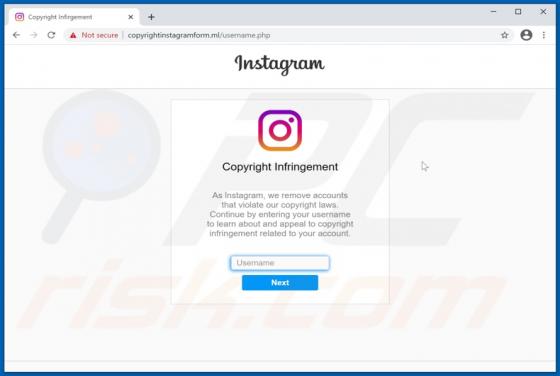
Instagram Copyright Infringement POP-UP Scam
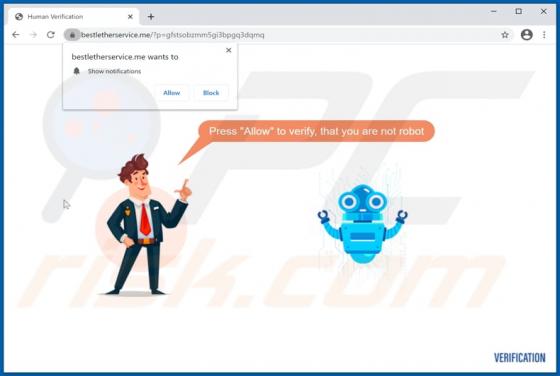
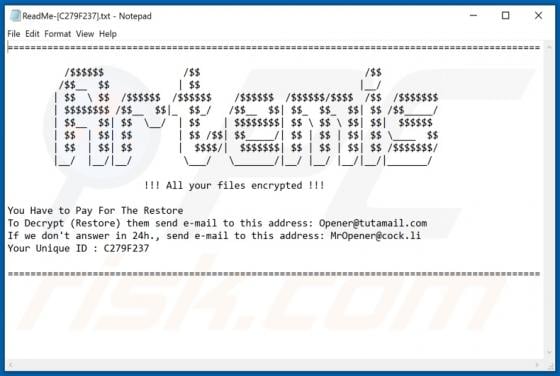
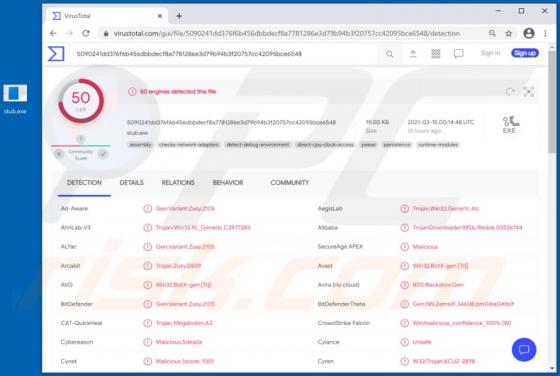
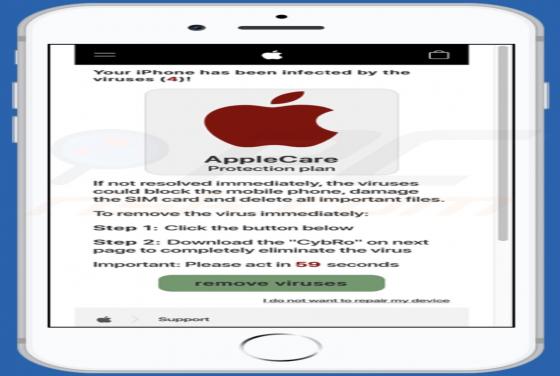
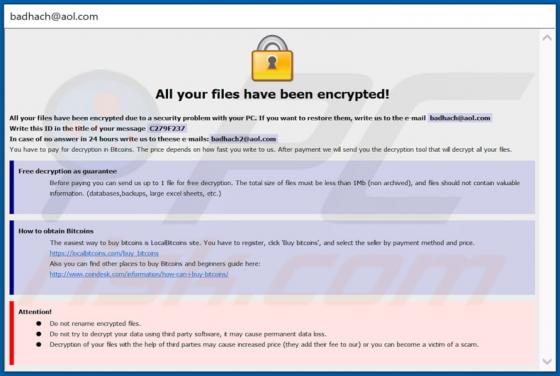
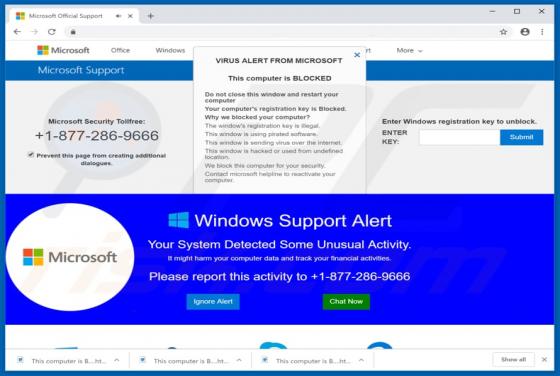
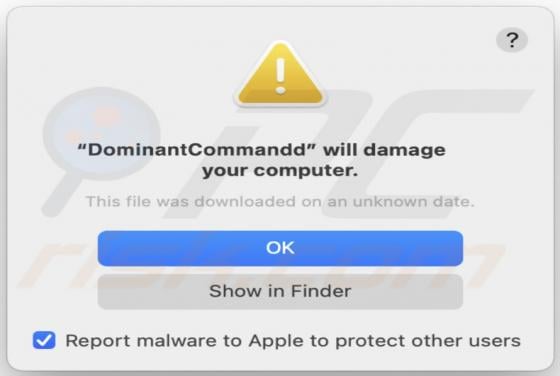
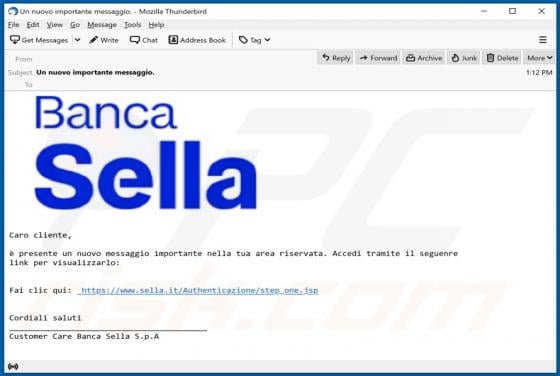
"Instagram Copyright Infringement" refers to a scam promoted on various untrusted websites. It operates as a phishing scam, claiming that content infringing copyright laws has been detected on users' accounts. In this way, it attempts to obtain Instagram log-in credentials (i.e., usernames and pas