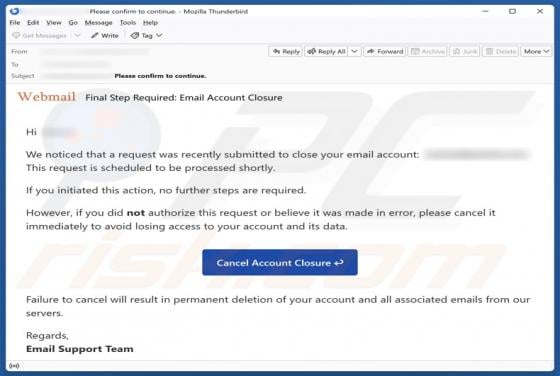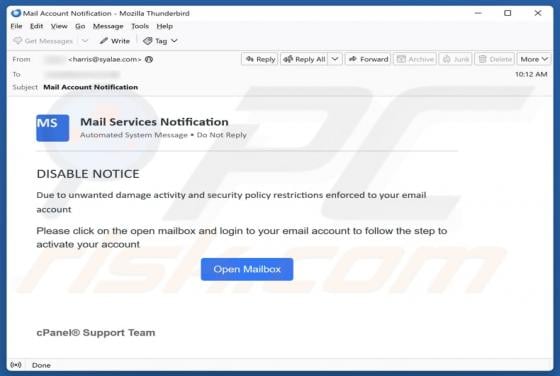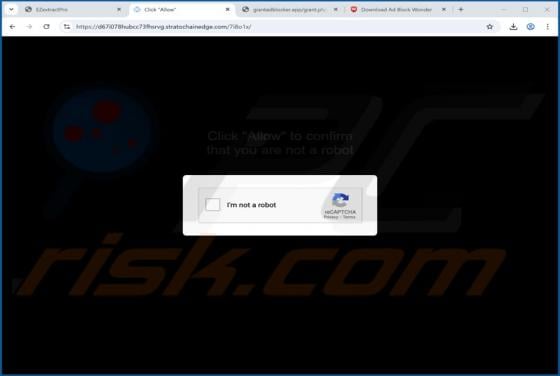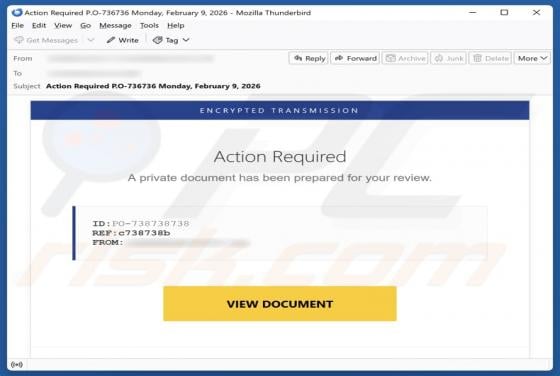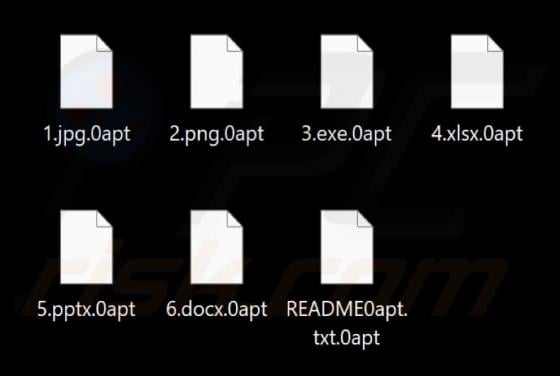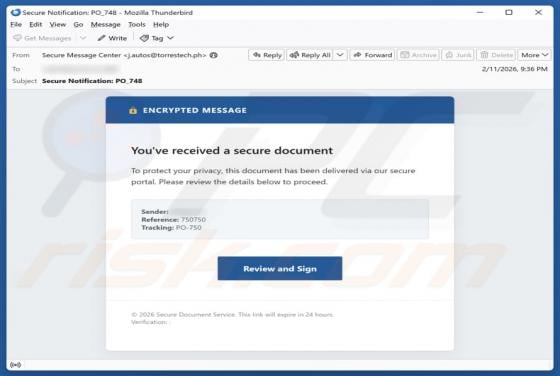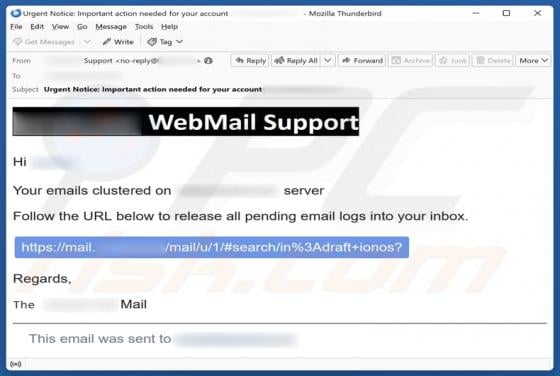
Webmail Support Email Scam
We have reviewed the email and found it to be a phishing attempt posing as an urgent notice from the email service provider. The message is designed to look urgent and important to deceive recipients into opening a fraudulent site and disclosing personal information. Recipients should not respond