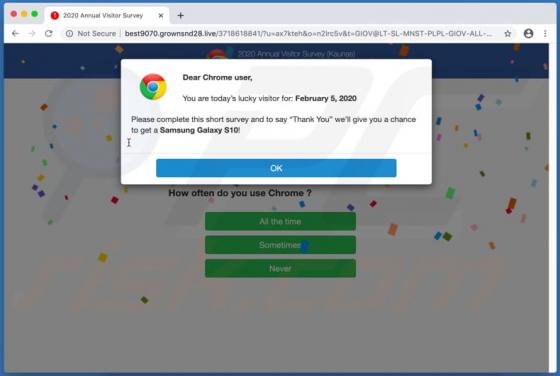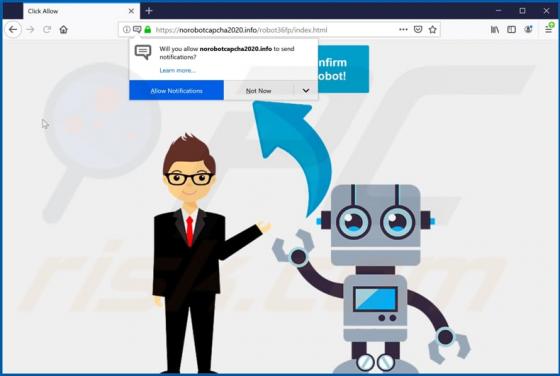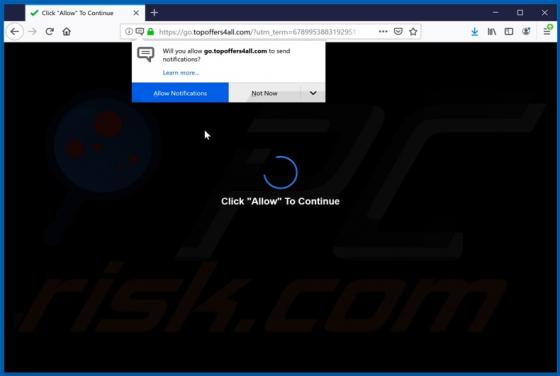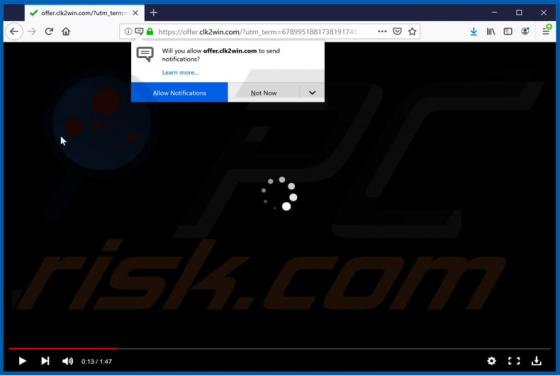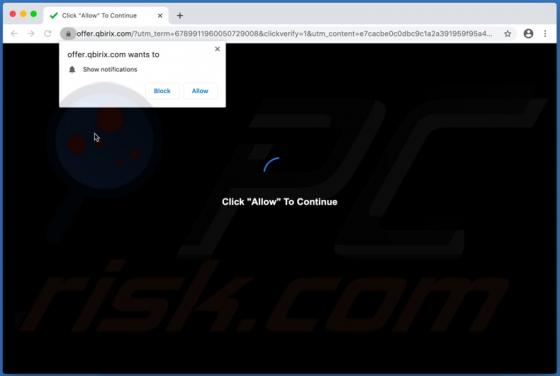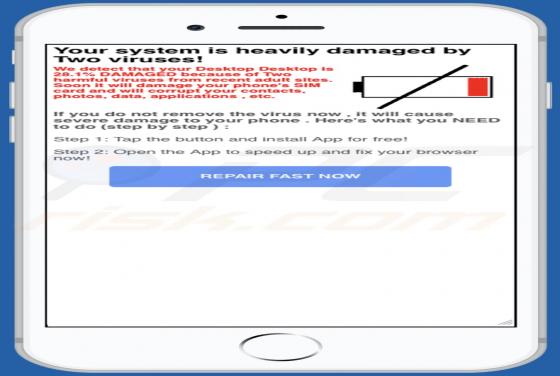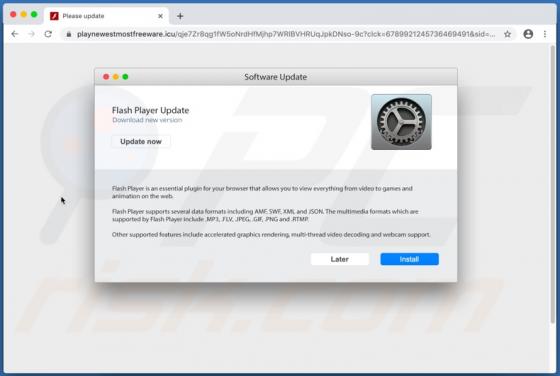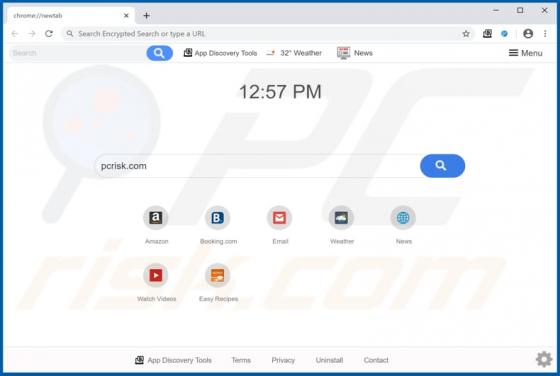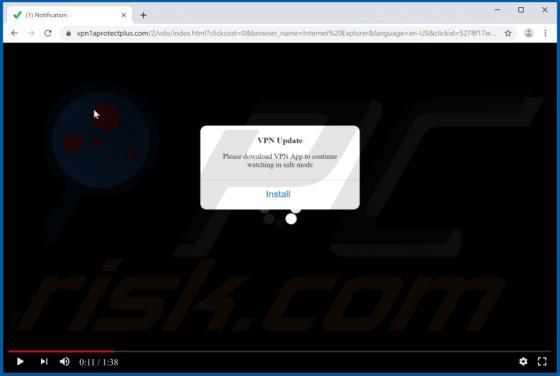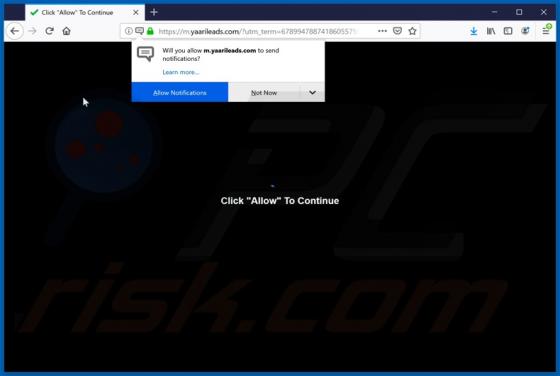
Yaarileads.com Ads
yaarileads[.]com is a rogue website and similar to thousands of others (for example, norobotcapcha2020.info, topoffers4all.com, and clk2win.com). Visitors to this site are presented with dubious content and/or are redirected to other untrusted or malicious web pages. Few users enter yaarileads[.]