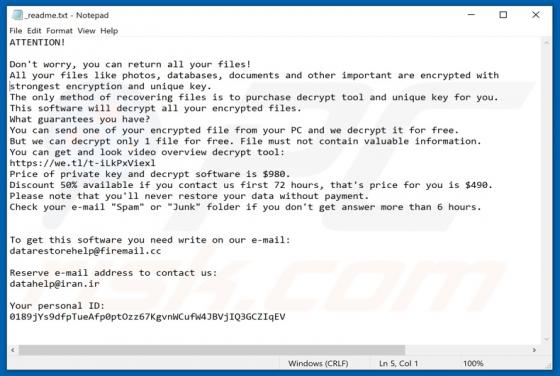
SystemDistrict Adware (Mac)
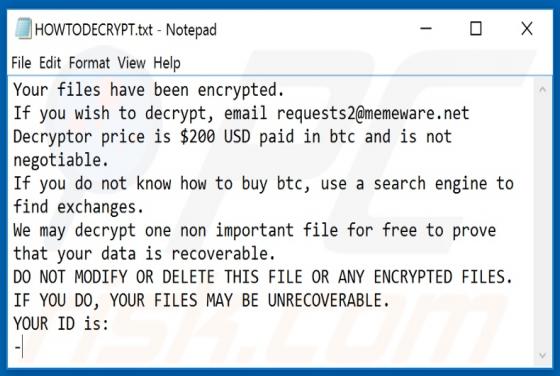
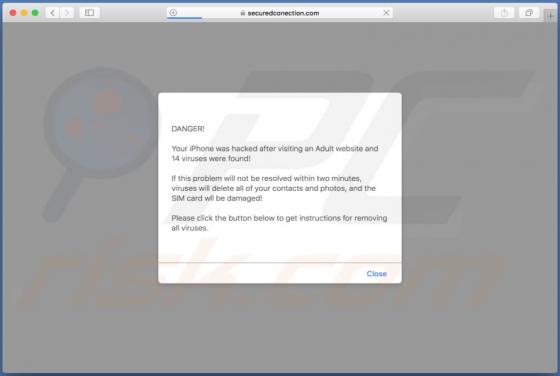
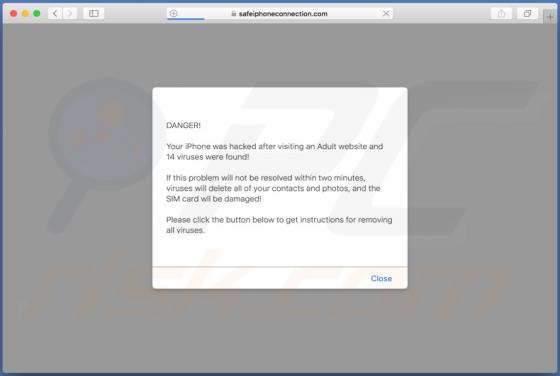
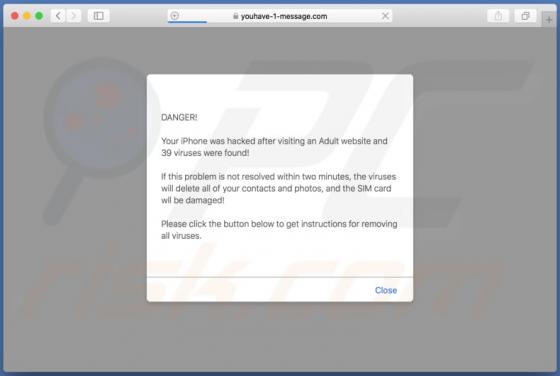
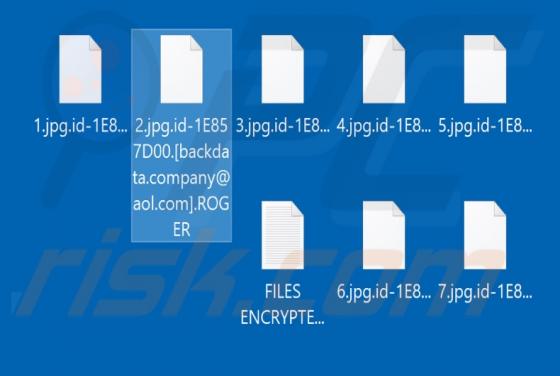
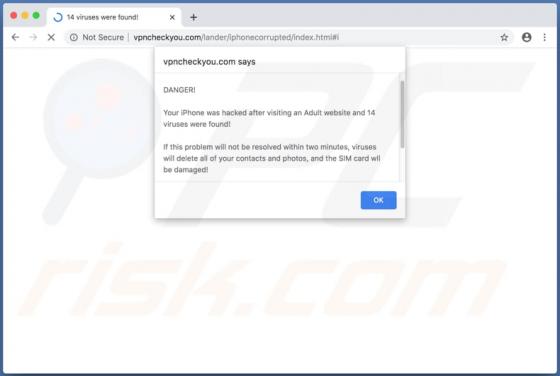
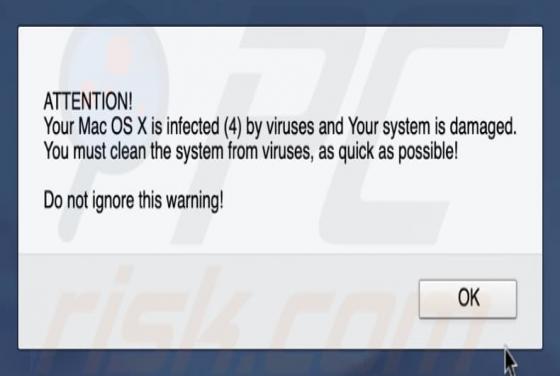
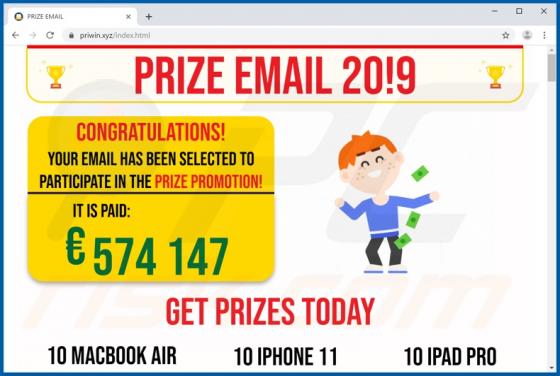
The SystemDistrict application should not be trusted, since it is categorized as adware and a potentially unwanted application (PUA). Apps of this type feed users with unwanted ads and often gather private information. Typically, people do not download or install this software intentionally. In