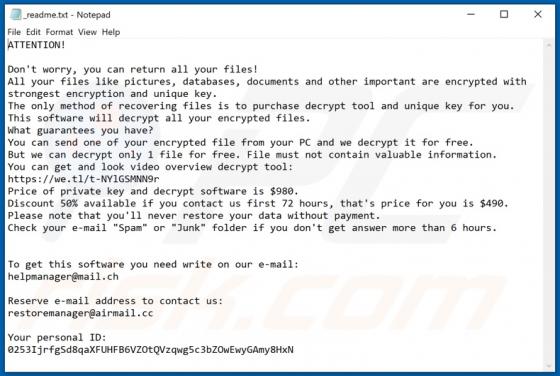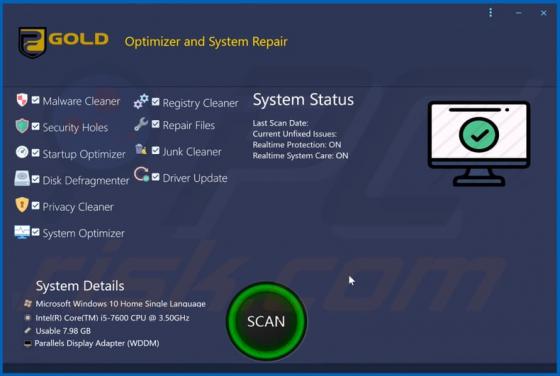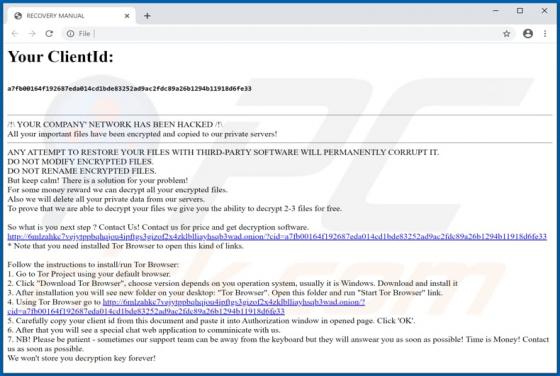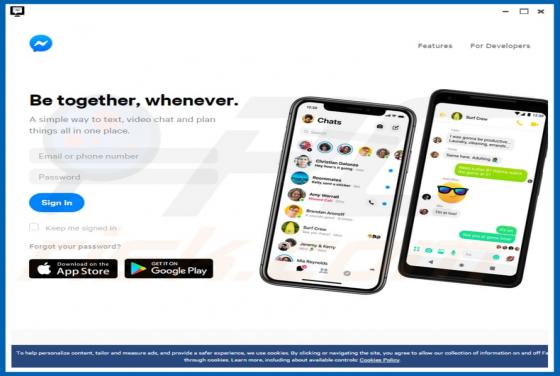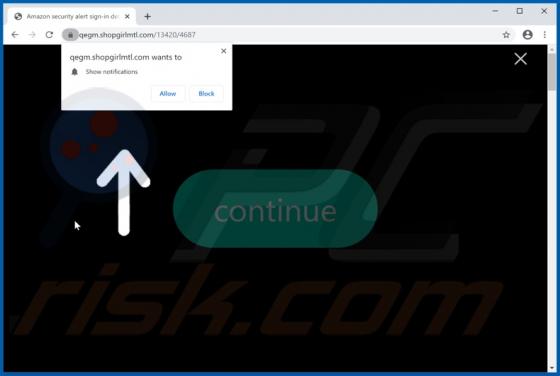
Shopgirlmtl.com Ads
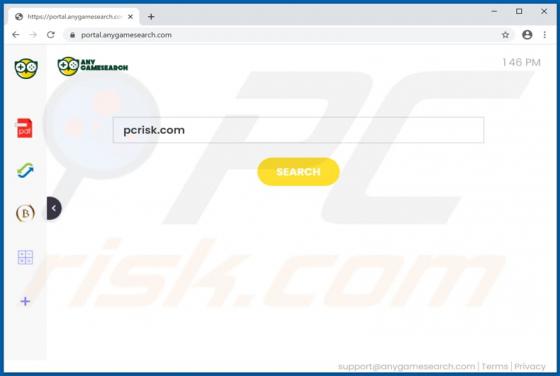
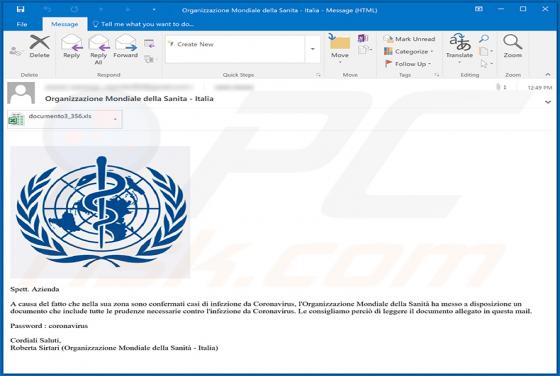
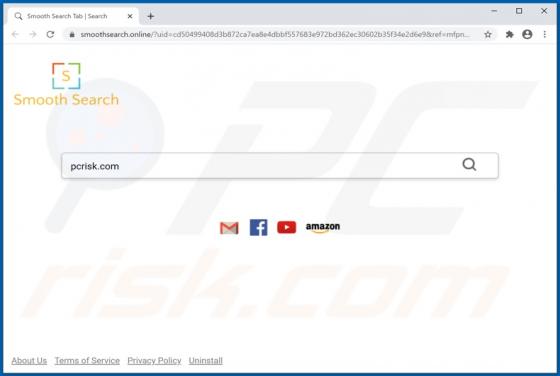
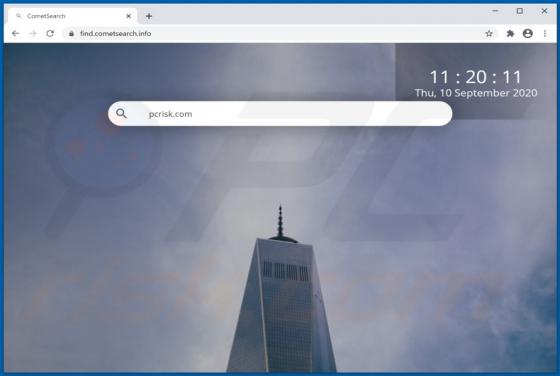
shopgirlmtl[.]com is a rogue site designed to present visitors with dubious content and/or redirect them to other untrusted or possibly malicious web pages. Few users access shopgirlmtl[.]com intentionally - most are redirected to it by intrusive advertisements or Potentially Unwanted Applications