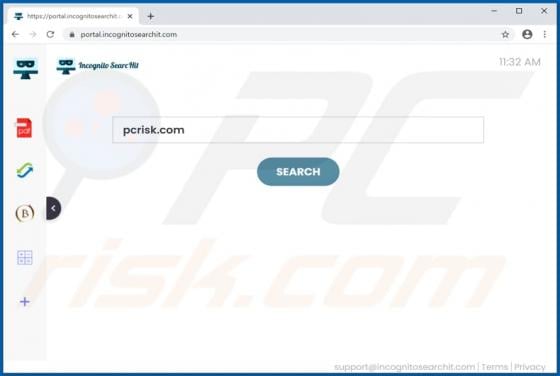
SkillFormat Adware (Mac)
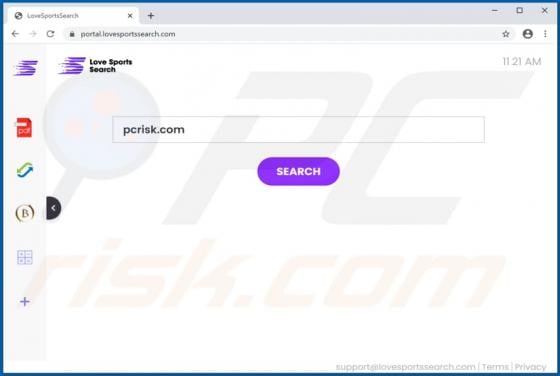
SkillFormat generates advertisements and promotes a fake search engine address, and thus functions as adware and a browser hijacker. Additionally, it is possible that SkillFormat gathers information relating to users' browsing habits and other data. This app is distributed via a deceptive instal