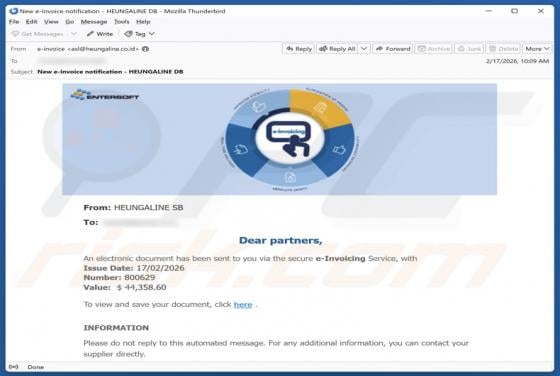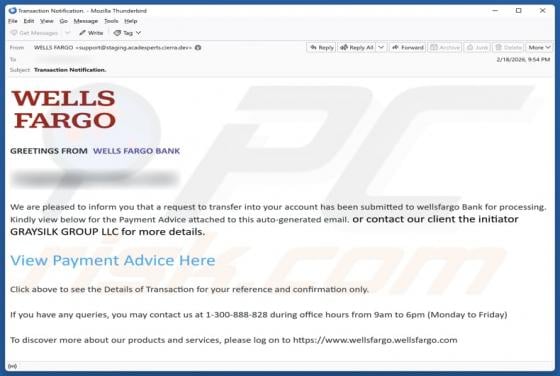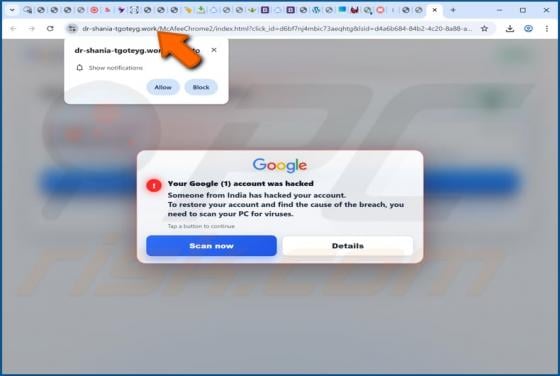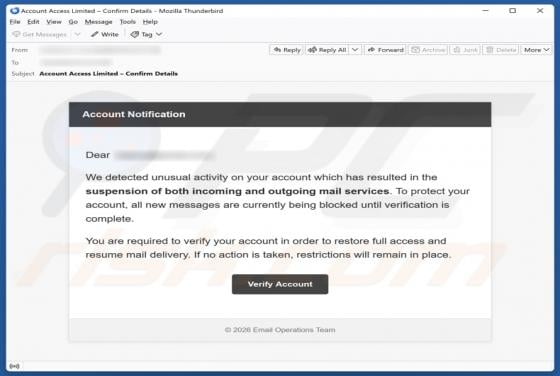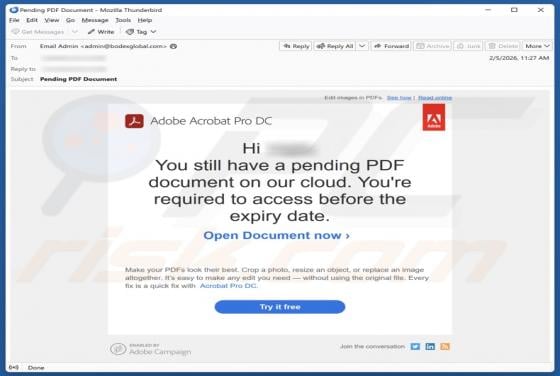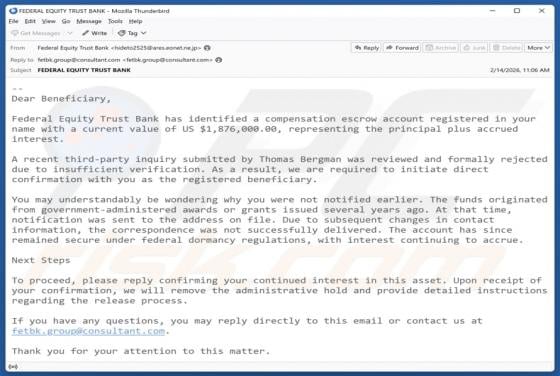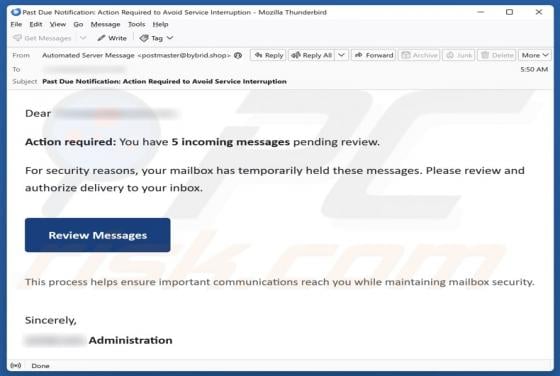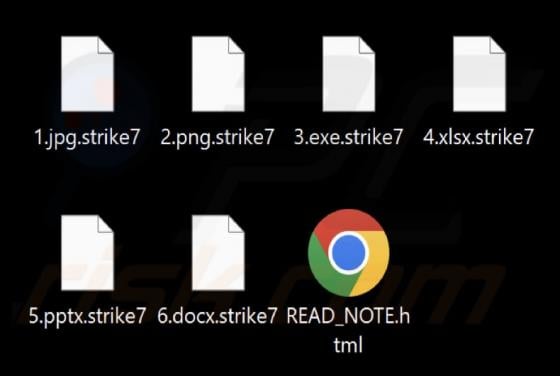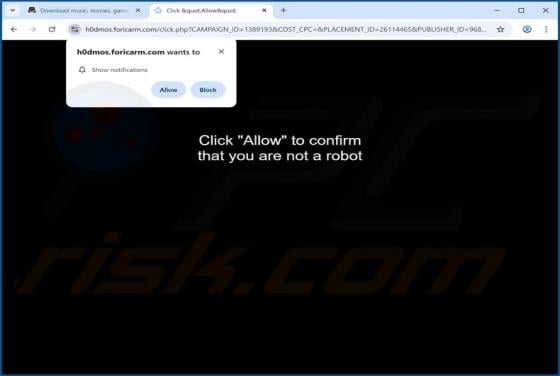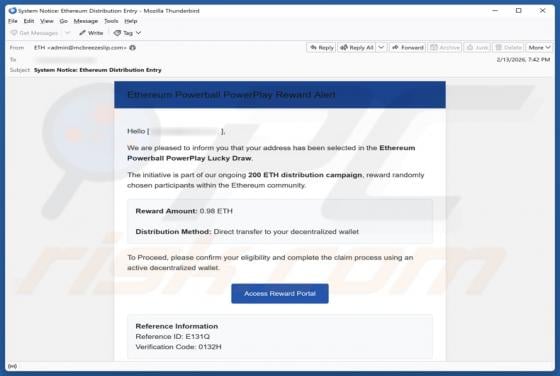
Ethereum Powerball PowerPlay Reward Email Scam
Our team has examined the email and concluded that it is a scam. The message is presented as an "Ethereum Powerball PowerPlay Reward Alert" to trick recipients into believing that they can receive rewards. However, none of the claims in this email are true, and falling for it can lead to various n