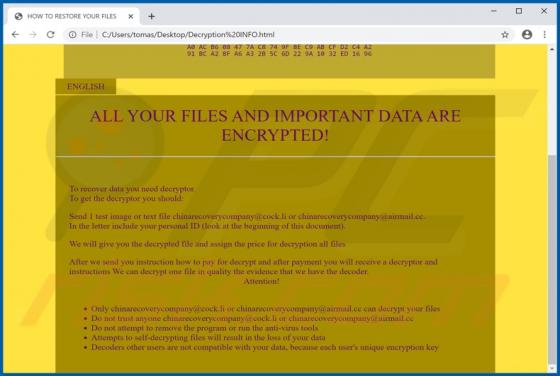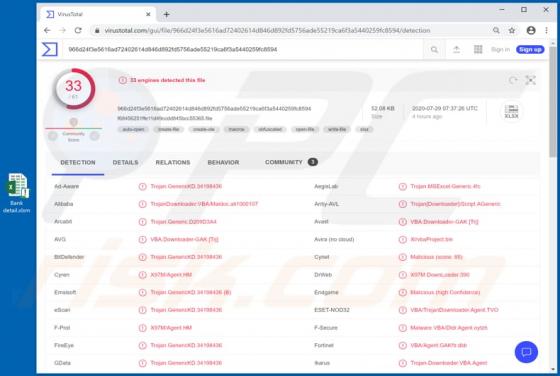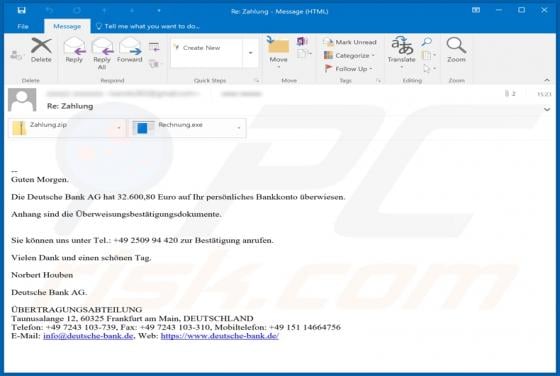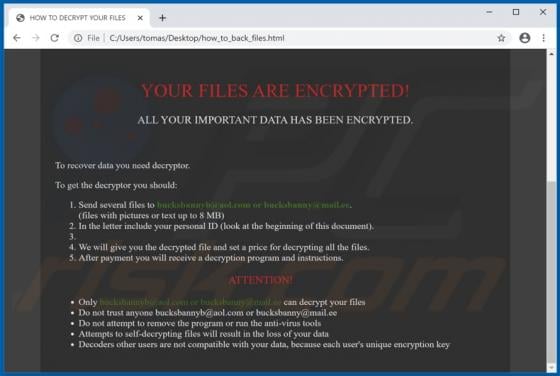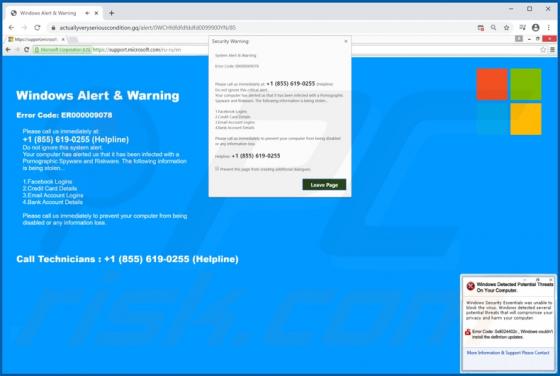
Windows Alert & Warning POP-UP Scam
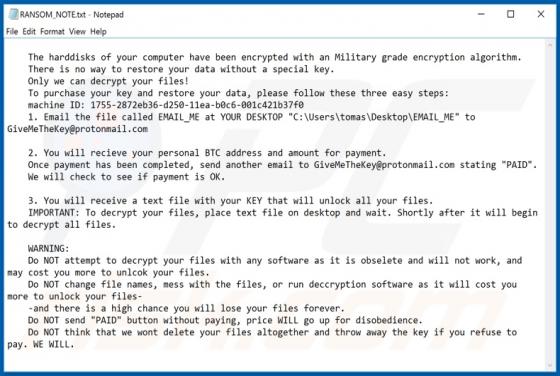
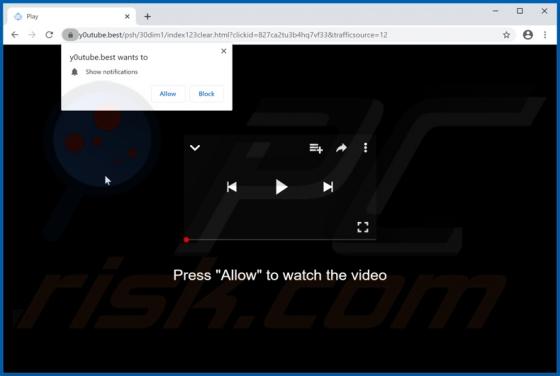
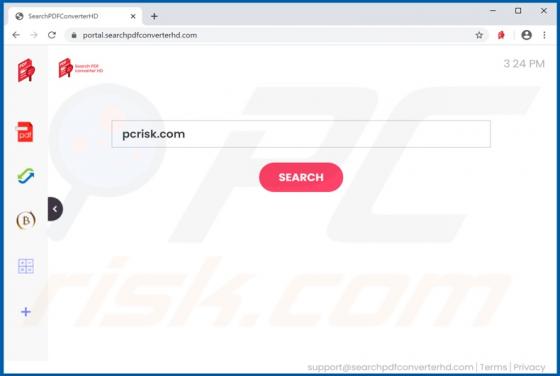
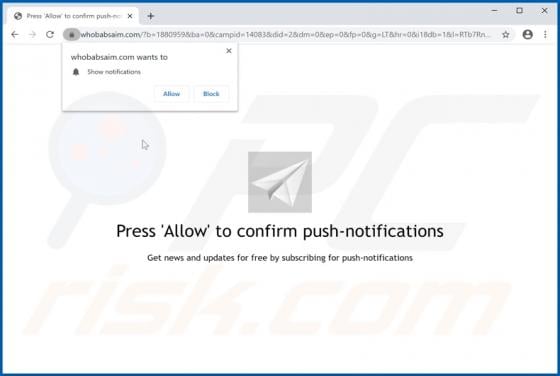
"Windows Alert & Warning" refers to a technical support scam promoted on various deceptive web pages. There are several variants of this scheme, however, they are practically identical message-wise, with slight graphical differences between them. As the name of this scam implies, it is disguis