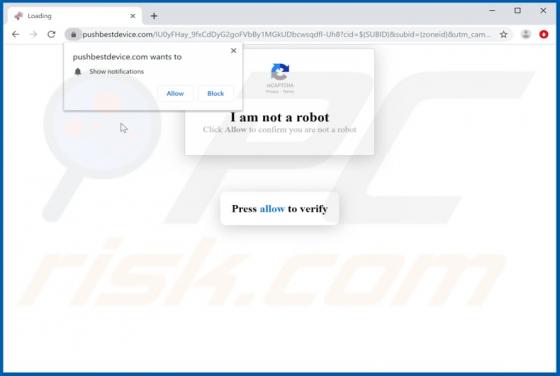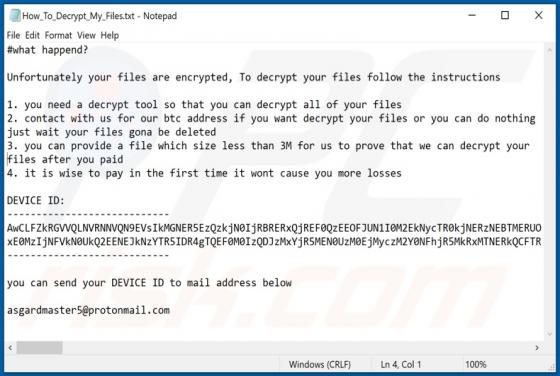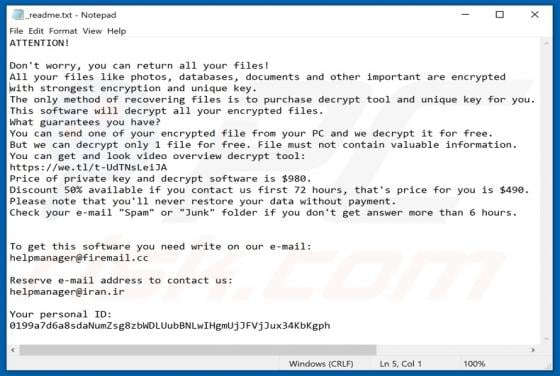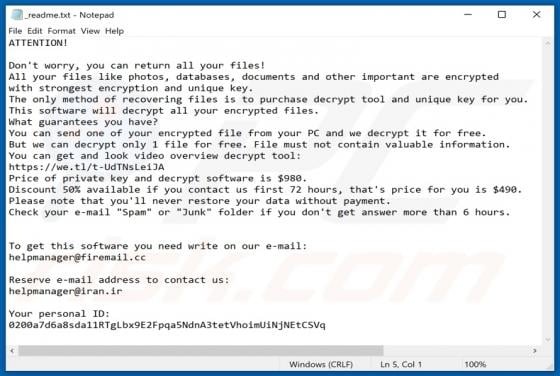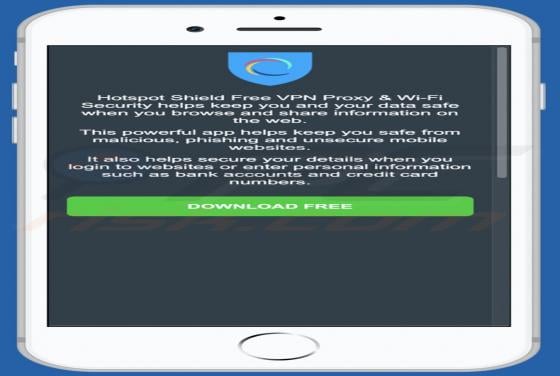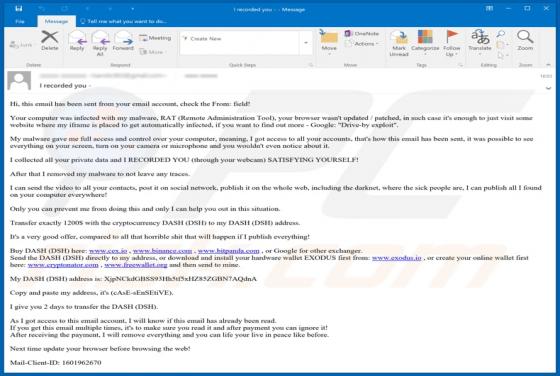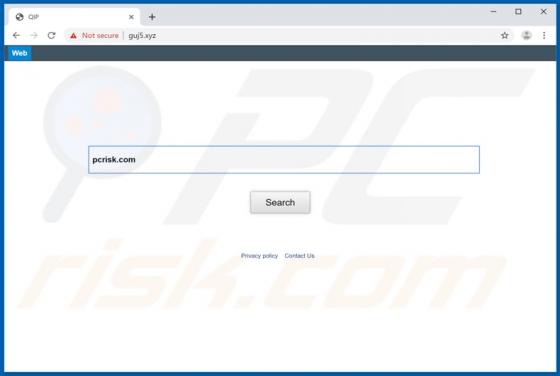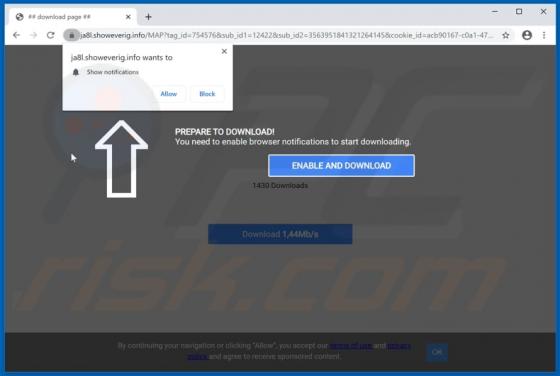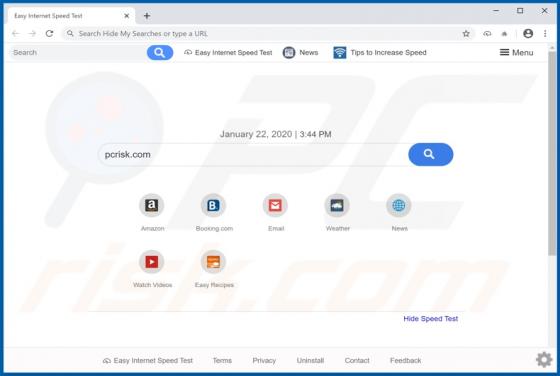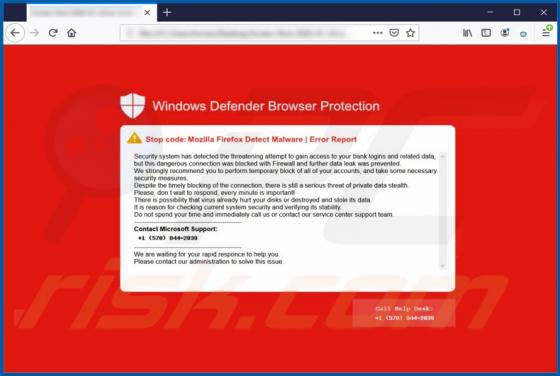
Windows Defender Browser Protection POP-UP Scam
"Windows Defender Browser Protection" is a technical support scam. This scam model operates by warning of potential/detected infections and urging users to contact a 'legitimate' support service. The "Windows Defender Browser Protection" scheme is run on various deceptive websites. It claims that