Avoid being scammed by websites displaying "Firewall Spyware Alert"
Phishing/ScamAlso Known As: Firewall Spyware Alert tech support scam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is the "Firewall Spyware Alert"?
"Firewall Spyware Alert" is the name of a technical support scam, which is promoted through various untrusted sites. There are several versions of this online scheme, yet thematically they are identical. The primary differences are visual, and there are slight variations on the fake messages.
Essentially, these scams claim that users' devices have been infected with spyware and/or other viruses, and urge them to establish contact with the scammers by calling the provided telephone numbers. The "Firewall Spyware Alert" scam is disguised as an alert from Microsoft (or its products).
It must be emphasized that none of the information provided by this scheme is true, and it is in no way associated with the real Microsoft Corporation. Tech support scams aim to gain and subsequently abuse victims' trust in order to generate profit at their expense.
These schemes pose a serious threat to device and user safety. Typically, users enter deceptive websites via mistyped URLs, or redirects caused by intrusive advertisements or installed Potentially Unwanted Applications (PUAs).
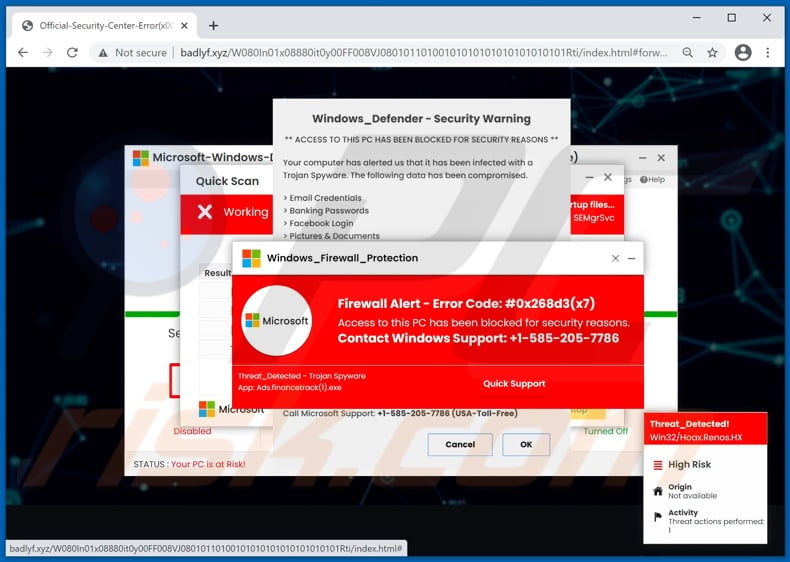
When users access web pages running the "Firewall Spyware Alert" scam, they are presented with multiple pop-up windows. The text in the pop-ups claims that the system has been infected with firewall/trojan spyware, and as a result the device is currently blocked.
The nonexistent threat can be specified as error "#0x268d3(x7)", "#x00082dfo09d", or something similar.
These windows can include brief infection/virus descriptions, results of fake system scams, potential threat lists (e.g., exposed email credentials, banking passwords, social media accounts, stored pictures and documents, etc.), and so on.
Throughout the messages, users are instructed to call the fake "helplines" in order to remove the alleged threats and recover access to their devices.
Technical support scams begin when the numbers they promote are called, yet how they progress from that point differs. The main source of revenue are the exorbitant fees for the scammers' "services". Typically, they attempt to gain remote access to the victims' devices.
From then on, they can run fake system scans, perform bogus malware removal processes, uninstall genuine protection tools, install fraudulent anti-viruses (which require purchase), infect the system with real malware (e.g., trojans, ransomware, cryptominers, etc.), extract sensitive/private information, and so on.
Scammers often infiltrate Remote Access Trojans (RATs) into their victims' systems, through which they can ensure (potentially indefinite) remote access and control over the computers.
Vulnerable data can be extracted from the victims by tricking them into revealing it, entering the information into phishing websites (e.g., disguised as online banking log-in pages, fake payment gateways, etc.), or via data-stealing malware.
Information of interest includes (but is not limited to): names, addresses, telephone numbers, emails, various account/service/platform log-in credentials (i.e., IDs, usernames, and passwords), banking account details, credit card numbers, etc. Scammers usually ask the victims to pay in digital currencies (e.g., cryptocurrencies, pre-paid vouchers, gift cards, etc.), which are difficult/impossible to trace or refund.
In many cases, successfully scammed victims are targeted repeatedly.
To summarize, by trusting the "Firewall Spyware Alert" scam, users can experience system infections, severe privacy issues, significant financial losses, and even identity theft. Should it be impossible to close a scam web page, use Windows Task Manager to end the browser process.
Additionally, when browser are reopened, it is important not to restore the previous browsing session, as that will also reopen the deceptive website.
As mentioned, scam sites can be force-opened by PUAs infiltrated into the system. These applications can have dangerous functions in varied combinations. Adware-type PUAs run intrusive advertisement campaigns.
The delivered ads promote untrusted/malicious websites and stealthily download/install software when they are clicked. Other PUAs called browser hijackers modify browser settings and restrict/deny access to them to promote fake search engines.
The promoted web searchers usually cannot provide search results, and so they redirect to Google, Bing, Yahoo, and other legitimate search engines. Furthermore, most PUAs have data tracking capabilities.
They monitor browsing activity (browsing and search engine histories) and collect sensitive information extracted from it (IP addresses, geolocations, and personally identifiable details). The collected data is then monetized by selling to third-parties.
Therefore, to protect device and user safety, remove all suspicious applications and browser extensions/plug-ins immediately upon detection.
| Name | Firewall Spyware Alert tech support scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud |
| Fake Claim | Scam claims users devices have been infected and blocked. |
| Disguise | Alert from Microsoft |
| Tech Support Scammer Phone Number | +1-585-205-7786 and +1-888-308-5768 |
| Related Domains | badlyf[.]xyz |
| Detection Names (badlyf[.]xyz) | Fortinet (Phishing), Google Safebrowsing (Phishing), Kaspersky (Malware), SCUMWARE.org (Malware), Trustwave (Malicious), Full List Of Detections (VirusTotal) |
| Serving IP Address (badlyf[.]xyz) | 157.230.233.245 |
| Symptoms | Fake error messages, fake system warnings, pop-up errors, hoax computer scan. |
| Distribution methods | Compromised websites, rogue online pop-up ads, potentially unwanted applications. |
| Damage | Loss of sensitive private information, monetary loss, identity theft, possible malware infections. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
"McAfee Tollfree", "Code #007d3Cx0d", "Error Code: #0x564897", "Microsoft Security Essentials Alert", and "Suspicious Movement Distinguished On You IP" are some examples of other tech support scams. The internet is rife with misleading, deceptive, and malicious content.
Popular scam models are: warnings that the system is infected or at risk, alerts that an essential piece of software is outdated or missing, "amazing" offers and deals, fake prize giveaways and raffles, etc.
Regardless of what the schemes offer, promise, request, or demand, the end-goal is the same: to generate revenue for the scammers/cyber criminals behind them. Due to the prevalence of online scams, exercise caution when browsing.
How did potentially unwanted applications install on my computer?
Unwanted downloads and installations often occur when developers distribute PUAs by integrating them into the download/installation setups of other programs as "extra offers". This distribution method is known as "bundling". The offers can be declined in "Custom", "Advanced" and other similar settings of the setups (or by unticking certain checkboxes).
Many users fail to check and change these settings (or untick the checkboxes), thereby allowing PUAs to infiltrate together with the desired software.
PUAs are also downloaded and installed by clicking deceptive advertisements (usually on untrusted sites) that execute certain scripts.
How to avoid installation of potentially unwanted applications
You are advised to research all software before download/installation. Use only official and verified download channels. Unofficial and free file-hosting websites, Peer-to-Peer sharing networks (BitTorrent, Gnutella, eMule), and other third party downloaders commonly offer harmful and bundled content, and are therefore untrusted and should be avoided.
When downloading/installing, read the terms, study all possible options, use the "Custom/Advanced" settings and opt-out of additional apps, tools, features, and so on.
Intrusive advertisements typically seem legitimate, however, they can redirect to dubious and malicious sites (e.g. gambling, pornography, adult-dating, and many others). If you encounter ads or redirects of this kind, inspect the system and remove all dubious applications and browser extensions/plug-ins immediately.
Installed programs must be activated and updated with tools or implemented functions that are provided by the official developers. No other third party, unofficial tools should be used.
Note that it is illegal to activate licensed software with ‘cracking’ tools. Files and programs should be downloaded from official websites and via direct download links. Avoid third party installers and the tools/sources mentioned above.
Do not open website links or files in irrelevant emails that are received from unknown, suspicious addresses. These bogus emails are often disguised as official and important. Regularly, scan your computer with reputable, up-to-date antivirus or anti-spyware software.
If your computer is already infected with PUAs, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate them.
Text presented in the "Firewall Spyware Alert" scam:
Main pop-up:
Windows_Firewall_protection
Microsoft
Firewall Alert - Error Code: #0x268d3(x7)
Access to this PC has been blocked for security reasons.
Contact Windows Support: +1-585-205-7786
Threat_Detected - Trojan Spyware
App: Ads.financetrack(1).exe
[Quick Support] [Go Back Safety]
-------------------------
Background pop-ups:
1:
Microsoft-Windows-Defender-Alert : Call +1-585-205-7786 (USA-Toll-Free)
You Are Protected
Protection Updates: Current
Last Scan: Not available | Quick Scan
Licenses Used: 1 of 5 | Install on Another Device
Security Identity Performance Firewall
Disabled At Risk Optimized Turned Off
STATUS : Your PC is at Risk!
2:
Quick Scan
Done
Working
Scanning commonly infected areas and startup files...
C:Program FilesWindows_DefenderMSASCuiL.exe
Results Summary
[+] Total items scanned:
[+] Total security risks detected:
[+] Total security risks resolved:
Total security risks requiring attention:
Microsoft [Pause][Stop]
3:
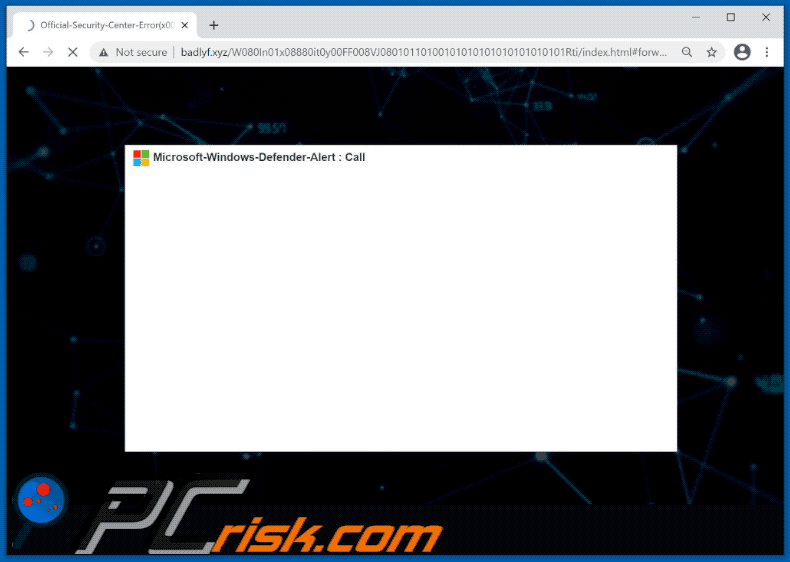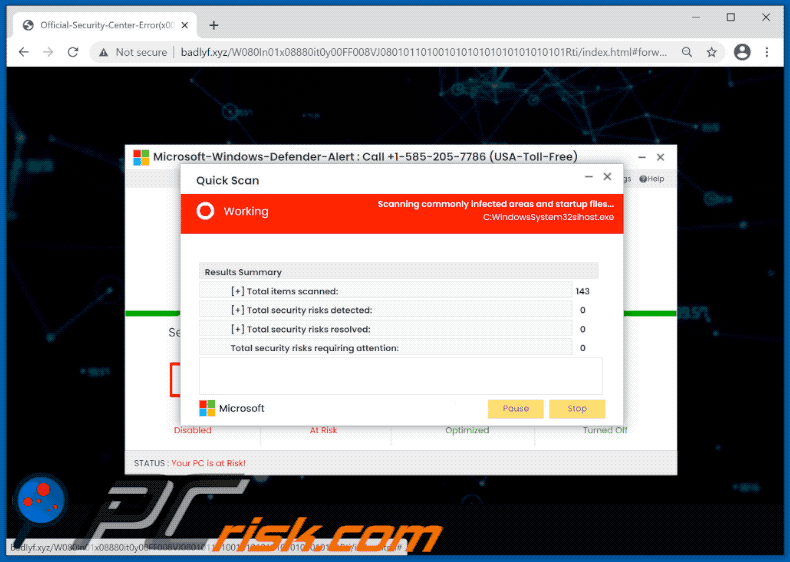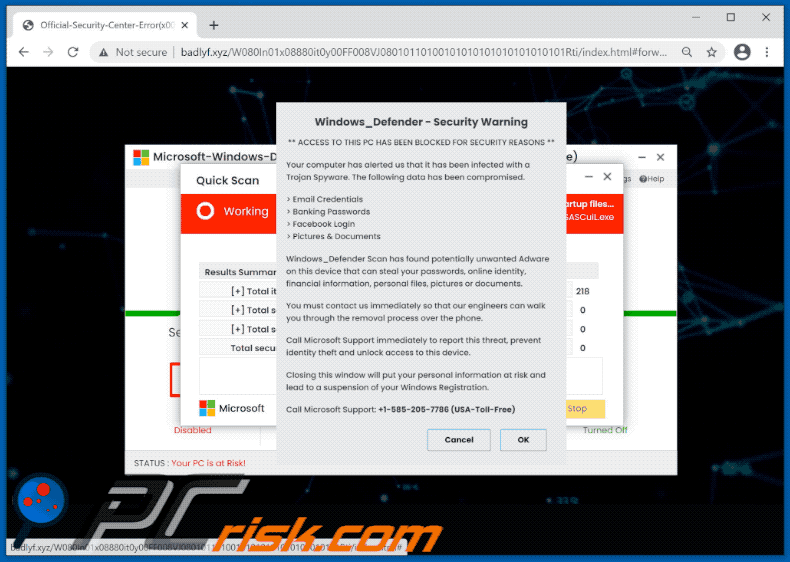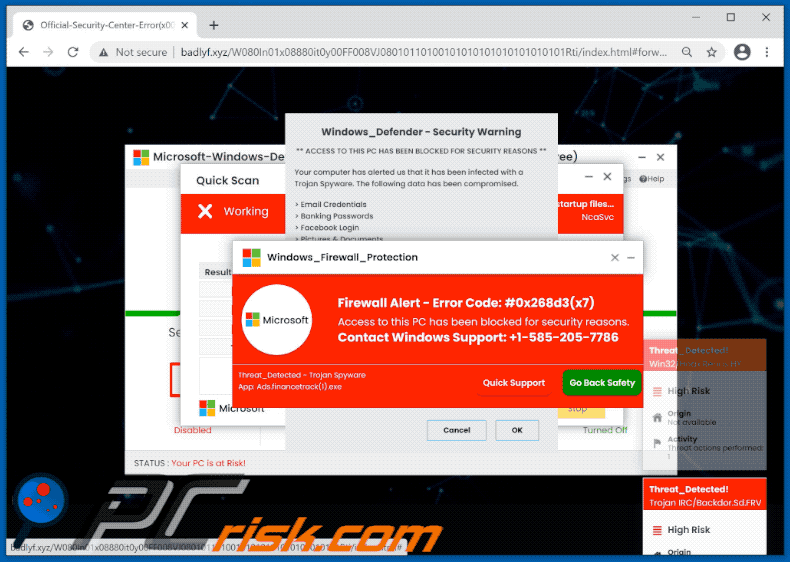
Windows_Defender - Security Warning
** ACCESS TO THIS PC HAS BEEN BLOCKED FOR SECURITY REASONS **
Your computer has alerted us that it has been infected with a Trojan Spyware. The following data has been compromised.
> Email Credentials
> Banking Passwords
> Facebook Login
> Pictures & Documents
Windows_Defender Scan has found potentially unwanted Adware on this device that can steal your passwords, online identity, financial information, personal files, pictures or documents.
You must contact us immediately so that our engineers can walk you through the removal process over the phone.
Call Microsoft Support immediately to report this threat, prevent identity theft and unlock access to this device.
Closing this window will put your personal information at risk and lead to a suspension of your Windows Registration.
Call Microsoft Support: +1-585-205-7786 (USA-Toll-Free)
[Cancel] [OK]
The appearance of "Firewall Spyware Alert" pop-up scam (GIF):
Screenshot of the "Firewall Spyware Alert" scam alternative variant:
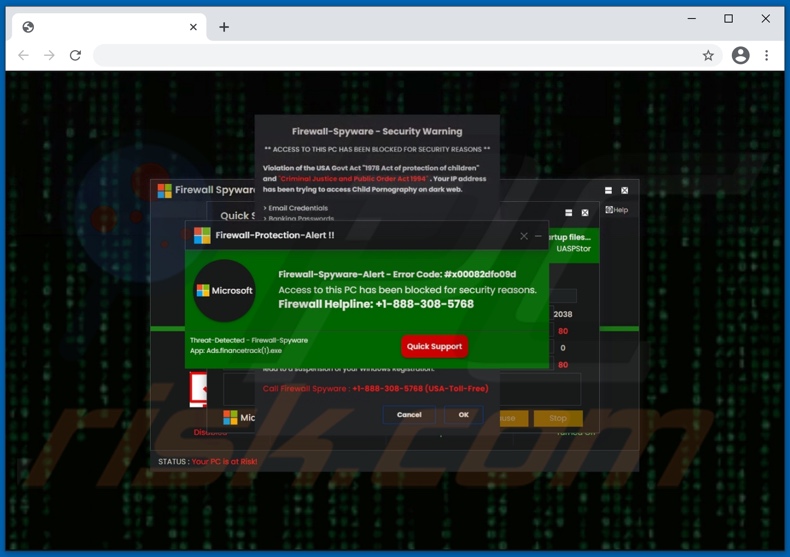
Text presented in this variant main pop-up window:
Firewall-Protection-Alert !!
Microsoft
Firewall-Spyware-Alert - Error Code: #x00082dfo09d
Access to this PC has been blocked for security reasons.
Firewall Helpline: +1-888-308-5768
Threat-Detected - Firewall-Spyware
App: Ads.financetrack(1).exe
[Quick Support]
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Firewall Spyware Alert tech support scam?
- How to identify a pop-up scam?
- How do pop-up scams work?
- How to remove fake pop-ups?
- How to prevent fake pop-ups?
- What to do if you fell for a pop-up scam?
How to identify a pop-up scam?
Pop-up windows with various fake messages are a common type of lures cybercriminals use. They collect sensitive personal data, trick Internet users into calling fake tech support numbers, subscribe to useless online services, invest in shady cryptocurrency schemes, etc.
While in the majority of cases these pop-ups don't infect users' devices with malware, they can cause direct monetary loss or could result in identity theft.
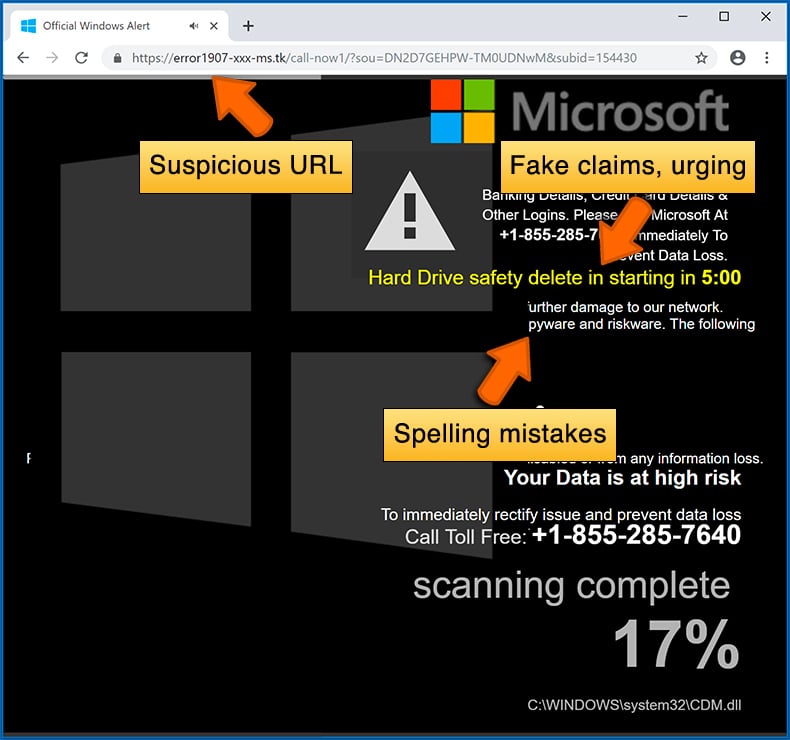
Cybercriminals strive to create their rogue pop-up windows to look trustworthy, however, scams typically have the following characteristics:
- Spelling mistakes and non-professional images - Closely inspect the information displayed in a pop-up. Spelling mistakes and unprofessional images could be a sign of a scam.
- Sense of urgency - Countdown timer with a couple of minutes on it, asking you to enter your personal information or subscribe to some online service.
- Statements that you won something - If you haven't participated in a lottery, online competition, etc., and you see a pop-up window stating that you won.
- Computer or mobile device scan - A pop-up window that scans your device and informs of detected issues - is undoubtedly a scam; webpages cannot perform such actions.
- Exclusivity - Pop-up windows stating that only you are given secret access to a financial scheme that can quickly make you rich.
Example of a pop-up scam:
How do pop-up scams work?
Cybercriminals and deceptive marketers usually use various advertising networks, search engine poisoning techniques, and shady websites to generate traffic to their pop-ups. Users land on their online lures after clicking on fake download buttons, using a torrent website, or simply clicking on an Internet search engine result.
Based on users' location and device information, they are presented with a scam pop-up. Lures presented in such pop-ups range from get-rich-quick schemes to fake virus scans.
How to remove fake pop-ups?
In most cases, pop-up scams do not infect users' devices with malware. If you encountered a scam pop-up, simply closing it should be enough. In some cases scam, pop-ups may be hard to close; in such cases - close your Internet browser and restart it.
In extremely rare cases, you might need to reset your Internet browser. For this, use our instructions explaining how to reset Internet browser settings.
How to prevent fake pop-ups?
To prevent seeing pop-up scams, you should visit only reputable websites. Torrent, Crack, free online movie streaming, YouTube video download, and other websites of similar reputation commonly redirect Internet users to pop-up scams.
To minimize the risk of encountering pop-up scams, you should keep your Internet browsers up-to-date and use reputable anti-malware application. For this purpose, we recommend Combo Cleaner Antivirus for Windows.
What to do if you fell for a pop-up scam?
This depends on the type of scam that you fell for. Most commonly, pop-up scams try to trick users into sending money, giving away personal information, or giving access to one's device.
- If you sent money to scammers: You should contact your financial institution and explain that you were scammed. If informed promptly, there's a chance to get your money back.
- If you gave away your personal information: You should change your passwords and enable two-factor authentication in all online services that you use. Visit Federal Trade Commission to report identity theft and get personalized recovery steps.
- If you let scammers connect to your device: You should scan your computer with reputable anti-malware (we recommend Combo Cleaner Antivirus for Windows) - cyber criminals could have planted trojans, keyloggers, and other malware, don't use your computer until removing possible threats.
- Help other Internet users: report Internet scams to Federal Trade Commission.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion