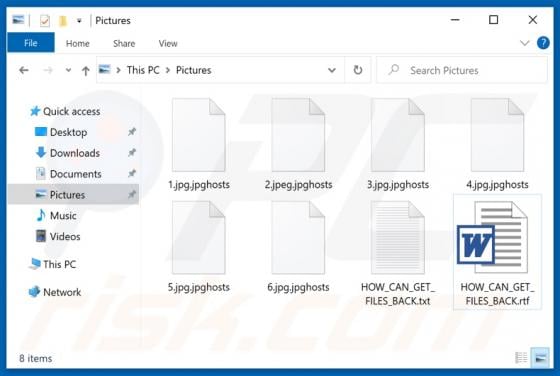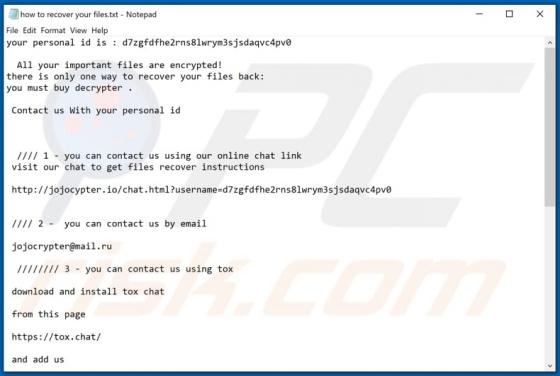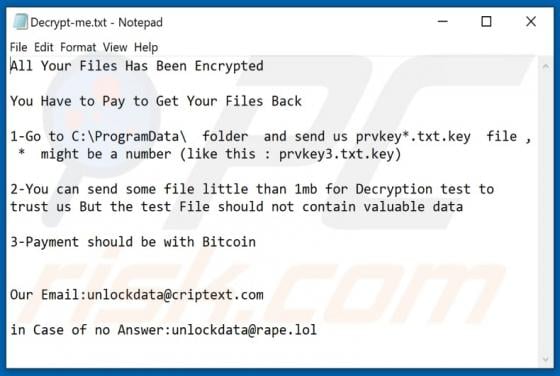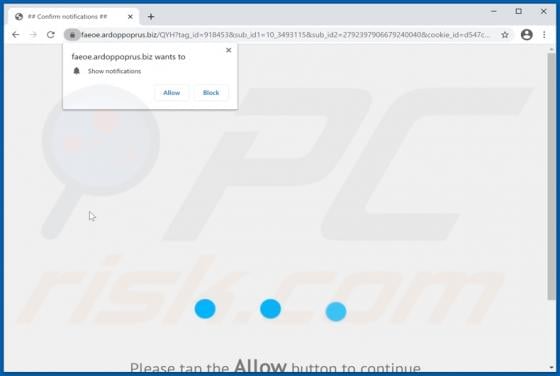
Ardoppoprus.biz Ads
Sharing many common traits with thedailyrobotcheck.site, bestletherservice.me, wholefreshposts.com, filemix-1.com, pushails.com, and thousands of others, ardoppoprus[.]biz is an untrusted website. Visitors to this site are presented with dubious content and/or are redirected to other rogue or poss