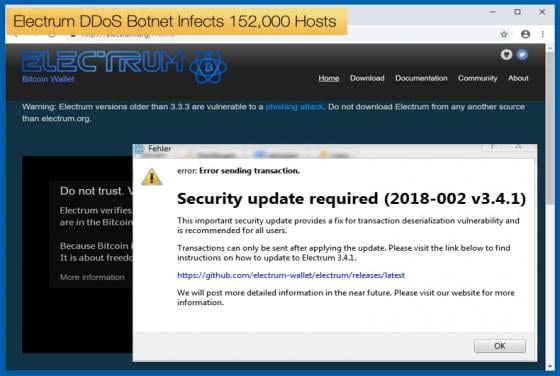
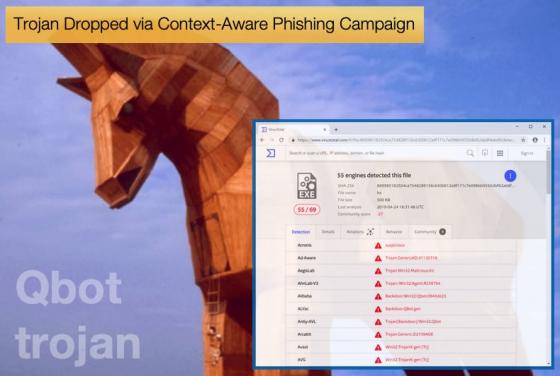
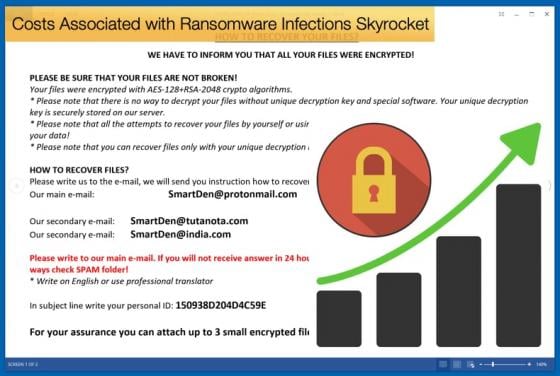
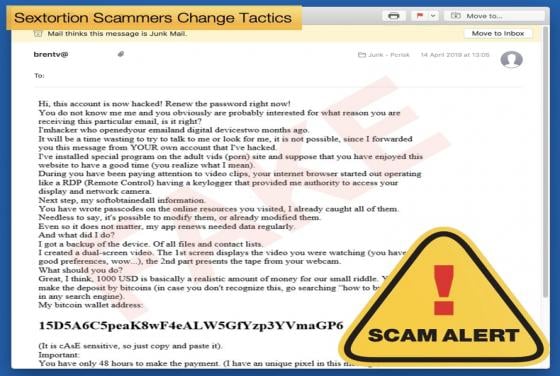
Ransomware Operators Exploit Zero-Day Vulnerability
Attackers have been actively exploiting a zero-day vulnerability in the widely used Oracle WebLogic Server to deliver not one but two ransomware variants. Zero-day vulnerabilities can be defined as a software security flaw that doesn’t yet have a patch. These vulnerabilities can result in security h