DoppelPaymer the Doppelganger Ransomware
A new week, a new ransomware variant seems to be an ongoing trend in the digital realm. This week continues the trend with news emerging of the discovery of a new ransomware variant, called DoppelPaymer. The new ransomware has been seen to be infecting victims since mid-June with the ransom asked sometimes topping hundreds of thousands of USD. According at security firm CrowdStrike the ransomware has seen at least eight variants which have extended the malware’s capabilities with each successive variant, the first of these dates back to April of this year.
DoppelPaymer takes its name from another ransomware BitPaymer, from which the early copies much of the latter’s code. Despite the similarities in the source code between the two pieces of malware, there are significant differences between the two. CrowdStrike noted that,
“There are obvious similarities between the tactics, techniques, and procedures (TTPs) used by DoppelPaymer and prior TTPs of BitPaymer, such as the use of TOR for ransom payment and the .locked extension. However, the code overlaps suggest that DoppelPaymer is a more recent fork of the latest version of BitPaymer. For example, in the latest version of BitPaymer, the code for RC4 string obfuscation reverses the bytes prior to encryption, and includes a helper function that provides support for multiple forms of symmetric encryption (i.e., RC4, 128-bit AES, and 256-bit AES)…”
These similarities are explained as a possible split within the group operating BitPaymer. The group operating BitPaymer are known as INDRIK SPIDER, a cybercriminal group specializing in wire fraud initially and responsible for the loss of millions. The group is best known for the development and deployment of the Dridex malware, a banking Trojan specifically designed to steal banking credentials for the use in wire fraud. The group became active in 2014 by former affiliates of the GameOver Zeus criminal network who internally referred to themselves as “The Business Club.” Due to increased pressure from authorities, the group’s successful use of Dridex waned. The group changed tactics in 2017 and unleashed BitPaymer upon the world in an attempt to extort funds by demanding high ransoms for encrypted data. The operators of DoppelPaymer have been seen using very similar tactics, including the demanding of high ransoms.
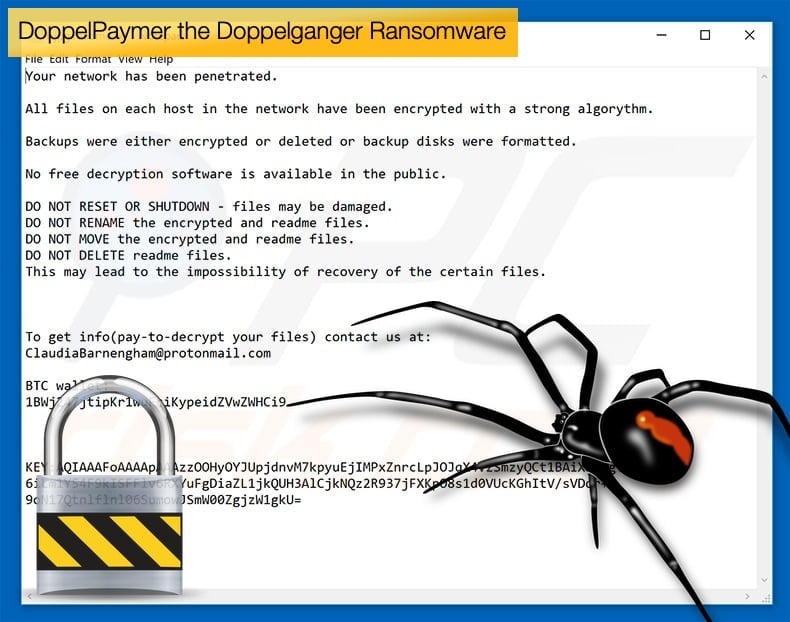
The price demanded by the group can vary from 2 BTC to 40 BTC, topping out 100 BTC. Despite Bitcoin’s current dip the ransom demanded in US Dollars can vary between approximately 25,000 USD to 1,200,000 USD. Both the ransom note and the payment portal of DoppelPaymer are incredibly similar to that used by BitPaymer. Further, the “Bit paymer” title is still present on the web page and a unique ID is still used to identify the victim. The portal provides a ransom amount, a countdown timer and a BTC address where the ransom payment can be sent.
Public Services Targeted
Based on previous victims of DoppelPaymer, it would seem that the operators of the ransomware are targeting public services offered by governments. This has proven to be a popular tactic amongst cybercriminal groups deploying ransomware. One of the first victims of DoppelPaymer was the City of Edcouch, Texas. City officials said in a statement that the city was left with a ransom note demanding 8 BTC to decrypt the data on the affected computers. The exact time of infection is unknown, however, according to city officials, the converted amount of the ransomware was 40,000 USD. This may suggest that the infection occurred in early May before the Bitcoin price slumped to 5,500 USD. The second known victim was the Chilean Ministry of Agriculture. The country's Computer Security Incident Response Team (CSIRT) confirmed on July 1 that a ransomware attack hit servers from a public service connected to the Ministry of Agriculture.
Another piece of evidence suggesting that DoppelPaymer is a forked development from BitPaymer is that both pieces of malware are still active and seemingly be used in parallel. Researcher’s noted that since November 2018, the latest version of BitPaymer has been used in at least 15 previous attacks. These attacks have continued through 2019 with incidents occurring in both June and July. The latest version of BitPaymer included an upgrade on the encryption scheme over previous versions. What is perhaps most worrisome is that the changes made and features added to DoppelPaymer make it the superior of the two ransomware variants. An example of this resides in the encryption process, DoppelPaymer employs a threaded encryption process which results in a significant encryption process. Researchers from CheckPoint concluded that,
“Both BitPaymer and DoppelPaymer continue to be operated in parallel and new victims of both ransomware families have been identified in June and July 2019. The parallel operations, coupled with the significant code overlap between BitPaymer and DoppelPaymer, indicate not only a fork of the BitPaymer code base, but an entirely separate operation. This may suggest that the threat actor who is operating DoppelPaymer has splintered from INDRIK SPIDER and is now using the forked code to run their own Big Game Hunting ransomware operations.”
It is hoped that those potential targets seen as fulling the “Big Game Hunting” target scope are aware of the dangers posed by DoppelPaymer. What has been called big game hunting by security researchers can be seen as cybercriminals actively targeting bigger organizations in the hope of bigger payouts. Rather than targeting individuals by targeting organizations and crippling their ability to conduct daily operations may force them into a corner to pay the ransom rather than suffering the costs associated with extensive downtime. In a separate report published by CrowdStrike, the operators of the Ryuk ransomware have netted approximately 3,700,000 USD, proving the tactic can be vastly profitable.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion