Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "Proof attached"?
"Proof attached" is the name of a spam email campaign that is categorized as a 'sextortion' scam. Generally, scams of this type are used to scare people (recipients) and trick them into believing that scammers have recorded a compromising video (or taken photos) and will proliferate the material unless recipients pay a specific sum.
In summary, this scam is used to extort money from people and we strongly recommend that you ignore the emails.
There are at least two variants of this particular scam, however, their purpose is essentially identical. The emails state that the recipient has installed a program that allowed these cyber criminals to use the computer microphone and webcam. It is stated that the webcam was used to record an embarrassing video of the recipient watching a pornographic video.
This program is apparently capable of stealing data such as contacts, account details, and so on. Scammers urge recipients to pay $310 within three days (or $660 within two days, depending on the version of this scam). In either case, the money must be transferred using a cryptocurrency (Bitcoin). A Bitcoin wallet address is provided in both variants.
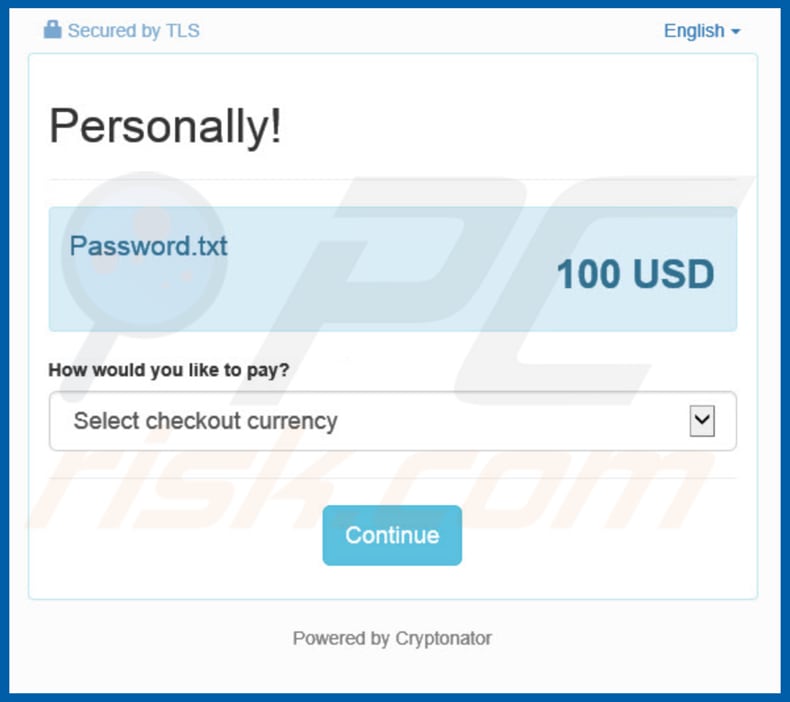
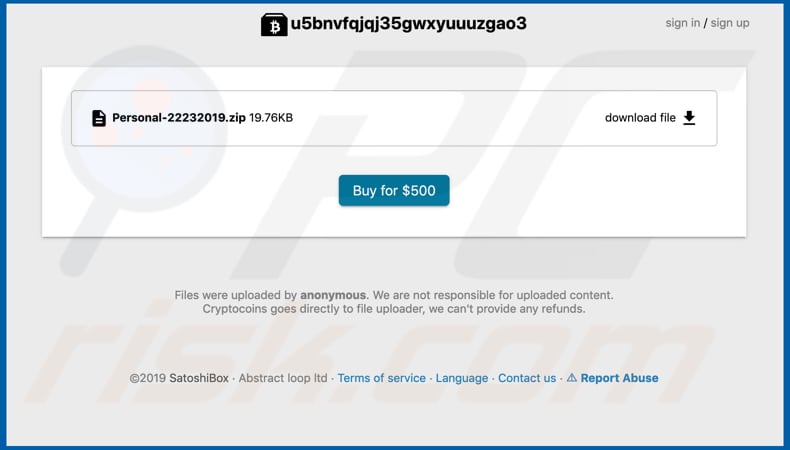
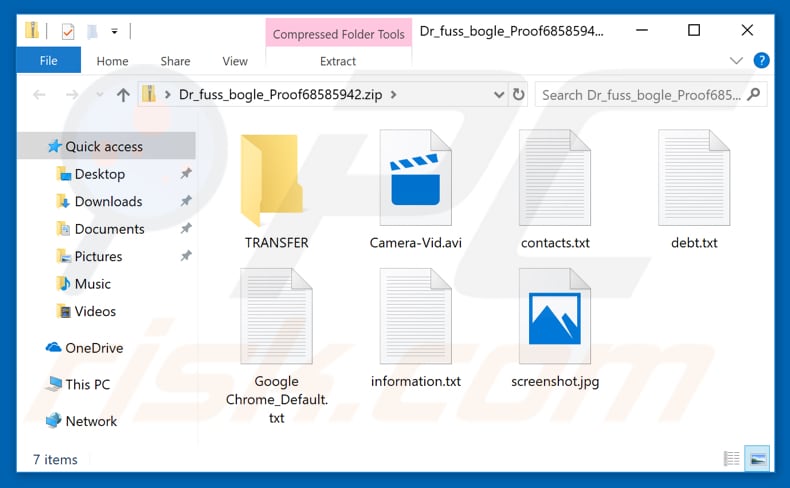
Additionally, the emails contain attachments (archive files) that contain videos, photos, text files, and so on. These files are presented as 'proof' that scammers have access to the recipient's computer, however, these archives are password protected. To open/extract these files, people must first pay.
These scam emails contain web links that open Satoshibox or Cryptonator pages (as in the screenshots below) for making payments. We strongly recommend that you do not pay, since this is just another way to extort money from people.
| Name | Proof Attached Email Scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud |
| Fake Claim | Crooks claim that they have a humiliating video of the recipient "pleasuring him/her self". It is also said that they have access to recipient's personal data (contacts, certain accounts, etc.) |
| Cyber Criminal Cryptowallet Address (Bitcoin) | 16fSXe21QhnmhvZskmtrWnvoRWFbAeAVG3 (cyber criminals use different cryptowallet addresses for different variants of this spam campaign). |
| Ransom Amount | $310, $660 (price depends on spam campaign's variant). |
| Symptoms | Unauthorized online purchases, changed online account passwords, identity theft, illegal access of one's computer. |
| Distribution methods | Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled domains. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
There are many other scams of this type. Scammers generally use them to extort money from recipients in various ways. A number of other examples are "Electronic Materials Involving Underage Children", "This Account Was Recently Infected", and "Hey. It's me! Your Future Friend Or Enemy".
These emails should not be taken seriously - the best option is to simply ignore them. Note, however, that other scams are used to proliferate computer infections such as LokiBot, TrickBot, Emotet, AZORult, Adwind, and so on. The main purpose of these spam campaigns (emails) is to trick people into opening the attached file or website link that leads to it.
These attachments are usually Microsoft Office documents, archives such as ZIP, RAR, JavaScript files, executables (.exe files), PDF documents, and so on. Once opened, they download and install high-risk malicious programs that can steal personal data such as passwords, logins of banking and other accounts, proliferate other infections, and so on.
These computer infections might cause financial loss, various privacy/browsing safety issues, and other serious problems.
We receive a great deal of feedback from concerned users about this scam email. Here is the most popular question we receive:
Q: Hi pcrisk.com team, I received an email stating that my computer was hacked and they have a video of me. Now they are asking for a ransom in Bitcoins. I think this must be true because they listed my real name and password in the email. What should I do?
A: Do not worry about this email. Neither hackers nor cyber criminals have infiltrated/hacked your computer and there is no video of you watching pornography. Simply ignore the message and do not send any Bitcoins. Your email, name, and password was probably stolen from a compromised website such as Yahoo (these website breaches are common). If you are concerned, you can check if your accounts have been compromised by visiting the haveibeenpwned website.
How do spam campaigns infect computers?
Spam campaigns used to proliferate viruses cause damage only if the attached files are opened. If the attachment is a Microsoft Office document, once opened, it will demand permission to disable "Protected View" mode. Infected MS Office files can download and install malicious programs only when this mode is disabled.
Therefore, we strongly recommend that you never disable it. If the attachment is an archive file such as ZIP, RAR or other, then its contents will need to be extracted and opened, otherwise they will not be able to cause any damage. Remember, no attachment can install computer infections without first being opened.
How to avoid installation of malware?
Do not open attachments that are present in emails received from unknown or suspicious email addresses or if the email (subject) is irrelevant. The same applies to website links, since they usually lead to infected files.
Avoid downloading software from unofficial websites, using Peer-to-Peer networks (eMule, torrent clients, and so on), third party downloaders and other similar sources. The safest way to download software is to use official websites and direct links. Install (or download) software with care - check "Custom", "Advanced" and other similar download or installation setup options.
Opt-out of offers to install additional applications/programs and only then finish the process. Do not use third party software updaters - update software using tools or functions provided by official developers only. Do not activate paid software using 'cracking' tools, since these are illegal and are often used to proliferate computer infections.
MS Office 2010 and later releases include the "Protected View" mode, which is designed to prevent downloaded malicious attachments from proliferating viruses. Therefore, we recommend that you use newer versions of MS Office. Having reputable anti-spyware or anti-virus software installed and enabled is also good prevention.
If you have already opened malicious attachments, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
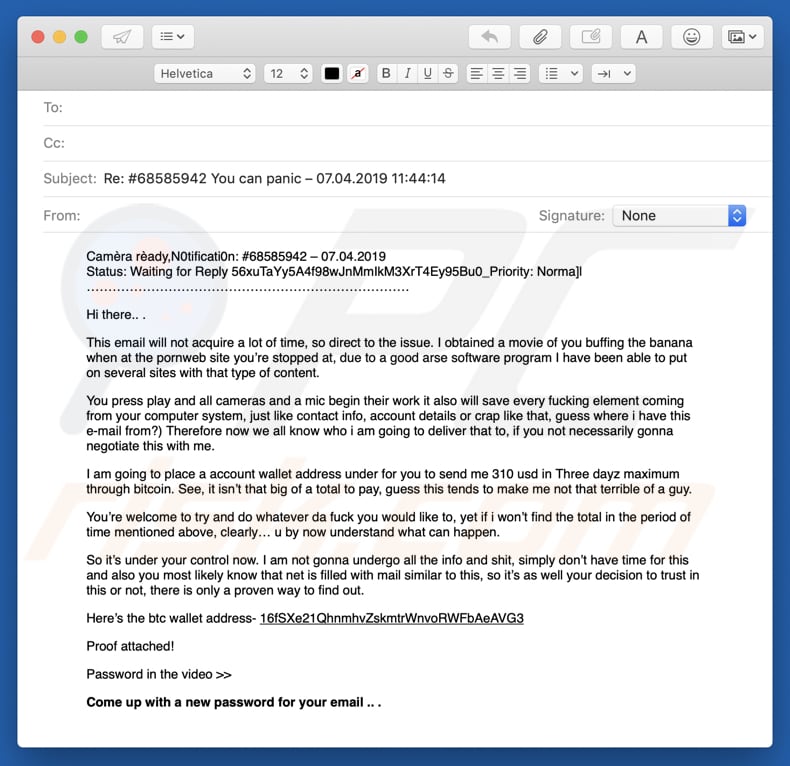
Text presented in the "Proof attached" email message (first variant):
Subject: Re: #68585942 You can panic ñ 07.04.2019 11:44:14
Attachment: Dr_fuss_bogle_Proof68585942.zip
Camèra rèady,N0tificati0n: #68585942 ñ 07.04.2019
Status: Waiting for Reply 56xuTaYy5A4f98wJnMmIkM3XrT4Ey95Bu0_Priority: Norma]lHi there.. .
This email will not acquire a lot of time, so direct to the issue. I obtained a movie of you buffing the banana when at the pornweb site youíre stopped at, due to a good arse software program I have been able to put on several sites with that type of content.
You press play and all cameras and a mic begin their work it also will save every fucking element coming from your computer system, just like contact info, account details or crap like that, guess where i have this e-mail from?) Therefore now we all know who i am going to deliver that to, if you not necessarily gonna negotiate this with me.
I am going to place a account wallet address under for you to send me 310 usd in Three dayz maximum through bitcoin. See, it isnít that big of a total to pay, guess this tends to make me not that terrible of a guy.
Youíre welcome to try and do whatever da fuck you would like to, yet if i wonít find the total in the period of time mentioned above, clearlyÖ u by now understand what can happen.
So itís under your control now. I am not gonna undergo all the info and shit, simply donít have time for this and also you most likely know that net is filled with mail similar to this, so itís as well your decision to trust in this or not, there is only a proven way to find out.
Hereís the btc wallet address- 16fSXe21QhnmhvZskmtrWnvoRWFbAeAVG3
Proof attached!
Password in the video >>
Come up with a new password for your email .. .
Screenshot of a second variant of "Proof attached scam":
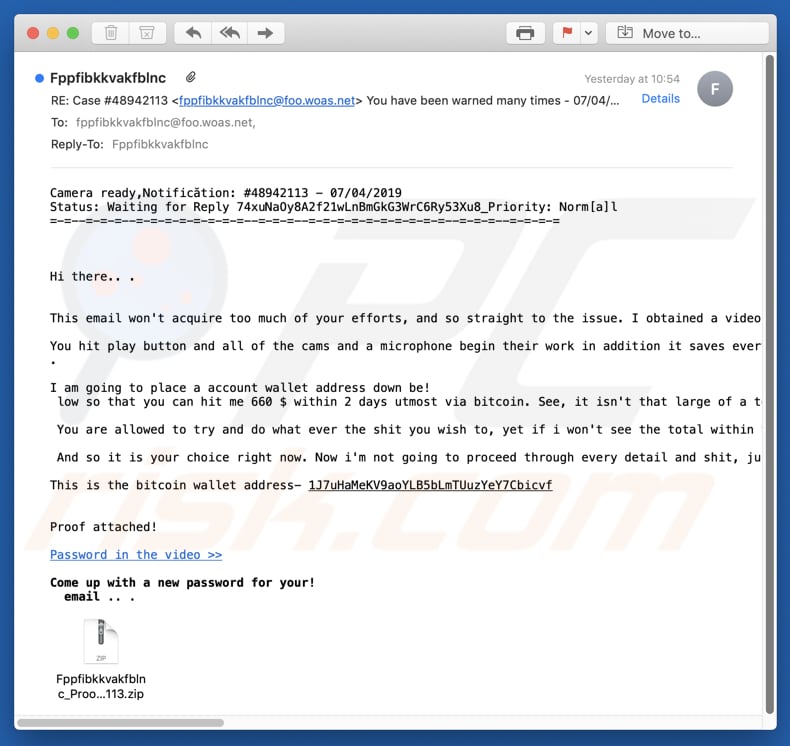
Text presented in the second variant of "Proof attached" scam:
Subject: Case #48942113 You have been warned many times - 07/04/2019 10:57:20
Camera ready,Notificition: #48942113 - 07/04/2019
Status: Waiting for Reply 74xuNaOy8A2f21wLnBmGkG3WrC6Ry53Xu8_Priority: Norm[a]l
=-=--=-=-=--=-=-=-=-=-=-=-=--=-=-=--=-=-=-=-=-=-=-=-=-=--=-=-=--=-=-=-=Hi there.. .
This email won't acquire too much of your efforts, and so straight to the issue. I obtained a video of you flogging the dolphin when at a pornpage you are visited, thanks to an incredible arse software program I've managed to put on a few web sites with that type of content.You hit play button and all of the cams and a microphone begin their work in addition it saves every fucking element through your pc, for example contact information, account details or shit such as that, guess just where i got this email address from?) Therefore now we all know just who i will deliver that to, if you aren't gonna negotiate this along with me.
I am going to place a account wallet address down be!
low so that you can hit me 660 $ within 2 days utmost via bitcoin. See, it isn't that large of a total to pay, guess that makes me not that terrible of a person.You are allowed to try and do what ever the shit you wish to, yet if i won't see the total within the period of time mentioned above, clearly... you already realize what will happen.
And so it is your choice right now. Now i'm not going to proceed through every detail and shit, just simply ain't got precious time for this and also you likely know that web is filled with mail such as this, therefore it is as well your decision to believe in this or not, there may be only one way to uncover.
This is the bitcoin wallet address- 1J7uHaMeKV9aoYLB5bLmTUuzYeY7Cbicvf
Proof attached!Password in the video >>
Come up with a new password for your!
email .. .
Cyber criminals attempt to sell the archive password via Cryptonator:
Screenshot of the files uploaded to Satoshibox:
Screenshot of the files in password-protected archive file (attachment):
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Proof Attached spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
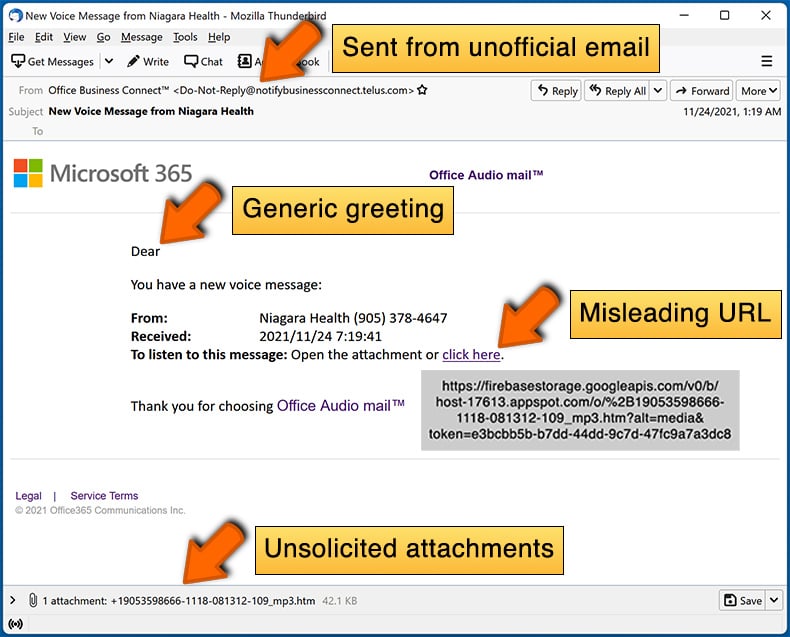
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion