Lebanese Internal Security Forces Virus
RansomwareAlso Known As: Lebanese Internal Security Forces Ransomware
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is Lebanese Internal Security Forces?
The Lebanese Internal Security Forces message demands payment of a $100 (100 Euro or 200,000 Lebanese pounds) fine in order to unblock your computer. This is a scam. This computer screen-blocking message is ransomware created by cyber criminals in order to extort money from unsuspecting PC users from Lebanon.
Computer users should be aware that no international authorities (including the Lebanese Internal Security Forces) use such messages to collect fines for any law violations. The deceptive message presented within this ransomware virus claims that computer users must pay the fine for using copyrighted files (music, videos, software) or for watching pornography.
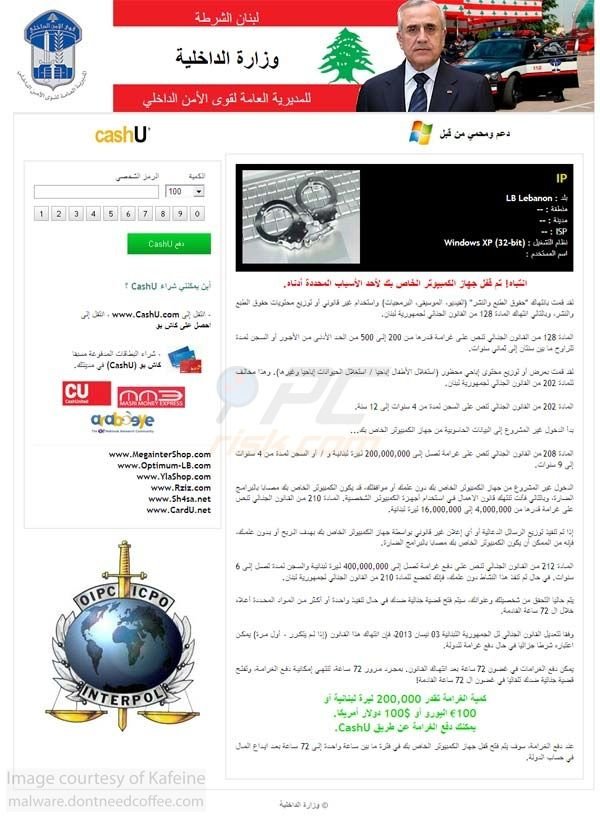
These claims are false - this deceptive message is not sent by any legitimate authorities. The main purpose of this screen locker is to steal money using chashU services. The ransomware virus originates from a family called Urausy and targets PC users predominantly from Lebanon.
These rogue messages, however, are localized and display variants (citing different authority names) from various countries. Localization is possible since ransomware viruses are capable of detecting the IP address of systems they infect.
For example, computer users from the USA see this message as if it sent by The ICE Cyber Crimes Center. The Lebanese Internal Security Forces screen-blocking message is not legitimate - do not trust it and do not pay any fines.
The Lebanese Internal Security Forces ransomware virus is distributed using exploit kits capable of detecting security vulnerabilities within users' computers, and then infecting them with malicious code. Common sources of exploit kits include email messages and malicious websites.
To protect your computer from these security threats, use legitimate antivirus and anti-spyware programs and keep your operating system and installed software (Flash, Java, etc.) up-to-date. If your computer is already infiltrated with the Lebanese Internal Security Forces virus, use the removal guide provided to eliminate this scam from your PC.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Lebanese Internal Security Forces?
- STEP 1. "Lebanese Internal Security Forces" virus removal using safe mode with networking.
- STEP 2. "Lebanese Internal Security Forces" ransomware removal using System Restore.
Lebanese Internal Security Forces virus removal:
Step 1
Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer starting process press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, then select Safe Mode with Networking from the list.
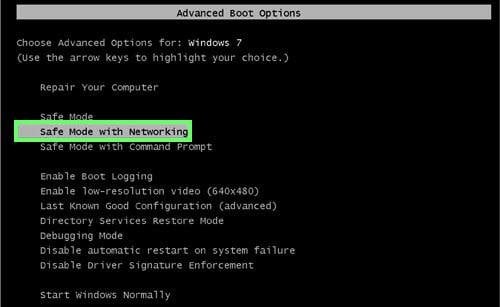
Video showing how to start Windows 7 in "Safe Mode with Networking":
Step 2
Log in to the account infected with the Lebanese Internal Security Forces virus. Start your Internet browser and download a legitimate anti-spyware program. Update the anti-spyware software and start a full system scan. Remove all entries detected.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
If you cannot start your computer in Safe Mode with Networking, try performing a System Restore.
Video showing how to remove ransomware virus using "Safe Mode with Command Prompt" and "System Restore":
1. During your computer starting process, press the F8 key on your keyboard multiple times until the Windows Advanced Options menu appears, and then select Safe Mode with Command Prompt from the list and press ENTER.
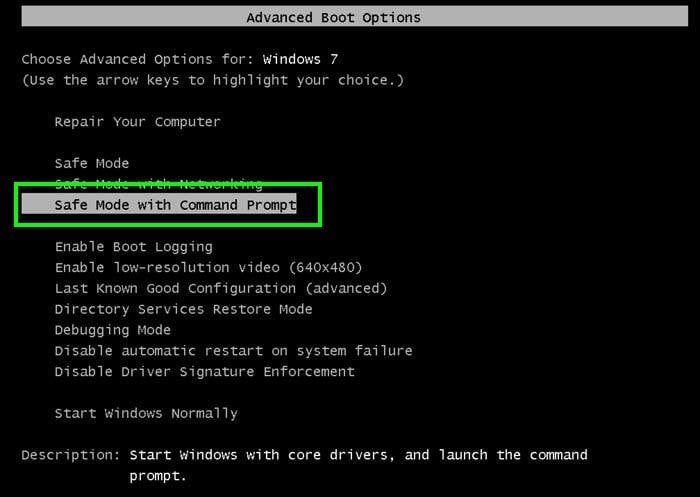
2. When Command Prompt Mode loads, enter the following line: cd restore and press ENTER.
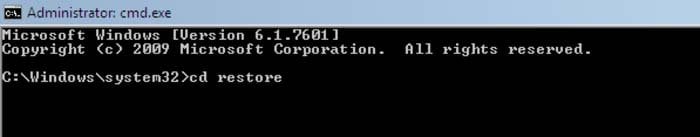
3. Next, type this line: rstrui.exe and press ENTER.
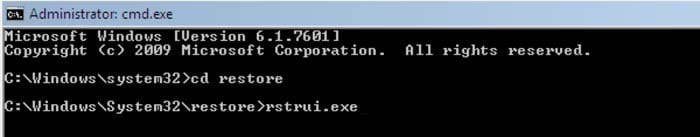
4. In the opened window click "Next".
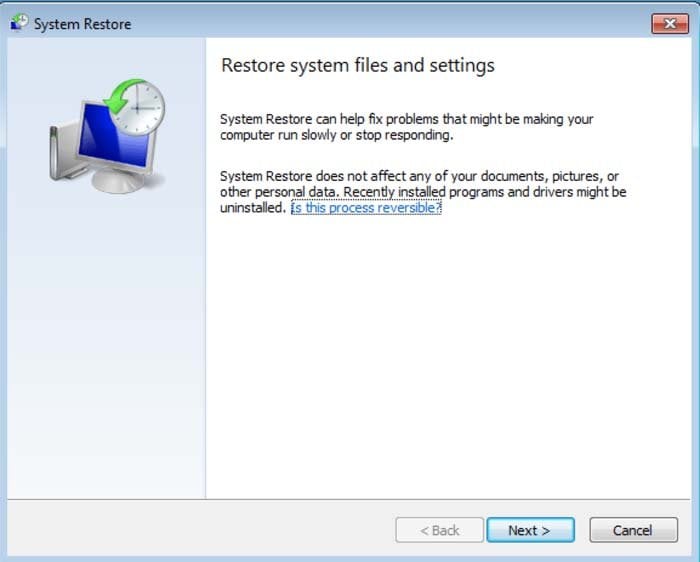
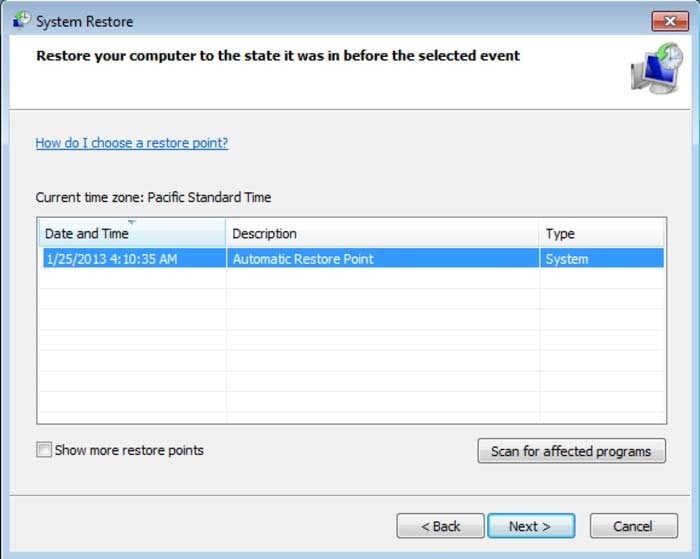
5. Select one of the available Restore Points and click "Next" (this will restore your computer system to an earlier time and date, prior to the ransomware infiltrating your PC).
6. In the opened window click "Yes".
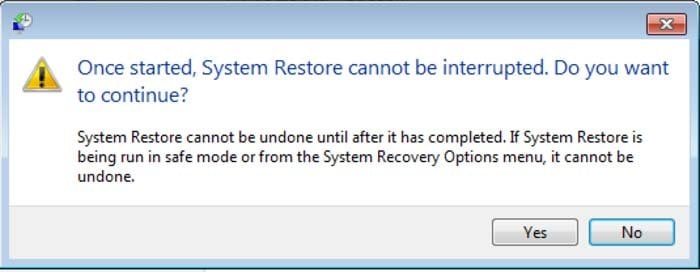
7. After restoring your computer to a previous date, download and scan your PC with recommended malware removal software to eliminate any remnants of the Lebanese Internal Security Forces virus.
If you cannot start your computer in Safe Mode with Networking (or with Command Prompt), boot your computer using a rescue disk.
Some variants of ransomware disable Safe Mode and make its removal complicated. For this step, you require access to another computer. After removing the Lebanese Internal Security Forces virus from your PC, restart your computer and scan it with legitimate antispyware software to remove any possible remnants of this security infection.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion