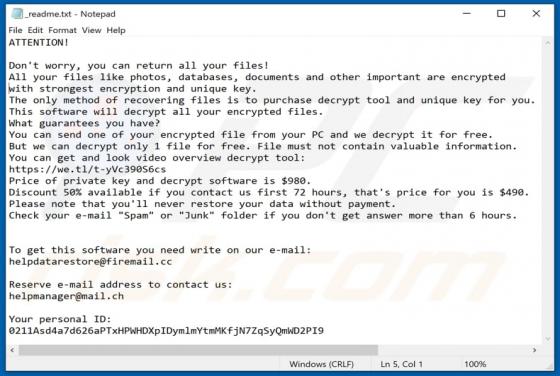
Rezm Ransomware
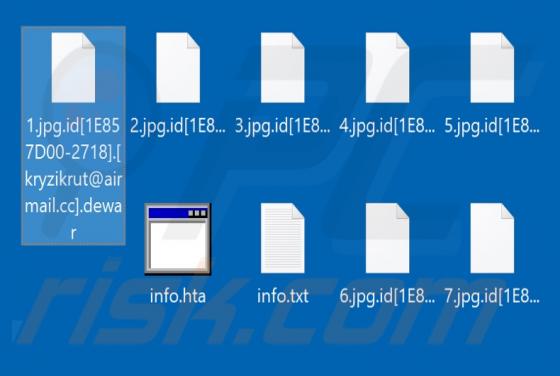
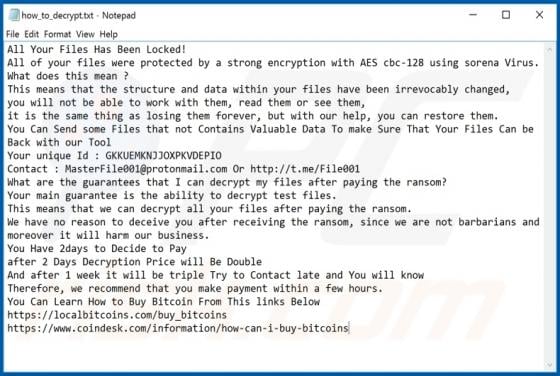
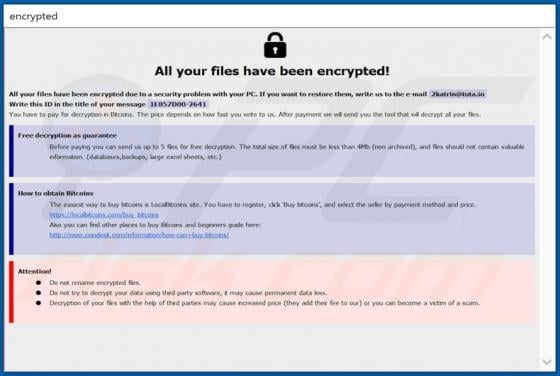
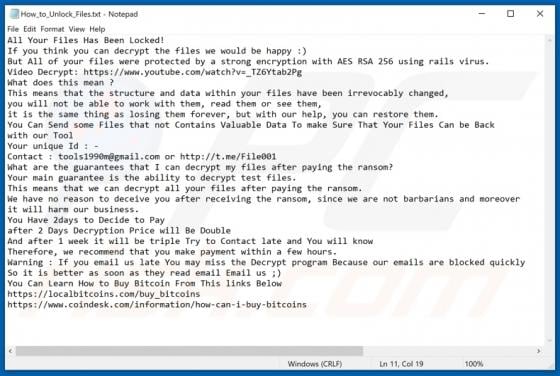
Rezm is a ransomware-type program that belongs to the Djvu family. It encrypts files that are stored on the infected computer, renames them and creates a ransom message. This ransomware renames all files by appending the ".rezm" extension to filenames. For example, Rezm renames a file named "1.jp