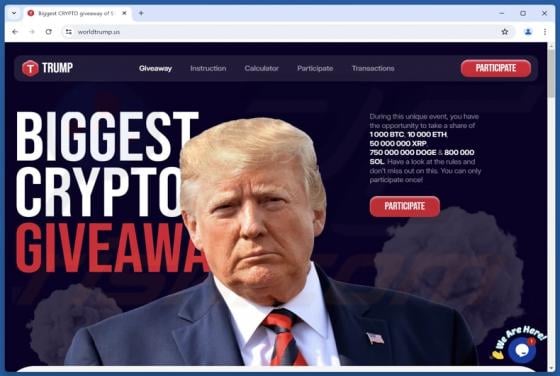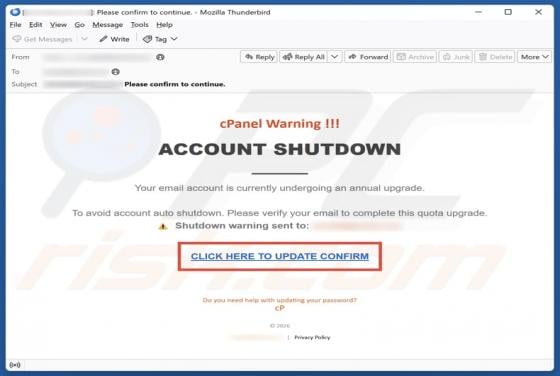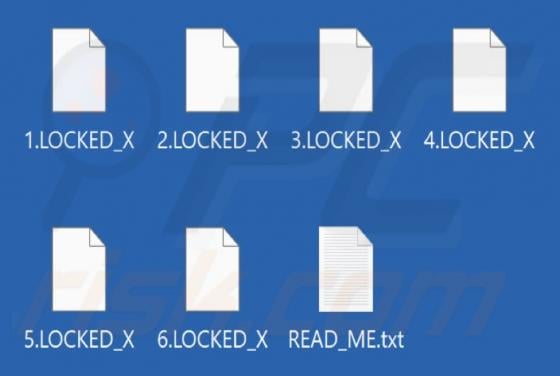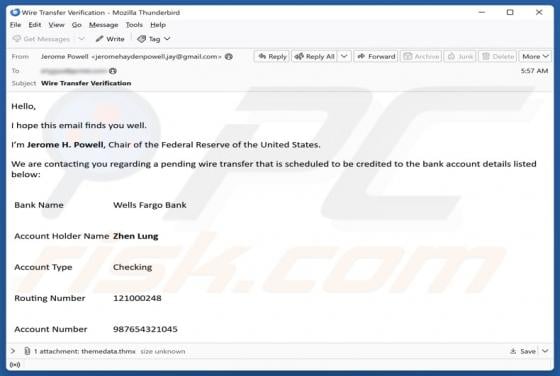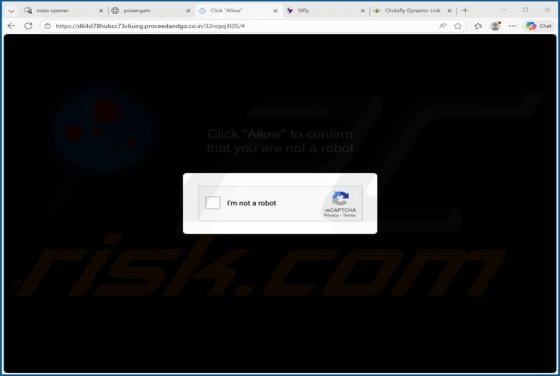
Proceedandgo.co.in Ads
Our analysis has revealed that proceedandgo.co[.]in is designed to trick visitors into agreeing to receive notifications. The website uses a deceptive message as a lure. If permitted, proceedandgo.co[.]in can deliver fake warnings and other types of misleading notifications that can expose users t