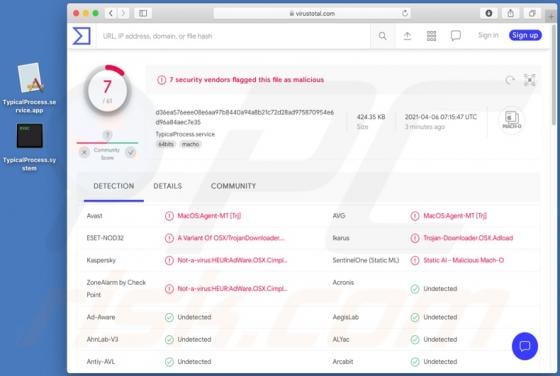
TypicalProcess Adware (Mac)
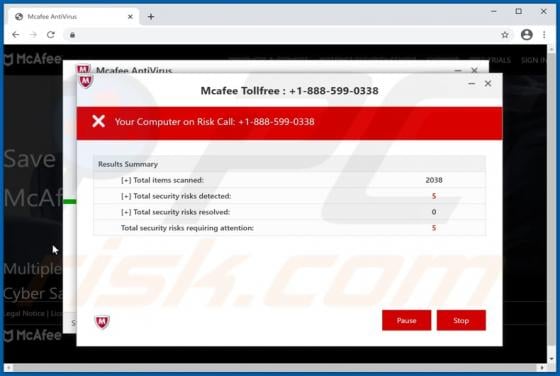
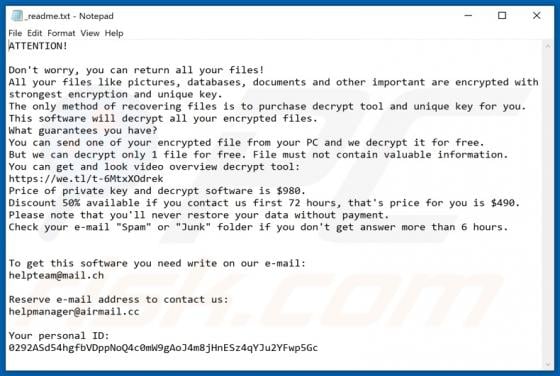
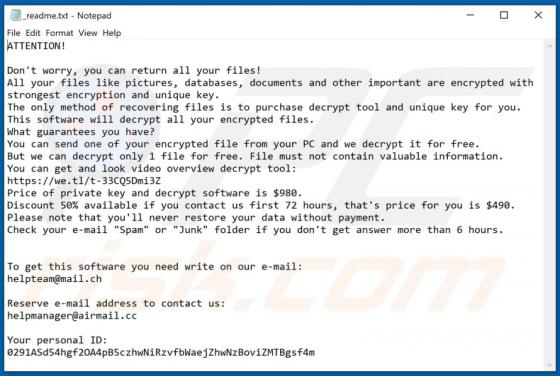
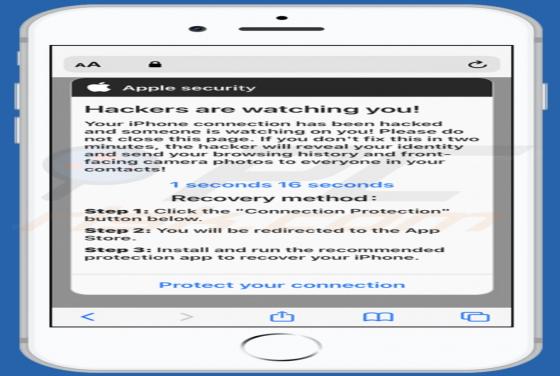
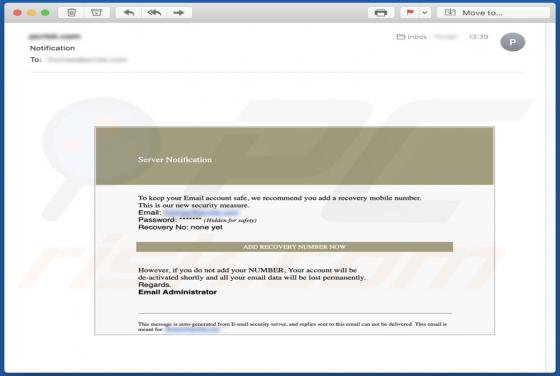
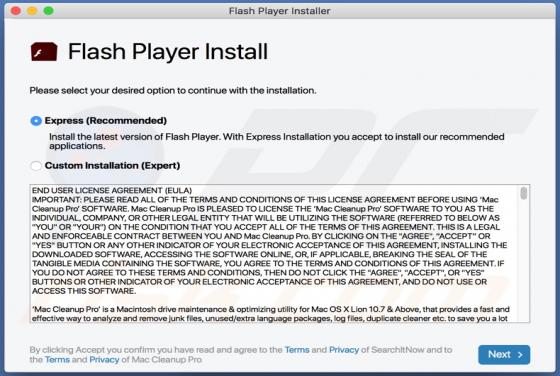
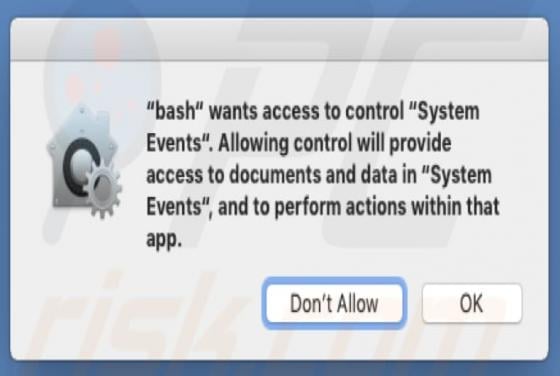
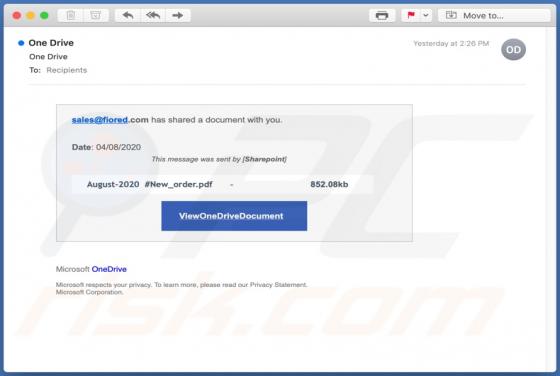
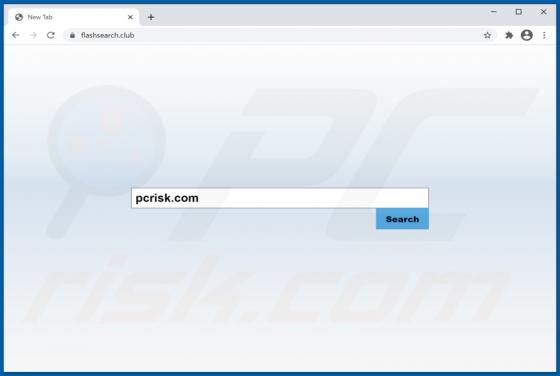
TypicalProcess is a rogue application categorized as adware. It also has browser hijacker traits. After successful infiltration, this app runs intrusive advertisement campaigns (i.e., delivers various ads) and makes modifications to browser settings in order to promote fake search engines. Addi