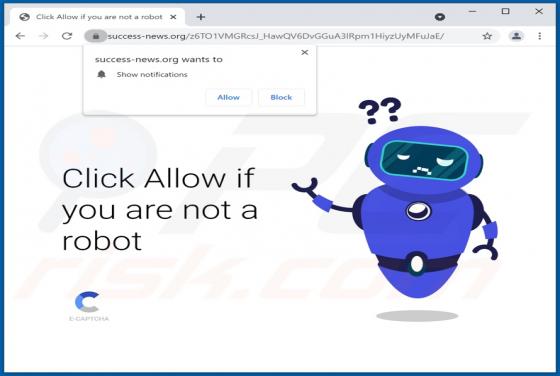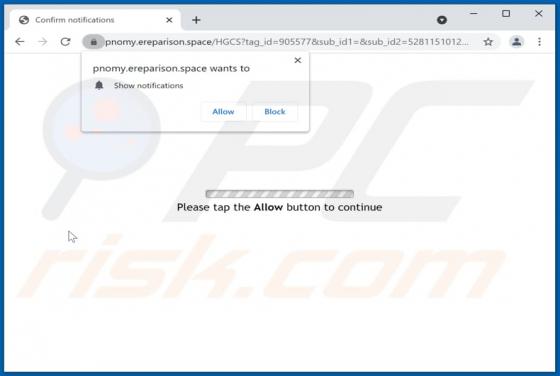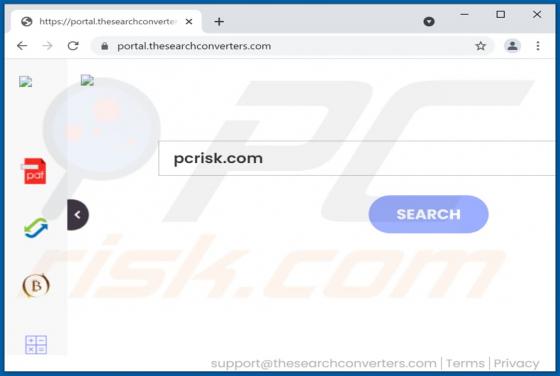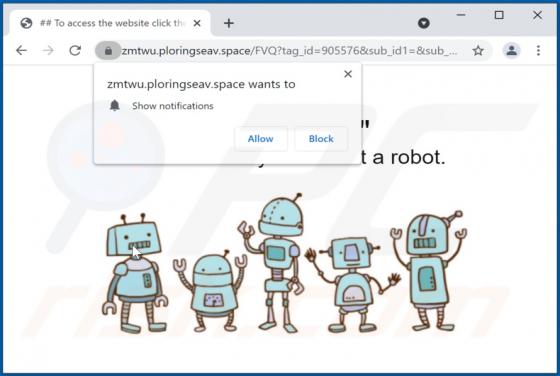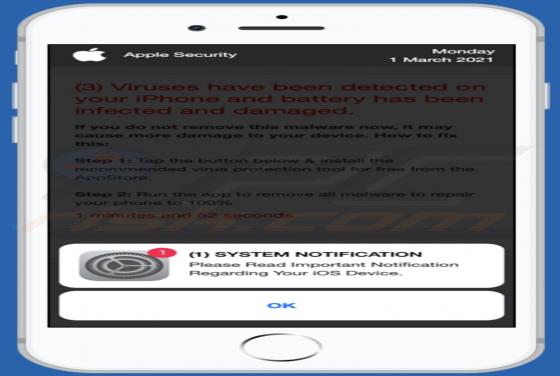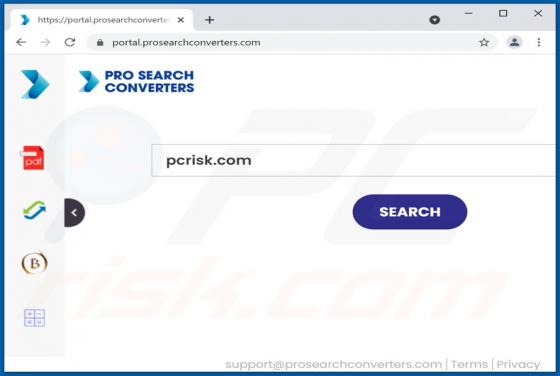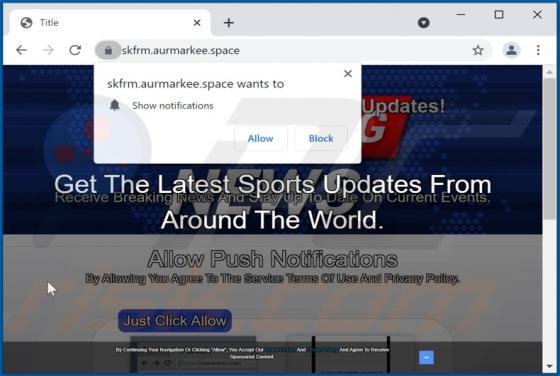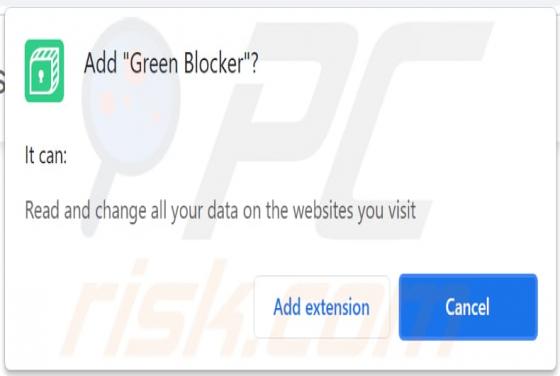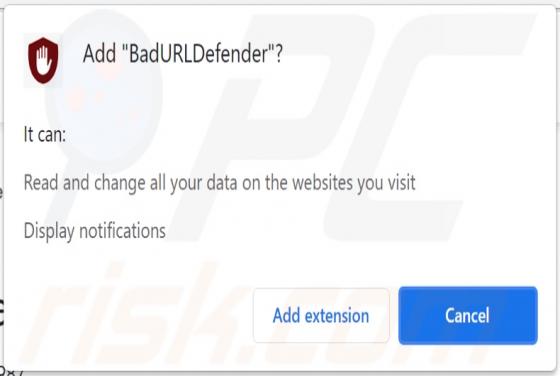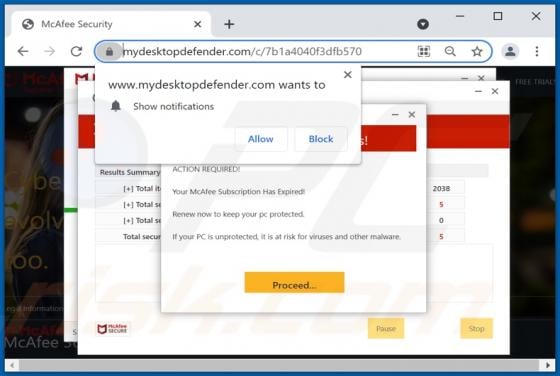
Mydesktopdefender.com Ads
Mydesktopdefender[.]com is a suspect site designed to load dubious content and/or redirects visitors to other webpages (likely unreliable or malicious ones). The Internet is full of such sites; success-news.org, ploringseav.space, and special-for.me are but some examples. Rogue websites like myde