Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is Enel email virus?
Enel is an Italian manufacturer and distributor of electricity and gas. There are multiple variants of phishing and malspam emails that are currently circulating and claiming to be from this company. Cyber criminals behind these emails attempt to trick recipients into providing sensitive information or installing malicious software called Ursnif.

These email messages claim to be notifications about an unfinished refund or unpaid bill. Their purpose is to steal personal data and details relating to credit and debit cards, or to deliver malware (a banking Trojan called Ursnif). There are at least two variants of these malspam emails and one phishing email.
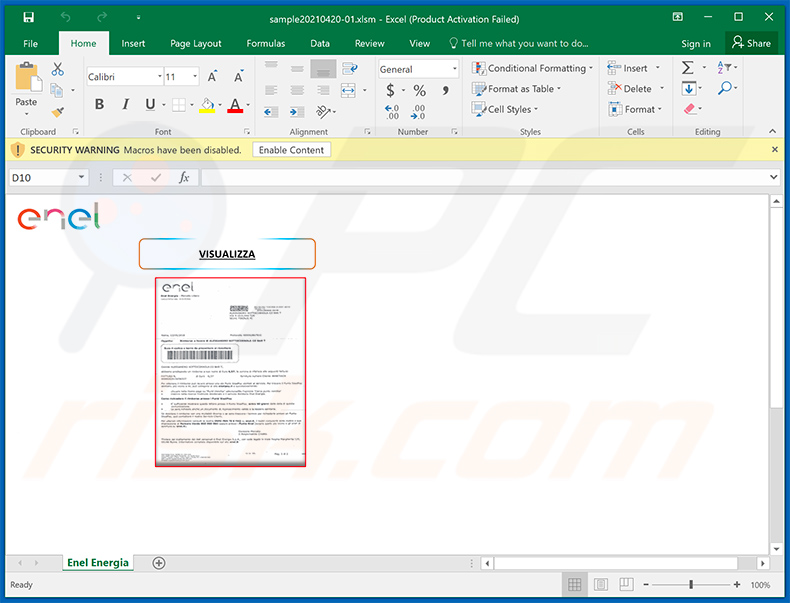
In the malspam emails, recipients are asked to check the attached document (supposedly an unfinished refund or unpaid bill). In both malspam variants, the attached file is a malicious Microsoft Excel document that, if opened and allowed to enable macros (Editing/Content), installs Ursnif onto the operating system.
The phishing email contains a website link designed to open a fake Enel website whereby users/visitors are asked to log in using their email addresses and passwords. Screenshots of the emails (and text within them) are provided below. The fake Enel website (login page) is used to steal login credentials.
Typically, cyber criminals attempt to steal this information to hijack accounts and then use them for malicious purposes. Depending on the type of a stolen account, criminals can use it to steal identities, send malspam, phishing emails, make fraudulent transactions, purchases, trick other people into making monetary transactions, access personal files or other data, and so on.
Stolen credentials can also be monetized by selling them to third parties (other cyber criminals).
The Ursnif Trojan is used to collect various sensitive information. The Trojan logs keystrokes (records keyboard input), gathers saved login credentials, web browsing activity, system information, and cookies. It can also restart the operating system, capture screen/take screenshots, and download and execute files.
Essentially, cyber criminals use this malware to steal sensitive information and distribute (install) other malicious software (e.g., ransomware, cryptocurrency miners).
| Name | Enel spam |
| Threat Type | Trojan, password-stealing virus, banking malware, spyware. |
| Hoax | Letter from Enel regarding unfinished refund and unpaid bill |
| Attachment(s) | Malicious MS Excel document |
| Detection Names (Ursnif in first phishing email) | Avast (Other:Malware-gen [Trj]), BitDefender (Trojan.Agent.FAPD), ESET-NOD32 (VBA/TrojanDownloader.Agent.VEK), Kaspersky (HEUR:Trojan.MSOffice.Agent.gen), Microsoft (TrojanDownloader:O97M/Dridex!MTB), Full List Of Detections (VirusTotal) |
| Detection Names (Ursnif in first phishing email) | ALYac (Trojan.Downloader.XLS.Gen), BitDefender (Trojan.GenericKD.45560735), ESET-NOD32 (VBA/TrojanDownloader.Agent.VJD), Kaspersky (HEUR:Trojan.Script.Generic), Microsoft (TrojanDownloader:O97M/Obfuse.VIS!MTB), Full List Of Detections (VirusTotal) |
| Symptoms | Trojans are designed to stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Payload | Ursnif |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software 'cracks'. |
| Damage | Stolen passwords and banking information, identity theft, the victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
More examples of phishing and malspam campaigns are "Email Disabling Service Email Scam", "Credito Agricola Email Scam", "METZA Email Virus" and "Cobra Industrial Machines Email Virus".
In most cases, recipients who fall for phishing, malspam emails infect their computers with malware, suffer monetary loss, lose access to personal accounts, have their identities stolen, or encounter other serious issues. Therefore, you are strongly advised to analyze suspicious emails (research carefully) before opening links to files within them.
Note that, in most cases, phishing and malspam messages claim to be from legitimate companies, organizations, or other entities.
How did "Enel email virus" infect my computer?
Malicious Microsoft Excel documents within these malspam emails install Ursnif after being opened and allowed to enable malicious macros (Editing/Content).
Note that malicious MS Office documents can install malware only when users enable editing/content (macros commands). If the documents are opened with MS Office versions prior to 2010, however, the documents install malicious software automatically, since these older versions do not include "Protected View" mode.
More examples of files that cyber criminals use within their malspam campaigns include PDF documents, MS Word documents, archive files such as ZIP, RAR, executable files like .exe, .run, and JavaScript files.
How to avoid installation of malware
You are advised to research all software before download/installation. Use only official and verified download channels. Unofficial and free file-hosting websites, Peer-to-Peer sharing networks (BitTorrent, Gnutella, eMule), and other third party downloaders commonly offer harmful and bundled content, and are therefore untrusted and should be avoided.
When downloading/installing, read the terms, study all possible options, use the "Custom/Advanced" settings and opt-out of additional apps, tools, features, and so on.
Intrusive advertisements typically seem legitimate, however, they can redirect to dubious and malicious sites (e.g. gambling, pornography, adult-dating, and many others). If you encounter ads or redirects of this kind, inspect the system and remove all dubious applications and browser extensions/plug-ins immediately.
Installed programs must be activated and updated with tools or implemented functions that are provided by the official developers. No other third party, unofficial tools should be used.
Note that it is illegal to activate licensed software with ‘cracking’ tools. Files and programs should be downloaded from official websites and via direct download links. Avoid third party installers and the tools/sources mentioned above.
Do not open website links or files in irrelevant emails that are received from unknown, suspicious addresses. These bogus emails are often disguised as official and important. Regularly, scan your computer with reputable, up-to-date antivirus or anti-spyware software.
If you have already opened the "Enel email virus" attachment, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the first malspam email:
Subject: Rimborso Riferimento PR47659U21Y1147
Enel Energia – Mercato libero dell'energia
Gentile Cliente,
Si tratta di un ultimo sollecito, si dispone di un rimborso incompiuto..
PIl rimborso delle 522,54€ è ancora valido fino 17/12/2020. É necessario compilare il modulo,
e ci dà due giorni lavorativi per elaborare la vostra richiesta.
Cordiali saluti, Enel Energia o 2020
Enel Energia rispetta l’ambiente utilizzando solo energia prodotta da fonti rinnovabili come acqua, sole, vento e calore della Terra, certificata dal Sistema di “Garanzie di Origine” del Gestore Servizi Energetici, in base alla Direttiva CE 2009/28/CE.
Screenshot of the malicious document attached to this email:
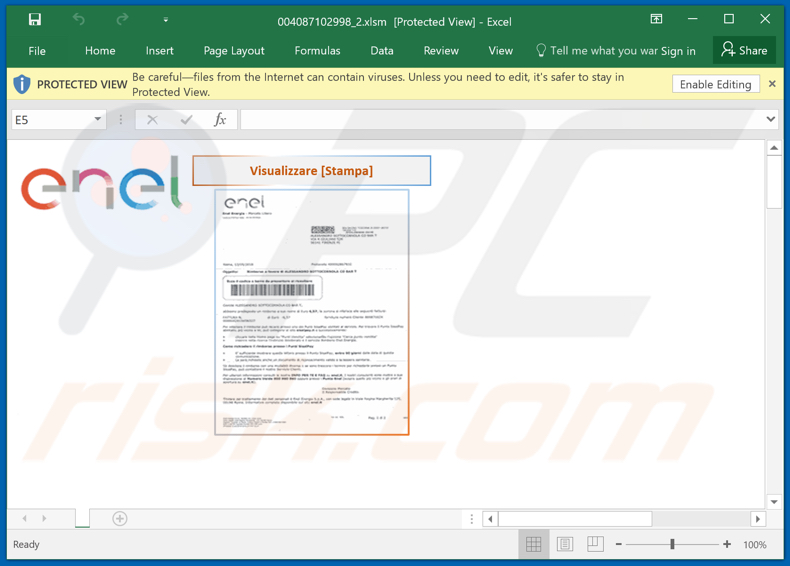
Screenshot of the second malspam email:
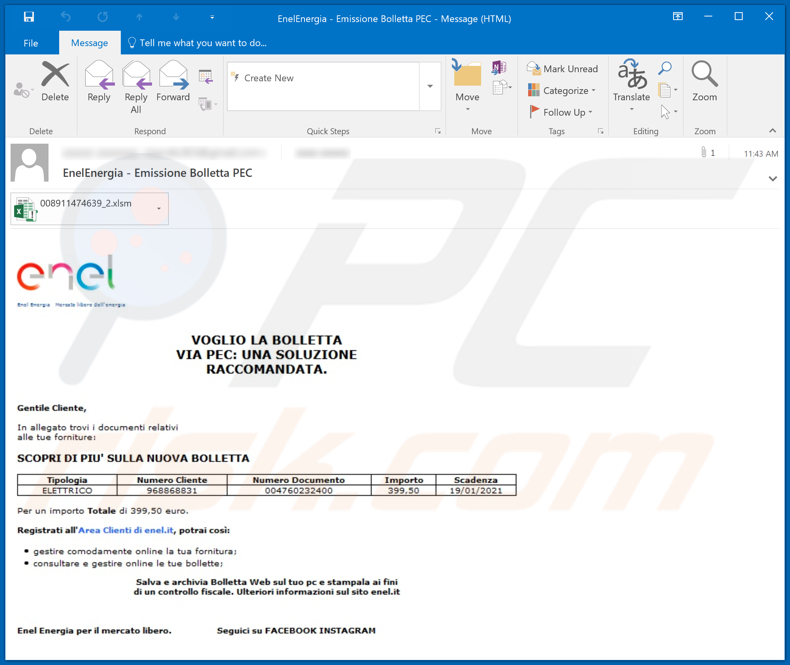
Text in this email:
Subject: EnelEnergia - Emissione Bolletta PEC
Enel Energia Mercato libero dell'energia
VOGLIO LA BOLLETTA
VIA PEC: UNA SOLUZIONE
RACCOMANDATA.
Gentile Cliente,In allegato trovi i documenti relativi
alle tue forniture:SCOPRI DI PIU' SULLA NUOVA BOLLETTA
- Numero Cliente Numero Documento Importo Scadenza
ELETTRICO 968868831 004760232400 399,50 19/01/2021Per un importo Totale di 399,50 euro.
Registrati all'Area Clienti di enel.it, potrai così:
• gestire comodamente online la tua fornitura;
• consultare e gestire online le tue bollette;Salva e archivia Bolletta Web sul tuo pc e stampala ai fini
di un controllo fiscale. Ulteriori informazioni sul sito enel.itEnel Energia per il mercato libero.Seguici su FACEBOOK INSTAGRAM
Malicious document attached to this email:
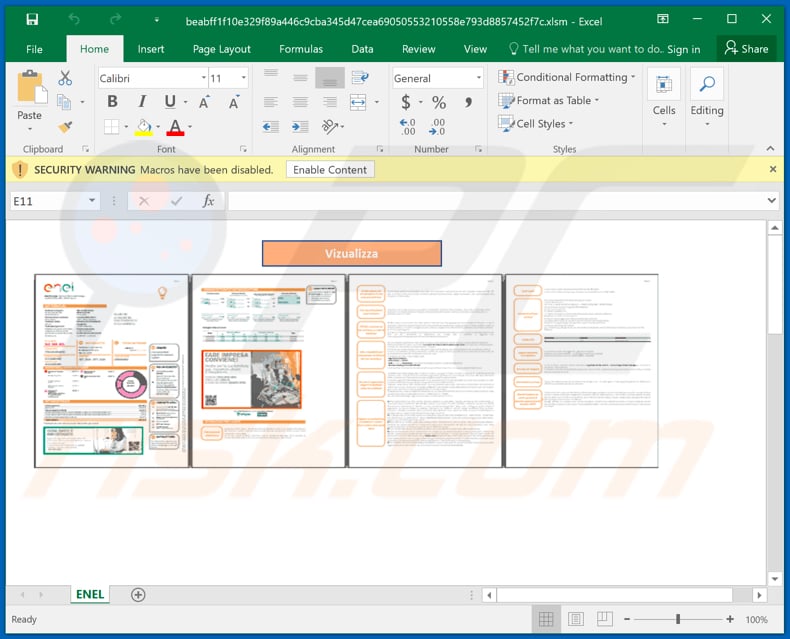
Screenshot of the phishing email:

Text in this email:
Subject: Rimborso Riferimento PR21188U14Y5292.
Gentile Cliente,
Si tratta di un ultimo sollecito, si dispone di un rimborso incompiuto..
Pll rimborso delle 89,56€ è ancora valido fino 10/02/2021. É necessario compilare il modulo,
e ci dà due giorni lavorativi per elaborare la vostra richiesta.
Area Clienti
Cordiali saluti, Enel Energia o 2020
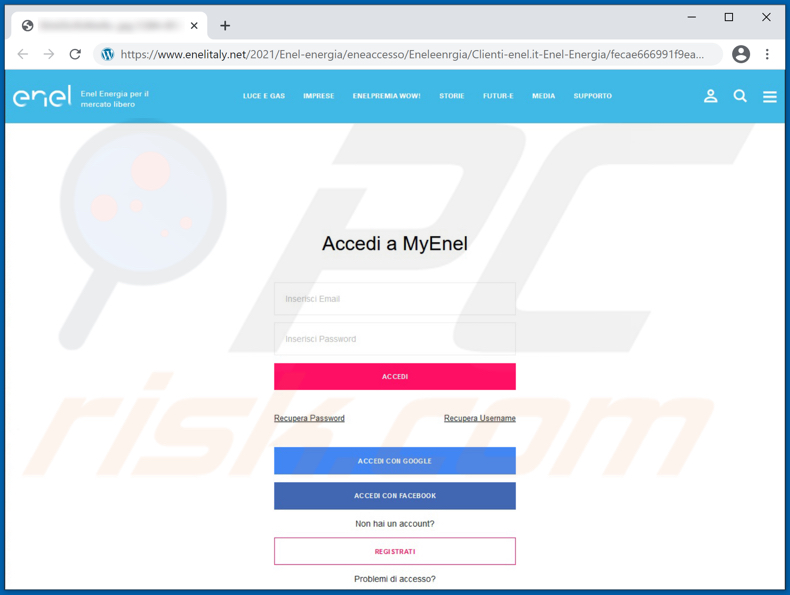
Deceptvie Enel website used to steal credentials:
Another example of a malicious Enel-themed MS Excel document (used to inject Ursnif trojan into the system) distributed via Enel-themed spam emails:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Enel spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
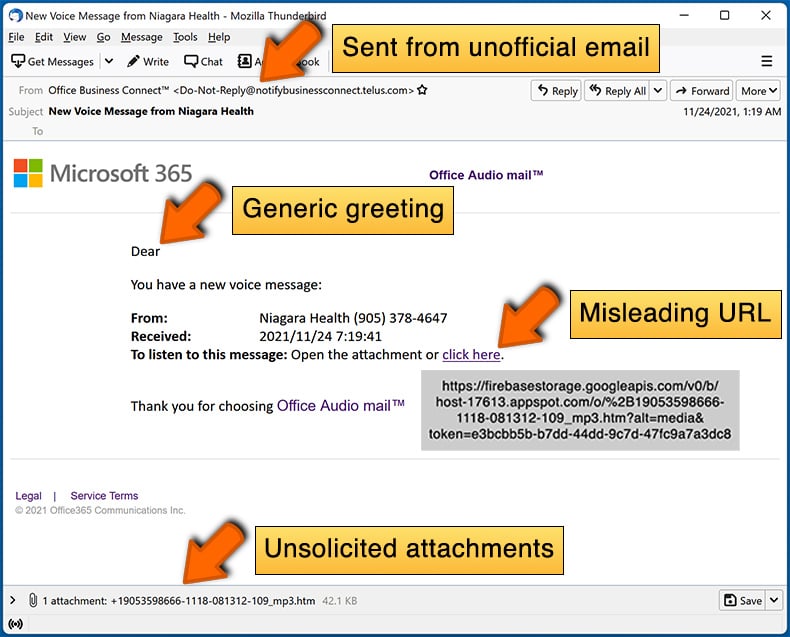
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion