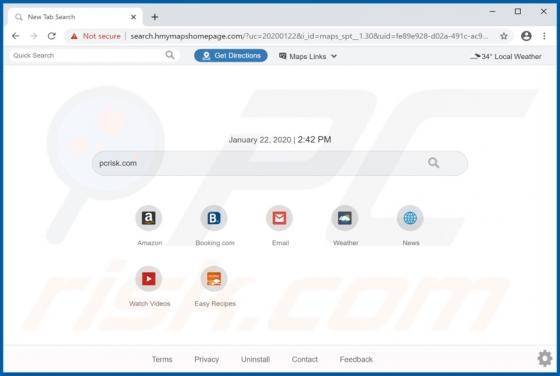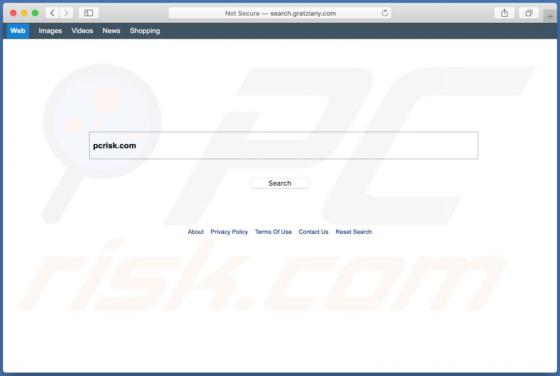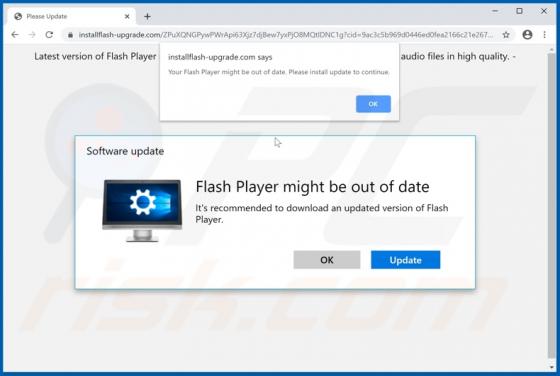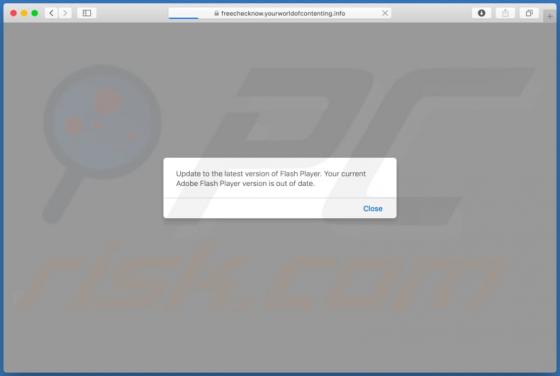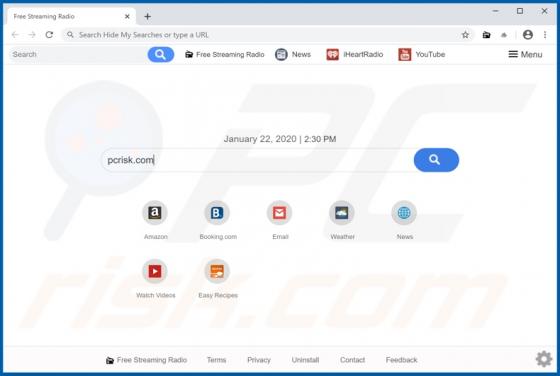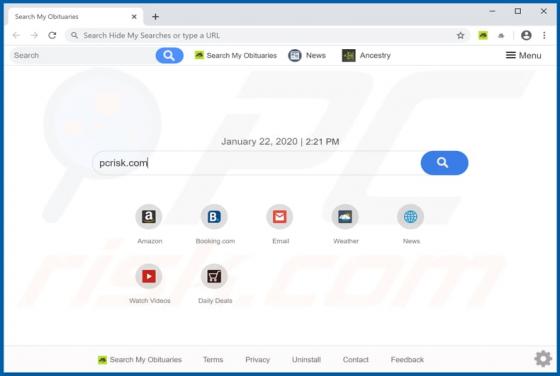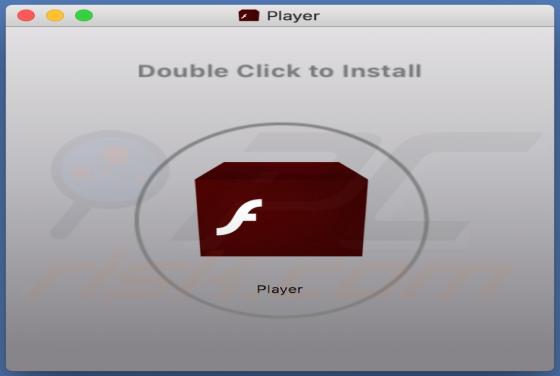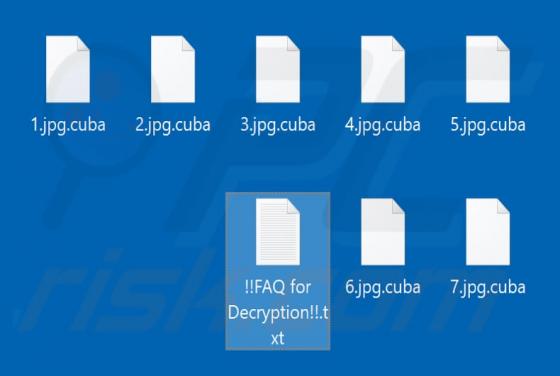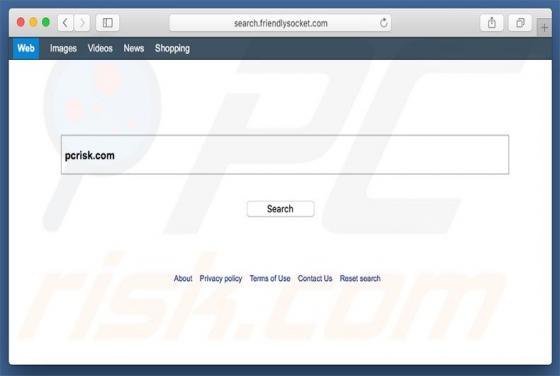
Search.friendlysocket.com Redirect (Mac)
Identical to search.cucumberhead.com, search.listchack.com, search.smacklek.com, and dozens of other bogus sites, search.friendlysocket.com is a fake Internet search engine claiming to improve the web browsing experience by generating the most relevant search results. These false claims often t