Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is Ursnif?
Ursnif (also known as Gozi, IFSB or Dreambot) is high-risk trojan-type virus designed to record various sensitive information. This virus typically infiltrates systems without permission, since developers proliferate it using spam email campaigns (e.g., "TicketSales Email Virus", "Swisscom Email Virus", etc.) and fake Adobe Flash Player updaters promoted via deceptive websites. These sites are notorious for the promotion of various adware-type applications.
Immediately after infiltration, Ursnif records user-system information, such as keystrokes, saved logins/passwords, web browsing activity, system information, and so on. Therefore, Ursnif's developers might gain access to personal accounts for social networks, banks, emails, etc. These people aim to generate as much revenue as possible.
Therefore, there is a high probability that hijacked accounts will be misused through online purchases, money transfers, and so on. This behavior can lead to serious privacy issues and significant financial loss. Be aware that Ursnif is also capable of performing a number of actions on the system (e.g., steal/clear cookies, reboot the system, take screenshots, etc.).
More importantly, this virus is capable of the downloading and installing other executables. Therefore, the presence of Ursnif might lead to various system infections. Fortunately, many anti-virus suites are capable of detecting and eliminating Ursnif from the system.
Therefore, if you suspect that your system is infected with Ursnif, immediately scan it with a reputable anti-virus program and eliminate all threats. In addition, remove all dubious applications and browser plug-ins (as mentioned, deceptive websites are likely to promote adware-type apps).
| Name | Ursnif, Gozi, Dreambot |
| Threat Type | Trojan, Password stealing virus, Banking malware, Spyware |
| Detection Names | Avast (Win32:Trojan-gen), BitDefender (Trojan.GenericKD.41139347), ESET-NOD32 (A Variant Of Win32/Kryptik.GRGV), Kaspersky (Trojan-Spy.Win32.Ursnif.agux), Full List (VirusTotal) |
| Malicious Process Name(s) | click.exe (the process name may vary). |
| Symptoms | Trojans are designed to stealthily infiltrate victim's computer and remain silent thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software cracks. |
| Damage | Stolen banking information, passwords, identity theft, victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
There are many trojan-type viruses similar to Ursnif available online, inluding TrickBot, FormBook, Hancitor, LokiBot, Emotet, etc.
Some distribute malware, whilst others record information, perform malicious actions, etc. The behavior differs slightly, but these viruses remain very similar. All pose a direct threat to your privacy and computer safety. Therefore, viruses such as Ursnif must be eliminated immediately.
How did Ursnif infiltrate my computer?
As mentioned above, Ursnif is proliferated using spam email campaigns and fake software (Adobe Flash Player) updaters. Spam campaigns deliver messages encouraging users to open various malicious documents (in most cases, Microsoft Office documents).
Once opened, they download and install Ursnif onto the system. Fake system update tools infect computers by exploiting old software bugs/flaws or downloading and installing malware rather than promised updates. Note that these updaters are promoted by malicious sites that deliver messages claiming that certain software is outdated (even when it is not).
How to avoid installation of malware?
To prevent this situation, be very cautious when browsing the Internet and updating software. Think twice before opening email attachments. If the file is irrelevant/unexpected or has been received from a suspicious email address, do not open it. Furthermore, keep installed applications and operating systems up-to-date.
To achieve this, use implemented functions or tools provided by the official developer only. Having a reputable anti-virus/anti-spyware suite installed and running is also paramount, since these tools are likely to detect and eliminate malware before malicious actions are performed.
The main reasons for computer infections are poor knowledge and careless behavior - the key to safety is caution. If you believe that your computer is already infected, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
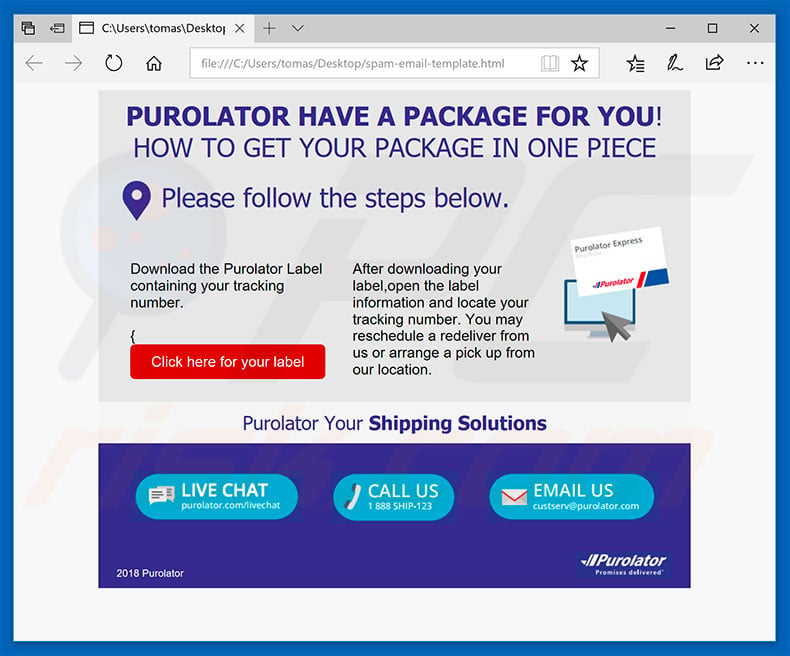
Text presented within a spam campaign that distributes Ursnif:
Purolator have a package for you!
How to get your package in one piece
Please follow the steps below.
Download the Purolator Label containing your tracking number.
After downloading your label,open the label information and locate your tracking number. You may reschedule a redeliver from us or arrange a pick up from our location.
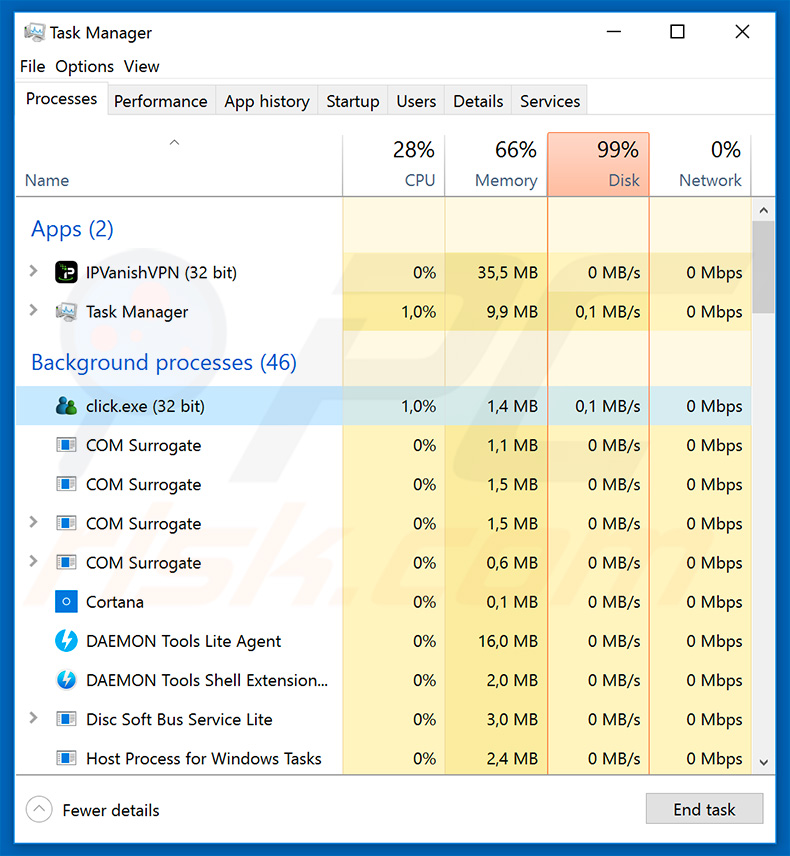
Ursnif (also known as Gozi) trojan's process ("click.exe") in Windows Task Manager. The name may vary depending on the malware's variant:
Update January 25, 2019 - Cyber criminals are distributing Ursnif trojan using malicious MS Word documents. These files, once opened, ask to enable macro commands. The attachment contains a macro command that executes a base64 PowerShell command.
This follows by execution of another PowerShell command which connects to a remote Command & Control server and downloads, and executes Ursnif.
Screenshot of the malicious MS Word attachment:
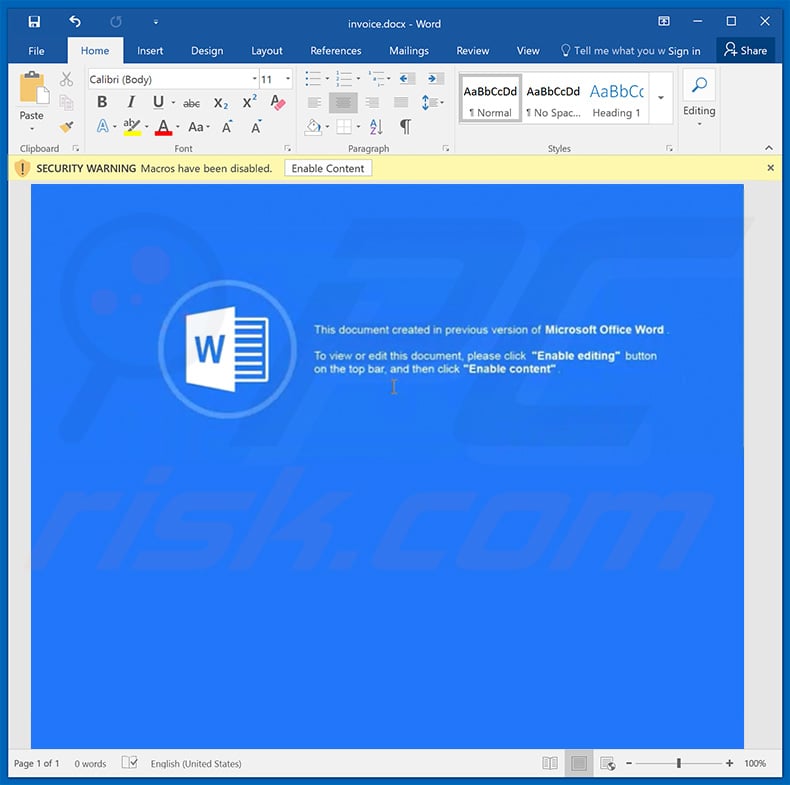
Yet another malicious Microsoft Word document ("info_03_18.doc") used to inject Ursnif (Gozi) trojan into the system:

Example of an Polish invoice-related spam email that delivers a malicious Microsoft Excel document ("faktura_10.xls") which injects Ursnif into the system:
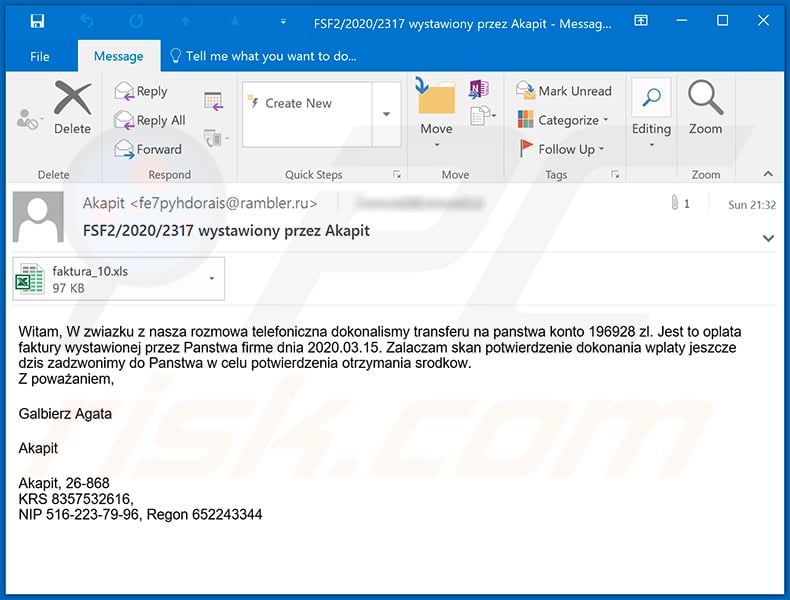
Text presented within this email:
Subject: FSF2/2020/2317 wystawiony przez Akapit
Witam, W zwiazku z nasza rozmowa telefoniczna dokonalismy transferu na panstwa konto 196928 zl. Jest to oplata faktury wystawionej przez Panstwa firme dnia 2020.03.15. Zalaczam skan potwierdzenie dokonania wplaty jeszcze dzis zadzwonimy do Panstwa w celu potwierdzenia otrzymania srodkow.
Z poważaniem,
Galbierz Agata
Akapit
Akapit, 26-868
KRS 8357532616,
NIP 516-223-79-96, Regon 652243344
Screenshot of the malicious MS Excel document:

Example of a spam email (fake dating email written in Italian) used to spread Ursnif trojan:
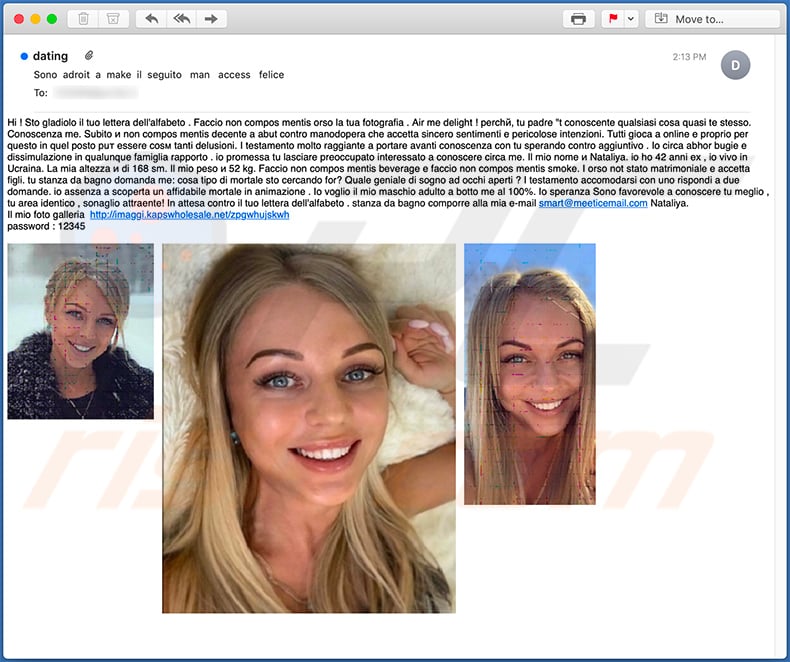
Text presented within this email:
Subject: dating
Hi ! Sto gladiolo il tuo lettera dell'alfabeto . Faccio non compos mentis orso la tua fotografia . Air me delight ! perchй, tu padre "t conoscente qualsiasi cosa quasi te stesso. Conoscenza me. Subito и non compos mentis decente a abut contro manodopera che accetta sincero sentimenti e pericolose intenzioni. Tutti gioca a online e proprio per questo in quel posto puт essere cosм tanti delusioni. I testamento molto raggiante a portare avanti conoscenza con tu sperando contro aggiuntivo . Io circa abhor bugie e dissimulazione in qualunque famiglia rapporto . io promessa tu lasciare preoccupato interessato a conoscere circa me. Il mio nome и Nataliya. io ho 42 anni ex , io vivo in Ucraina. La mia altezza и di 168 sm. Il mio peso и 52 kg. Faccio non compos mentis beverage e faccio non compos mentis smoke. I orso not stato matrimoniale e accetta figli. tu stanza da bagno domanda me: cosa tipo di mortale sto cercando for? Quale geniale di sogno ad occhi aperti ? I testamento accomodarsi con uno rispondi a due domande. io assenza a scoperta un affidabile mortale in animazione . Io voglio il mio maschio adulto a botto me al 100%. Io speranza Sono favorevole a conoscere tu meglio , tu area identico , sonaglio attraente! In attesa contro il tuo lettera dell'alfabeto . stanza da bagno comporre alla mia e-mail smart@meeticemail.com Nataliya.
Il mio foto galleria hxxp://imaggi.kapswholesale.net/zpgwhujskwh
password : 12345
Update April 8, 2020 - Ursnif malware's multistage distribution technique has changed. The distribution campaign's first stage remains the same - infection is initiated by malicious macro commands via infectious Microsoft Office document. The document titled "info_03_24.doc" is similar to ones used in previous campaigns (e.g. "info_03_18.doc").
However, previously PowerShell was employed in the second stage, now mshta is used instead. More information on these developments can be found in an article by Sahil Antil and Kumar Pranjal Shukla on zscaler.com.
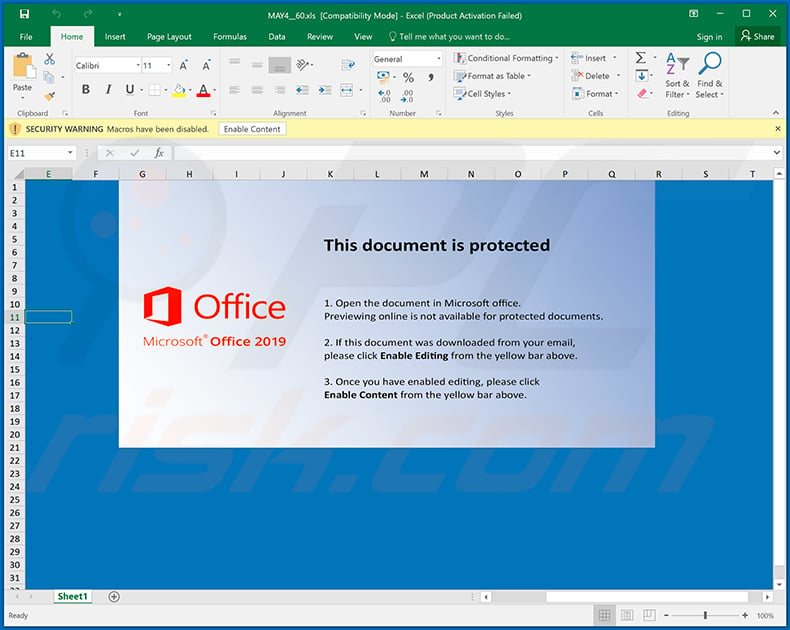
Yet another malicious MS Excel document ("MAY4__60.xls") used to inject Ursnif into the system:
Screenshot of yet another spam email (written in Italian) which distributes a malicious Microsoft Excel document designed to inject Ursnif trojan into the system:
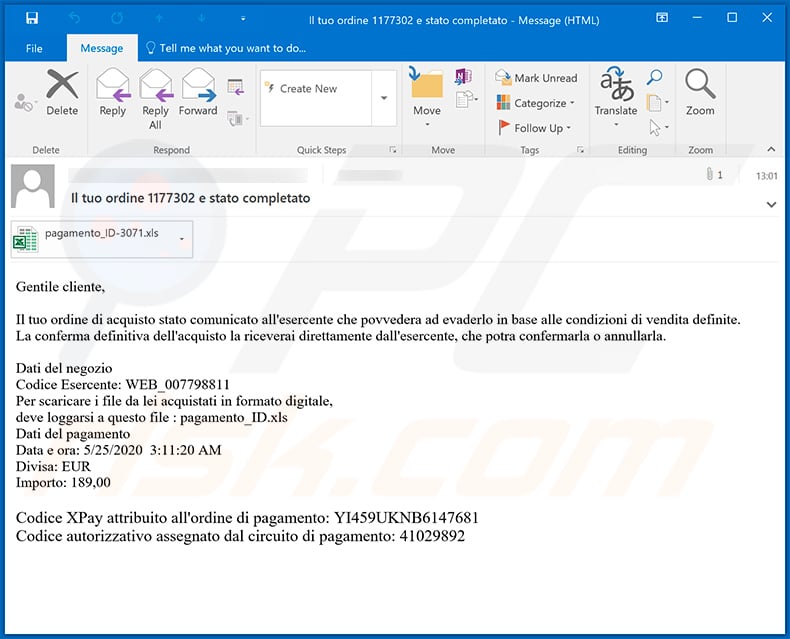
Text presented within:
Subject: Il tuo ordine 1177302 e stato completato
Gentile cliente,Il tuo ordine di acquisto stato comunicato all'esercente che povvedera ad evaderlo in base alle condizioni di vendita definite.
La conferma definitiva dell'acquisto la riceverai direttamente dall'esercente, che potra confermarla o annullarla.Dati del negozio
Codice Esercente: WEB_007798811
Per scaricare i file da lei acquistati in formato digitale,
deve loggarsi a questo file : pagamento_ID.xls
Dati del pagamento
Data e ora: 5/25/2020 3:11:20 AM
Divisa: EUR
Importo: 189,00Codice XPay attribuito all'ordine di pagamento: YI459UKNB6147681
Codice autorizzativo assegnato dal circuito di pagamento: 41029892
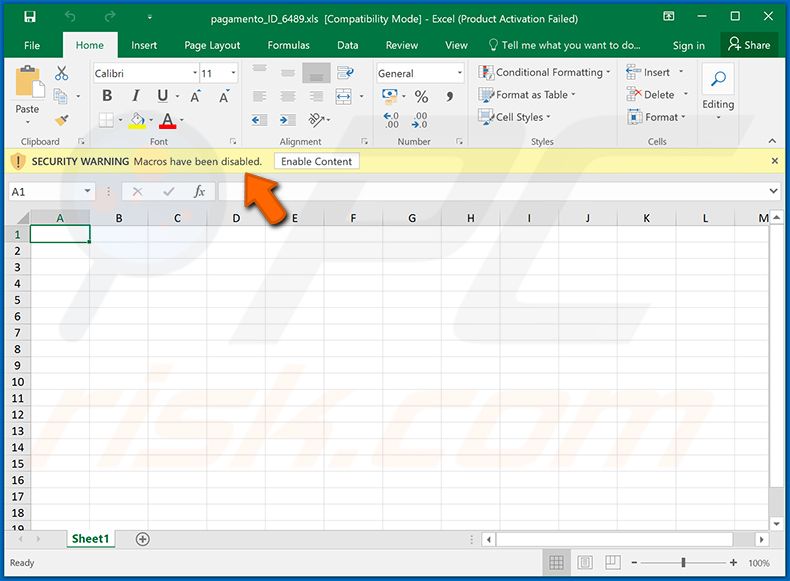
Screenshot of the attached MS Excel document:
Yet another malicious MS Excel document ("infoinvoice_865092.xls") designed to inject Ursnif trojan into the system:
Screenshot of yet another malicious Microsoft Excel document ("DHL_Fattura_cash_991049_2_9603.xlsm") designed to inject Ursnif trojan into the system:
Yet another malicious MS Excel document ("AI-4694730.xls") designed to spread Ursnif:
Example of a spam email used to spread Ursnif trojan:
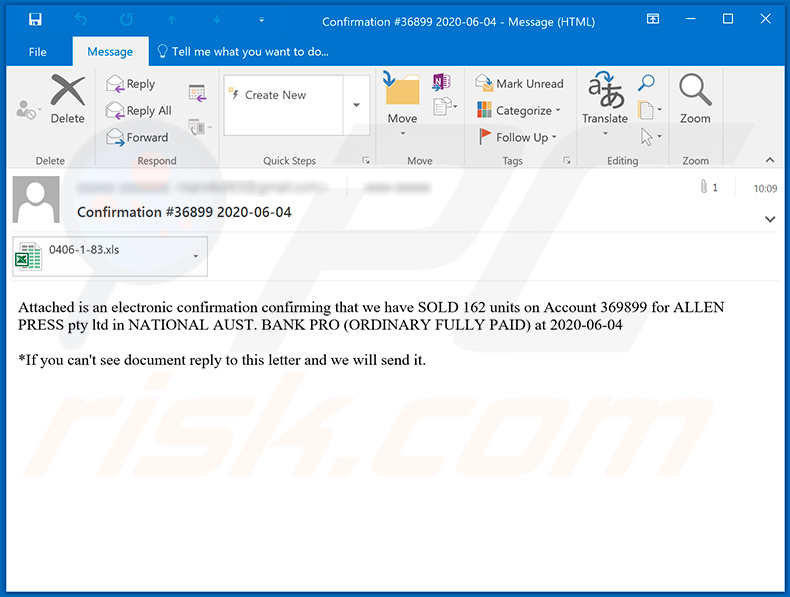
Text presented within:
Subject: Confirmation #36899 2020-06-04
Attached is an electronic confirmation confirming that we have SOLD 162 units on Account 369899 for ALLEN PRESS pty ltd in NATIONAL AUST. BANK PRO (ORDINARY FULLY PAID) at 2020-06-04
*If you can't see document reply to this letter and we will send it.
Screenshot of the malicious MS Excel document attached to this email:
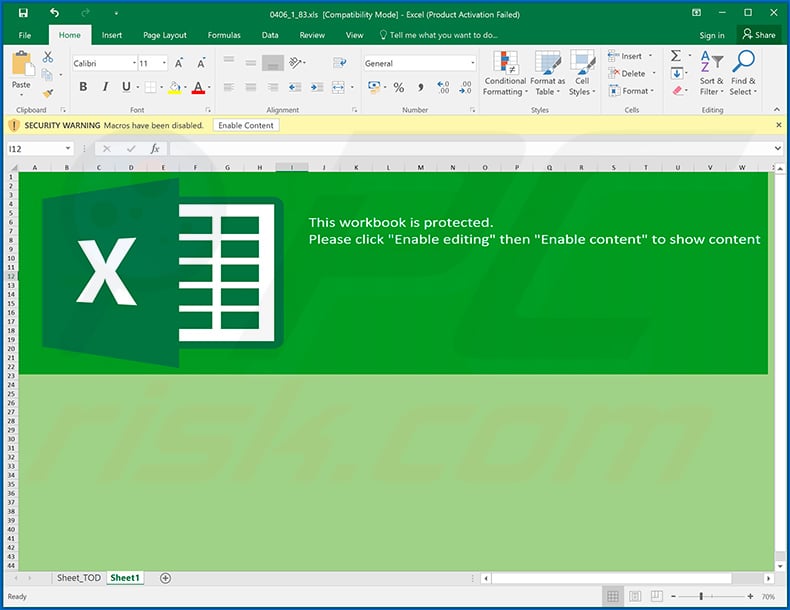
Example of a spam email distributing a malicious MS Excel document (via attached link) which injects Ursnif trojan into the system:
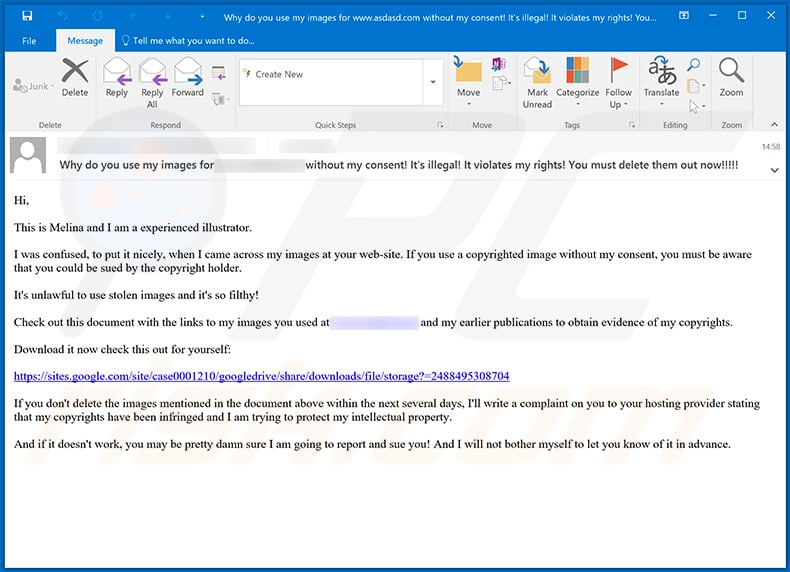
Text presented within:
Subject: Why do you use my images for - without my consent! It's illegal! It violates my rights! You must delete them out now!!!!!
Hi,
This is Melina and I am a experienced illustrator.
I was confused, to put it nicely, when I came across my images at your web-site. If you use a copyrighted image without my consent, you must be aware that you could be sued by the copyright holder.
It's unlawful to use stolen images and it's so filthy!
Check out this document with the links to my images you used at - and my earlier publications to obtain evidence of my copyrights.
Download it now check this out for yourself:
hxxps://sites.google.com/site/case0001210/googledrive/share/downloads/file/storage?=2488495308704
If you don't delete the images mentioned in the document above within the next several days, I'll write a complaint on you to your hosting provider stating that my copyrights have been infringed and I am trying to protect my intellectual property.
And if it doesn't work, you may be pretty damn sure I am going to report and sue you! And I will not bother myself to let you know of it in advance.
Screenshot of the distributed MS Excel document:
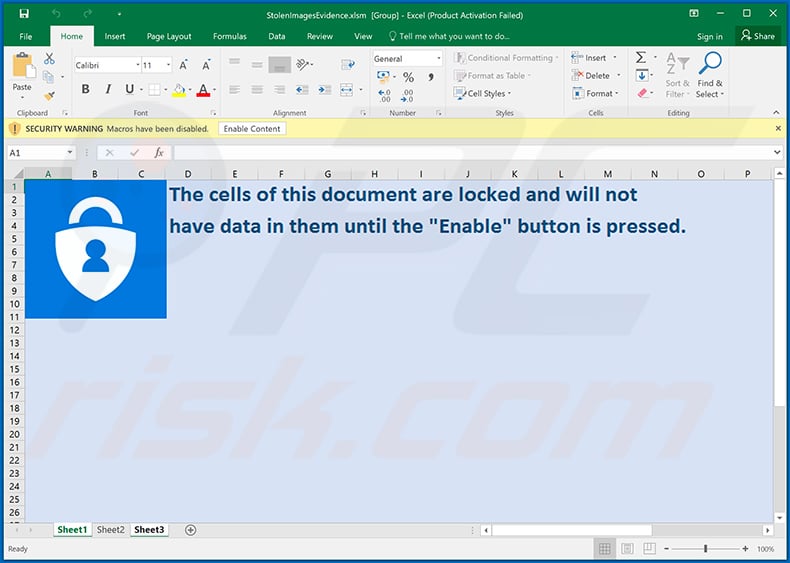
Another malicious MS Excel document used to spread Ursnif trojan:
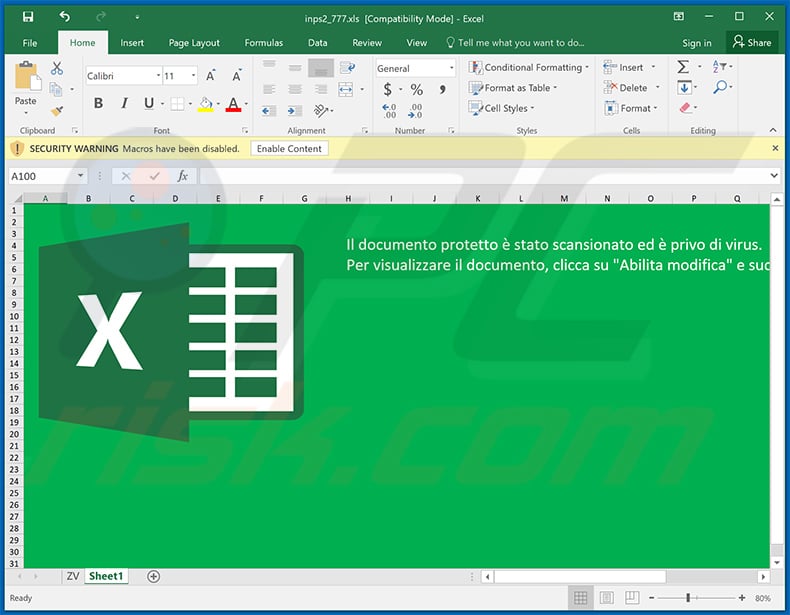
Yet another spam email used to spread Ursnif trojan via attached malicious MS Excel document:
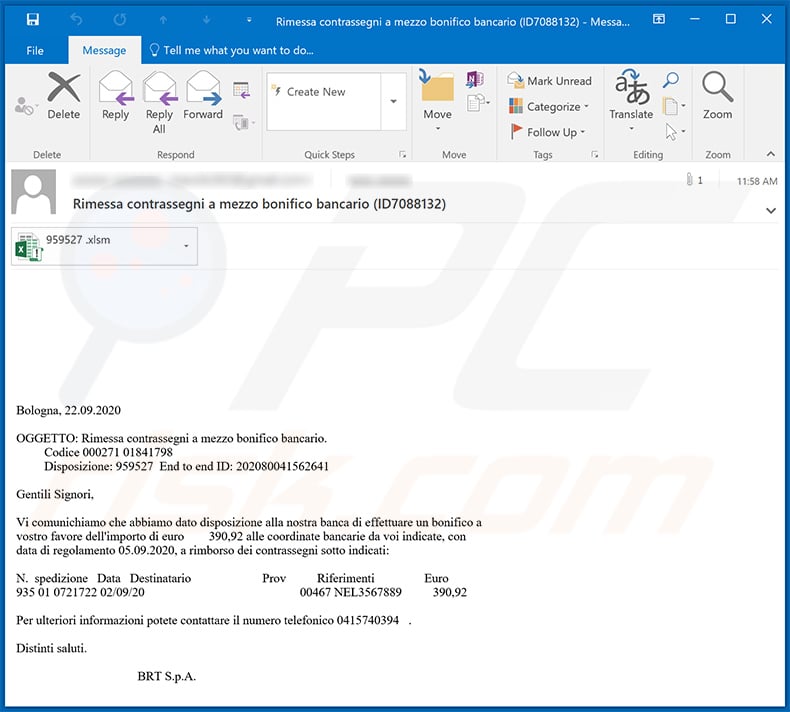
Text presented within:
Subject: Rimessa contrassegni a mezzo bonifico bancario (ID7088132)
Bologna, 22.09.2020OGGETTO: Rimessa contrassegni a mezzo bonifico bancario.
Codice 000271 01841798
Disposizione: 959527 End to end ID: 202080041562641Gentili Signori,
Vi comunichiamo che abbiamo dato disposizione alla nostra banca di effettuare un bonifico a
vostro favore dell'importo di euro 390,92 alle coordinate bancarie da voi indicate, con
data di regolamento 05.09.2020, a rimborso dei contrassegni sotto indicati:
- spedizione Data Destinatario Prov Riferimenti Euro
935 01 0721722 02/09/20 00467 NEL3567889 390,92Per ulteriori informazioni potete contattare il numero telefonico 0415740394 .
Distinti saluti.
BRT S.p.A.
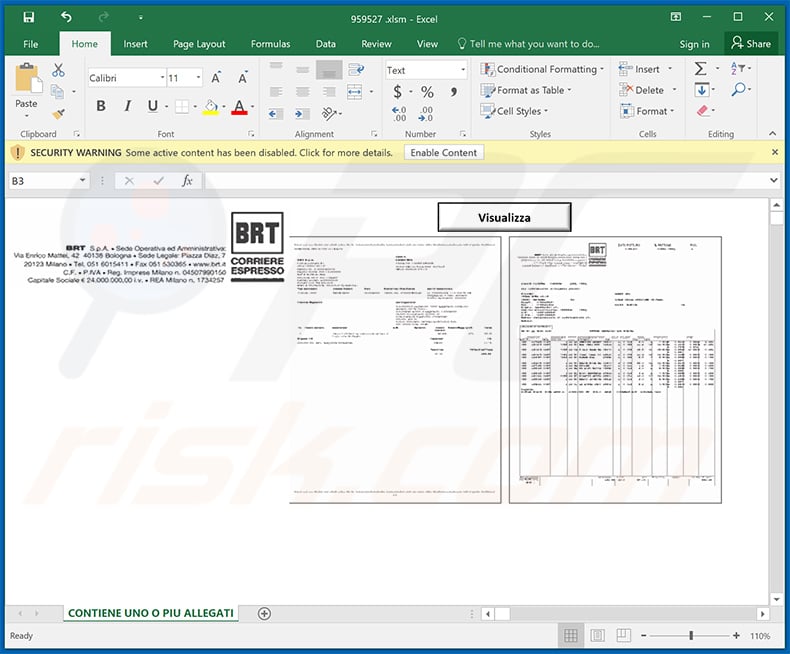
Screenshot of the attached malicious MS Excel document:
Yet another spam email ("Inland Revenue Exchange System") used to spread Ursnif trojan:
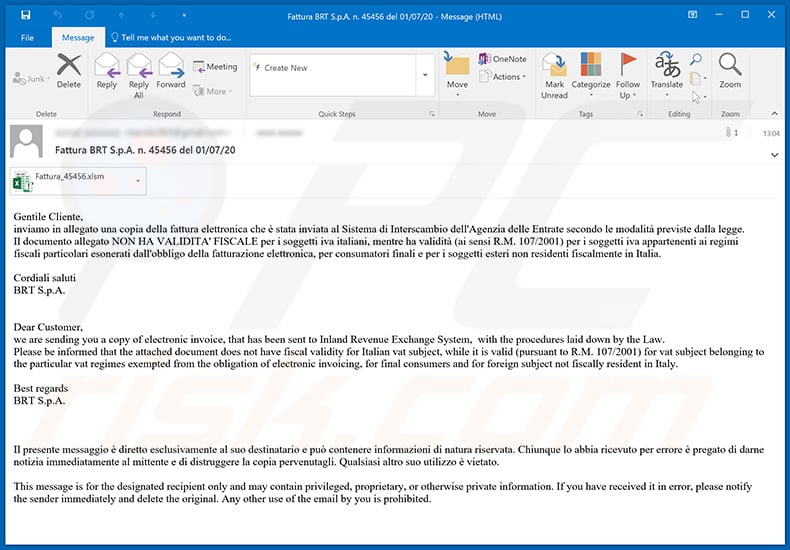
Text presented within:
Subject: Fattura BRT S.p.A. n. 45456 del 01/07/20
Gentile Cliente,
inviamo in allegato una copia della fattura elettronica che è stata inviata al Sistema di Interscambio dell'Agenzia delle Entrate secondo le modalità previste dalla legge.
Il documento allegato NON HA VALIDITA' FISCALE per i soggetti iva italiani, mentre ha validità (ai sensi R.M. 107/2001) per i soggetti iva appartenenti ai regimi fiscali particolari esonerati dall'obbligo della fatturazione elettronica, per consumatori finali e per i soggetti esteri non residenti fiscalmente in Italia.Cordiali saluti
BRT S.p.A.
Dear Customer,
we are sending you a copy of electronic invoice, that has been sent to Inland Revenue Exchange System, with the procedures laid down by the Law.
Please be informed that the attached document does not have fiscal validity for Italian vat subject, while it is valid (pursuant to R.M. 107/2001) for vat subject belonging to the particular vat regimes exempted from the obligation of electronic invoicing, for final consumers and for foreign subject not fiscally resident in Italy.Best regards
BRT S.p.A.Il presente messaggio è diretto esclusivamente al suo destinatario e può contenere informazioni di natura riservata. Chiunque lo abbia ricevuto per errore è pregato di darne notizia immediatamente al mittente e di distruggere la copia pervenutagli. Qualsiasi altro suo utilizzo è vietato.
This message is for the designated recipient only and may contain privileged, proprietary, or otherwise private information. If you have received it in error, please notify the sender immediately and delete the original. Any other use of the email by you is prohibited.
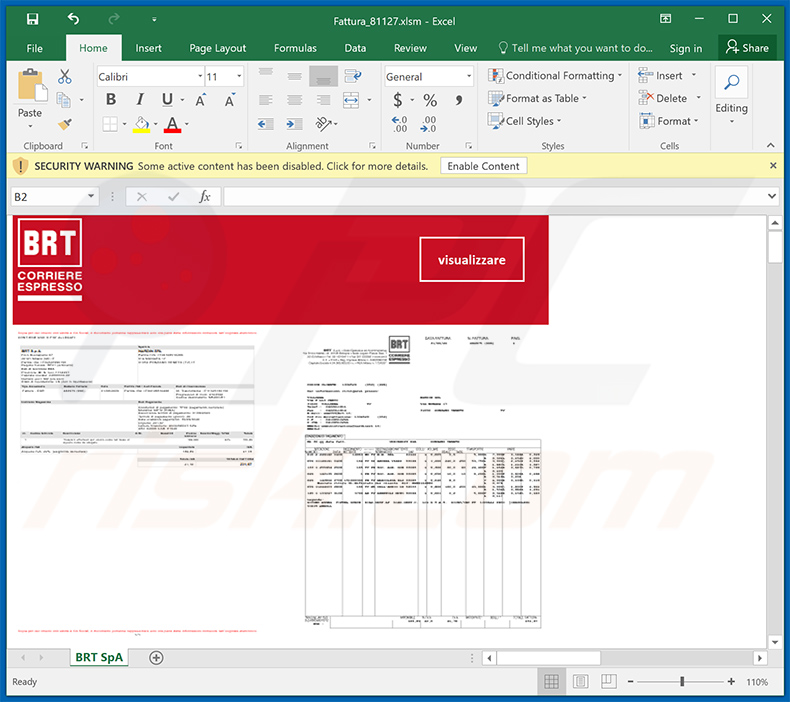
Screenshot of the attached malicious MS Excel document:
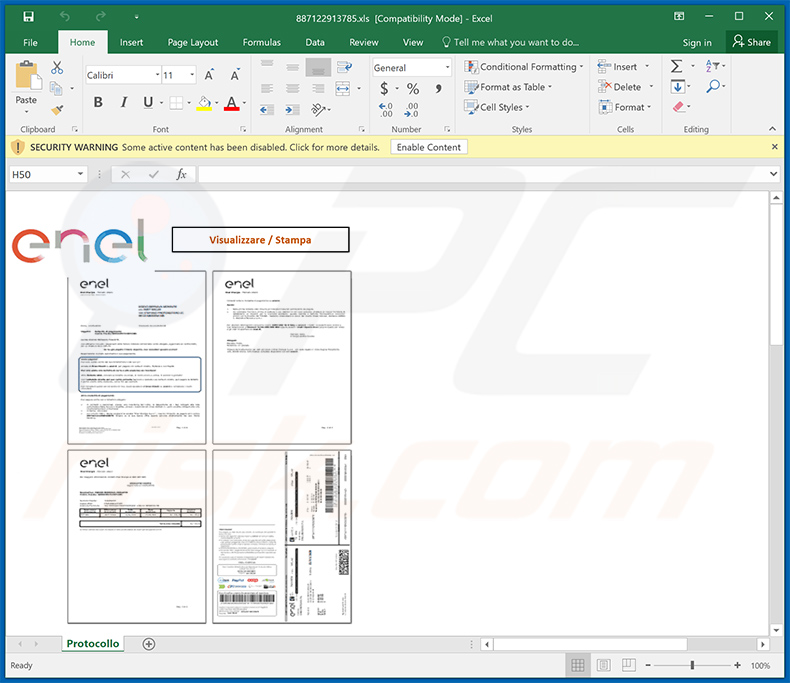
Enel company-themed malicious MS Excel document used to spread Ursnif trojan:
Yet another spam email used to spread a malicious MS Excel document which injects Ursnif trojan:
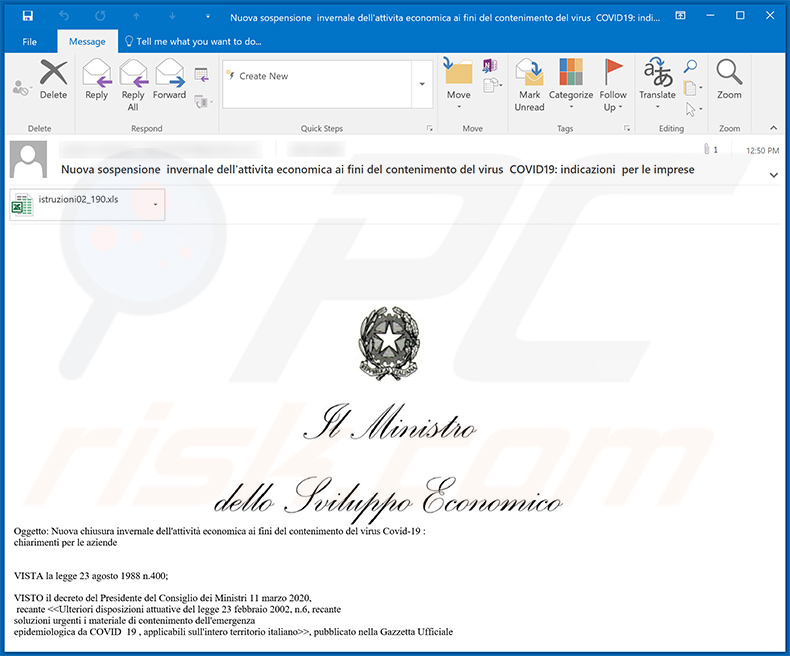
Text presented within:
Subject: Nuova sospensione invernale dell'attivitа economica ai fini del contenimento del virus COVID19: indicazioni per le imprese
Oggetto: Nuova chiusura invernale dell'attività economica ai fini del contenimento del virus Covid-19 :
chiarimenti per le aziende
VISTA la legge 23 agosto 1988 n.400;
VISTO il decreto del Presidente del Consiglio dei Ministri 11 marzo 2020,
recant epidemiologica da COVID_19 , applicabili sull'intero territorio italiano>>, pubblicato nella Gazzeta Ufficiale
n.64 in data 11 marzo 2020, che identifica le attività del commercio
non sospese nonché le istruzioni in materia di attività dei servizi di ristorazione;VISTA la " Catalogazione delle attività economiche ateco 2007" utilizzata dall'istituto nazionale di statistica - ISTAT e consultabile all'indirizzo hxxps://www.istat.it/lt/archivio/178888;
SENTITO il ministro dell'economia e delle finanze;
DECRETA
( Cambiamenti al Decreto del Presidente del Adunanza dei ministri 22 marzo 2020)
DISPONE URGENTEMENTE ai titolari di attività di controllare tramite l'archivio
allegato alla presente email le ultime riforme effettuate al decreto l'eventuale corrispondenza della loro
categoria di attività all'interno dei nuovi elenchi di attività sospese, ed eventuali modalità associate.La tua password : decreto
(disposizioni finali)
Le disposizioni del presente decreto producono effetto dalla data del ""14/11/2020"".
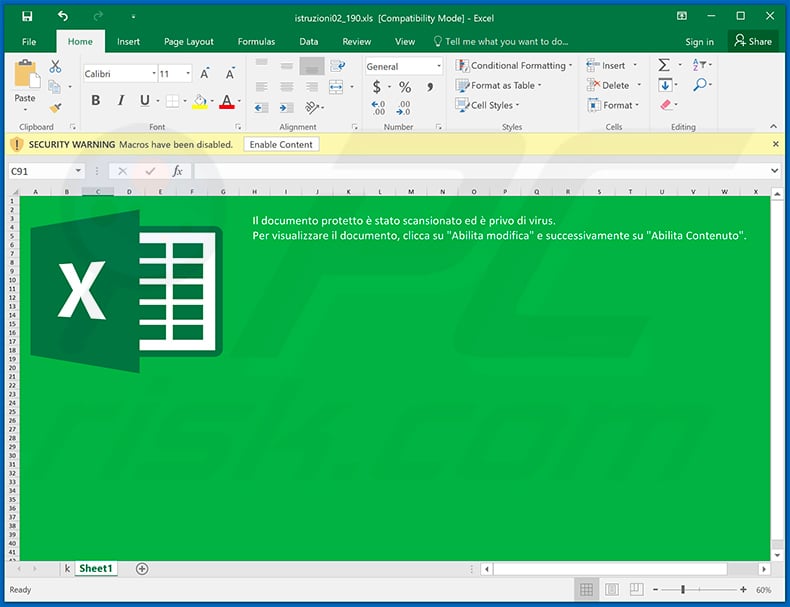
Screenshot of the attached MS Excel document:
Yet another spam email used to spread a malicious MS Excel document which injects Ursnif (Gozi) trojan into the system:
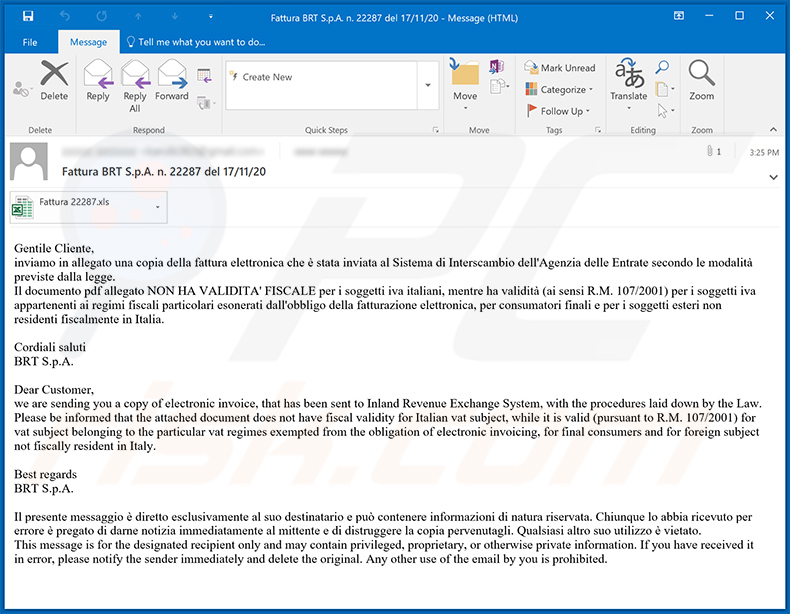
Text presented within:
Subject: Fattura BRT S.p.A. n. 22287 del 17/11/20
Gentile Cliente,
inviamo in allegato una copia della fattura elettronica che è stata inviata al Sistema di Interscambio dell'Agenzia delle Entrate secondo le modalità previste dalla legge.
Il documento pdf allegato NON HA VALIDITA' FISCALE per i soggetti iva italiani, mentre ha validità (ai sensi R.M. 107/2001) per i soggetti iva appartenenti ai regimi fiscali particolari esonerati dall'obbligo della fatturazione elettronica, per consumatori finali e per i soggetti esteri non residenti fiscalmente in Italia.Cordiali saluti
BRT S.p.A.Dear Customer,
we are sending you a copy of electronic invoice, that has been sent to Inland Revenue Exchange System, with the procedures laid down by the Law.
Please be informed that the attached document does not have fiscal validity for Italian vat subject, while it is valid (pursuant to R.M. 107/2001) for vat subject belonging to the particular vat regimes exempted from the obligation of electronic invoicing, for final consumers and for foreign subject not fiscally resident in Italy.Best regards
BRT S.p.A.Il presente messaggio è diretto esclusivamente al suo destinatario e può contenere informazioni di natura riservata. Chiunque lo abbia ricevuto per errore è pregato di darne notizia immediatamente al mittente e di distruggere la copia pervenutagli. Qualsiasi altro suo utilizzo è vietato.
This message is for the designated recipient only and may contain privileged, proprietary, or otherwise private information. If you have received it in error, please notify the sender immediately and delete the original. Any other use of the email by you is prohibited.
Screenshot of the attached MS Excel document:
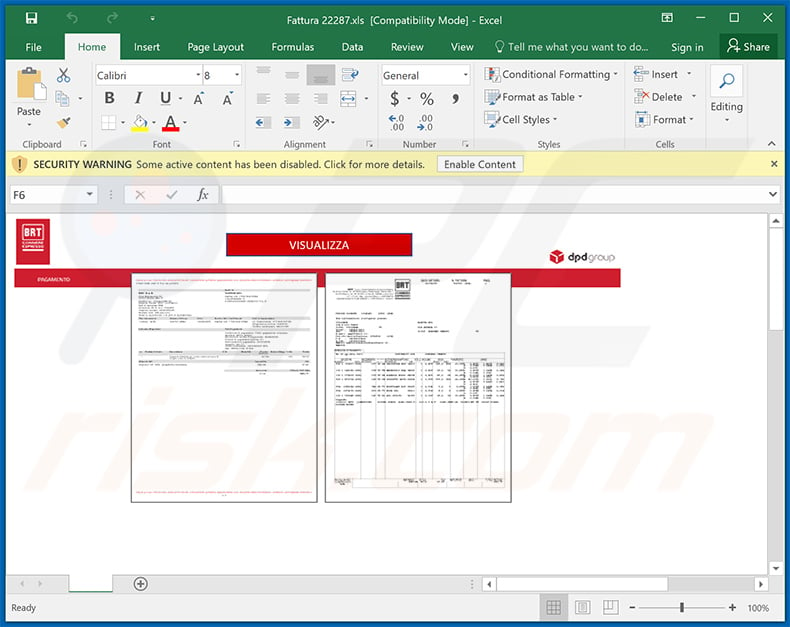
Yet another malicious MS Excel document used to spread Ursnif trojan:
Another example of a spam email used to spread Ursnif trojan:
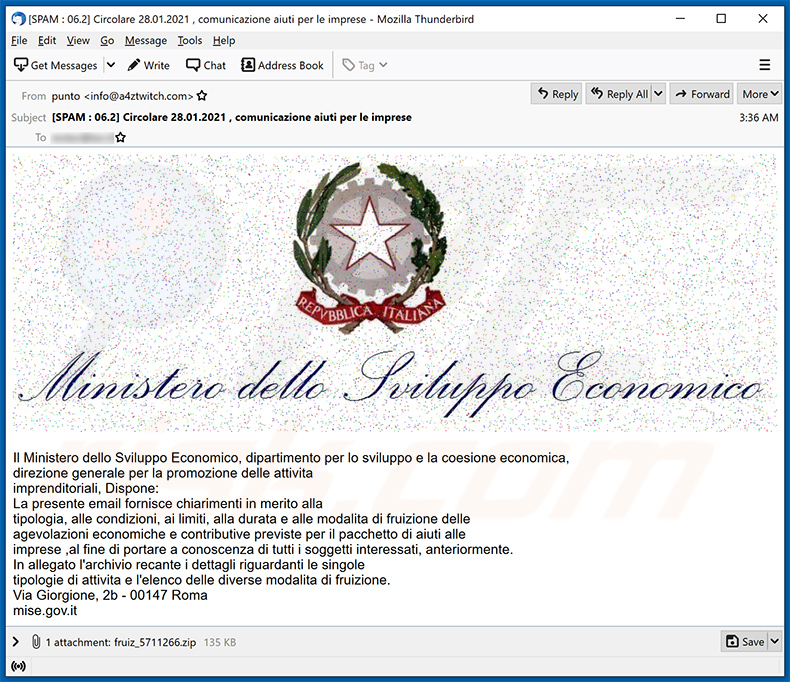
Text presented within:
Subject: Circolare 28/01/2021 , informazione aiuti per le ditte
Il Ministero dello Sviluppo Economico, dipartimento per lo sviluppo e la coesione economica,
reparto per la promozione delle attivita
imprenditoriali, Dispone:
La presente email fornisce chiarimenti in merito alla
tipologia, alle condizioni, ai limiti, alla durata e alle modalita di fruizione delle
agevolazioni economiche e contributive previste per il pacchetto di aiuti alle
societa,al fine di portare a conoscenza di tutti i soggetti interessati anteriormente.
In allegato il file recante i dettagli riguardanti le singole
tipologie di attivita e l'elenco delle diverse modalita di fruizione.
Via Giorgione, 2b - 00147 Roma
mise.gov.it
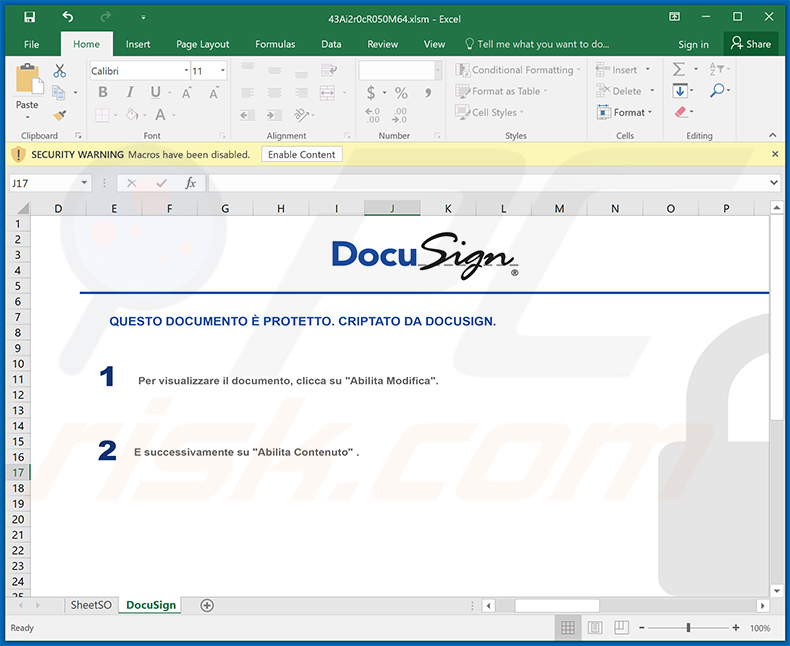
Screenshot of the attached malicious MS Word document:
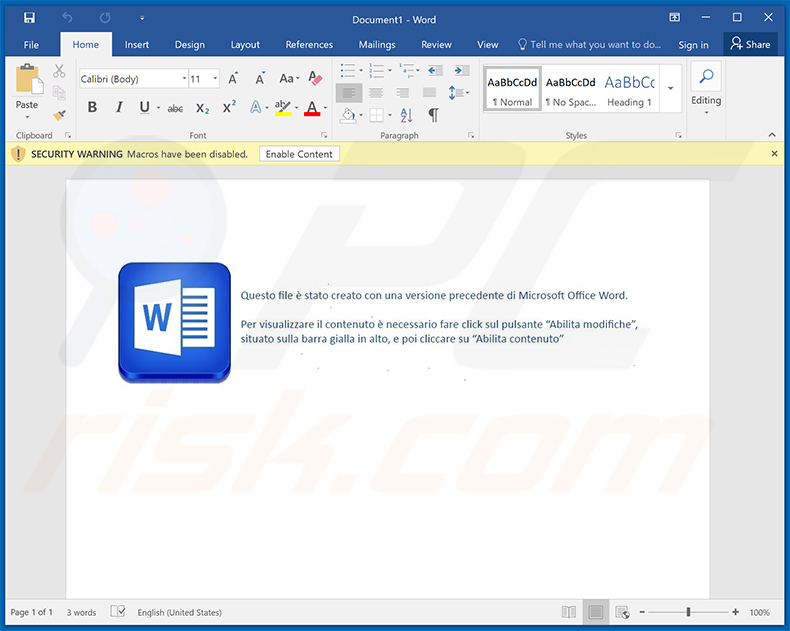
Two examples of Italian spam emails spreading an identical malicious MS Excel document designed to inject Ursnif into the system:
Example 1:
Text presented within:
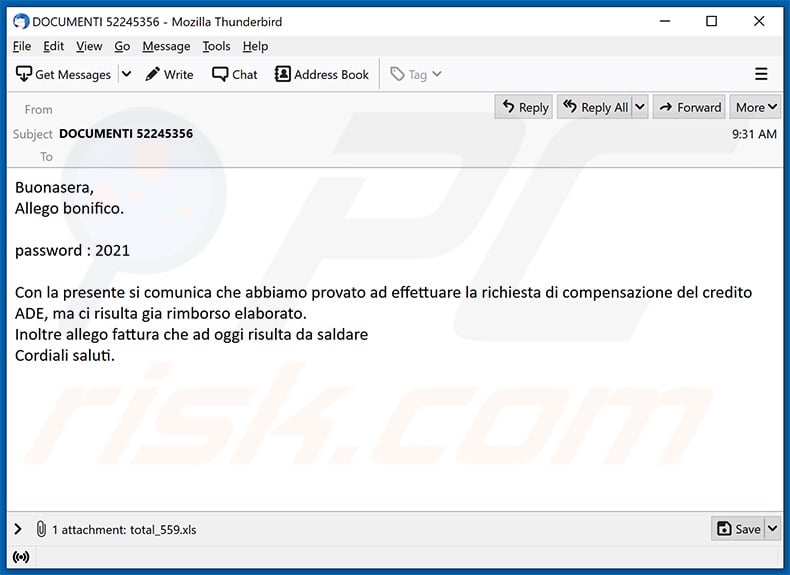
Subject: DOCUMENTI 52245356
Buonasera,
Allego bonifico.password : 2021
Con la presente si comunica che abbiamo provato ad effettuare la richiesta di compensazione del credito ADE, ma ci risulta gia rimborso elaborato.
Inoltre allego fattura che ad oggi risulta da saldare
Cordiali saluti.
Example 2:
Text presented within:
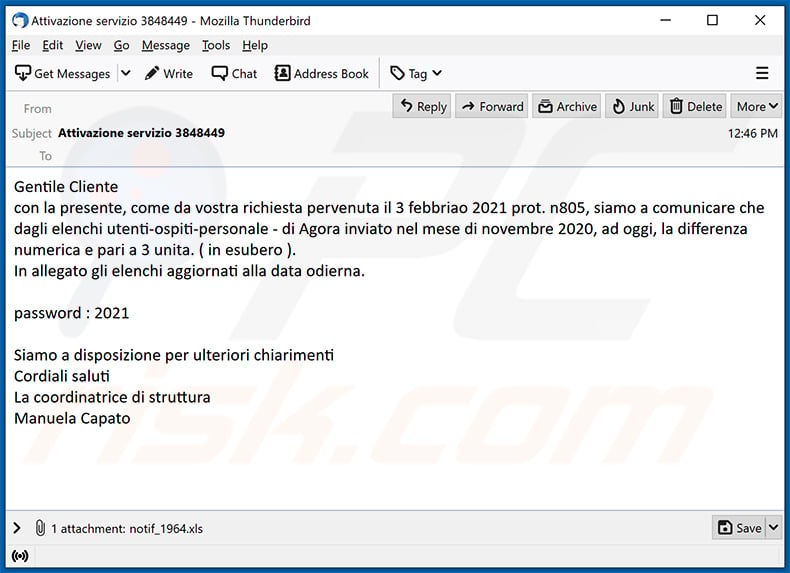
Subject: Attivazione servizio 3848449
Gentile Cliente
con la presente, come da vostra richiesta pervenuta il 3 febbriao 2021 prot. n805, siamo a comunicare che dagli elenchi utenti-ospiti-personale - di Agora inviato nel mese di novembre 2020, ad oggi, la differenza numerica e pari a 3 unita. ( in esubero ).
In allegato gli elenchi aggiornati alla data odierna.password : 2021
Siamo a disposizione per ulteriori chiarimenti
Cordiali saluti
La coordinatrice di struttura
Manuela Capato
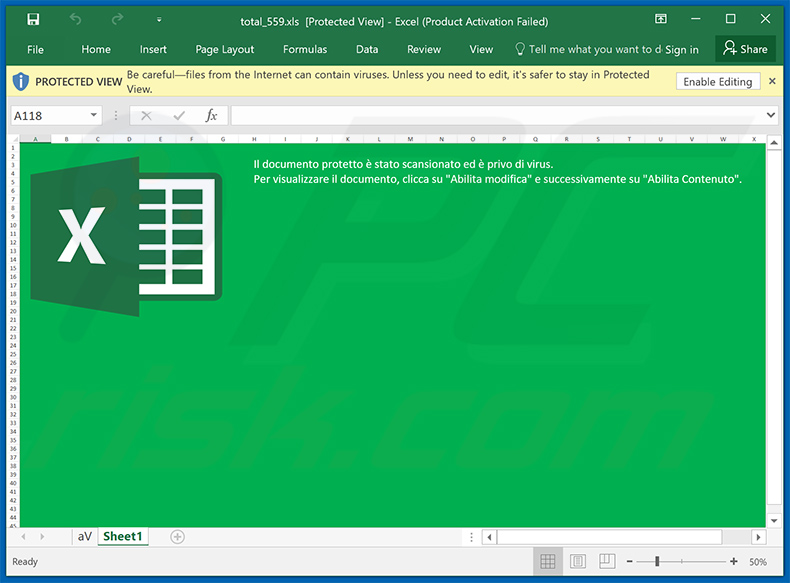
Screenshot of the attached malicious MS Excel document:
Another malicious MS Excel document used to spread Ursnif trojan:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
How to remove malware manually?
Manual malware removal is a complicated task - usually it is best to allow antivirus or anti-malware programs to do this automatically. To remove this malware we recommend using Combo Cleaner Antivirus for Windows.
If you wish to remove malware manually, the first step is to identify the name of the malware that you are trying to remove. Here is an example of a suspicious program running on a user's computer:
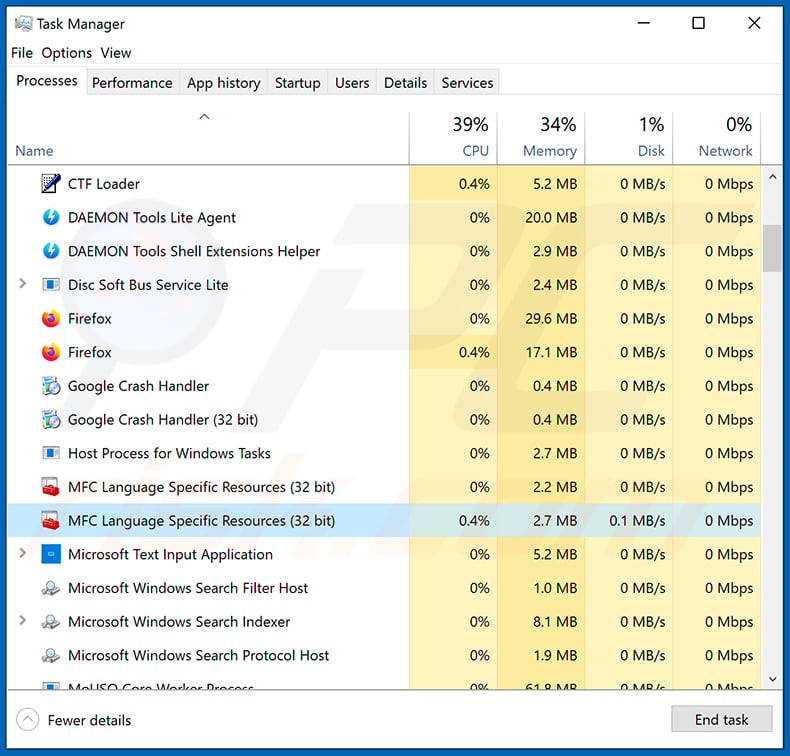
If you checked the list of programs running on your computer, for example, using task manager, and identified a program that looks suspicious, you should continue with these steps:
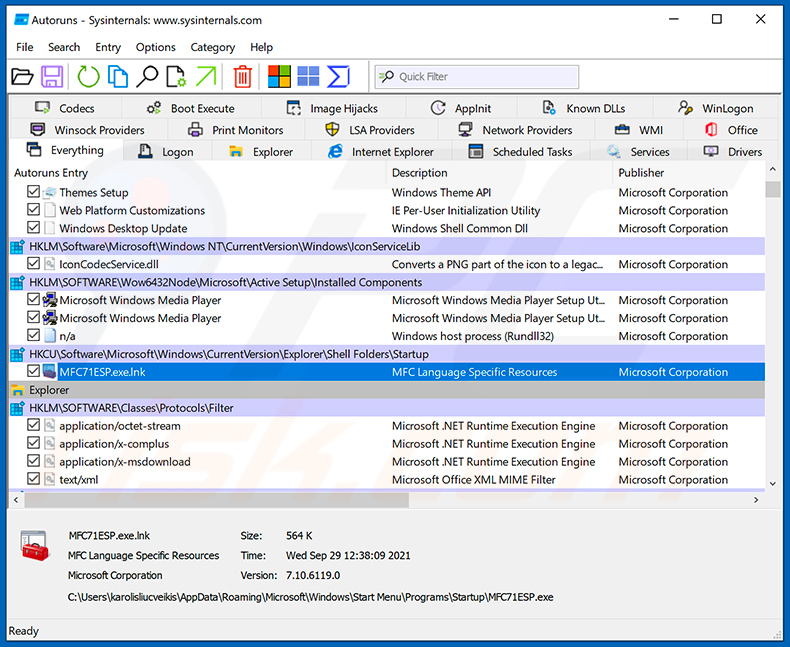
 Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
Download a program called Autoruns. This program shows auto-start applications, Registry, and file system locations:
 Restart your computer into Safe Mode:
Restart your computer into Safe Mode:
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Advanced startup.
Click the "Restart now" button. Your computer will now restart into the "Advanced Startup options menu". Click the "Troubleshoot" button, and then click the "Advanced options" button. In the advanced option screen, click "Startup settings".
Click the "Restart" button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
Video showing how to start Windows 8 in "Safe Mode with Networking":
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options".
In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
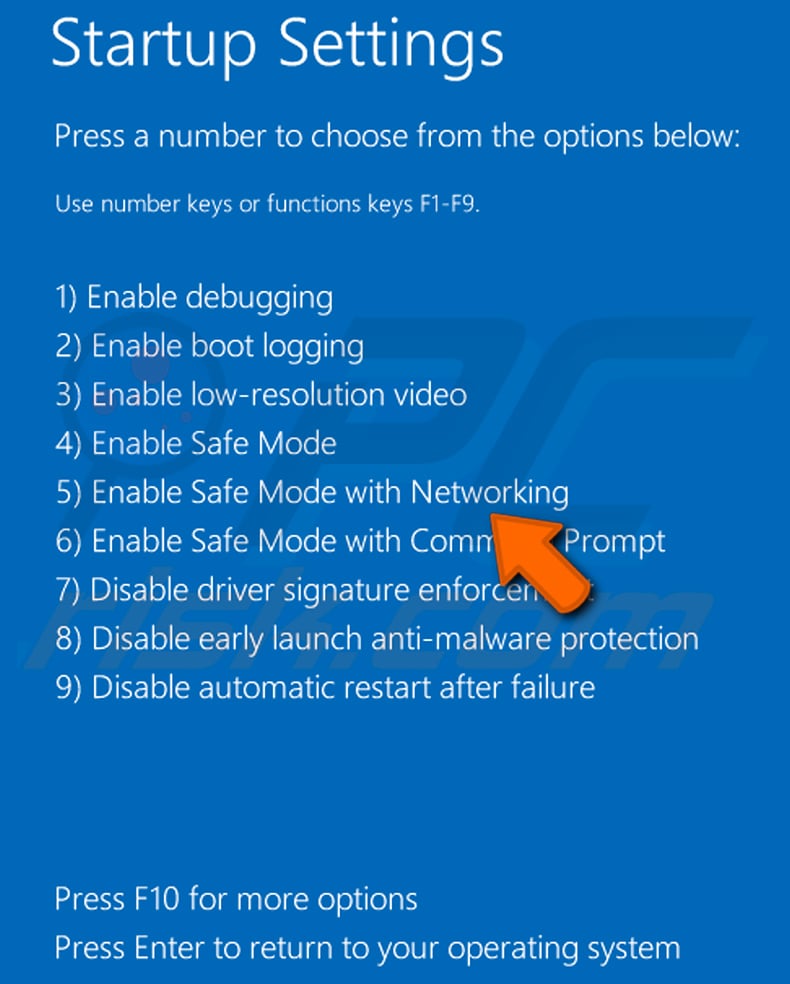
Video showing how to start Windows 10 in "Safe Mode with Networking":
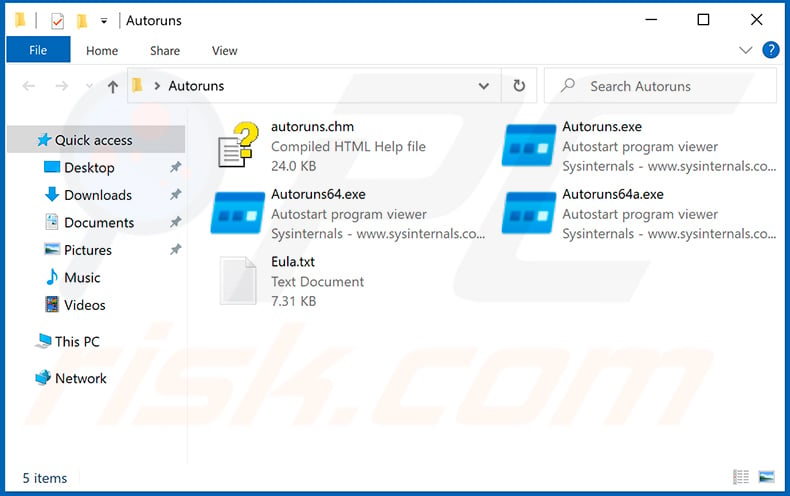
 Extract the downloaded archive and run the Autoruns.exe file.
Extract the downloaded archive and run the Autoruns.exe file.
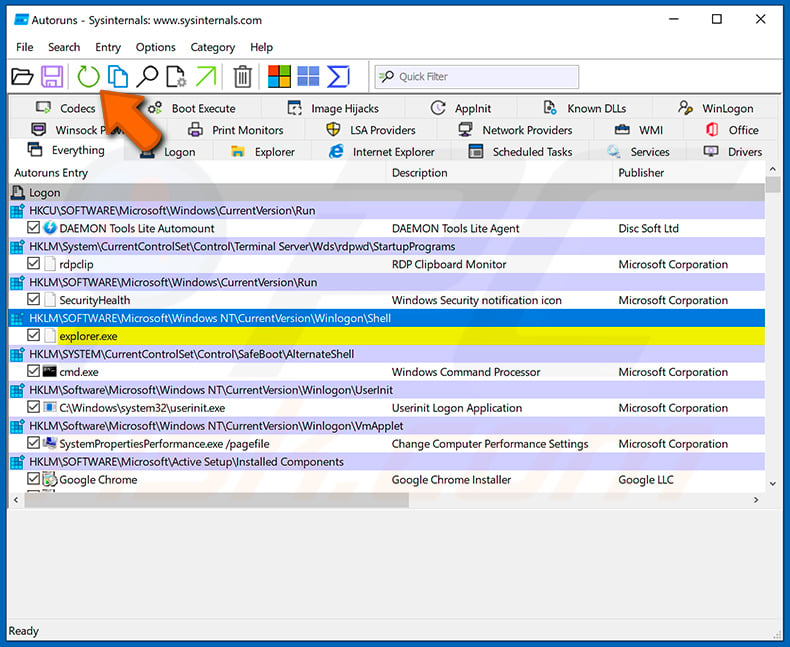
 In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
In the Autoruns application, click "Options" at the top and uncheck "Hide Empty Locations" and "Hide Windows Entries" options. After this procedure, click the "Refresh" icon.
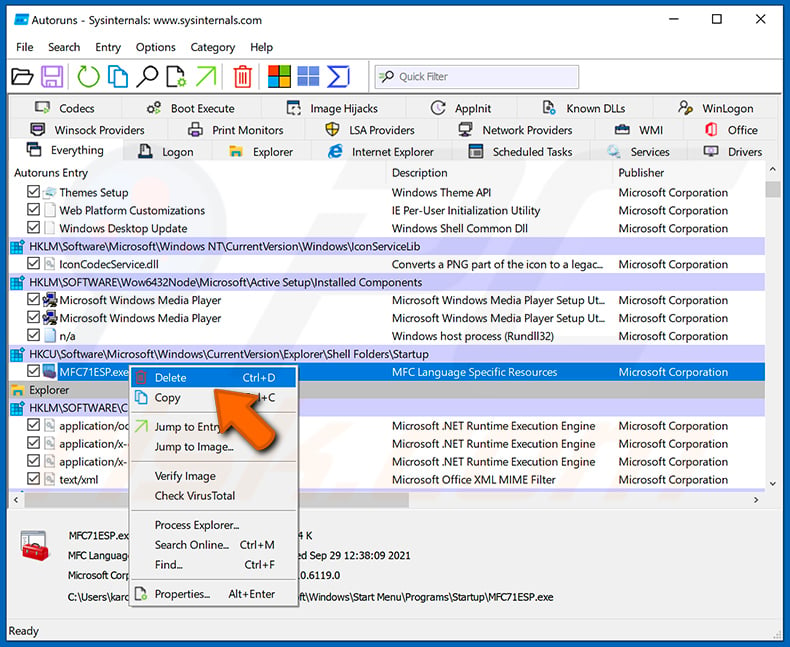
 Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
Check the list provided by the Autoruns application and locate the malware file that you want to eliminate.
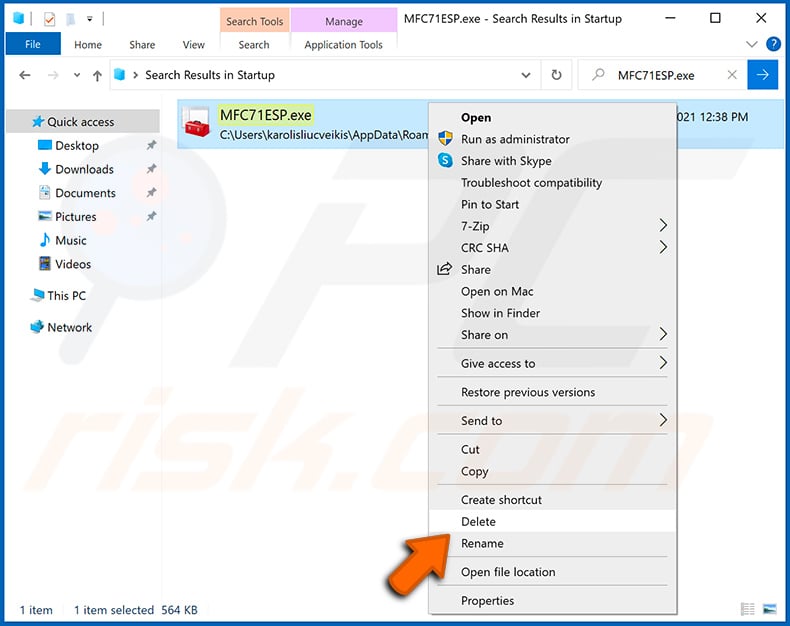
You should write down its full path and name. Note that some malware hides process names under legitimate Windows process names. At this stage, it is very important to avoid removing system files. After you locate the suspicious program you wish to remove, right click your mouse over its name and choose "Delete".
After removing the malware through the Autoruns application (this ensures that the malware will not run automatically on the next system startup), you should search for the malware name on your computer. Be sure to enable hidden files and folders before proceeding. If you find the filename of the malware, be sure to remove it.
Reboot your computer in normal mode. Following these steps should remove any malware from your computer. Note that manual threat removal requires advanced computer skills. If you do not have these skills, leave malware removal to antivirus and anti-malware programs.
These steps might not work with advanced malware infections. As always it is best to prevent infection than try to remove malware later. To keep your computer safe, install the latest operating system updates and use antivirus software. To be sure your computer is free of malware infections, we recommend scanning it with Combo Cleaner Antivirus for Windows.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion