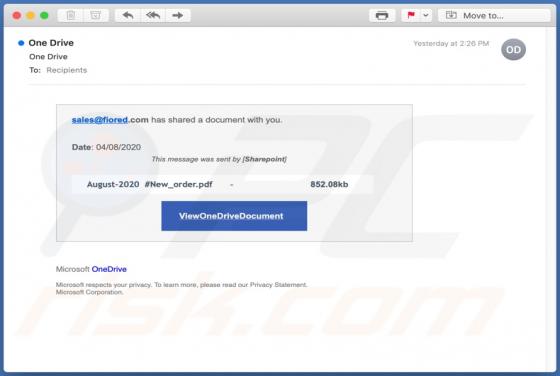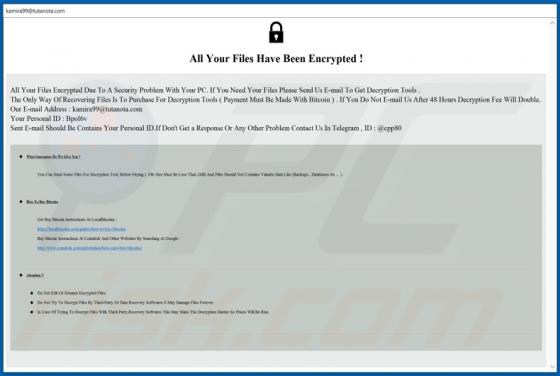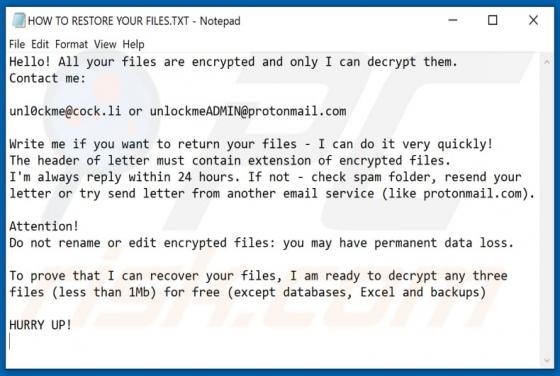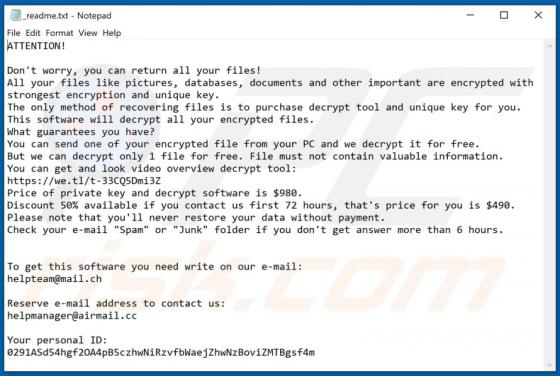
Fdcz Ransomware
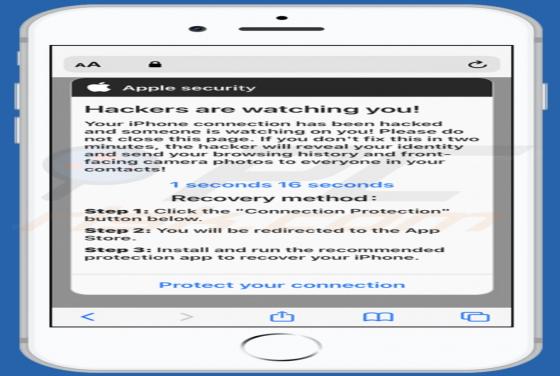
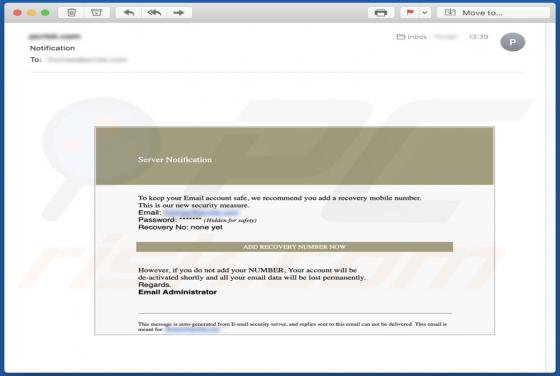
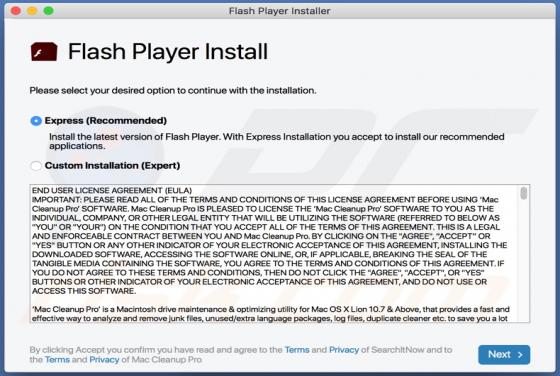
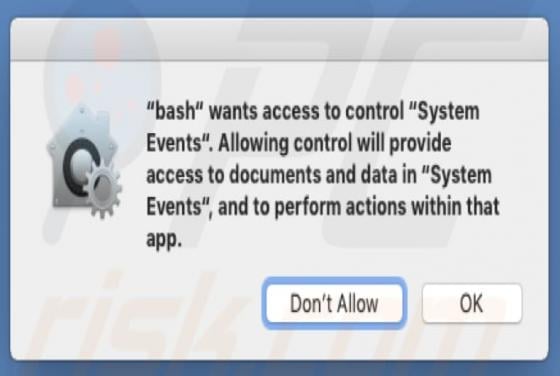
Fdcz is a type of malware that encrypts files and appends its extension to filenames. Ransomware victims cannot access or use their files unless they decrypt them with a specific decryption tool (program, key). Fdcz appends ".fdcz" as the file extension to the filenames. For example, "1.jpg" is