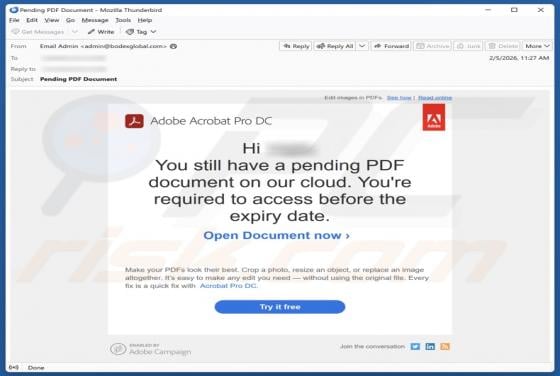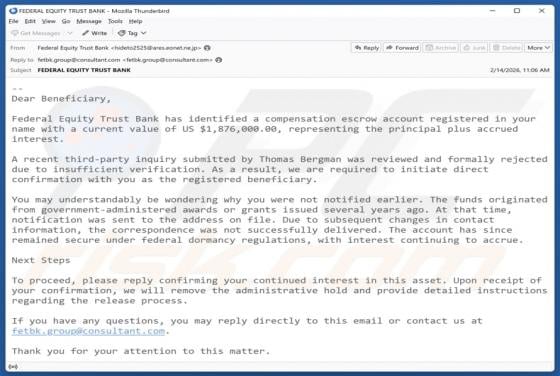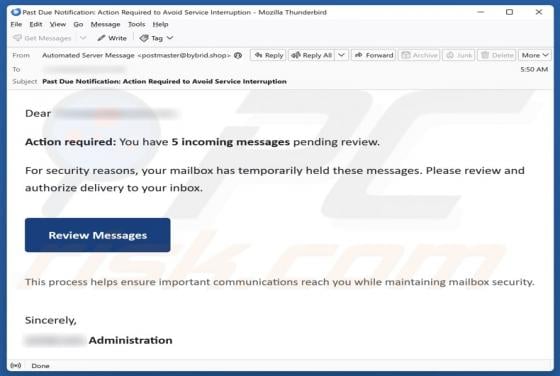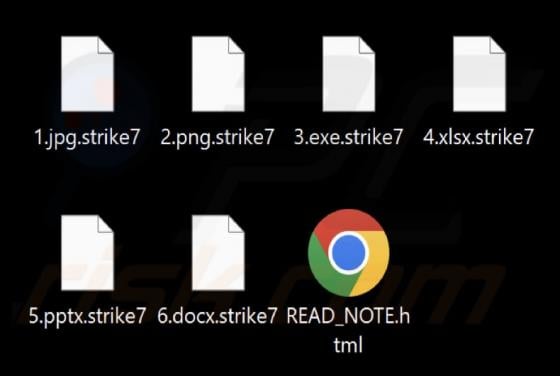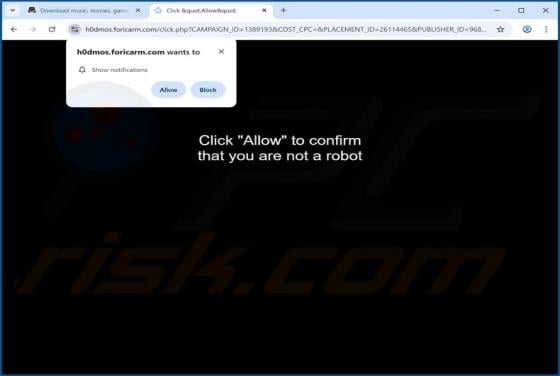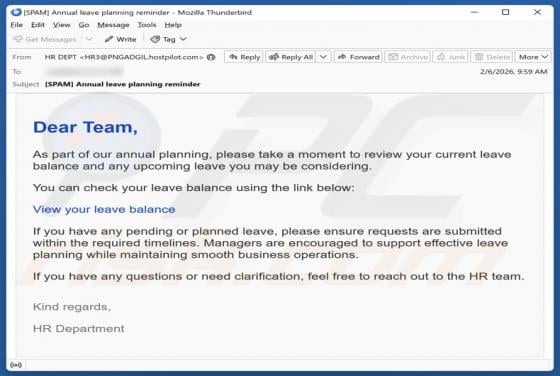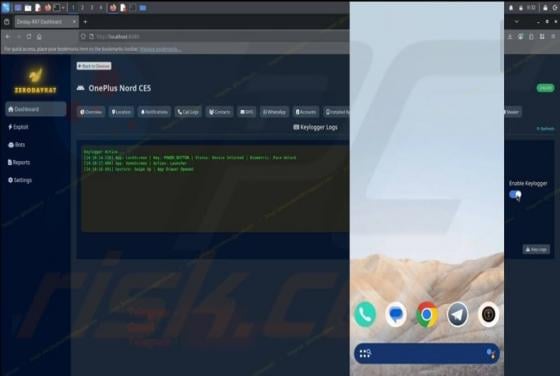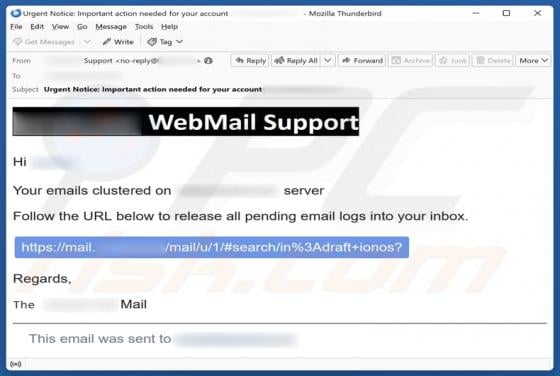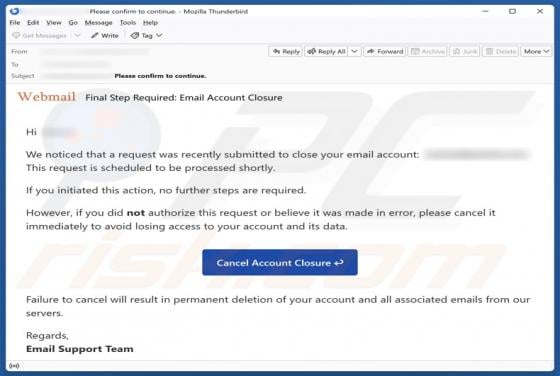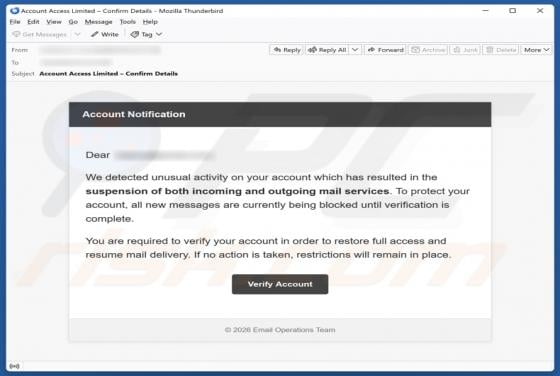
Unusual Activity On Your Account Email Scam
Our team has inspected the email and found that it contains a fake notification about suspicious activity on the recipient's account. The message also includes a link to a deceptive page designed to pilfer personal details. Such messages are classified as phishing attempts, and they should be igno