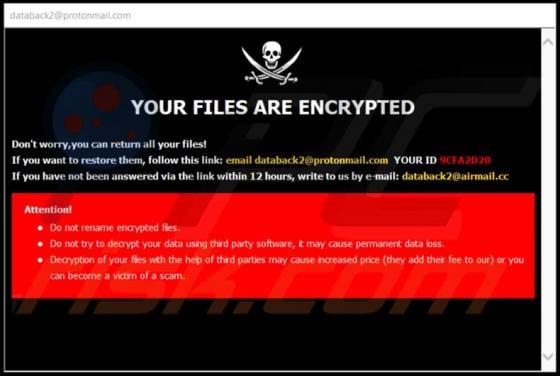
CoronaCrypt Ransomware
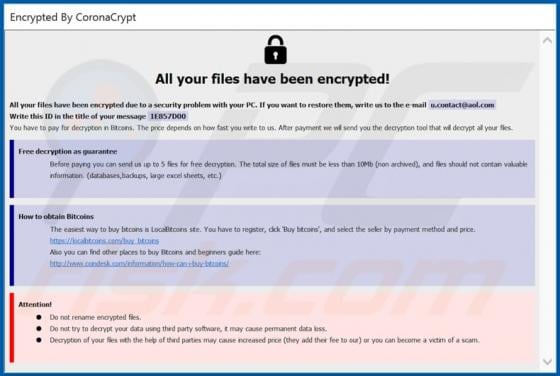
CoronaCrypt ransomware is designed to encrypt files, modify filenames, display a ransom message and create the "How_To_Restore_Your_Files.txt" text file (another ransom message). It renames files by adding its name, u.contact@aol.com email address, victim's ID, and appending the ".Encrypted" exten