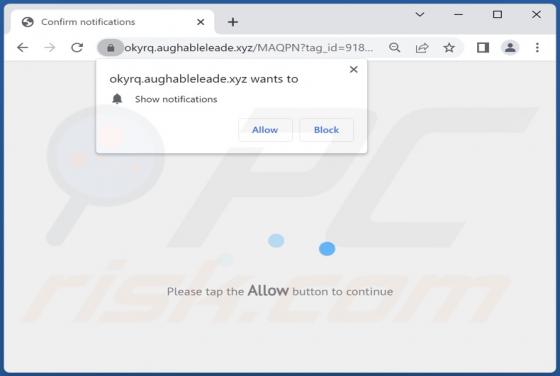
Kriptor Ransomware
While checking the VirusTotal page for recently submitted malware samples, we came across Kriptor - ransomware that encrypts files. We also found that Kriptor appends ".Kriptor" extension to filenames, changes the desktop wallpaper, and drops the "read_it.txt" file (a ransom note) on a desktop. A