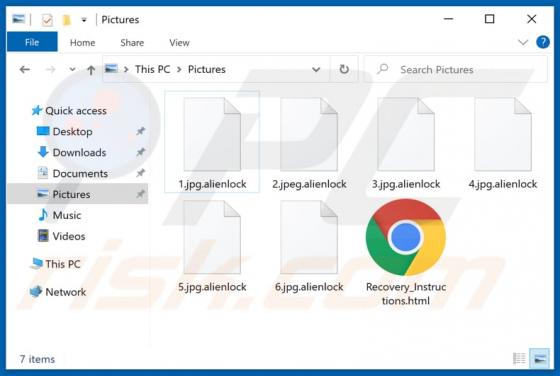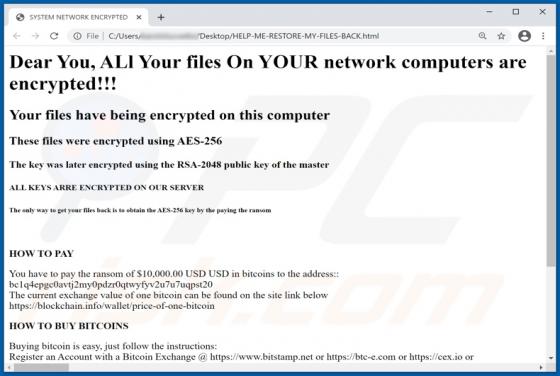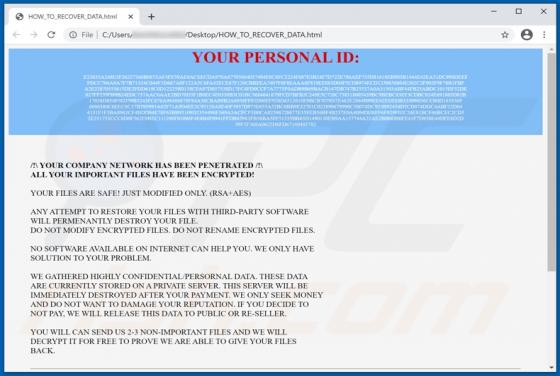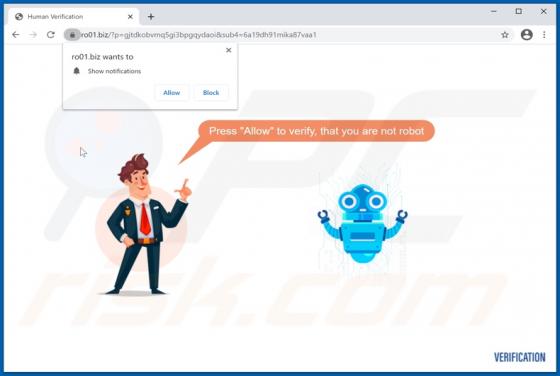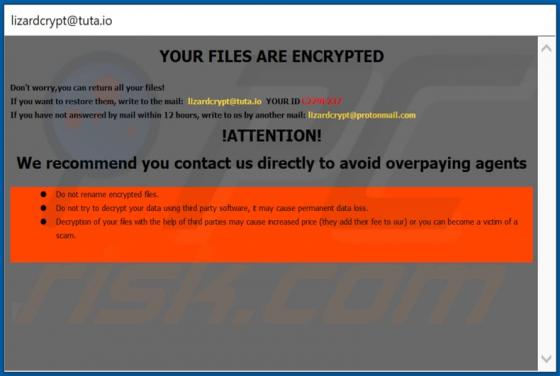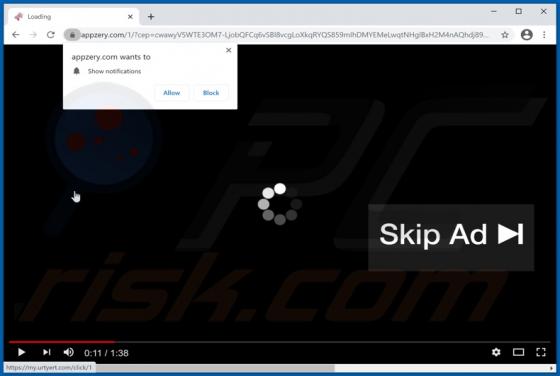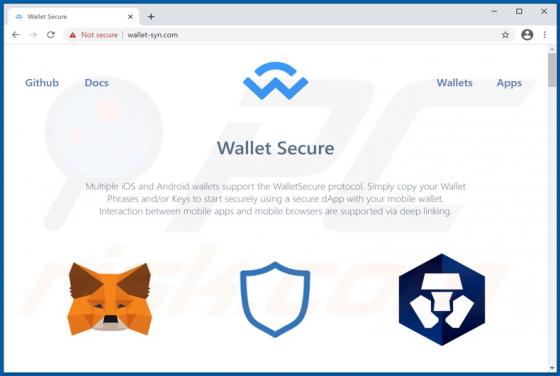
Wallet Secure POP-UP Scam
"Wallet Secure" is a scam promoted on various deceptive web pages. The scheme is presented as a service designed to store and securely connect digital wallets. through the "Wallet Secure" scam - victims' wallet credentials are extracted, which are then used to gain access and control over the wall