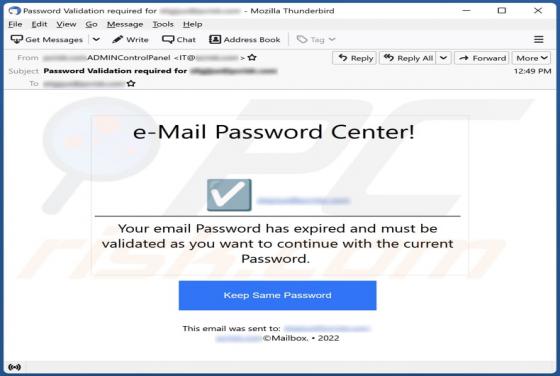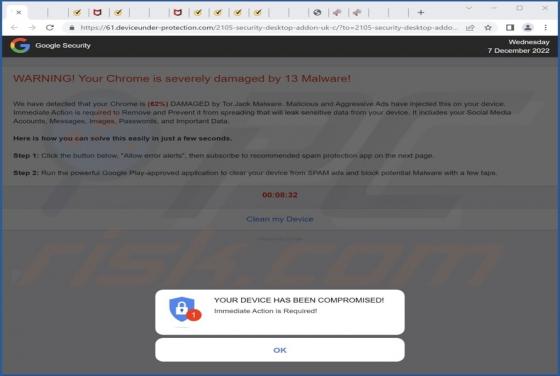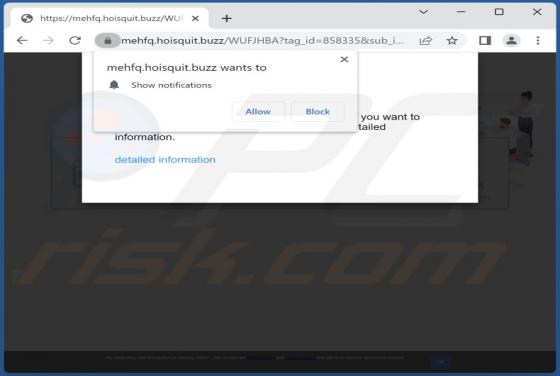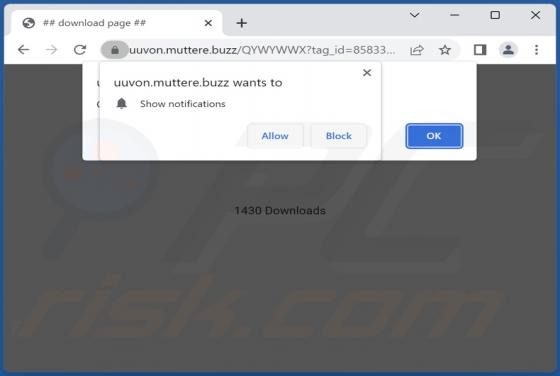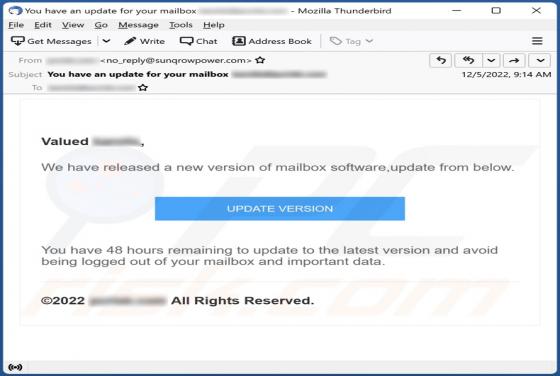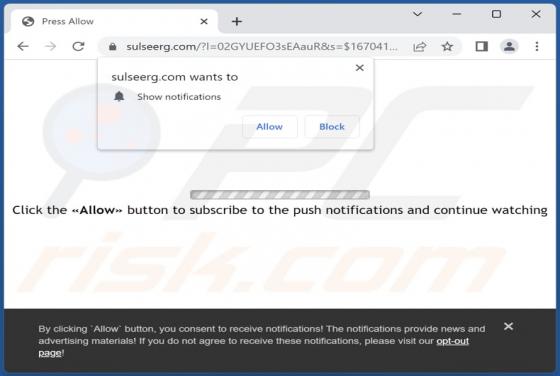
Sulseerg.com Ads
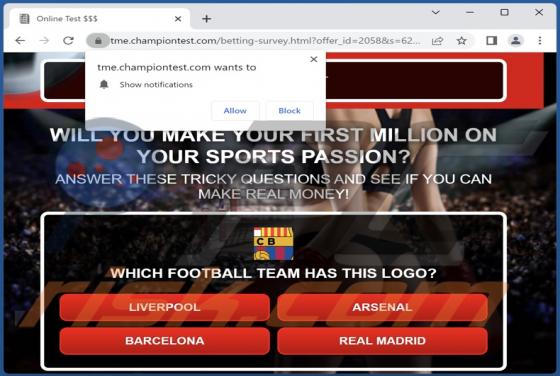
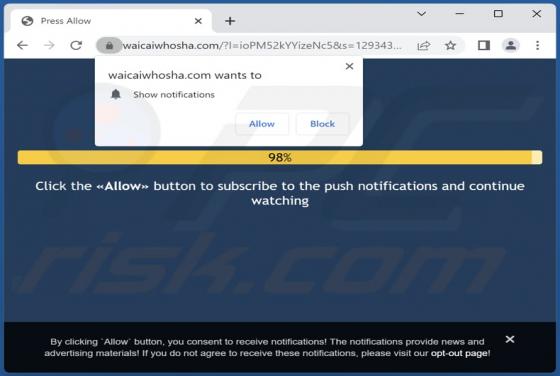
Sulseerg[.]com is designed to trick visitors into agreeing to receive notifications. It uses a clickbait technique (displays a deceptive message) to get that permission. Also, sulseerg[.]com redirects to other websites. We found sulseerg[.]com while inspecting pages that use rogue advertising netw