Emotet Returns With A Sneaky Way To Avoid Detection
On March 7, 2022, Bleeping Computer broke the news that Emotet activity had surged back to life and the malware was once again facilitating the sending of malicious spam emails.
After a three-month break, the malware’s operators deemed it was time to ramp up operations once more from an all too brief hiatus. Emotet’s operators have been known to take extended periods away from time to time only to resurface a few months later.
Emotet is somewhat notorious for several reasons, but of late, its use as a ransomware dropper to deliver ransomware payloads to compromised machines has garnered it a fair bit of additional notoriety.
Historically, the botnet functionality of Emotet is distributed through Microsoft Word and Excel attachments that contain malicious macros. If a user opens the attachment and enables macros, a DLL will be downloaded and executed that installs the Emotet malware on the device.
 The malware can then sit on the system inactive for some time until it receives instructions from an operator’s command and control server. Once an instruction is received, the malware will steal email contacts and email content for use in future spam campaigns.
The malware can then sit on the system inactive for some time until it receives instructions from an operator’s command and control server. Once an instruction is received, the malware will steal email contacts and email content for use in future spam campaigns.
Further, as alluded to above, the malware can be used to grant other malware payloads initial access to the compromised machine. Once initial access is granted, the compromised network is now vulnerable to ransomware attacks, data breaches, cyber espionage campaigns, and other cyber attacks.
This initial attempt to boot up Emotet operations after a three-month hiatus would ultimately be a failure primarily due to Microsoft’s default disabling of macros for its software products. In this attempt, security researchers noted that rather than using reply chain emails as had been previously seen, threat actors were using a fake invoice as the lure. Bleeping Computer went on to state,
Attached to these emails are ZIP archives containing inflated Word documents that are over 500 MB in size. They are padded with unused data to make the files larger and harder for antivirus solutions to scan and detect as malicious. These Microsoft Word documents use Emotet’s ‘Red Dawn’ document template, prompting users to enable content on the document to see it correctly.
If the user clicks on the prompt to enable the correct viewing of the document, the Emotet DLL will be downloaded. This is over 500 MB as well and also contains dummy data to bypass antivirus detection. However, as Microsoft disabled macros by default, most users will not be able to download the malware by mistake, believing it to be a legitimate invoice.
Emotet Begins Using Microsoft OneNote
This move to block macros by default by Microsoft has led threat actors to pursue other infection vectors, including such as Microsoft OneNote, ISO images, and JS files. Emotet’s developers and operators have also learned from the above-mentioned failed campaign and are using OneNote to distribute their malware.
Security researcher abel appears to have been the first researcher to spot Emotet’s new campaign leveraging OneNote. The new campaign uses OneNote attachments and is distributed in reply-chain emails that impersonate guides, how-tos, invoices, and job references.
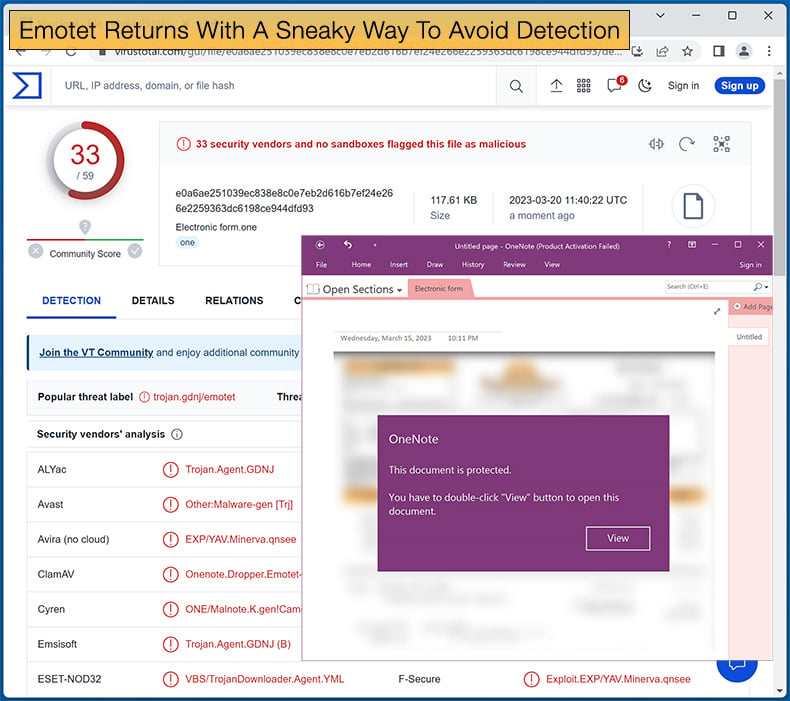
If the possible victim attempts to open the malicious OneNote attachment, the user is informed that the document is protected, and they will need to click “View” to see the document.
How threat actors are abusing OneNote to distribute malware comes down to OneNote allowing you to create documents that contain design elements that overlay an embedded document.
However, when you double-click on the location where the embedded file is located, even if there is a design element over it, that file will be launched. A threat actor just needs to place the embedded file behind a design element.
In the Emotet campaign, a malicious VBScript file called “click.wsf” is hidden underneath the “View” button. Once the “View” button is clicked, the infection routine begins with the Emotet DLL being downloaded.
OneNote will notify the user that attempting to launch an embedded file can result in malware being downloaded to the machine; however, many users will simply click “OK” without a second thought.
Microsoft is aware of this security loophole and is in the process of developing improved security features to prevent OneNote from being abused in this way; however, there is no set release date for these features, so it is important to educate staff members of this infection vector.
Further, it is advised that Windows admins configure group policies to protect against malicious Microsoft OneNote files. Admins can use these group policies to either block embedded files in Microsoft OneNote altogether or allow you to specify specific file extensions that should be blocked from running.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion