Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is File Recovery?
File Recovery is a fake hard disk drive optimization/repair program. This misleading software is derived from a relatively new rogue family, which, rather than displaying fake security scans, generates hard drive error messages and attempts to trick unsuspecting PC users into believing that they could lose their stored information.
While the tactics employed by File Recovery are different to most fake programs released by Internet criminals, the outcome is the same. Creators of File Recovery hope that you will fall for the trickery incorporated within this software and purchase a license key in order to fix the supposedly 'detected' hard drive errors.
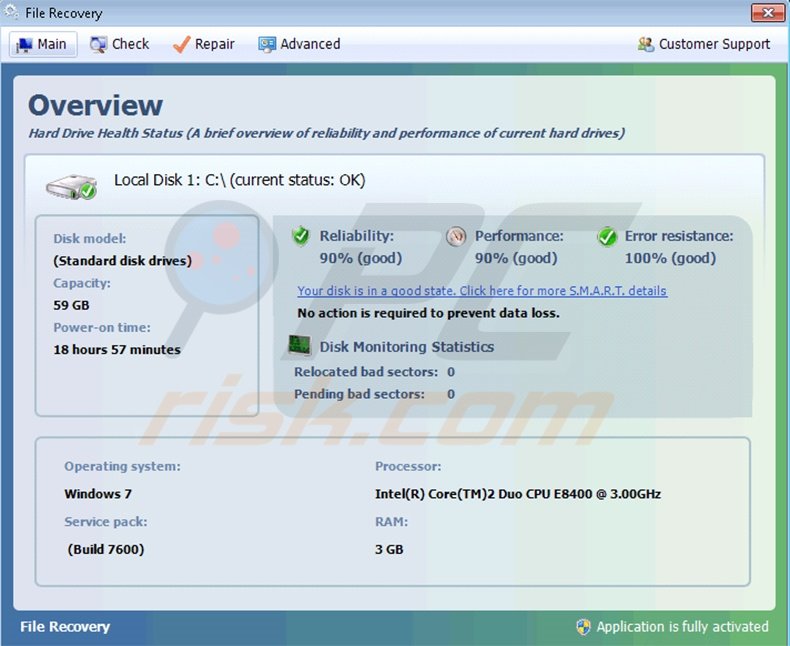
To make the error detection list appear authentic, File Recovery hides your files and Start menu items. Do not panic about your missing data - this malicious software does not actually remove any of your files, and the process of hiding them is designed to encourage you to activate the full version of File Recovery.
This bogus program merely imitates the process of scanning your hard drive; the 'Check' window shown by this software is pre-generated and the 'errors' that File Recovery indicates, do not exist. In fact, your computer hardware is likely to be fine.
If you click the 'Remove issues' button in File Recovery's 'Repair' window, you will be asked to enter your credit card information and purchase this malicious program. Do not buy this scam program - you will send your money to Cyber criminals and your computer will remain infected with the File Recovery fake hard drive scanner.
The best way to treat this misleading software is to eliminate it from your PC. Follow the removal instructions provided to regain your hidden files.
File Recovery is not unique - it is a renamed variant of the Data Recovery and Smart HDD rogue programs. Internet criminals who release these misleading hard drive scanners do not bother to change the user interface of their rogue programs, and the core elements and deceptive strategy used to trick PC users, remains unchanged.
Commonly, File Recovery is proliferated through Trojans and malicious websites, which exploit security vulnerabilities in users' computers. Ignore any hard drive issues supposedly 'detected' by File Recovery and use this removal guide to remove this scam and unhide your files.
Fake hard drive error detection list entries and fake warning messages generated by File Recovery:
Hard drive boot sector reading error. During - I/O system initialization, the boot device driver might have failed to initialize the boot device. File system initialization might have failed because it did not recognize the data on the boot device.
System blocks were not found. This has most likely occurred because of hard disk failure. This may also lead to a potential loss of data.
Error 0x0000002E - DATA_BUS_ERROR The Stop 0x2E message is typically caused by failed or defective RAM (including motherboard, Level 2cache, or video memory), incompatible or mismatched memory hardware, or when a device driver attempts to access an address in the 0x8xxxxxx range that does not exist (does not map to a physical address).
Error 0x00000024 - NTFS_FILE_SYSTEM
Error 0x00000078 - INACCESSIBLE_BOOT_DEVICE
Error 0x0000002E - DATA_BUS_ERROR
Error 0x00000050 - PAGE_FAULT_I
Your computer is in a critical state. Hard disk error detected. This can lead to hard disk failure and potential loss of data. It is highly recommended that you repair all found errors to prevent loss of files, applications and documents stored on your computer.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is File Recovery?
- STEP 1. Remove File Recovery using a registration key.
- STEP 2. Remove File Recovery using Safe Mode with Networking.
- STEP 3. Restore hidden desktop files and icons.
File Recovery removal:
After the fake HDD check performed by File Recovery, click "Repair 7 Issues", in the open window choose "I already have an activation code. Click here to activate" and enter this information:
Registration E-mail: mail@email.com
Activation Key: 56723489134092874867245789235982
You can now download and install the spyware remover, which will completely remove this fake HDD optimizer from your PC.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
If you cannot download or run the spyware remover, try running the registry fix (link below). It enables execution of programs. Download the registryfix.reg file, double click it, click YES, and then OK.
File Recovery removal instructions (on infected computer):
If you were unable to remove File Recovery using the removal tools, you can follow these removal instructions to perform some steps manually and help the removal process.
1. Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK.
During your computer starting process press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, then select Safe Mode with Networking from the list.
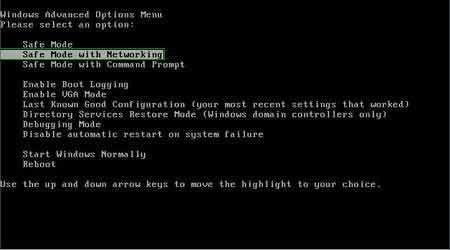
Video showing how to start Windows 7 in "Safe Mode with Networking":
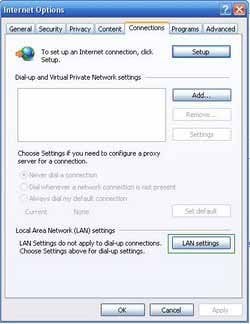
2. Open Internet Explorer, click Tools and select Internet Options. Select "Connections".
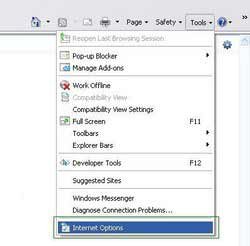
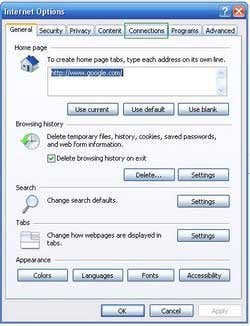
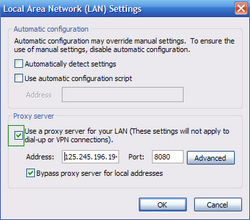
3.Click LAN settings, if 'Use a proxy server for your LAN' is checked, uncheck it and press OK.
4. Download legitimate anti-spyware software to fully remove File Recovery from your computer.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
6. After removing File Recovery reset your Hosts files. Do not skip this step, since this malware modifies your Hosts file and you will encounter browser redirect problems.
The Hosts file is used to resolve canonical names of websites to IP addresses. When it is changed, the user may be redirected to malicious websites, despite observing legitimate URLs in address bar.
It is difficult to determine if the site is genuine when the Hosts file is modified. To fix this, please download the Microsoft Fix It tool that restores your Hosts file to the Windows default.
Run this tool when downloaded and follow the on-screen instructions. Download link below:
Complete these steps if after removal of File Recovery your Desktop icons or files are hidden:
Step 1
File Recovery hides most user files. If you cannot see your files, do not panic.
The files are not missing, they are simply hidden. When downloaded and spyware remover has removed the infection, please download and run this tool to unhide your files (Link below).
It is important to run this tool only when the infection has been removed from your computer. This unhide files tool is useless if run on an infected computer.
When the unhide files tool finishes, your Windows desktop icons may still be missing. To fix this, download this .REG file. Double click when downloaded, click Yes, and then click OK. Reboot your computer and your desktop items should now be visible.
Step 2
Reboot your computer to check if everything is OK and File Recovery the rogue spyware is removed. Check if you can find all your files.
If some files remain missing, open My Computer, Click Tools, then select Folder Options... and under the View tab, select the radio button "Show hidden files and folders", press OK. You should now see your hidden files and folders.
To unhide them, Right click on the file or folder, then select Properties and uncheck the "Hidden" Check box.
That's it! You're done.
Summary:
The fake antivirus programs (also known as "rogue antivirus programs" or "scareware") are applications that tries to lure computer users into paying for their non-existent full versions to remove the supposedly detected security infections (although the computer is actually clean). These bogus programs are created by cyber criminals who design them to look as legitimate antivirus software. Most commonly rogue antivirus programs infiltrate user's computer using poop-up windows or alerts which appear when users surf the Internet. These deceptive messages trick users into downloading a rogue antivirus program on their computers. Other known tactics used to spread scareware include exploit kits, infected email messages, online ad networks, drive-by downloads, or even direct calls to user's offering free support.
A computer that is infected with a fake antivirus program might also have other malware installed on it as rogue antivirus programs often are bundled with Trojans and exploit kits. Noteworthy that additional malware that infiltrates user's operating system remains on victim's computer regardless of whether a payment for a non-existent full version of a fake antivirus program is made. Here are some examples of fake security warning messages that are used in fake antivirus distribution:
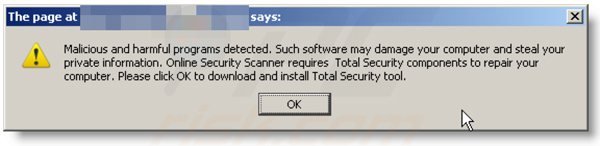
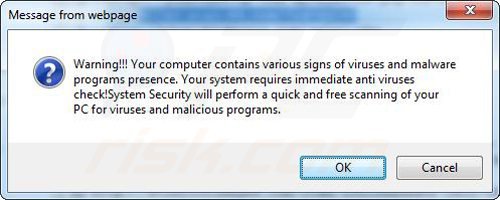
Computer users who are dealing with a rogue security software shouldn't buy it's full version. By paying for a license key of a fake antivirus program users would send their money and banking information to cyber criminals. Users who have already entered their credit card number (or other sensitive information) when asked by such bogus software should inform their credit card company that they have been tricked into buying a rogue security software. Screenshot of a web page used to lure computer users into paying for a non-existent full version of file recovery rogue and other rogue antivirus programs:
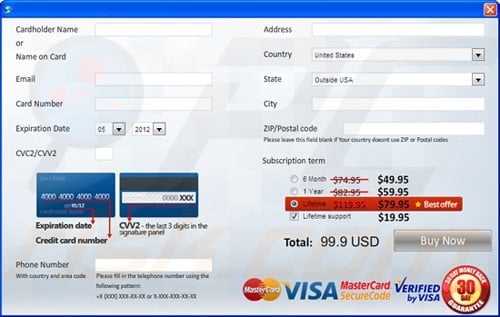
To protect your computer from file recovery rogue and other rogue antivirus programs users should:
- Keep their operating system and all of the installed programs up-to-date.
- Use legitimate antivirus and anti-spyware programs.
- Use caution when clicking on links in social networking websites and email messages.
- Don't trust online pop-up messages which state that your computer is infected and offers you to download security software.
Symptoms indicating that your operating system is infected with a fake antivirus program:
- Intrusive security warning pop-up messages.
- Alerts asking to upgrade to a paid version of a program to remove the supposedly detected malware.
- Slow computer performance.
- Disabled Windows updates.
- Blocked Task Manager.
- Blocked Internet browsers or inability to visit legitimate antivirus vendor websites.
If you have additional information on file recovery rogue or it's removal please share your knowledge in the comments section below.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion