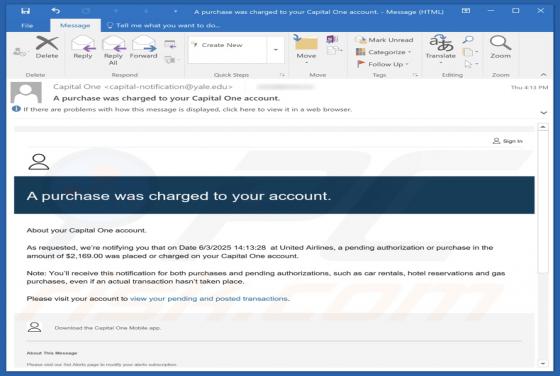
Capital One - Purchase Was Charged To Your Account Email Scam
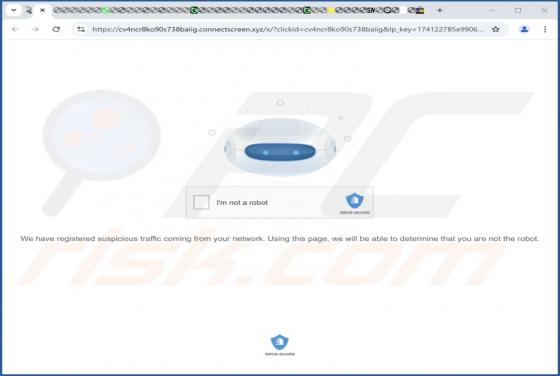
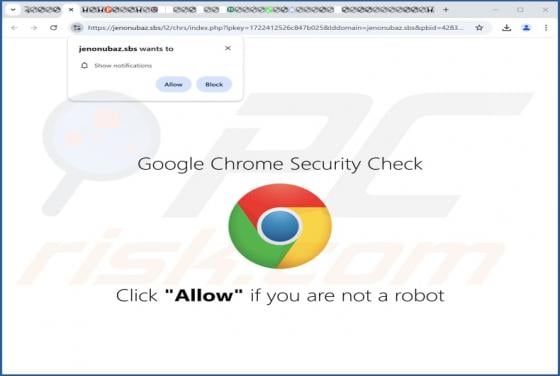
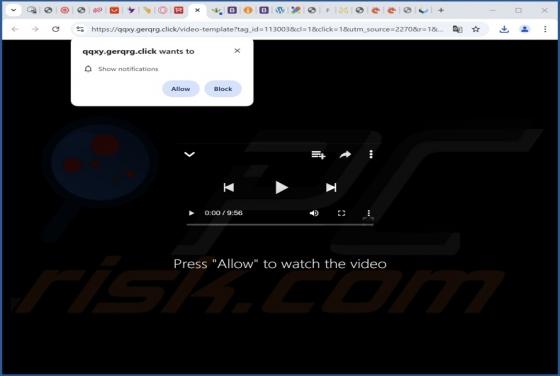
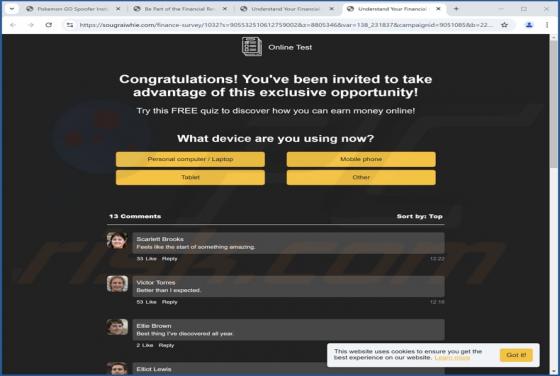
Our inspection of the "Capital One - Purchase Was Charged To Your Account" email revealed that it is spam. This fake message alerts recipients of a purchase made with their account – thus, the email lures them into revealing their log-in credentials to a phishing website. It must be emphasized th