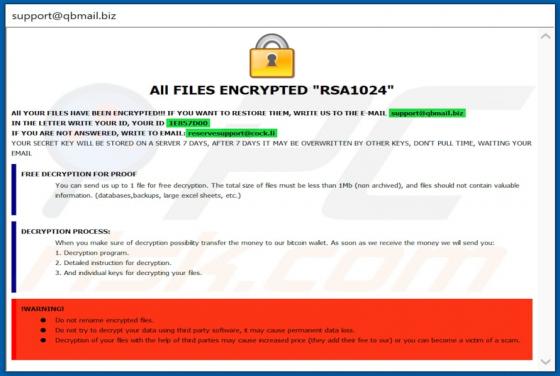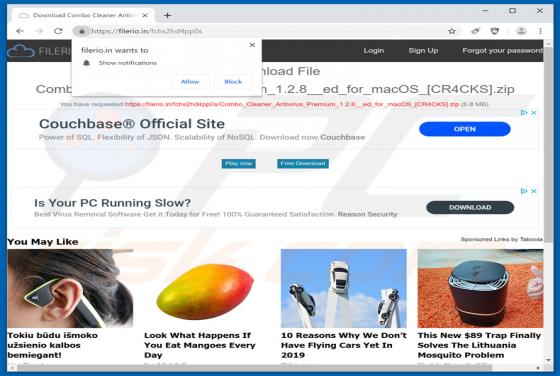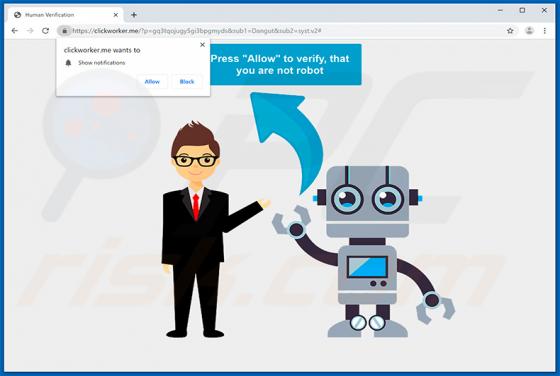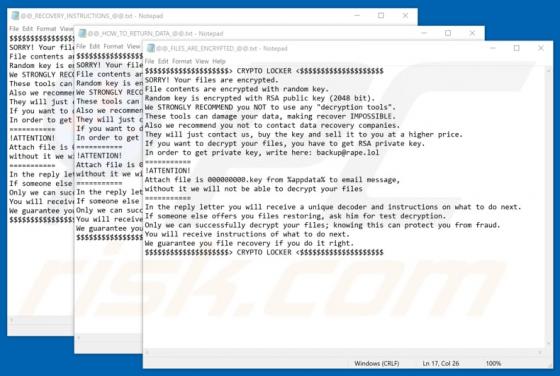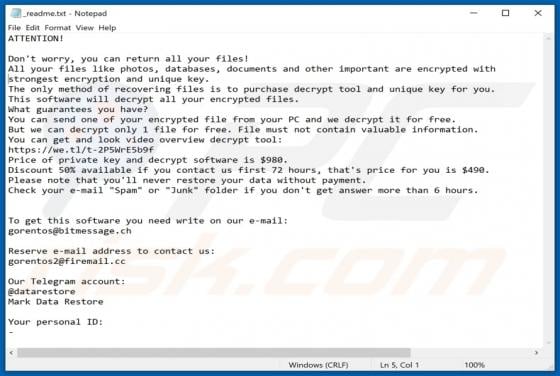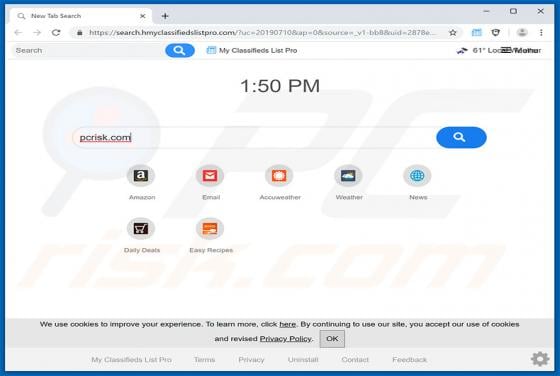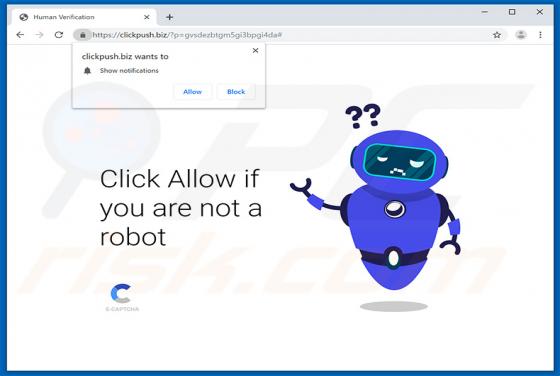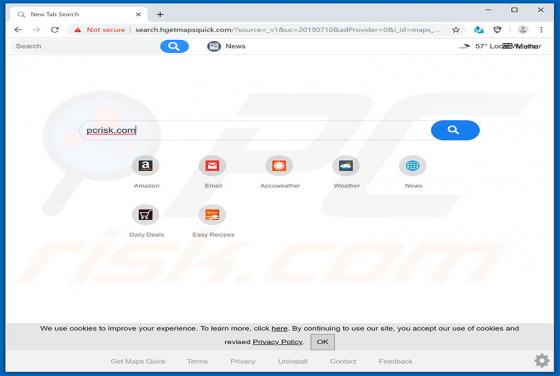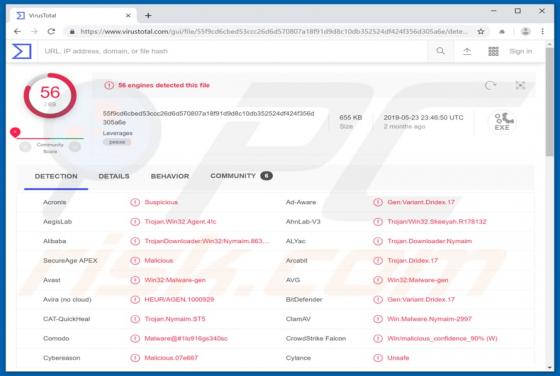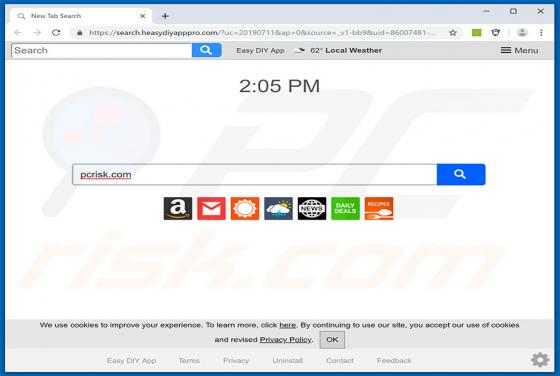
Easy DIY App Browser Hijacker
Identical to My Classifieds List Pro, Get Maps Quick, Find My Route, and many others, Easy DIY App is a deceptive application that falsely claims to provide quick access to various do-it-yourself (DIY) tutorials. On initial inspection, this app may seem legitimate and useful, however, it is categ