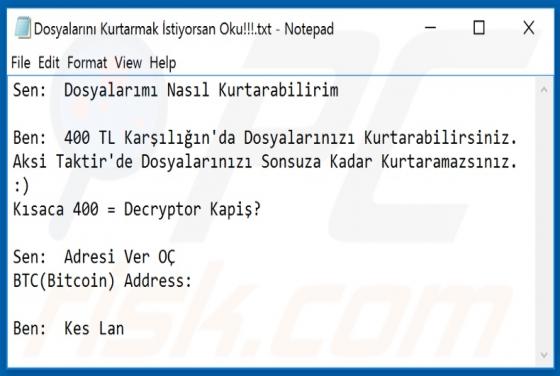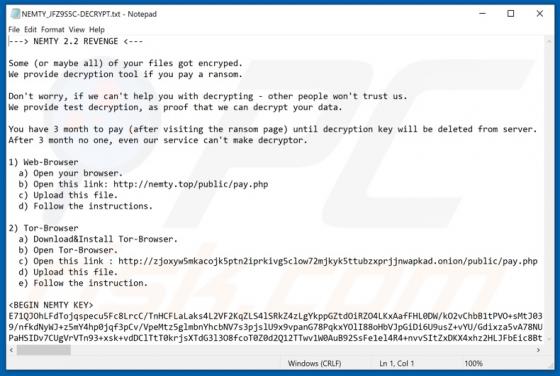
CStealer Trojan
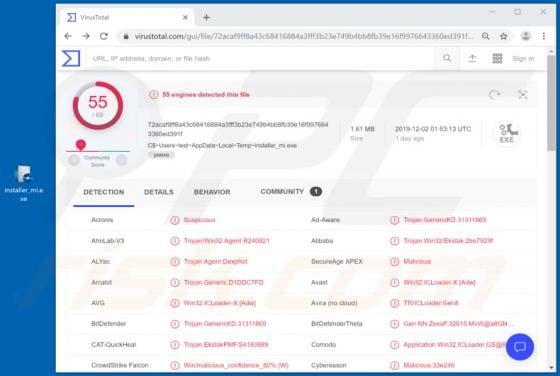
Discovered by MalwareHunterTeam and further researched by James, CStealer is malicious software classified as a trojan. This malware is designed to steal passwords stored in Google Chrome browsers. Trojan infections are high-risk and can lead to a number of significant issues. Trojan-type