Avoid getting scammed by "Unfortunately there are bad news" spam email
Phishing/ScamAlso Known As: Unfortunately, There Are Some Bad News For You spam
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is "Unfortunately, there are some bad news for you" email scam?
"Unfortunately, there are some bad news for you" is the name of a sextortion spam campaign. The emails sent through this campaign claim that the sender has made a sexually explicit video featuring the recipient, and this recording will be publicized - unless the ransom demands are met.
It must be emphasized that this is a scam; hence, no compromising videos of the recipient exist, and all the other claims made by these letters are false.
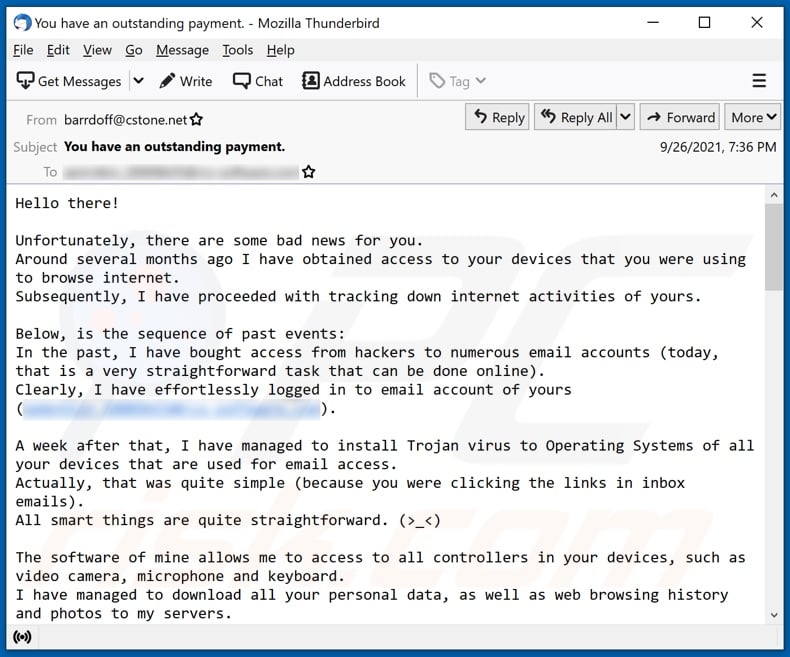
"Unfortunately, there are some bad news for you" email in detail
The "Unfortunately, there are some bad news for you" scam emails contain lengthy messages intended to trick the recipients into paying a ransom over a nonexistent video. The letters claim that the recipient's device was infected with malware several months ago, which allegedly allowed the sender access and control over the machine.
The emails state that the malware was used to record the recipient while they were visiting adult-oriented websites. Recipients are given two days to pay 1750 USD in Bitcoin cryptocurrency - else the explicit video will be shared with their contacts and leaked online.
As mentioned in the introduction, these emails are scams; they must simply be ignored as the letters pose no threat to the recipients.
| Name | Unfortunately, there are some bad news for you Email Scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud |
| Fake Claim | Scam emails claim that there is a compromising video of the recipient in the sender's possession, and unless a ransom is paid - the recording will be publicized. |
| Ransom Amount | 1750 USD in Bitcoin cryptocurrency |
| Cyber Criminal Cryptowallet Address (Bitcoin) | 3Cgq1LBwGg4n8Lx91qGcmv4a5nQ1rpBicK, 324M5a7SHLk6w14Y6imgNS2HszvZXEpWts, 3D3Es7Kh8FkCEYgEoM93fi5xx78PkyXikt, 38SLFfW65Ma2fyy4jyovkYnpXFLzc3Vvst, bc1qdtxpx79ck5xfd7xgmlguqc6frgw3rqyfehfvx2, 17Ga9z9f3HFBafsmMq76NVsVX5r1CzxhaP, bc1qu6c0sd9unfjdtxe8q3uj6yuh37veelmgg78exe, bc1qgq6s557g39lu3ys9twttmkxm5zhykw7rrlyk2n, 34oXnVoPfR8DCyaCQkmTTXtuHyKYLa9xkH, bc1q0etcl4a8gyew7774u3v7pfhyxef9u2dsvthm93, 1CW1kBHJsuS9zRj5qvpoAgEwDJQA3bUVPW, 1GtGZpzfRkAVBL48F68mi8bTcatwpTZGm8, bc1qypuk7gy4zpnsyztt49h3fehsc58xy53ja9kpvv, 17aB5wwDJ6EGdzzMgp3Y5deKCrqe7ga3qR, bc1qewfsx6pgjhnv3plk4vjem5ne0q3gh9af6ty7wn, 1LJsS3xXPx6Qsp9W2Vt9io3wAn5NmCcqbp, 16RrKqp6gvepFSBMTcoVzdJZ1NSbA7PjZA, 1ELed4R6FhJEL5pQQzP6PM9wFQbvHjuZng, 15PjLxvFvVuUASkWLTReBDf1SAnGboiE3Q, 1L1VmEatFZZSdU2DYD3JnS9RtpzXdPGmLZ, 18KX7w8j8ryEefqQK9cNB5ArjnBtG5giZM, 1AXBHuEiGvryS2HkM2tSPFnDDqt92sC8DM, bc1qq85lm69h3z6wuatrtgzmzakzz2cdv6s3prxurr, 1CK41adce6KuM3UM2eySnzUyR9SAJnf4wu, 1QDgvdFPUvUdUMXYMm6eZg55cicyfYrmGs, 17uHKCWeRBuGEYw2ujLDZna3b7sfxwT2ij, bc1qje8je64ecgwh3aa37tjx3pdktfhp6wj5jh6heh, 114t3CxEdMqJSoJB1AgMMWejtdC8xn3ZUQ, 1Pp5DTCTRSzoFyaHbrSEWGDWZZRp3rMsWv, 1Lt2Ns6FEPTPHA6pENS1Rhym1KAt43FFUp, 1Q3bj3y63wqXPGcsXhiC9N1YbYhF5euBBY, 1B4h63LjY8ZZBLuk1r5s6HkeVRV5W6uRE2, bc1q5xq5xyecgxr8j3872a6w2ashl49l0szs0m4z2n, 17kmbhxxMsrFhmQNim1jbjD6AeBUQ2SbYp, 1HQWaFbMUvQqeRQsWzyX4HsAvzvhVLqZxL, 1C2ek9b57xdVY9rPUaUnczxN5vGjVS8EhA, 1pSw6eh5GoWtBrETzPbM36DGxc6Tes5Mp, 1JSrCb8fwX15475Jztt3yA7JWHXzzxTX9h, 1LrBGezKti4m2cov7CKuurLnCfQvjp2o1A, 1LV8rSHsXYQ9JWUM4LRAGywH8RA6DXH6A7, 1Mjt2xobFExdZBGfjTVDcgzJWQxRxoHBdA, 1771s891APz1wNKdn5fe3Vknmf5pN18cWu, 1Bg62SYMjRfcSVaUM9VoAcr8Fy6bX2qQbN, 1GvxuP9puQCMNQvEKuwNrLeGwp9LWV4822, 1LzA9kzQkGDTYSfbbLE8gK5RAJ5ke32ntC, 12vuAcRSYDWuGHEVNVtQaEjBCBevps3ZcE, 1EeaB9n9RKCsxbzzmVNNPbcu9Lrq89Bm4Y, 1PQfyHsqnU1mpQHgbgNsbAxDLw5u2mgqgb, 1Aohp9uhpReFfZirTimqD1LUYtZ2gpvBtP, 1kZ8v4CZ29izLdtacgkdsCkMU5P7uVqKJ, 19emozKjqs4dUv3JjsHSXtKPDcGYwW2e5X, 18QoRGdPTpu6wMVKjf8PA43ZXndAJfrHvM, 15kiZUAtEYRC3m5ZWo2DYkrCeGbj5fRhDN, 1EaTepwwBEDQhmHsjuwQtX5V3ZMnnTbnY8, 1P8zGx51BpyxEy5jBgr5ugoPXbSgyd7fpw, 1Dwi3dsfYEzbU3QDtjNC8DNfoaVNAcNRYC, 1BwDYXp1YCa2NLfGiF5Gfnkmgf61MqupHb, 1B5ic9iQpyafTEfWxHM4Xq6PkzbickrL8g, 13Hayv2eeuwHTcUNhZVeCJytdBQosoSwVq, 1FhTVkgUpVyWNRG8bJkgyJipEmoEtitZwd, 15KquhG7RGkyXvEVT1aXLgPt4qgBEVe8rN, 19PRxthVN1P9hsXcStqc2Kp8Yy4hXyXVau, 153tGcwGFcj33YXxtjvgnzCYW1FhcPo1CM, bc1qufltvvk9y59zc7eyhq9608tk08ze3e0rft39av, 1MW4maqRuqi62YiRNMaBiHT65WJJMEAvQw, 17YJKh4TNBDrgFKfbjbQHCGEmZH8uvFoVp, 1B33LTohL4pWrZsjSpzLYjZ6WorWkwnoGE, 1K8g3n8Z9t265pMYuhpKc8jfmPS6cY7Qcr, 18wgLNrXoSqtCDSiTuAgQs9gfojHeecSnN, 1M4bujoHX8TVpWw65zxNHKeDTHZXouZcpR, 1GvZB6bVDrt6ynaR9YEUSE1H2K8DzPLtmq, 14UTJBbtUsKxPtkf8WvGwWBpB4D6MmGqAk, 1YcRyyF4obSGLyh1QJ9jyxv67ksYmM2oc, 1Dgd4jfNiGPoRrRPNgwgw2vcr6TgNGJ2FB, 13jKLyAFhjVRiWyg1TTPVjweFBAyUyBiy8, 19U1xBf2UZeLfPkVh1Gu3WGHheYCzjsVxs, 1GL673KXwLGMDKcxJ2CqrgqJrxnUpokvai, 114vHR5SDqqX7DAtYcFe7hmCZD4Jsad3jH, 1JvFwMdSUWdkDiWWiNggzZEf8kY4JXRGbf, 1HTAhiza95JocaB3ZtXrv5qmGPkjpBECNa, 12gHyoR78pjHpfueWUYyMudnwNMc6NGEPY, 1KXiY1reDCotVXpYdar6zoNknqGAsi1WeG, bc1qagz7afujdtmuf06y6tk39t8cw7vlnptrxu2fre, 1McWWFd3eYwvm7v2Rj2jMmDZGFWyFRjZ4P, 1EfCwNrGgGbNAn4bKUX7XydSzFu4RHheC4, 1EV3qSyz4XKoZAWvB1eVSYqHyqCNRdv9i7, bc1qs87pnevg3dhm2s74dg04j9q7ge0ces9dmvuvdz, bc1qvje0spxuly7hepumvdzupekfxcc08jkfpzrvye |
| Symptoms | Unauthorized online purchases, changed online account passwords, identity theft, illegal access of the computer. |
| Distribution methods | Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled domains. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Spam campaigns in general
"This is the last reminder", "I am a programmer and hacked your computer 3 months ago", "I have e-mailed you from your account", and "Your cloud storage was compromised" are a couple examples of sextortion spam campaigns.
Deceptive emails use various scam models to gain and abuse user trust, e.g., notifications concerning recipients' email or other online accounts (used for phishing log-in credentials), fake lotteries and inheritances, letters relating to payments and bills, and so forth. Aside from phishing and other scams, spam mail is also used to proliferate malware (e.g., ransomware, trojans, cryptocurrency miners, etc.).
How do spam campaigns infect computers?
Systems are infected via virulent files distributed as attachments or download links in spam emails. These files can be in various formats, e.g., Microsoft Office and PDF documents, archives, executables, JavaScript, etc. When the files are opened - the infection chain is triggered.
For example, Microsoft Office documents execute malicious macro commands to infect systems. The process occurs the moment a document is opened in Microsoft Office versions released prior to 2010. This is prevented by the "Protected View" mode in later versions; instead, users can manually enable editing/content (i.e., macro commands). However, infectious documents may contain deceptive messages intended to lure users into enabling macros.
How to avoid installation of malware?
Suspect and irrelevant emails must not be opened, especially any attachments or links found in them. Additionally, it is advised to use Microsoft Office versions released after 2010.
Malware is also spread via dubious download channels (e.g., unofficial and freeware sites, Peer-to-Peer sharing networks, etc.), illegal activation ("cracking") tools, and fake updates. Therefore, it is important to always download from official/verified sources and activate/update programs with tools provided by genuine developers.
It is paramount to have a dependable anti-virus installed and kept updated. This software has to be used to perform regular system scans and to remove threats. If you've already opened malicious attachments, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the "Unfortunately, there are some bad news for you" scam email letter:
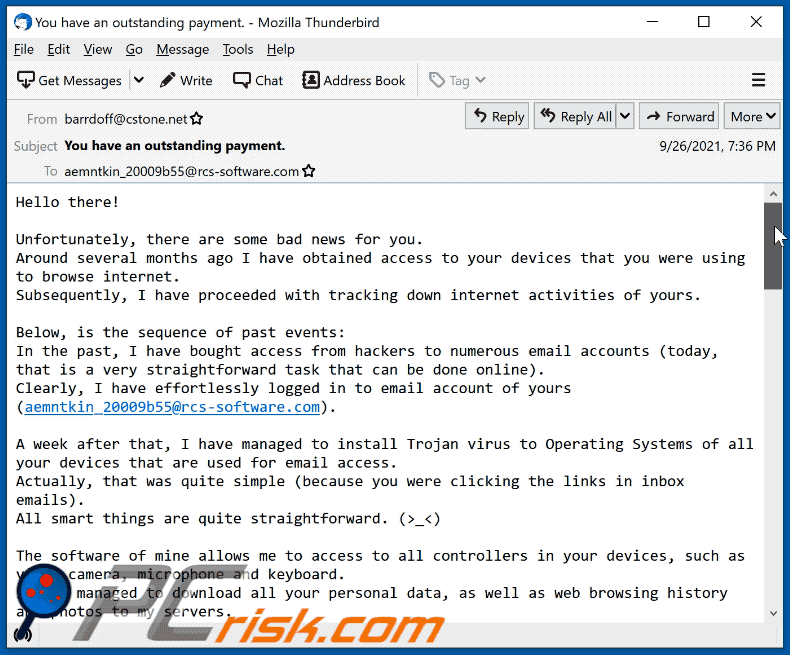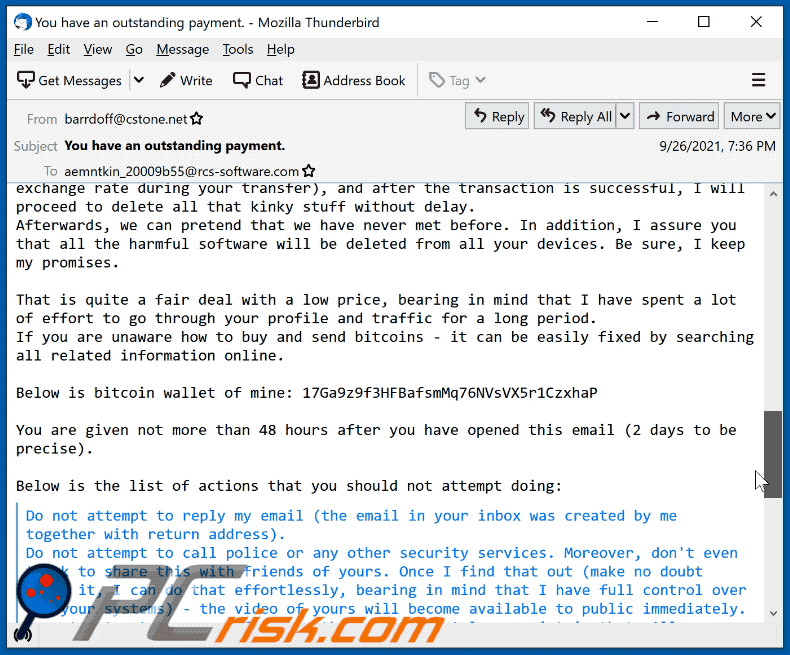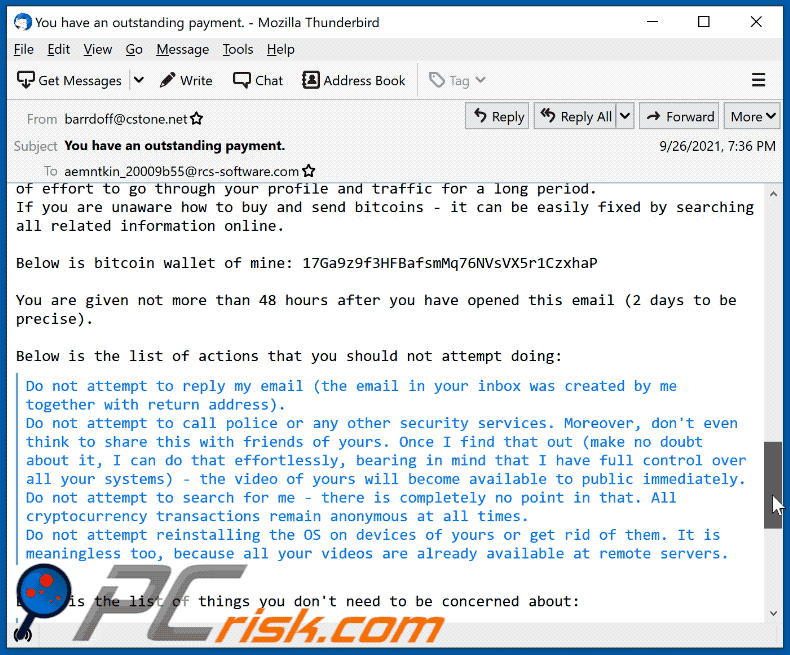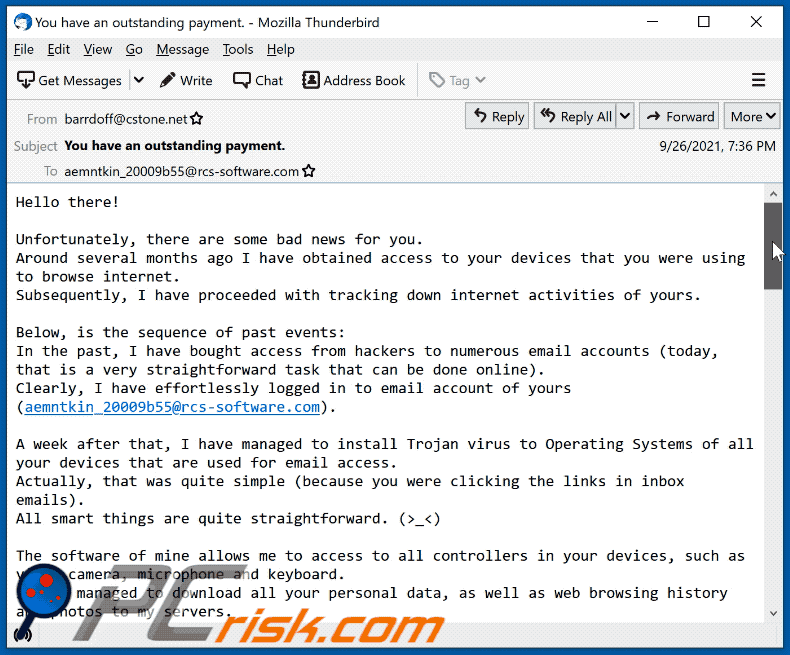
Subject: You have an outstanding payment.
Hello there!
Unfortunately, there are some bad news for you.
Around several months ago I have obtained access to your devices that you were using to browse internet.
Subsequently, I have proceeded with tracking down internet activities of yours.
Below, is the sequence of past events:
In the past, I have bought access from hackers to numerous email accounts (today, that is a very straightforward task that can be done online).
Clearly, I have effortlessly logged in to email account of yours (**********).
A week after that, I have managed to install Trojan virus to Operating Systems of all your devices that are used for email access.
Actually, that was quite simple (because you were clicking the links in inbox emails).
All smart things are quite straightforward. (>_<)
The software of mine allows me to access to all controllers in your devices, such as video camera, microphone and keyboard.
I have managed to download all your personal data, as well as web browsing history and photos to my servers.
I can access all messengers of yours, as well as emails, social networks, contacts list and even chat history.
My virus unceasingly refreshes its signatures (since it is driver-based), and hereby stays invisible for your antivirus.
So, by now you should already understand the reason why I remained unnoticed until this very moment...
While collecting your information, I have found out that you are also a huge fan of websites for adults.
You truly enjoy checking out porn websites and watching dirty videos, while having a lot of kinky fun.
I have recorded several kinky scenes of yours and montaged some videos, where you reach orgasms while passionately masturbating.
If you still doubt my serious intentions, it only takes couple mouse clicks to share your videos with your friends, relatives and even colleagues.
It is also not a problem for me to allow those vids for access of public as well.
I truly believe, you would not want this to occur, understanding how special are the videos you love watching, (you are clearly aware of that) all that stuff can result in a real disaster for you.
Let's resolve it like this:
All you need is $1750 USD transfer to my account (bitcoin equivalent based on exchange rate during your transfer), and after the transaction is successful, I will proceed to delete all that kinky stuff without delay.
Afterwards, we can pretend that we have never met before. In addition, I assure you that all the harmful software will be deleted from all your devices. Be sure, I keep my promises.
That is quite a fair deal with a low price, bearing in mind that I have spent a lot of effort to go through your profile and traffic for a long period.
If you are unaware how to buy and send bitcoins - it can be easily fixed by searching all related information online.
Below is bitcoin wallet of mine: 17Ga9z9f3HFBafsmMq76NVsVX5r1CzxhaP, 1B5ic9iQpyafTEfWxHM4Xq6PkzbickrL8g, 1P8zGx51BpyxEy5jBgr5ugoPXbSgyd7fpw, 12vuAcRSYDWuGHEVNVtQaEjBCBevps3ZcE, 1Dwi3dsfYEzbU3QDtjNC8DNfoaVNAcNRYC, 1PQfyHsqnU1mpQHgbgNsbAxDLw5u2mgqgb, 1BwDYXp1YCa2NLfGiF5Gfnkmgf61MqupHb, 13Hayv2eeuwHTcUNhZVeCJytdBQosoSwVq, 1FhTVkgUpVyWNRG8bJkgyJipEmoEtitZwd, 15KquhG7RGkyXvEVT1aXLgPt4qgBEVe8rN, 19PRxthVN1P9hsXcStqc2Kp8Yy4hXyXVau
You are given not more than 48 hours after you have opened this email (2 days to be precise).
Below is the list of actions that you should not attempt doing:
> Do not attempt to reply my email (the email in your inbox was created by me together with return address).
> Do not attempt to call police or any other security services. Moreover, don't even think to share this with friends of yours. Once I find that out (make no doubt about it, I can do that effortlessly, bearing in mind that I have full control over all your systems) - the video of yours will become available to public immediately.
> Do not attempt to search for me - there is completely no point in that. All cryptocurrency transactions remain anonymous at all times.
> Do not attempt reinstalling the OS on devices of yours or get rid of them. It is meaningless too, because all your videos are already available at remote servers.
Below is the list of things you don't need to be concerned about:
> That I will not receive the money you transferred.
- Don't you worry, I can still track it, after the transaction is successfully completed, because I still monitor all your activities (trojan virus of mine includes a remote-control option, just like TeamViewer).
> That I still will make your videos available to public after your money transfer is complete.
- Believe me, it is meaningless for me to keep on making your life complicated. If I indeed wanted to make it happen, it would happen long time ago!
Everything will be carried out based on fairness!
Before I forget...moving forward try not to get involved in this kind of situations anymore!
An advice from me - regularly change all the passwords to your accounts.
Appearance of the "Unfortunately, there are some bad news for you" scam email (GIF):
A German variant of "Unfortunately, There Are Some Bad News For You" scam email:
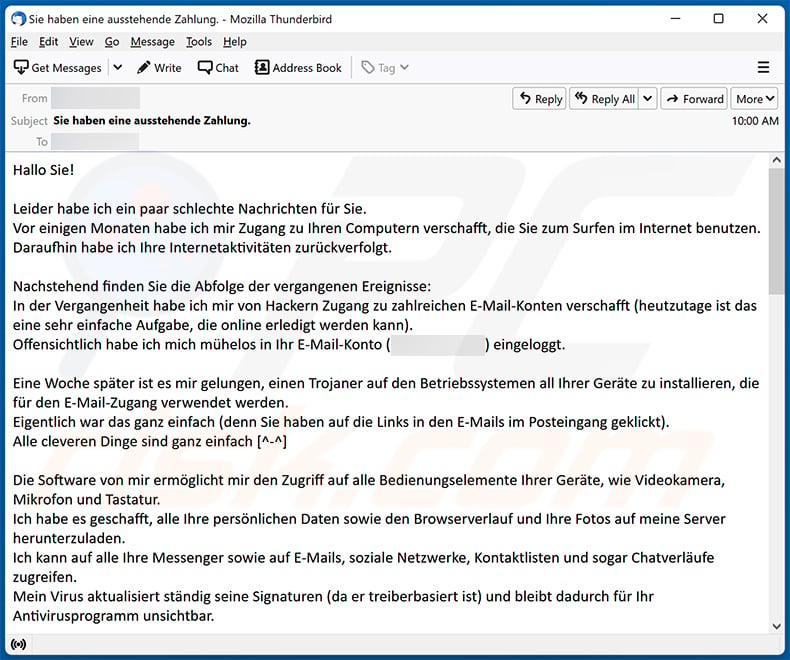
Text presented within:
Subject: Sie haben eine ausstehende Zahlung.
Hallo Sie!
Leider habe ich ein paar schlechte Nachrichten für Sie.
Vor einigen Monaten habe ich mir Zugang zu Ihren Computern verschafft, die Sie zum Surfen im Internet benutzen.
Daraufhin habe ich Ihre Internetaktivitäten zurückverfolgt.Nachstehend finden Sie die Abfolge der vergangenen Ereignisse:
In der Vergangenheit habe ich mir von Hackern Zugang zu zahlreichen E-Mail-Konten verschafft (heutzutage ist das eine sehr einfache Aufgabe, die online erledigt werden kann).
Offensichtlich habe ich mich mühelos in Ihr E-Mail-Konto (********) eingeloggt.Eine Woche später ist es mir gelungen, einen Trojaner auf den Betriebssystemen all Ihrer Geräte zu installieren, die für den E-Mail-Zugang verwendet werden.
Eigentlich war das ganz einfach (denn Sie haben auf die Links in den E-Mails im Posteingang geklickt).
Alle cleveren Dinge sind ganz einfach [^-^]Die Software von mir ermöglicht mir den Zugriff auf alle Bedienungselemente Ihrer Geräte, wie Videokamera, Mikrofon und Tastatur.
Ich habe es geschafft, alle Ihre persönlichen Daten sowie den Browserverlauf und Ihre Fotos auf meine Server herunterzuladen.
Ich kann auf alle Ihre Messenger sowie auf E-Mails, soziale Netzwerke, Kontaktlisten und sogar Chatverläufe zugreifen.
Mein Virus aktualisiert ständig seine Signaturen (da er treiberbasiert ist) und bleibt dadurch für Ihr Antivirusprogramm unsichtbar.Jetzt sollten Sie bereits den Grund verstehen, warum ich bis zu diesem Moment unbemerkt blieb...
Beim Sammeln Ihrer Informationen habe ich herausgefunden, dass Sie auch ein großer Fan von Webseiten für Erwachsene sind.
Sie schauen sich gerne Pornoseiten an und sehen sich versaute Videos an und haben dabei jede Menge versauten Spaß.
Ich habe mehrere perverse Szenen von Ihnen aufgenommen und einige Videos montiert, in denen Sie beim leidenschaftlichen Masturbieren zum Orgasmus kommen.Wenn Sie immer noch an meinen ernsthaften Absichten zweifeln, ist es nur ein paar Mausklicks entfernt, Ihre Videos mit Ihren Freunden, Verwandten und sogar Kollegen zu teilen.
Es ist auch kein Problem für mich, diese Videos auch für die Öffentlichkeit zugänglich zu machen.
Ich denke, dass Sie das nicht wollen, denn Sie wissen, wie besonders die von Ihnen geschauten Videos sind (Sie sind sich dessen bewusst), und all das kann für Sie zu einer echten Katastrophe führen.Lassen Sie uns das folgendermaßen lösen:
Alles, was Sie brauchen, ist eine Überweisung von 1800€ auf mein Konto (in Bitcoin, je nach dessen Wechselkurs während der Überweisung),
und nachdem die Transaktion erfolgreich war, werde ich das ganze perverse Zeug ohne Verzögerung löschen.
Danach können wir so tun, als ob wir uns nie zuvor getroffen hätten. Außerdem versichere ich Ihnen, dass die gesamte Schadsoftware von allen Ihren Geräten gelöscht wird. Seien Sie sicher, ich halte meine Versprechen.Das ist ein ziemlich fairer Deal mit einem niedrigen Preis, bedenkt man, dass ich mir viel Mühe gegeben habe, Ihr Profil und Ihren Datenverkehr über einen langen Zeitraum hinweg zu überprüfen.
Wenn Sie nicht wissen, wie man Bitcoins kauft und verschickt - lässt sich leicht beheben, indem Sie alle entsprechenden Informationen online suchen.Unten ist meine Bitcoin-Wallet: 1CW1kBHJsuS9zRj5qvpoAgEwDJQA3bUVPW
Sie haben nicht mehr als 48 Stunden Zeit, nachdem Sie diese E-Mail geöffnet haben (2 Tage, um genau zu sein).
Im Folgenden finden Sie eine Liste von Aktionen, die Sie nicht durchführen sollten:
*Versuchen Sie nicht, auf meine E-Mail zu antworten (die E-Mail in Ihrem Posteingang wurde von mir zusammen mit der Absenderadresse erstellt).
*Versuchen Sie nicht, die Polizei oder einen anderen Sicherheitsdienst anzurufen. Und denken Sie nicht einmal daran, dies Ihren Freunden mitzuteilen.
Sobald ich das herausfinde (Ich kann das ohne Zweifel mühelos tun, wenn man bedenkt, dass ich die volle Kontrolle über alle Ihre Systeme habe), wird das Video von Ihnen sofort öffentlich zugänglich sein.
*Versuchen Sie nicht, nach mir zu suchen - das ist völlig sinnlos. Alle Kryptowährungstransaktionen bleiben zu jeder Zeit anonym.
*Versuchen Sie nicht, das Betriebssystem auf Ihren Geräten neu zu installieren oder sie loszuwerden. Es ist auch sinnlos, weil alle Ihre Videos bereits auf entfernten Servern verfügbar sind.Im Folgenden finden Sie eine Liste von Dingen, über die Sie sich keine Gedanken machen müssen:
*Dass ich das von Ihnen überwiesene Geld nicht erhalten werde.
- Keine Sorge, ich kann es auch nach erfolgreicher Transaktion noch zurückverfolgen, denn ich überwache weiterhin alle Ihre Aktivitäten (mein Trojanervirus enthält eine Fernsteuerungsoption, genau wie TeamViewer).
*Dass ich Ihre Videos auch nach Abschluss des Geldtransfers noch öffentlich zugänglich machen werde.
- Glauben Sie mir, es ist sinnlos, wenn ich Ihnen das Leben weiterhin schwer mache. Wenn ich das wirklich wollte, wäre es schon längst geschehen!Alles wird auf der Grundlage der Fairness durchgeführt!
Bevor ich es vergesse...versuchen Sie in Zukunft, sich nicht mehr auf solche Situationen einzulassen!
Ein Rat von mir - ändern Sie regelmäßig alle Passwörter zu Ihren Konten.
Another variant of "Unfortunately, There Are Some Bad News For You" spam email:
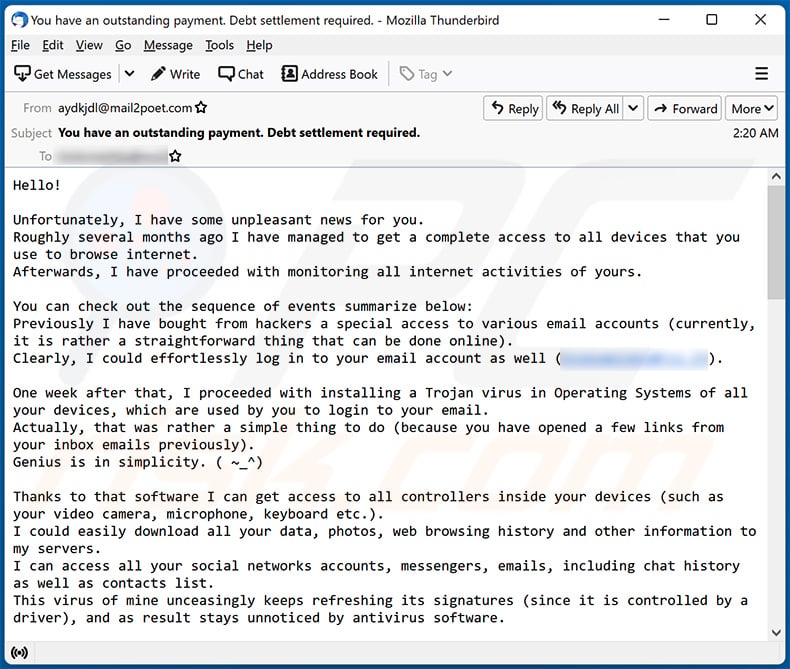
Text presented within:
Subject: You have an outstanding payment. Debt settlement required.
Hello!
Unfortunately, I have some unpleasant news for you.
Roughly several months ago I have managed to get a complete access to all devices that you use to browse internet.
Afterwards, I have proceeded with monitoring all internet activities of yours.You can check out the sequence of events summarize below:
Previously I have bought from hackers a special access to various email accounts (currently, it is rather a straightforward thing that can be done online).
Clearly, I could effortlessly log in to your email account as well (********).One week after that, I proceeded with installing a Trojan virus in Operating Systems of all your devices, which are used by you to login to your email.
Actually, that was rather a simple thing to do (because you have opened a few links from your inbox emails previously).
Genius is in simplicity. ( ~_^)Thanks to that software I can get access to all controllers inside your devices (such as your video camera, microphone, keyboard etc.).
I could easily download all your data, photos, web browsing history and other information to my servers.
I can access all your social networks accounts, messengers, emails, including chat history as well as contacts list.
This virus of mine unceasingly keeps refreshing its signatures (since it is controlled by a driver), and as result stays unnoticed by antivirus software.Hereby, I believe by this time it is already clear for you why I was never detected until I sent this letter...
While compiling all the information related to you, I have also found out that you are a true fan and frequent visitor of adult websites.
You truly enjoy browsing through porn websites, while watching arousing videos and experiencing an unimaginable satisfaction.
To be honest, I could not resist but to record some of your kinky solo sessions and compiled them in several videos, which demonstrate you masturbating and cumming in the end.If you still don't trust me, all it takes me is several mouse clicks to distribute all those videos with your colleagues, friends and even relatives.
In addition, I can upload them online for entire public to access.
I truly believe, you absolutely don't want such things to occur, bearing in mind the kinky stuff exposed in those videos that you usually watch, (you definitely understand what I am trying to say) it will result in a complete disaster for you.We can still resolve it in the following manner:
You perform a transfer of $1590 USD to me (a bitcoin equivalent based on the exchange rate during the funds transfer), so after I receive the transfer, I will straight away remove all those lecherous videos without hesitation.
Then we can pretend like it has never happened before. In addition, I assure that all the harmful software will be deactivated and removed from all devices of yours. Don't worry, I am a man of my word.It is really a good deal with a considerably low the price, bearing in mind that I was monitoring your profile as well as traffic over an extended period.
If you still unaware about the purchase and transfer process of bitcoins - all you can do is find the necessary information online.My bitcoin wallet is as follows: 1MW4maqRuqi62YiRNMaBiHT65WJJMEAvQw, 1Bg62SYMjRfcSVaUM9VoAcr8Fy6bX2qQbN, 1GvxuP9puQCMNQvEKuwNrLeGwp9LWV4822, 1LzA9kzQkGDTYSfbbLE8gK5RAJ5ke32ntC
You are left with 48 hours and the countdown starts right after you open this email (2 days to be specific).
Don't forget to keep in mind and abstain from doing the following:
> Do not attempt to reply my email (this email was generated in your inbox together with the return address).
> Do not attempt to call police as well as other security services. Moreover, don't even think of sharing it with your friends. If I get to know about it (based on my skills, that would be very easy, since that I have all your systems under my control and constant monitoring) - your dirty video will become public without delay.
> Don't attempt searching for me - it is completely useless. Cryptocurrency transactions always remain anonymous.
> Don't attempt reinstalling the OS of your devices or even getting rid of them. It is meaningless too, because all your private videos are already been available on remote servers.Things you should be concerned about:
> That I will not receive the funds transfer you make.
Relax, I will be able to track it immediately, after you complete the funds transfer, because I unceasingly monitor all activities that you do (trojan virus of mine can control remotely all processes, same as TeamViewer).
> That I will still distribute your videos after you have sent the money to me.
Believe me, it is pointless for me to proceed with troubling you after that. Besides that, if that really was my intention, it would happen long time ago!It all will be settled on fair conditions and terms!
One last advice from me... Moving forward make sure you don't get involved in such type of incidents again!
My suggestion - make sure you change all your passwords as often as possible.
A Spanish variant of "Unfortunately, There Are Some Bad News For You" email scam:
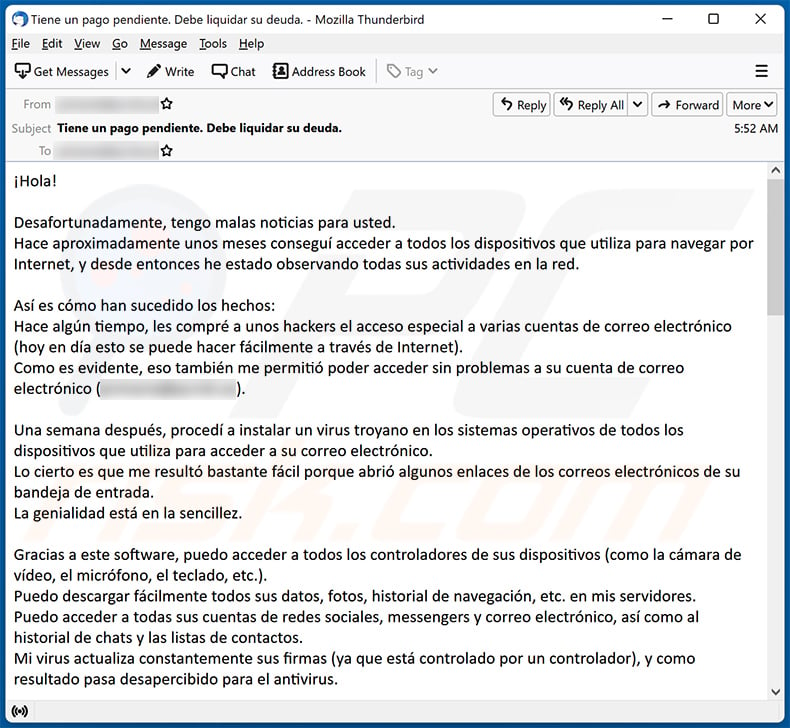
Text presented within:
Subject: Tiene un pago pendiente. Debe liquidar su deuda.
¡Hola!Desafortunadamente, tengo malas noticias para usted.
Hace aproximadamente unos meses conseguí acceder a todos los dispositivos que utiliza para navegar por Internet, y desde entonces he estado observando todas sus actividades en la red.Así es cómo han sucedido los hechos:
Hace algún tiempo, les compré a unos hackers el acceso especial a varias cuentas de correo electrónico (hoy en día esto se puede hacer fácilmente a través de Internet).
Como es evidente, eso también me permitió poder acceder sin problemas a su cuenta de correo electrónico (*********).Una semana después, procedí a instalar un virus troyano en los sistemas operativos de todos los dispositivos que utiliza para acceder a su correo electrónico.
Lo cierto es que me resultó bastante fácil porque abrió algunos enlaces de los correos electrónicos de su bandeja de entrada.
La genialidad está en la sencillez.Gracias a este software, puedo acceder a todos los controladores de sus dispositivos (como la cámara de vídeo, el micrófono, el teclado, etc.).
Puedo descargar fácilmente todos sus datos, fotos, historial de navegación, etc. en mis servidores.
Puedo acceder a todas sus cuentas de redes sociales, messengers y correo electrónico, así como al historial de chats y las listas de contactos.
Mi virus actualiza constantemente sus firmas (ya que está controlado por un controlador), y como resultado pasa desapercibido para el antivirus.Así que a estas alturas ya entenderá por qué nunca me ha detectado hasta recibir este correo...
Gracias a la información que he recopilado sobre usted, he descubierto que le encantan los sitios web para adultos y que los visita con frecuencia.
Está claro que disfruta mucho navegando por páginas porno y viendo vídeos muy excitantes que le producen una satisfacción inimaginable.
Sinceramente, no he podido resistirme a grabar algunas de sus pervertidas sesiones en solitario y las he recopilado en varios vídeos,
en los que aparece masturbándose y corriéndose al final.Por si aún duda de mi palabra, debe saber que con solo unos clics de ratón podría distribuir todos esos vídeos a sus compañeros, amigos e incluso familiares.
Además, puedo subirlos a Internet para que cualquiera pueda acceder a ellos.
Estoy seguro de que lo último que querrá es que ocurra algo así, teniendo en cuenta las cosas tan pervertidas que aparecen en los vídeos que suele ver
(seguro que ya me entiende), ya que sería un completo desastre para usted.Sin embargo, podemos solucionarlo de la siguiente manera:
Me hará una transferencia de 1390€ (el equivalente en bitcoins según el tipo de cambio en el momento de la transferencia),
y cuando reciba la transferencia, eliminaré inmediatamente todos esos vídeos lascivos sin dudarlo.
Y después podremos fingir que nada de esto ha sucedido nunca. Además, le garantizo que desactivaré y eliminaré todo el software dañino de todos sus dispositivos.
No se preocupe, soy un hombre de palabra.En realidad es un buen trato y por muy poco dinero, sobre todo teniendo en cuenta todo el tiempo que he estado vigilando su perfil y su tráfico.
Si todavía no conoce el proceso de compra y transferencia de bitcoins, podrá encontrar toda la información necesaria en Internet.Mi monedero bitcoin es el siguiente: 1YcRyyF4obSGLyh1QJ9jyxv67ksYmM2oc
Tiene 48 horas, y la cuenta atrás comienza justo después de abrir este correo electrónico (2 días para ser exactos).
No olvide tener en cuenta y abstenerse de hacer lo siguiente:
> No intente responder a mi correo electrónico (este correo se ha generado en su bandeja de entrada junto con la dirección de respuesta).
> No intente llamar a la policía ni a otros servicios de seguridad. Es más, ni se le ocurra contárselo a sus amigos. Si lo descubro (dadas mis habilidades me resultaría muy fácil,
ya que controlo y vigilo todos sus sistemas constantemente), publicaré inmediatamente el vídeo en el que sale haciendo cochinadas.
> No intente localizarme, sería completamente inútil. Las transacciones de criptomonedas siempre son anónimas.
> No intente reinstalar el sistema operativo de sus dispositivos ni deshacerse de ellos. No tendría sentido, puesto todos sus vídeos privados ya están guardados en servidores remotos.Cosas que pueden preocuparle:
> Que yo no reciba el dinero que me ha transferido.
Tranquilo, podré rastrear la transferencia en cuanto la haga, ya que monitorizo incesantemente todas sus actividades
(mi virus troyano puede controlar remotamente todos los procesos, igual que TeamViewer).
> Que siga distribuyendo sus vídeos después de haberme enviado el dinero.
Créame, no me interesa seguir causándole molestias una vez que reciba el dinero. Además, si esa fuera mi intención, ¡lo habría hecho hace mucho tiempo!¡Solucionaremos esto de manera justa!
Un último consejo de mi parte... En adelante, ¡asegúrese de no volver a verse envuelto en este tipo de incidentes!
Le recomiendo que cambie todas sus contraseñas tan a menudo como sea posible.
Yet another example of an email from this spam campaign:
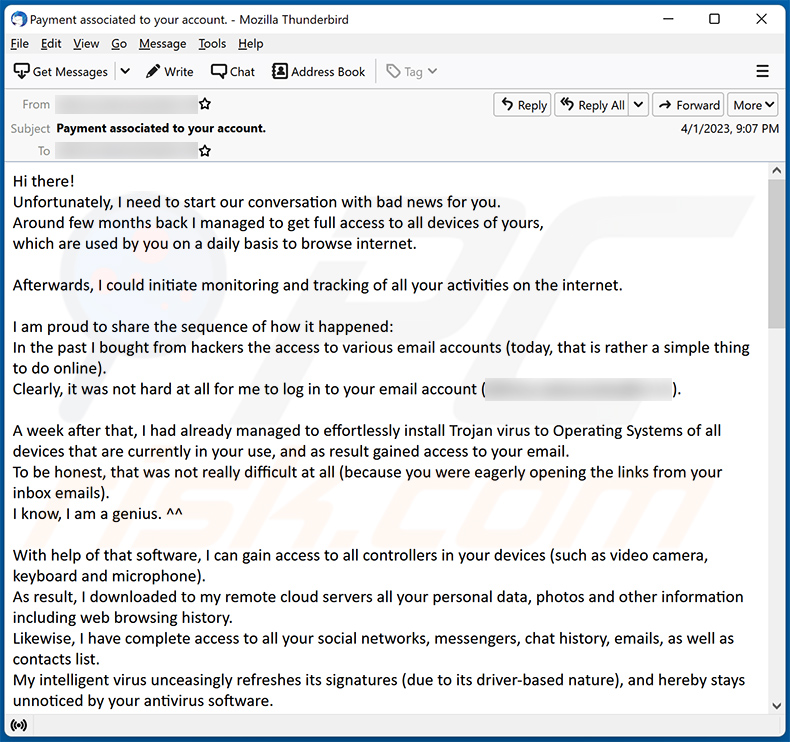
Text presented within:
Subject: Payment associated to your account.
Hi there!
Unfortunately, I need to start our conversation with bad news for you.
Around few months back I managed to get full access to all devices of yours,
which are used by you on a daily basis to browse internet.Afterwards, I could initiate monitoring and tracking of all your activities on the internet.
I am proud to share the sequence of how it happened:
In the past I bought from hackers the access to various email accounts (today, that is rather a simple thing to do online).
Clearly, it was not hard at all for me to log in to your email account (********).A week after that, I had already managed to effortlessly install Trojan virus to Operating Systems of all devices that are currently in your use, and as result gained access to your email.
To be honest, that was not really difficult at all (because you were eagerly opening the links from your inbox emails).
I know, I am a genius. ^^With help of that software, I can gain access to all controllers in your devices (such as video camera, keyboard and microphone).
As result, I downloaded to my remote cloud servers all your personal data, photos and other information including web browsing history.
Likewise, I have complete access to all your social networks, messengers, chat history, emails, as well as contacts list.
My intelligent virus unceasingly refreshes its signatures (due to its driver-based nature), and hereby stays unnoticed by your antivirus software.Herbey, I believe that now you finally start realizing how I could easily remain unnoticed all this while until this very letter...
While collecting information related to you, I had also unveiled that you are a true fan of porn sites.
You truly enjoy browsing through adult sites and watching horny vids, while playing your dirty solo games.Bingo! I also recorded several filthy scenes with you in the main focus and montaged some dirty videos, which demonstrate your passionate masturbation and cum sessions.
In case you still don't believe me, all I need is just one-two mouse clicks to make all your unmasking videos become available to your friends, colleagues, and even relatives.
Well, if you still doubt me, I can easily make recorded videos of your orgasms become a public.
I truly believe that you surely would avoid that from happening,
taking in consideration the type of the XXX videos you love watching, (you are clearly aware of what I mean) it will result in a huge disaster for you.Well, there is still a way to settle this tricky situation in a peaceful manner:
You will need to transfer $960 USD to my account (refer to Bitcoin equivalent based on the exchange rate at the moment transfer),
so once funds transfer is complete, I will straight away proceed with deleting all that dirty content from servers once and for all.Afterwards, you can consider that we never met before. You have my honest word, that all the harmful software will also be deactivated and deleted from all your devices currently in use.
Worry not, I keep my promises.
That is truly a win-win solution that comes at a relatively reduced cost, mostly knowing how much effort I spent on monitoring your profile and traffic for a considerably long time.
In event that you have no idea about means of buying and transferring bitcoins – don't hesitate to use any search engine for your assistance (e.g., Google, Yahoo, Bing, etc.).My bitcoin wallet is as follows: 1Lt2Ns6FEPTPHA6pENS1Rhym1KAt43FFUp
I have allocated 48 hours for you to do that, and the timer started right after you opened this very email (2 days to be exact).
Don't even think of doing anything of the following:
*Abstain from attempting to reply me (this email was created by me inside your inbox page and the return address was generated accordingly).
*Abstain from attempting to get in touch with police or any other security services. Moreover, don't even think of sharing this to you friends.
Once I discover this (apparently, that is absolutely easy for me, taking in consideration that I have complete control over all systems you use) - your kinky video will straight away be made public.
*Don't even think of attempting to find me – that is completely useless. Don't forget that all cryptocurrency transactions remain completely anonymous.
*Don't attempt reinstalling the OS on all your devices or getting rid of them. That won't lead you to success either, because I have already saved all videos at my remote servers as a backup.Things you should not be concerned about:
*That your funds transfer won't reach my wallet.
- Worry not, I can see everything, hence after you finish the transfer, I will get a notification right away
(trojan virus of mine uses a remote-control feature, which functions similarly to TeamViewer).
*That I will still distribute your videos although you make the funds transfer.
- My word, I have no intention or interest in continuing making your life troublesome.
Anyway, If I truly wanted that, it would happen long time ago without me notifying you!Everything can be settled in a peaceful and just way!
And lastly... make sure you don't get caught afterwards in such type of incidents anymore!
My fair advice – ensure you change all your passwords on a regular basis.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Unfortunately, There Are Some Bad News For You spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
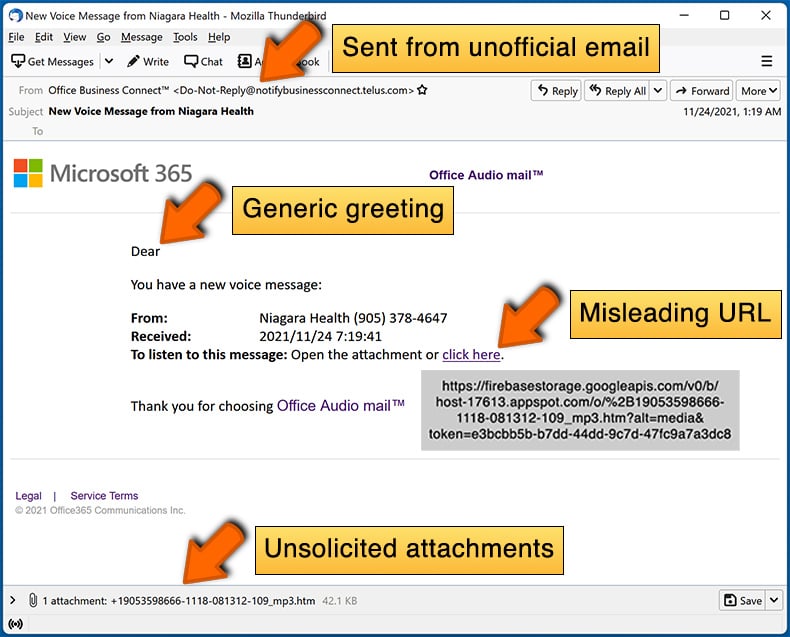
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Frequently Asked Questions (FAQ)
Why did I receive this email?
Spam emails are sent by the thousand with the hopes that someone will fall for them; they are not personal.
Was my computer actually hacked and does the sender have any information?
No, the "Unfortunately, there are some bad news for you" email is a scam, and none of its claims are true. That means that no videos of you exist in the scammer's possession, nor are your devices infected.
How did cyber criminals get my email password?
If you've received spam emails from your own email account, it is likely that you have fallen victim to a phishing scam at some point. Scams of this type operate by tricking victims to sign into their accounts (e.g., emails) through phishing sites or files disguised as log-in pages. Alternatively, cyber criminals may have gained your log-in credentials through a data breach.
I have sent cryptocurrency to the address presented in this email, can I get my money back?
No, as cryptocurrency transactions are practically untraceable and irreversible.
I have provided my personal information when tricked by a spam email, what should I do?
If you've provided account log-in credentials - immediately change the passwords of all potentially compromised accounts and contact their official support. If the disclosed information was of a different nature (e.g., ID card information, credit card numbers, etc.) - contact the appropriate authorities without delay.
I have read a spam email but didn't open the attachment, is my computer infected?
No, opening and reading spam emails will not result in a system infection. However, opening any attachments or clicking the links present in such letters - can trigger malware download/installation.
I have downloaded and opened a file attached to a spam email, is my computer infected?
Whether your system is infected - depends on the file's type. If the opened file was an executable - then, most likely, yes. However, you may have avoided jumpstarting a system infection if the file was a document (e.g., .doc, .pdf, etc.), since these files may require additional actions to begin infection processes.
Will Combo Cleaner remove malware infections present in email attachments?
Yes, Combo Cleaner is able to detect and eliminate nearly all known malware infections. Note that it is crucial to perform a full system scan since high-end malicious software tends to hide deep within the infected system.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion