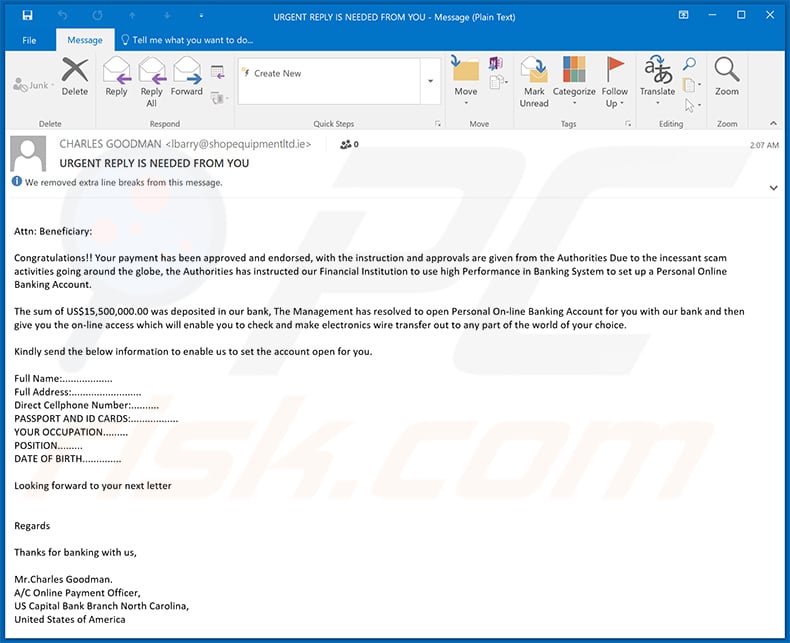
Another variant of "Beneficiary/Inheritance" scam email:
Text presented within:
Subject: URGENT REPLY IS NEEDED FROM YOU
Attn: Beneficiary:
Congratulations!! Your payment has been approved and endorsed, with the instruction and approvals are given from the Authorities Due to the incessant scam activities going around the globe, the Authorities has instructed our Financial Institution to use high Performance in Banking System to set up a Personal Online Banking Account.
The sum of US$15,500,000.00 was deposited in our bank, The Management has resolved to open Personal On-line Banking Account for you with our bank and then give you the on-line access which will enable you to check and make electronics wire transfer out to any part of the world of your choice.
Kindly send the below information to enable us to set the account open for you.
Full Name:..................
Full Address:.........................
Direct Cellphone Number:..........
PASSPORT AND ID CARDS:.................
YOUR OCCUPATION.........
POSITION.........
DATE OF BIRTH..............Looking forward to your next letter
Regards
Thanks for banking with us,
Mr.Charles Goodman.
A/C Online Payment Officer,
US Capital Bank Branch North Carolina,
United States of America
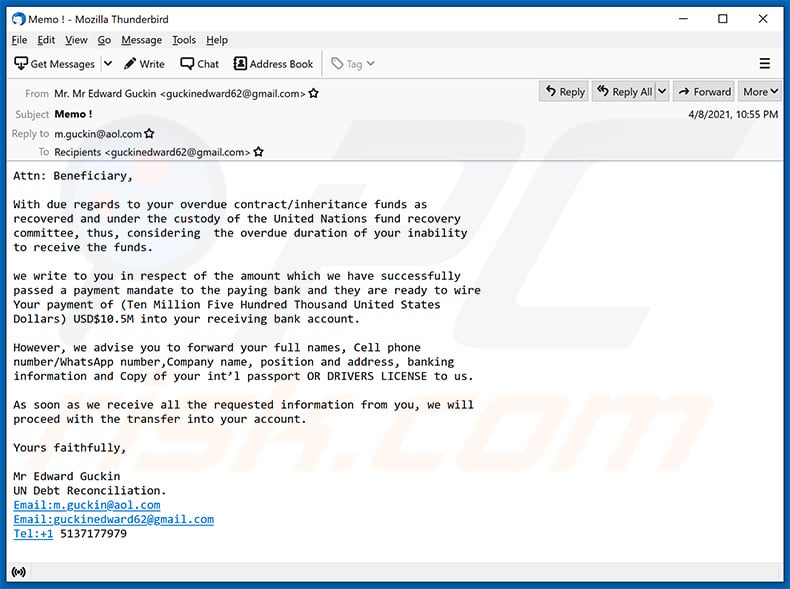
Yet another variant of Beneficiary/Inheritance-themed spam email:
Text presented within:
Subject: Memo !
Attn: Beneficiary,
With due regards to your overdue contract/inheritance funds as
recovered and under the custody of the United Nations fund recovery
committee, thus, considering the overdue duration of your inability
to receive the funds.we write to you in respect of the amount which we have successfully
passed a payment mandate to the paying bank and they are ready to wire
Your payment of (Ten Million Five Hundred Thousand United States
Dollars) USD$10.5M into your receiving bank account.However, we advise you to forward your full names, Cell phone
number/WhatsApp number,Company name, position and address, banking
information and Copy of your int’l passport OR DRIVERS LICENSE to us.As soon as we receive all the requested information from you, we will
proceed with the transfer into your account.Yours faithfully,
Mr Edward Guckin
UN Debt Reconciliation.
Email:m.guckin@aol.com
Email:guckinedward62@gmail.com
Tel:+1 5137177979
Yet another example of Beneficiary/Inheritance-themed spam email:
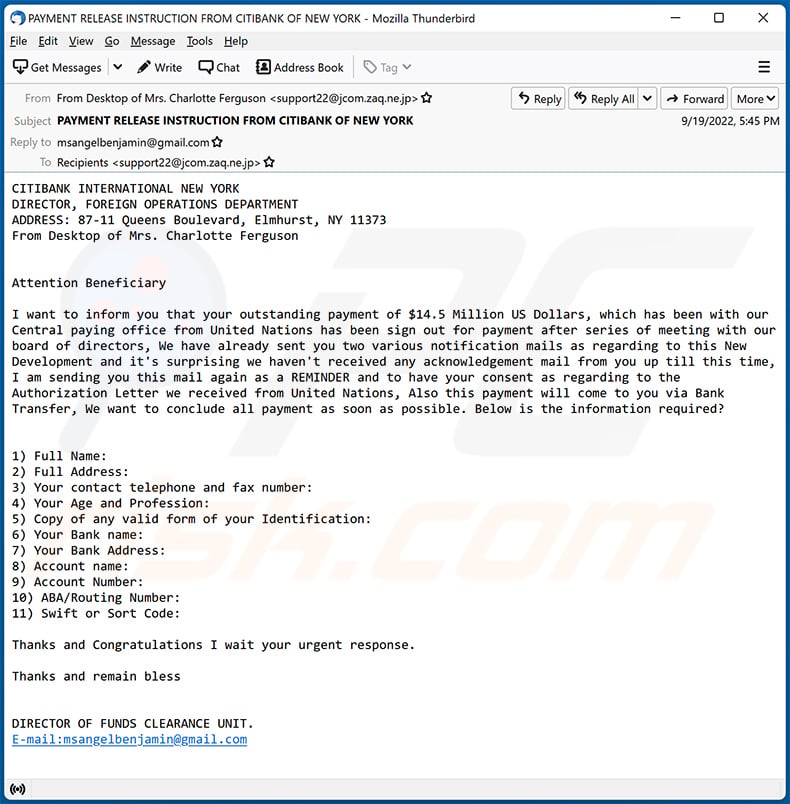
Text presented within:
Subject: PAYMENT RELEASE INSTRUCTION FROM CITIBANK OF NEW YORK
CITIBANK INTERNATIONAL NEW YORK
DIRECTOR, FOREIGN OPERATIONS DEPARTMENT
ADDRESS: 87-11 Queens Boulevard, Elmhurst, NY 11373
From Desktop of Mrs. Charlotte Ferguson
Attention BeneficiaryI want to inform you that your outstanding payment of $14.5 Million US Dollars, which has been with our Central paying office from United Nations has been sign out for payment after series of meeting with our board of directors, We have already sent you two various notification mails as regarding to this New Development and it's surprising we haven't received any acknowledgement mail from you up till this time, I am sending you this mail again as a REMINDER and to have your consent as regarding to the Authorization Letter we received from United Nations, Also this payment will come to you via Bank Transfer, We want to conclude all payment as soon as possible. Below is the information required?
1) Full Name:
2) Full Address:
3) Your contact telephone and fax number:
4) Your Age and Profession:
5) Copy of any valid form of your Identification:
6) Your Bank name:
7) Your Bank Address:
8) Account name:
9) Account Number:
10) ABA/Routing Number:
11) Swift or Sort Code:Thanks and Congratulations I wait your urgent response.
Thanks and remain bless
DIRECTOR OF FUNDS CLEARANCE UNIT.
E-mail:msangelbenjamin@gmail.com
Yet another example of beneficiary-themed spam email:
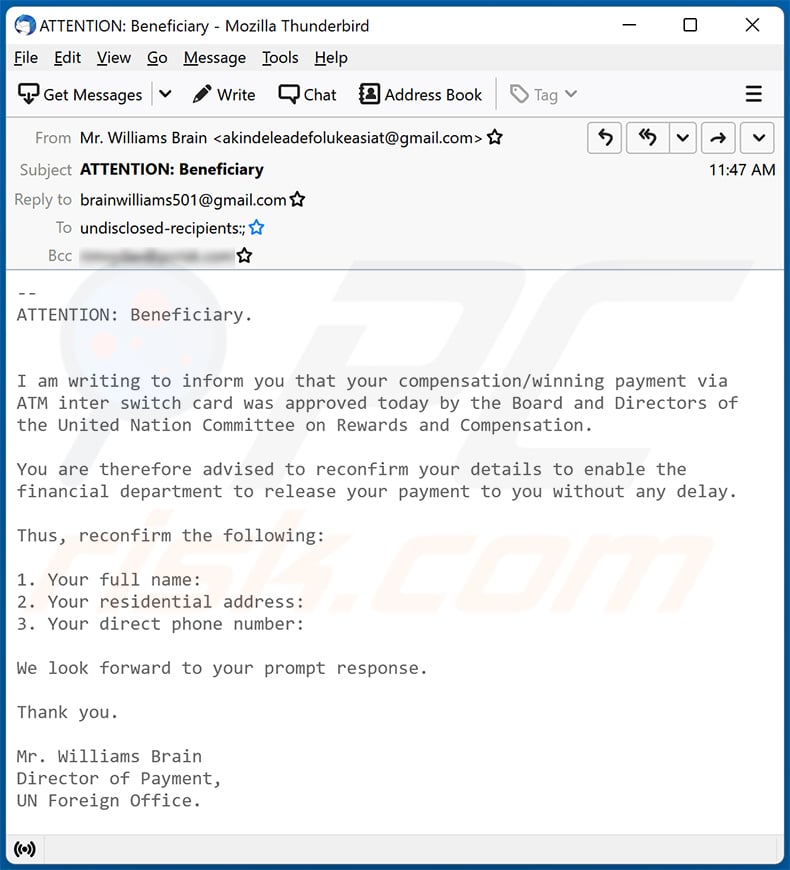
Text presented within:
Subject: ATTENTION: Beneficiary
--
ATTENTION: Beneficiary.
I am writing to inform you that your compensation/winning payment via
ATM inter switch card was approved today by the Board and Directors of
the United Nation Committee on Rewards and Compensation.You are therefore advised to reconfirm your details to enable the
financial department to release your payment to you without any delay.Thus, reconfirm the following:
1. Your full name:
2. Your residential address:
3. Your direct phone number:We look forward to your prompt response.
Thank you.
Mr. Williams Brain
Director of Payment,
UN Foreign Office.
Yet another example of an email from "Beneficiary/Inheritance" spam campaign:
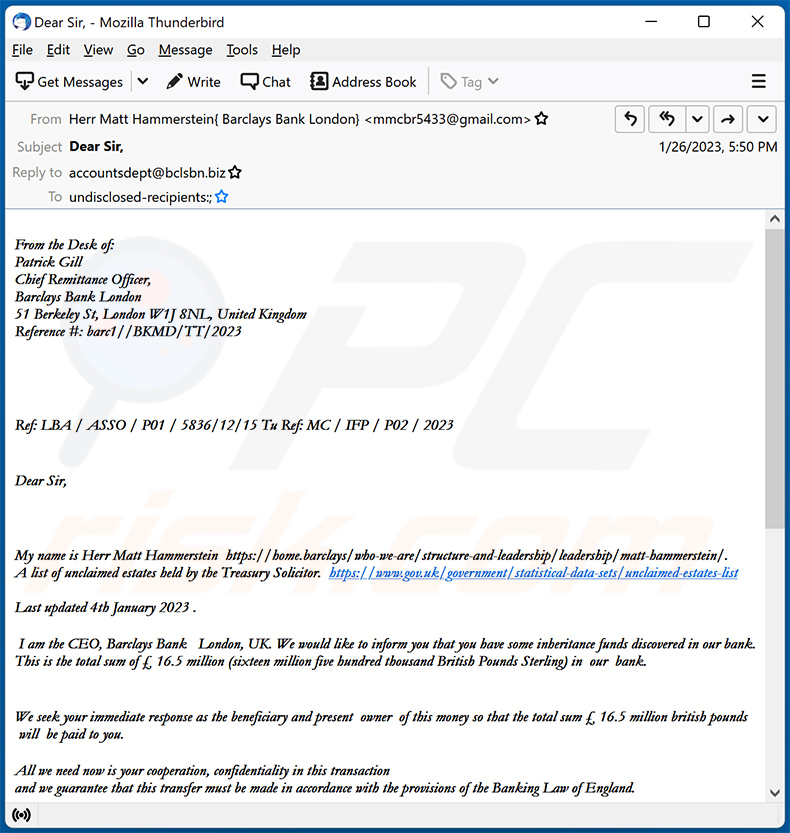
Text presented within:
Subject: Dear Sir,
From the Desk of:
Patrick Gill
Chief Remittance Officer,
Barclays Bank London
51 Berkeley St, London W1J 8NL, United Kingdom
Reference #: barc1//BKMD/TT/2023
Ref: LBA / ASSO / P01 / 5836/12/15 Tu Ref: MC / IFP / P02 / 2023
Dear Sir,My name is Herr Matt Hammerstein -.
A list of unclaimed estates held by the Treasury Solicitor. -Last updated 4th January 2023 .
I am the CEO, Barclays Bank London, UK. We would like to inform you that you have some inheritance funds discovered in our bank. This is the total sum of £ 16.5 million (sixteen million five hundred thousand British Pounds Sterling) in our bank.
We seek your immediate response as the beneficiary and present owner of this money so that the total sum £ 16.5 million british pounds will be paid to you.
All we need now is your cooperation, confidentiality in this transaction
and we guarantee that this transfer must be made in accordance with the provisions of the Banking Law of England.Send the below details to us .
1. Full Name:
2. Your direct mobile number:
3. Your contact address:
Herr Matt Hammerstein
From the Desk of:
Patrick Gill
Chief Remittance Officer,
Barclays Bank London
51 Berkeley St, London W1J 8NL, United Kingdom
Reference #: barc1//BKMD/TT/2023
Another example of beneficiary/inheritance-themed spam email:
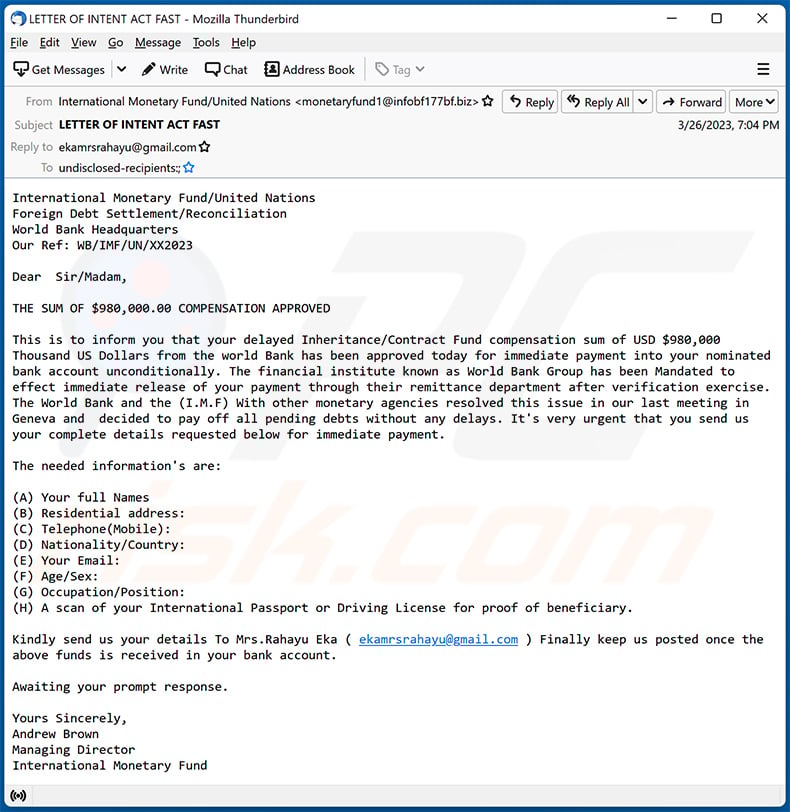
Text presented within:
Subject: LETTER OF INTENT ACT FAST
International Monetary Fund/United Nations
Foreign Debt Settlement/Reconciliation
World Bank Headquarters
Our Ref: WB/IMF/UN/XX2023Dear Sir/Madam,
THE SUM OF $980,000.00 COMPENSATION APPROVED
This is to inform you that your delayed Inheritance/Contract Fund compensation sum of USD $980,000 Thousand US Dollars from the world Bank has been approved today for immediate payment into your nominated bank account unconditionally. The financial institute known as World Bank Group has been Mandated to effect immediate release of your payment through their remittance department after verification exercise. The World Bank and the (I.M.F) With other monetary agencies resolved this issue in our last meeting in Geneva and decided to pay off all pending debts without any delays. It's very urgent that you send us
your complete details requested below for immediate payment.The needed information's are:
(A) Your full Names
(B) Residential address:
(C) Telephone(Mobile):
(D) Nationality/Country:
(E) Your Email:
(F) Age/Sex:
(G) Occupation/Position:
(H) A scan of your International Passport or Driving License for proof of beneficiary.Kindly send us your details To Mrs.Rahayu Eka ( ekamrsrahayu@gmail.com ) Finally keep us posted once the above funds is received in your bank account.
Awaiting your prompt response.
Yours Sincerely,
Andrew Brown
Managing Director
International Monetary Fund
Another example of an email from "Beneficiary/Inheritance" spam campaign:
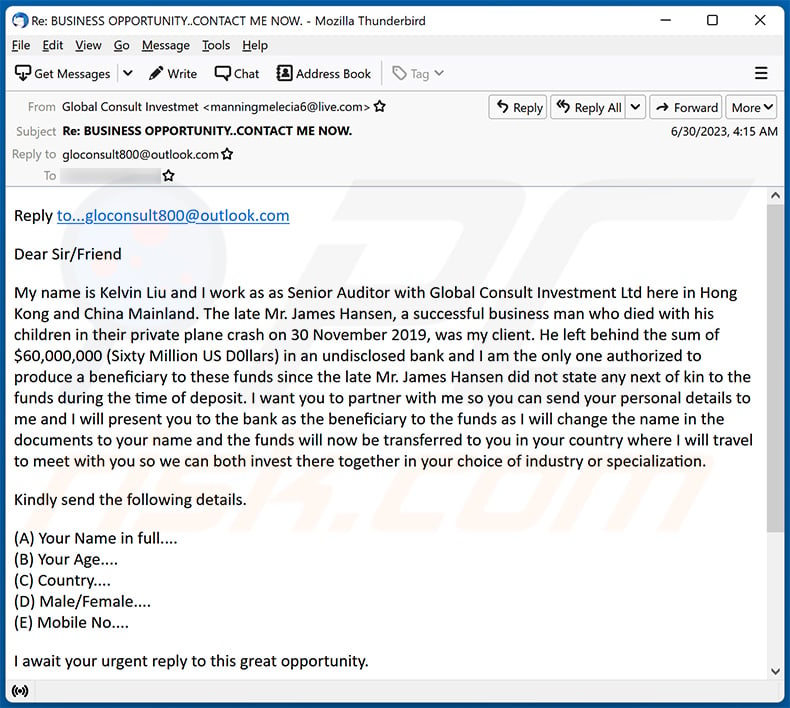
Text presented within:
Subject: Re: BUSINESS OPPORTUNITY..CONTACT ME NOW.
Reply to...gloconsult800@outlook.com
Dear Sir/Friend
My name is Kelvin Liu and I work as as Senior Auditor with Global Consult Investment Ltd here in Hong Kong and China Mainland. The late Mr. James Hansen, a successful business man who died with his children in their private plane crash on 30 November 2019, was my client. He left behind the sum of $60,000,000 (Sixty Million US D0llars) in an undisclosed bank and I am the only one authorized to produce a beneficiary to these funds since the late Mr. James Hansen did not state any next of kin to the funds during the time of deposit. I want you to partner with me so you can send your personal details to me and I will present you to the bank as the beneficiary to the funds as I will change the name in the documents to your name and the funds will now be transferred to you in your country where I will travel to meet with you so we can both invest there together in your choice of industry or specialization.
Kindly send the following details.
(A) Your Name in full....
(B) Your Age....
(C) Country....
(D) Male/Female....
(E) Mobile No....I await your urgent reply to this great opportunity.
Yours Faithfully,
Mr. Kelvin Liu
Senior Auditor
Global Consult Investment Ltd.
Hong Kong & China Mainland
Email: gloconsult800@outlook.com
Another example of inheritance-themed scam email:
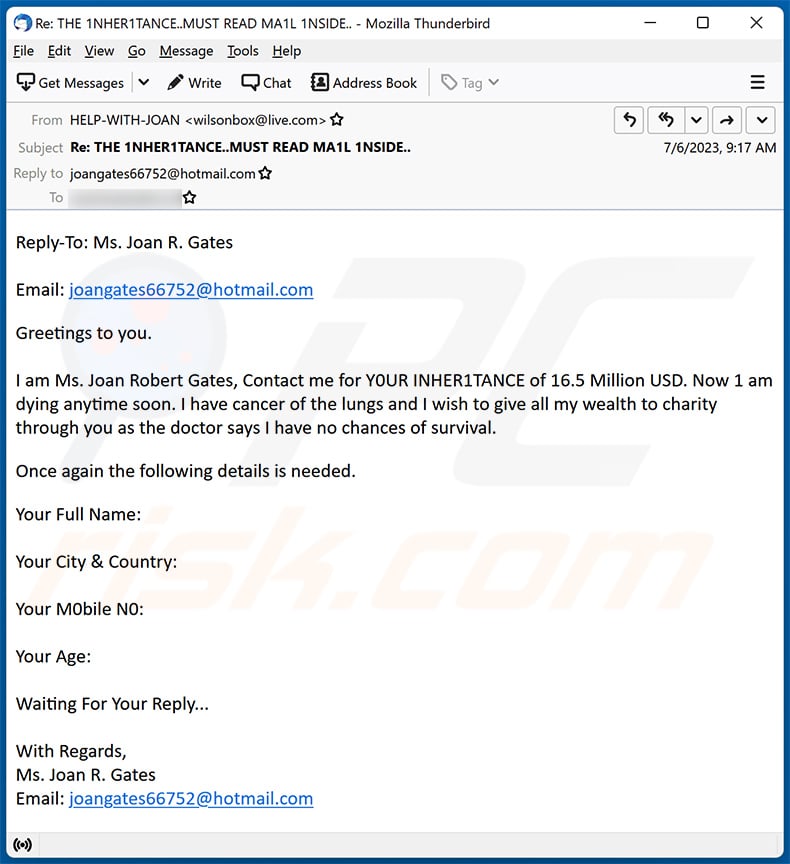
Text presented within:
Subject: Re: THE 1NHER1TANCE..MUST READ MA1L 1NSIDE..
Reply-To: Ms. Joan R. Gates
Email: joangates66752@hotmail.com
Greetings to you.
I am Ms. Joan Robert Gates, Contact me for Y0UR INHER1TANCE of 16.5 Million USD. Now 1 am dying anytime soon. I have cancer of the lungs and I wish to give all my wealth to charity through you as the doctor says I have no chances of survival.Once again the following details is needed.
Your Full Name:
Your City & Country:
Your M0bile N0:
Your Age:
Waiting For Your Reply...
With Regards,
Ms. Joan R. Gates
Email: joangates66752@hotmail.com
Yet another example of an email from "Beneficiary/Inheritance" spam campaign:
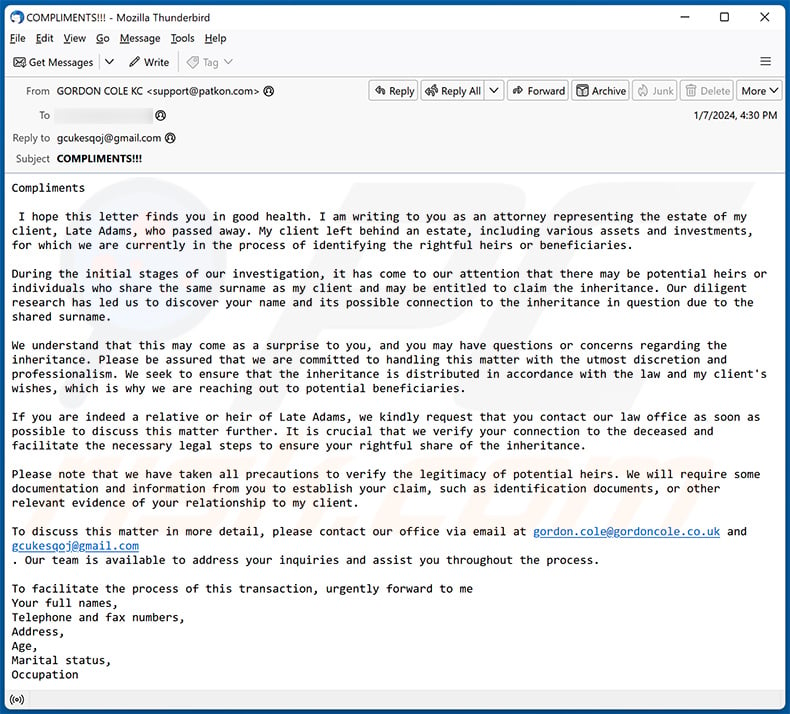
Text presented within:
Subject: COMPLIMENTS!!!
ComplimentsI hope this letter finds you in good health. I am writing to you as an attorney representing the estate of my client, Late Adams, who passed away. My client left behind an estate, including various assets and investments, for which we are currently in the process of identifying the rightful heirs or beneficiaries.
During the initial stages of our investigation, it has come to our attention that there may be potential heirs or individuals who share the same surname as my client and may be entitled to claim the inheritance. Our diligent research has led us to discover your name and its possible connection to the inheritance in question due to the shared surname.
We understand that this may come as a surprise to you, and you may have questions or concerns regarding the inheritance. Please be assured that we are committed to handling this matter with the utmost discretion and professionalism. We seek to ensure that the inheritance is distributed in accordance with the law and my client's wishes, which is why we are reaching out to potential beneficiaries.
If you are indeed a relative or heir of Late Adams, we kindly request that you contact our law office as soon as possible to discuss this matter further. It is crucial that we verify your connection to the deceased and facilitate the necessary legal steps to ensure your rightful share of the inheritance.
Please note that we have taken all precautions to verify the legitimacy of potential heirs. We will require some documentation and information from you to establish your claim, such as identification documents, or other relevant evidence of your relationship to my client.
To discuss this matter in more detail, please contact our office via email at gordon.cole@gordoncole.co.uk and gcukesqoj@gmail.com
. Our team is available to address your inquiries and assist you throughout the process.To facilitate the process of this transaction, urgently forward to me
Your full names,
Telephone and fax numbers,
Address,
Age,
Marital status,
OccupationI will be expecting to hear from you.
Regards
Gordon Cole KC
Thank you for your cooperation, and we look forward to hearing from you soon.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Beneficiary/Inheritance spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
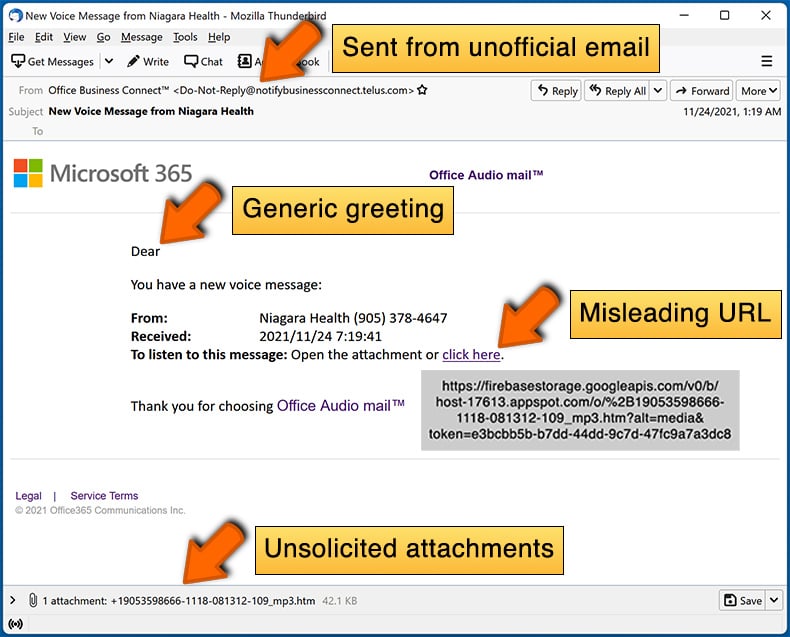
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Frequently Asked Questions (FAQ)
Why did I receive this email?
Most likely, scammers have sent this email to many addresses (all recipients have received the same letter). Most scammers use email addresses leaked after data breaches.
I have provided my personal information when tricked by this email, what should I do?
If you have provided sensitive information such as login credentials (usernames, IDs, passwords, etc.), change your passwords as soon as possible. In case you have provided your credit car details, ID card information, or other details, contact the corresponding authorities.
I have downloaded and opened a malicious file attached to an email, is my computer infected?
It depends on the file type. For example, executable files infect computers right after opening them. PDF, and MS Office documents do not inject malware unless additional steps are performed.
I have sent cryptocurrency to scammers, can I get my money back?
Crypto transactions are virtually untraceable. Therefore, it is very unlikely that you will be able to retrieve your funds.
I have read the email but didn't open the attachment, is my computer infected?
If you only read the email, then your computer is safe.
Will Combo Cleaner remove malware infections that were present in email attachment?
Yes, Combo Cleaner will remove malware from the operating system. It is capable of detecting almost all known malware. Note that high-end malware usually hides deep in the system. In such cases, running a full system scan is required to eliminate malware.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion