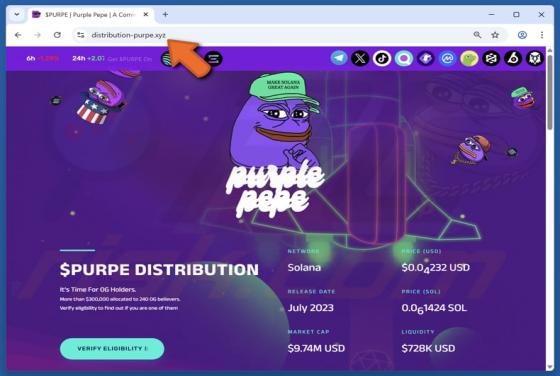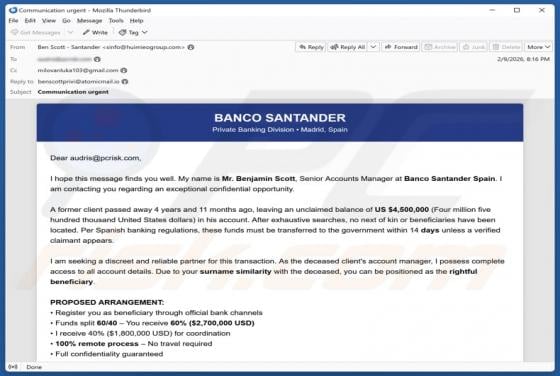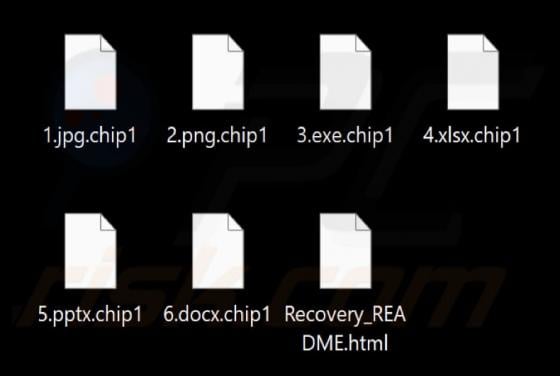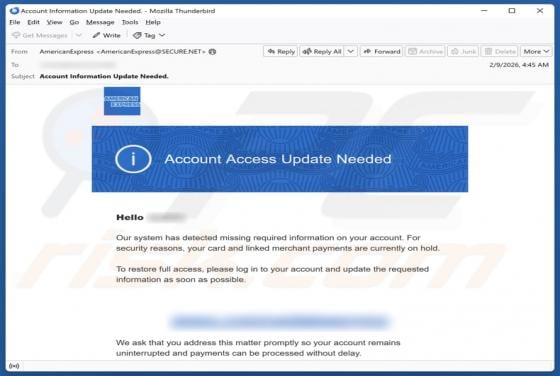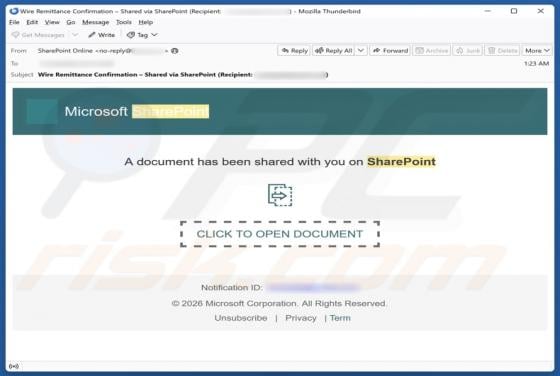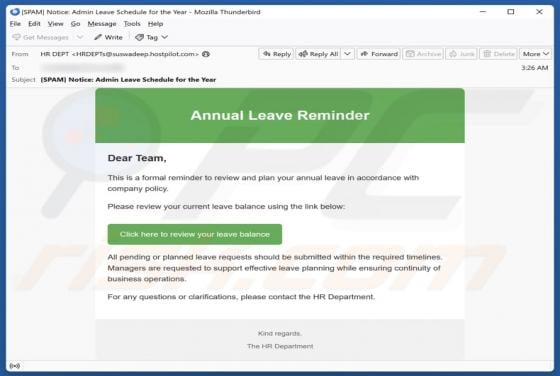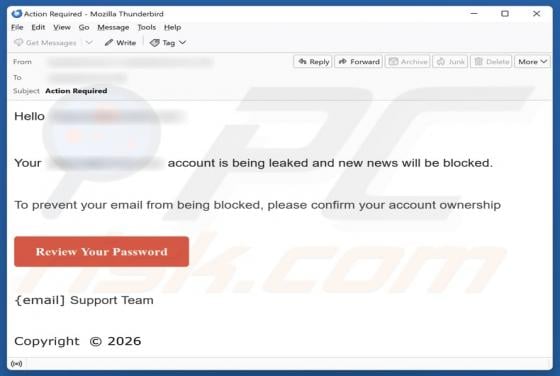
Your Account Is Being Leaked Email Scam
We have inspected the message and determined that it is a phishing email masquerading as an urgent notification from the email service provider. It is designed to trick recipients into opening a fake login website and disclosing personal information. Victims of this scam may lose access to persona