Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is PayPal Email Virus?
"PayPal Email Virus" is a spam email campaign similar to FedEx Shipment, Barclays Secured Message, Electronic Intuit, and many others.
This campaign is used to proliferate a high-risk trojan called TrickBot. The message essentially states that a number of PayPal accounts have been hacked and, therefore, users must confirm their personal information by opening an attached MS Word document (which is malicious).
As mentioned above, the message encourages users to open an attached document to confirm their account details. This is a scam - the opened malicious attachment instantly downloads and installs the TrickBot trojan. Note that PayPal is a legitimate company and has nothing to do with this spam campaign.
It is very common for cyber criminals to claim to be employees of huge companies or governmental institutions. In this way, they increase the chance of convincing users into opening attachments - users are much more likely to open emails received from familiar names. TrickBot is high-risk malware that gathers sensitive information.
After successful infiltration, it hijacks browsers and modifies visited website content so that all entered logins/passwords are saved on a remote server. The presence of such malware can lead to serious privacy issues and significant financial loss, since cyber criminals might gain access to personal accounts of social networks, banks, and so on.
Therefore, if you have already opened attachments distributed via the "PayPal Email Virus" campaign, you should immediately scan the system with a legitimate anti-virus/anti-spyware suite and remove all detected threats.
| Name | PayPal spam |
| Threat Type | Trojan, Password stealing virus, Banking malware, Spyware |
| Symptoms | Trojans are designed to stealthily infiltrate victim's computer and remain silent thus no particular symptoms are clearly visible on an infected machine. |
| Distribution methods | Infected email attachments, malicious online advertisements, social engineering, software cracks. |
| Damage | Stolen banking information, passwords, identity theft, victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
There are dozens of trojan-type viruses similar to TrickBot including, for example, DanaBot, Emotet, and FormBook. As with TrickBot, many trojans are distributed using spam emails, likely to gather sensitive information, and are often designed to infiltrate the system with other malware (usually ransomware).
Therefore, the presence of any trojan is very dangerous - these viruses pose a direct threat to your privacy and computer safety.
How did PayPal Email Virus infect my computer?
"PayPal Email Virus" is used to proliferate a malicious MS Word attachment. After opening the document, users are asked to enable macro commands. Once macros are enabled, the attachment immediately executes commands that download and install TrickBot.
Although this distribution method is very simple, it has a major flaw - the malicious attachment is only able to download malware if it is opened using MS Word. Thus, using other software (capable of opening .doc formats) will prevent the infection. Furthermore, TrickBot targets the MS Windows Operating System only and users of other platforms are safe.
How to avoid installation of malware?
To prevent this situation, be very cautious when browsing the Internet. Carefully analyze each email attachment received. If the file seems irrelevant or has been received from a suspicious address, you should never open it. Be aware also that 2010 and newer MS Office versions open newly-downloaded documents in "Protected View" mode.
This prevents malicious attachments from downloading and installing malware. Therefore, using old versions is not recommended. Furthermore, you should have a reputable anti-virus/anti-spyware suite installed and running. The main reasons for computer infections are poor knowledge and careless behavior.
The key to safety is caution. If you have already opened a "PayPal Email Virus" attachment, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the "PayPal Email Virus" email message:
Subject: PayPal account warning
Greetings, dear Client! please!
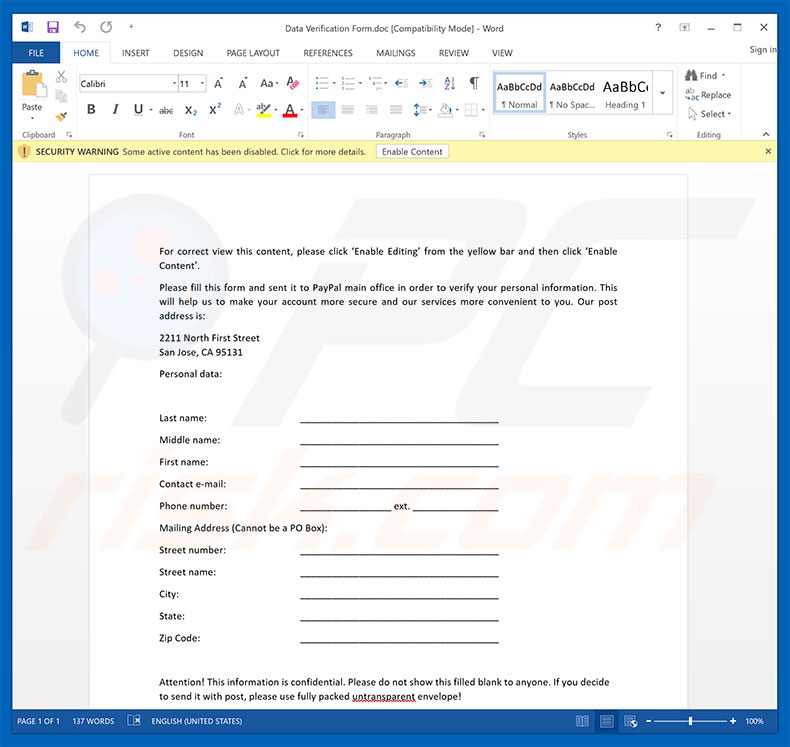
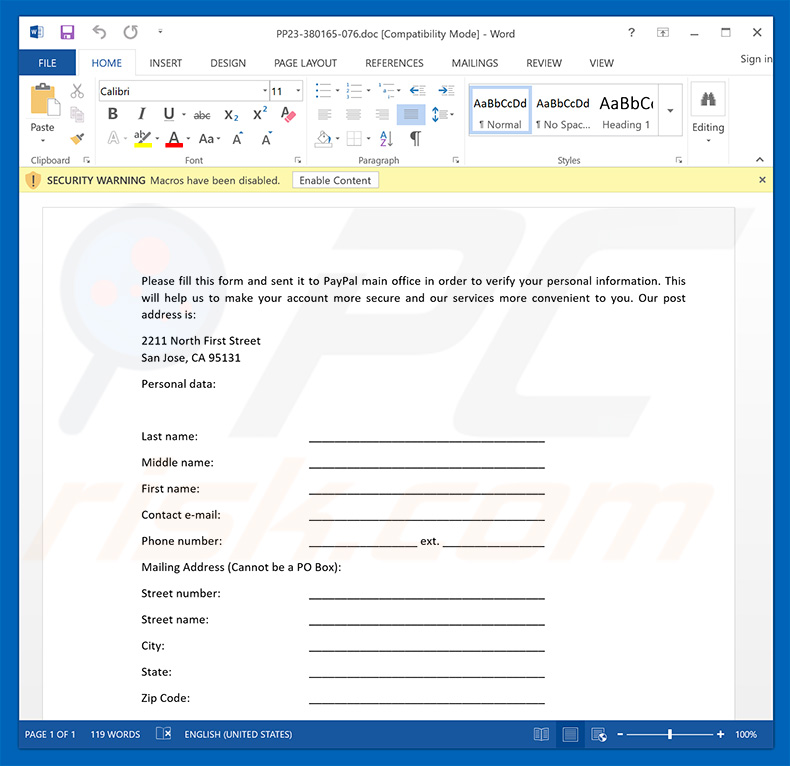
We noticed a lot of frauds performed by machinations with online servicesof the accounts of our clients. Attackers obtain access to accounts by stealing login data and passwords. This may be very dangerous for your funds and our reputation, so we are asking you to perform some actions, in order to prevent fraud. To protect your funds, verify please your account data. It will let us approve your post address and personal data. Also we strongly recommend to keep passwords and login data, in the safe place. To make your account information verified, please fill and send the next form via e-mail or via post. Our post address is:
2211 North First Street
San Jose, CA 95131
ATTACHED FILE: Data Verification Form
If you will not react on this notification, we will be forced to temporarily block your online services until you won’t verify your account information.
Important: Do not send or show your login data to anybody! We NEVER ask our clients to send it to us! Also we recommend to check your devices with antiviral software to detect and eliminate the vulnerabilities.
We are sorry for such inconvenience.
Yours faithfully,
PayPal Security Center.
Malicious attachment distributed via "PayPal Email Virus" spam campaign:
Another variant of "PayPal Email Virus" spam campaign:
Text presented within this email:
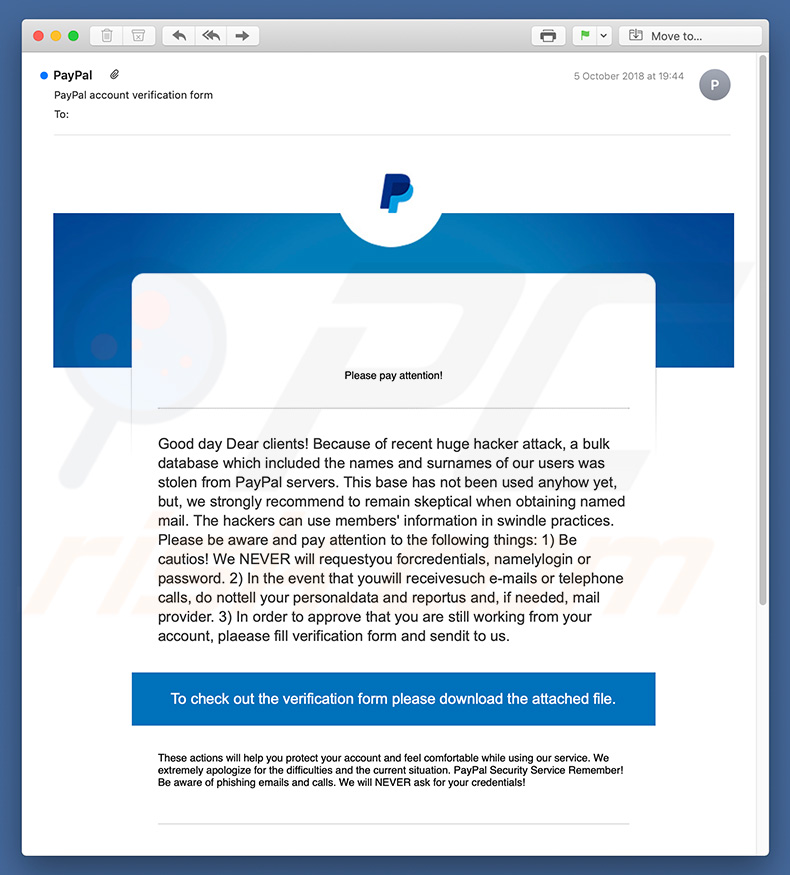
Please pay attention!
Good day Dear clients! Because of recent huge hacker attack, a bulk database which included the names and surnames of our users was stolen from PayPal servers. This base has not been used anyhow yet, but, we strongly recommend to remain skeptical when obtaining named mail. The hackers can use members' information in swindle practices. Please be aware and pay attention to the following things: 1) Be cautios! We NEVER will requestyou forcredentials, namelylogin or password. 2) In the event that youwill receivesuch e-mails or telephone calls, do nottell your personaldata and reportus and, if needed, mail provider. 3) In order to approve that you are still working from your account, plaease fill verification form and sendit to us.
To check out the verification form please download the attached file.
These actions will help you protect your account and feel comfortable while using our service. We extremely apologize for the difficulties and the current situation. PayPal Security Service Remember! Be aware of phishing emails and calls. We will NEVER ask for your credentials!
Malicious attachment distributed via this variant:
Another variant of "PayPal Email Virus" spam campaign (used to distribute Hancitor):

Text presented within this email:
Good Afternoon,
You received a payment of $133.17 USD
Thanks for using PayPal. To see all the transaction details, download your PayPal Transaction details file:
Download transaction details file
It may take a few moments for this transaction to appear in your account.
Seller Protection - Eligible
Question? Go to the Help Center at: www.paypal.com/help.
Please do not reply to this email. This mailbox is not monitored and you will not receive a response. For assistance, log in to your PayPal account and click Help in the top right corner of any PayPal page.
You can receive plain text emails instead of HTML emails. To change your notifications preferences, log into your account, go to your Profile, and click My settings.Copyright © 1999-2018 PayPal, Inc. All rights reserved. PayPal is located at 2211 N. First St., San Jose, CA 95131.
PayPal PPX000000:5.1:78m7m6j2z2z0
Two other variants of "PayPal Email Virus" spam campaign, both promoting a link to download the exact same malicious MS Office document.
Sample 1:
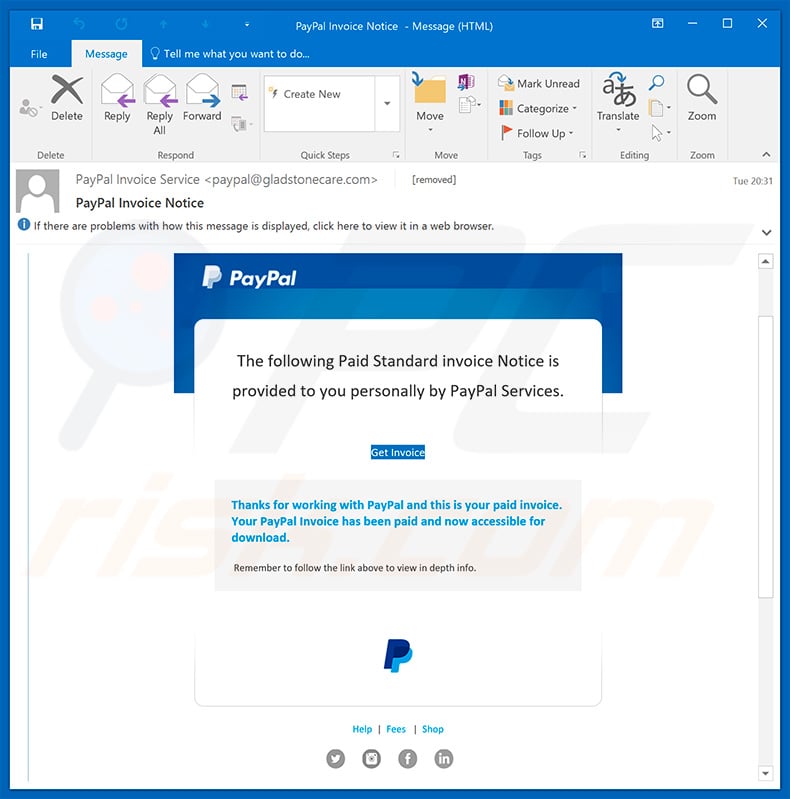
Text presented within this email:
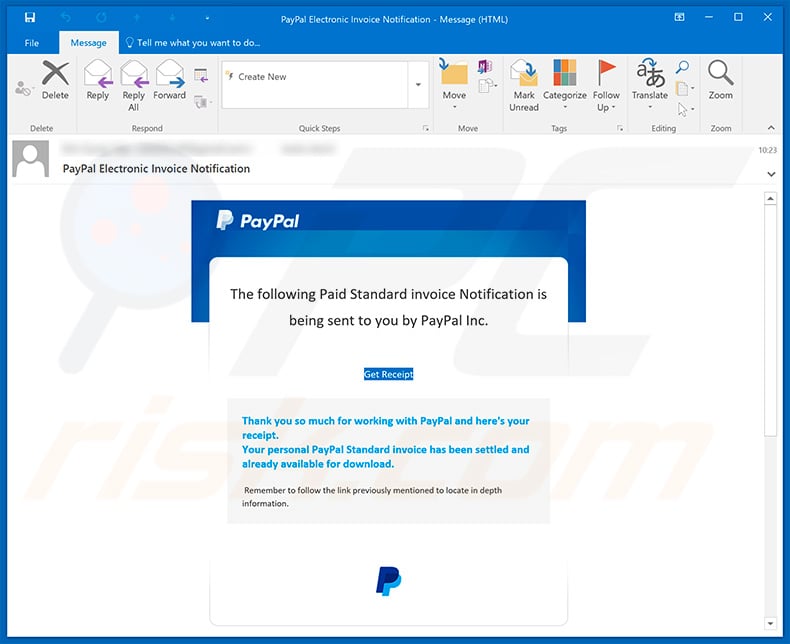
The following Paid Standard invoice Notice is provided to you personally by PayPal Services.
Get Invoice
Thanks for working with PayPal and this is your paid invoice.
Your PayPal Invoice has been paid and now accessible for download.
Remember to follow the link above to view in depth info.Help | Fees | Shop
Just click here to Remove your address
Please do not respond to this e mail. We are not able to respond to questions delivered to this e-mail. For fast responses to your concerns, visit our Support Center by clicking "Support" found on any PayPal page.
PayPal is Certified as a Funds Transmitter by the Nyc Department of Financial Services. PayPal, NMKS #910537, License #FB3351, Massachusetts Foreign Transmittal Certificate. PayPal, Transmit Money By Money Order By The Division of Banking, Commonwealth of Pennsylvania. PayPal, Rhode Island Licensed Money Transferor. PayPal, INC., NHOS #910456, LICENSE #44866, IS LICENSED BY THE ATLANTA DEPARTMENT OF BUSINESS BANKING AND FINANCING.Copyright laws 2018 PayPal, Inc. PayPal is placed at 2215 N. First St., San Antonio, CA 95234.
Sample 2:
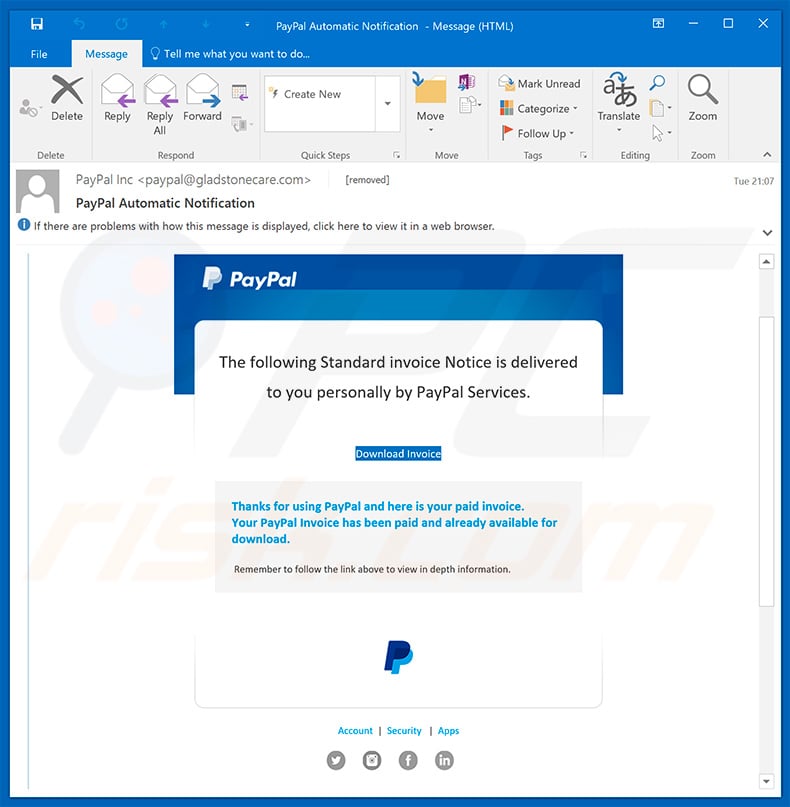
Text presented within this email:
The following Standard invoice Notice is delivered to you personally by PayPal Services.
Download Invoice
Thanks for using PayPal and here is your paid invoice.
Your PayPal Invoice has been paid and already available for download.
Remember to follow the link above to view in depth information.Account | Security | Apps
Click this link to Unsubscribe
Please do not respond to this email. We are unable to react to requests sent to this address. For fast replies to your inquiries, visit our Support Center simply by clicking "Support" found on any PayPal email.
PayPal Inc. is Licensed as a Funds Transmitter by the Nyc State Dept of Monetary Services. PayPal, NMKS #920437, Permit #FT3355, Massachusetts Foreign Transmittal Permit. PayPal, Inc., Transmit Funds By Money Order By The Division of Banking, Commonwealth of Pennsylvania. PayPal, Inc. Rhode Island Certified Money Transferor. PAYPAL, INC., NHLS #910447, PERMIT #34967, IS LICENSED BY ATLANTA DEPT OF BUSINESS BANKING AND FINANCING.
Copyright 2018 PayPal, Inc. PayPal is placed at 2215 N. 1st St., San Jose, CA 96154.
Screenshot of the malicious attachment (once macros are enabled, this document downloads and executes Hancitor trojan):

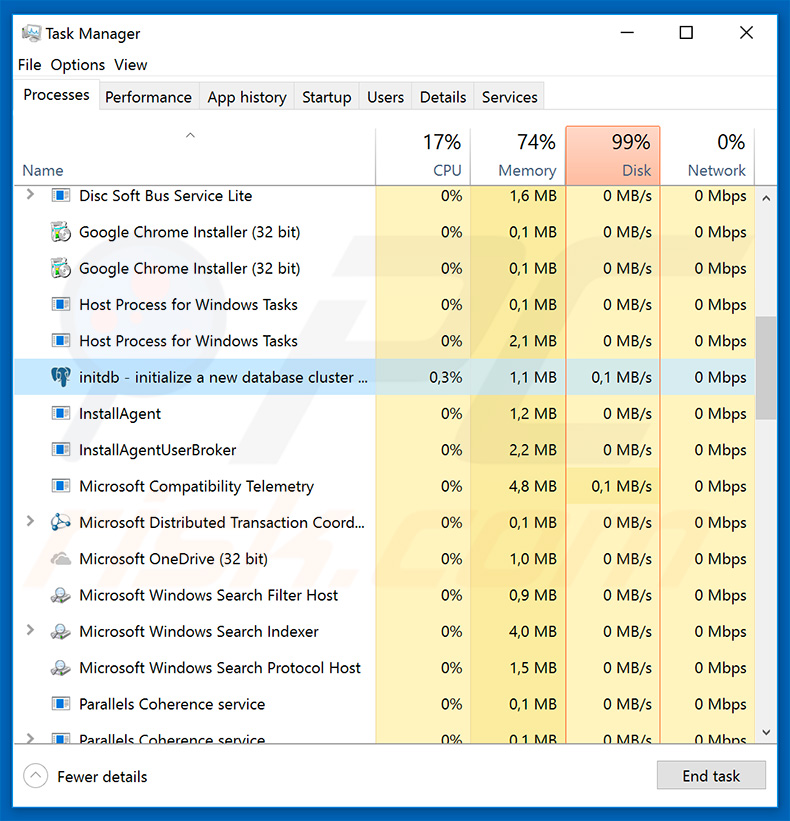
Hancitor trojan's process ("initdb - initialize a new database cluster") in Windows Task Manager. After infiltrating the system this trojan injects Ursnif malware into the system.
Update 19 December, 2018 - Crooks now use this spam campaign to steal logins/passwords - they send emails that contain a link to fake PayPal login page. Once the account credentials are entered, they're instantly saved in a remote server controlled by cyber criminals. In other word, crooks instantly gain access to victim's PayPal account.
Screenshot of the email:
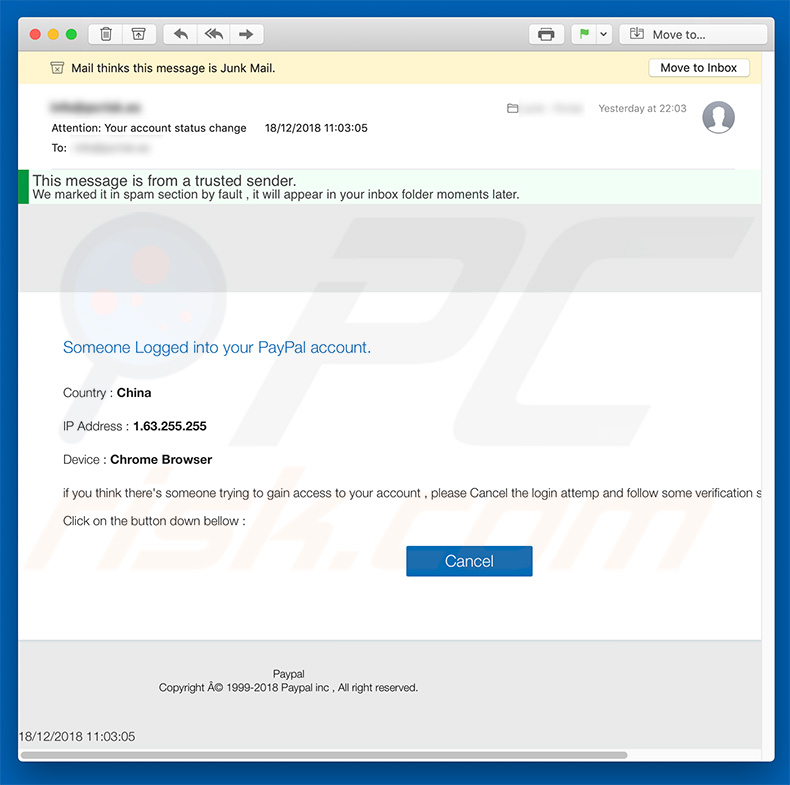
Text presented within this letter:
PayPal Email Virus Update - password stealing email - phishing
Subject: Attention: Your account status change
This message is from a trusted sender.
We marked it in spam section by fault , it will appear in your inbox folder moments later.Someone Logged into your PayPal account.
Country : China
IP Address : 1.63.255.255
Device : Chrome Browser
if you think there's someone trying to gain access to your account , please Cancel the login attemp and follow some verification steps.
Click on the button down bellow : Cancel (clicking this link leads to a phishing website - if you entered your password in this site be sure to contact PayPal (explaining you have been tricked by a phishing email) and change your password immediately)
Screenshot of fake PayPal login website promoted via this email:
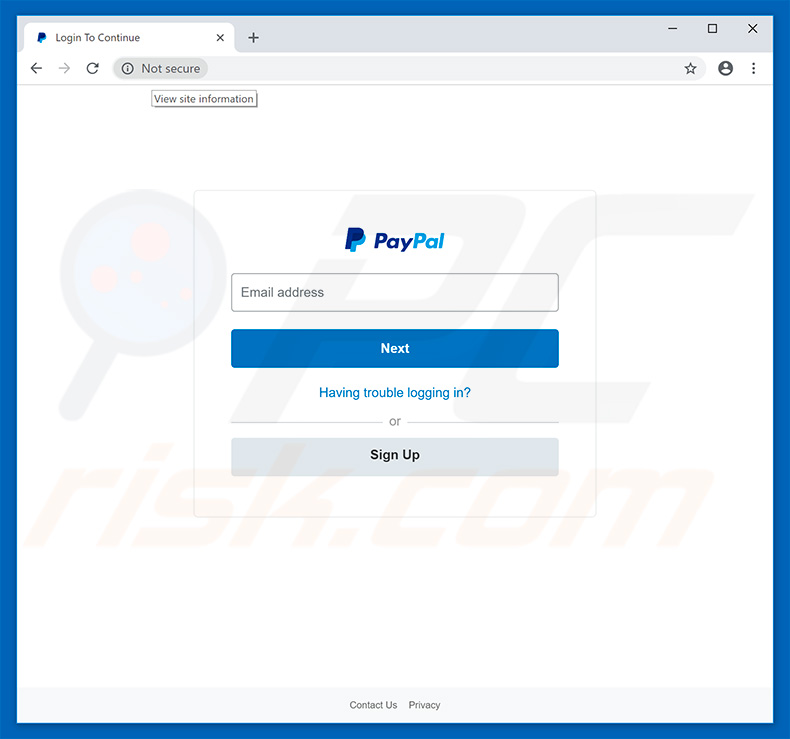
Another variant of "PayPal Email Virus" spam campaign's phishing mail:
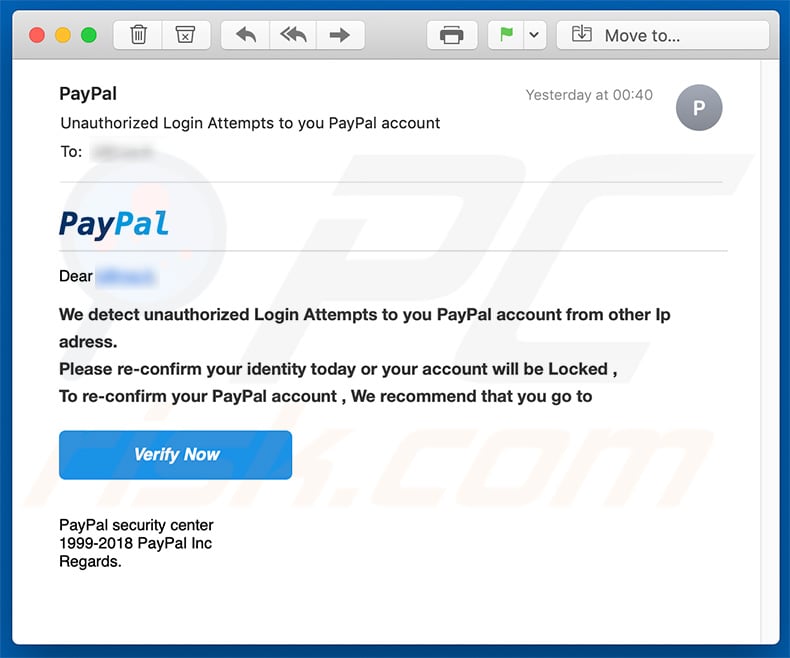
Text presented within this email:
Dear ******,
We detect unauthorized Login Attempts to you PayPal account from other Ip adress.
Please re-confirm your identity today or your account will be Locked ,
To re-confirm your PayPal account , We recommend that you go toVerify Now
PayPal security center
1999-2018 PayPal Inc
Regards.
Two additional examples of PayPal-related spam emails used for phishing purposes:
Example 1:
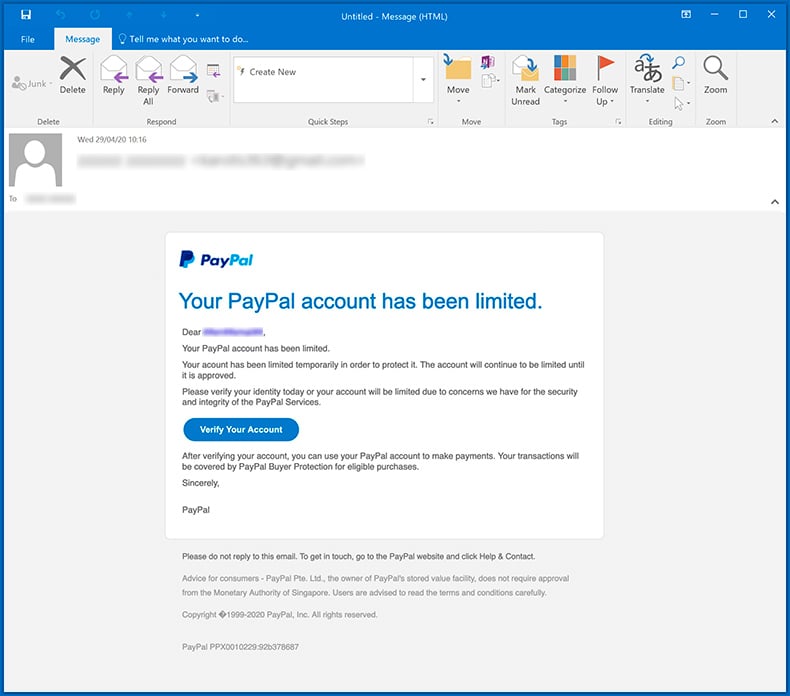
Text presented within:
PayPal
Your PayPal account has been limited.Dear ***,
Your Paypal account has been limited.
Your account has been limited temporarily in order to protect it. The account will continue to be limited until it is approved.
Please verify your identity today or your account will be limited due to concerns we have for the security and integrity of the PayPal Services.
Verify Your Account
After verifying your account, you canuse your PayPal account to make payments. Your transactions will be covered by PayPal Buyer Protection for eligible purchases.
Sincerely,
PayPalPlease do not reply to this email. To get in touch, go to the PayPal website and click Help & Contact.
Advice for consumers - PayPal Pte. Ltd., the owner of PayPal's stored value facility, does not require approval from the Monetary Authority of Singapore. Users are advised to read the terms and conditions carefully.
Copyright 1999-2020 PayPal, Inc. All rights reserved.
PayPal PPX0010229:92b378687
Example 2:
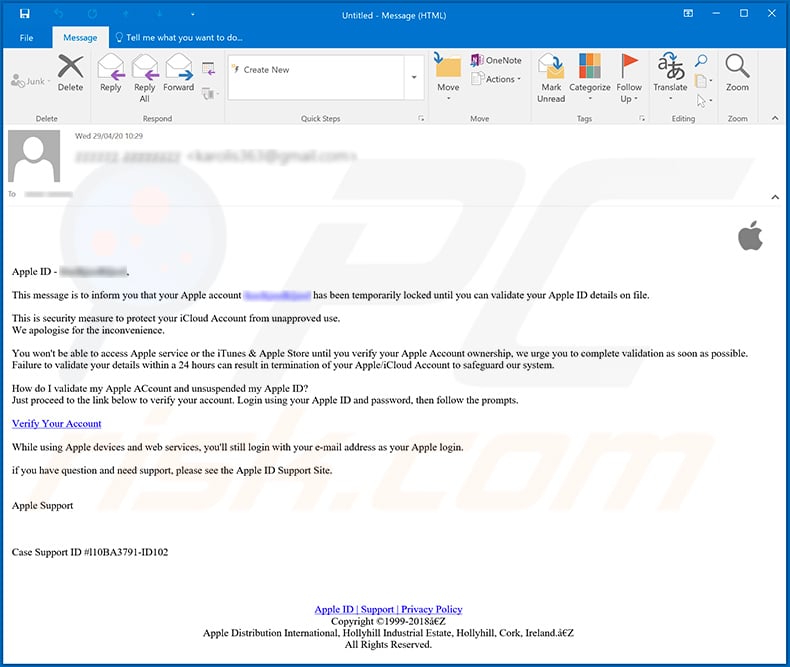
Text presented within:
Apple ID - *****,
This message is to inform you that your Apple account **** has been temporarily locked until you can validate your Apple ID details on file.
This is security measure to protect your iCloud Account from unapproved use.
We apologise for the inconvenience.You won't be able to access Apple service or the iTunes & Apple Store until you verify your Apple Account ownership, we urge you to complete validation as soon as possible. Failure to validate your details within a 24 hours can result in termination of your Apple/iCloud Account to safeguard our system.
How do I validate my Apple ACcount and unsuspended my Apple ID?
Just proceed to the link below to verify your account. Login using your Apple ID and password, then follow the prompts.Verify Your Account
While using Apple devices and web services, you'll still login with your e-mail address as your Apple login.
if you have question and need support, please see the Apple ID Support Site.
Apple SupportCase Support ID #l10BA3791-ID102
Apple ID | Support | Privacy Policy
Copyright ©1999-2018å€Z
Apple Distribution International, Hollyhill Industrial Estate, Hollyhill, Cork, Ireland.å€Z
All Rights Reserved.
Screenshot of yet another PayPal-themed spam email used for phishing purposes (the promoted website was disabled at the time of research):
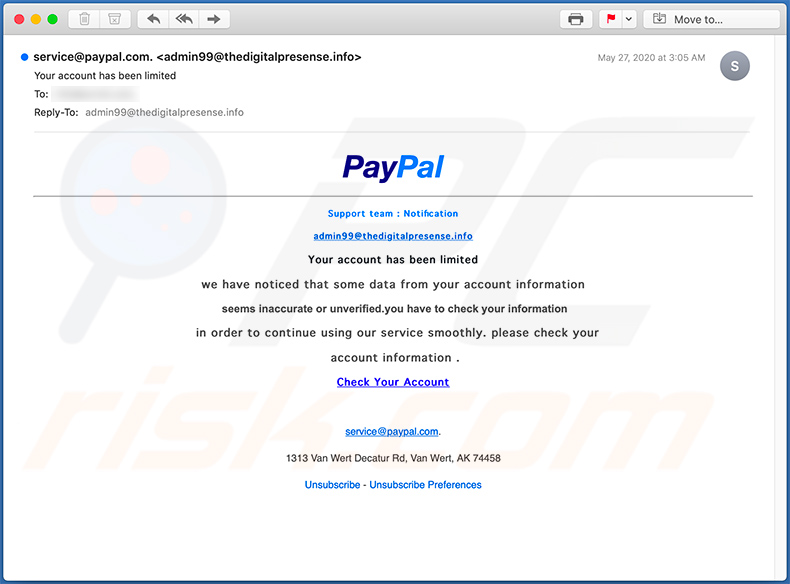
Text presented within:
Subject: Your account has been limited
PayPal
Support team : Notification
admin99@thedigitalpresense.info
Your account has been limited
we have noticed that some data from your account information
seems inaccurate or unverified.you have to check your information
in order to continue using our service smoothly. please check your
account information .
Check Your Account
service@paypal.com.
1313 Van Wert Decatur Rd, Van Wert, AK 74458
Unsubscribe - Unsubscribe Preferences
Yet another PayPal-themed spam email used for phishing purposes:
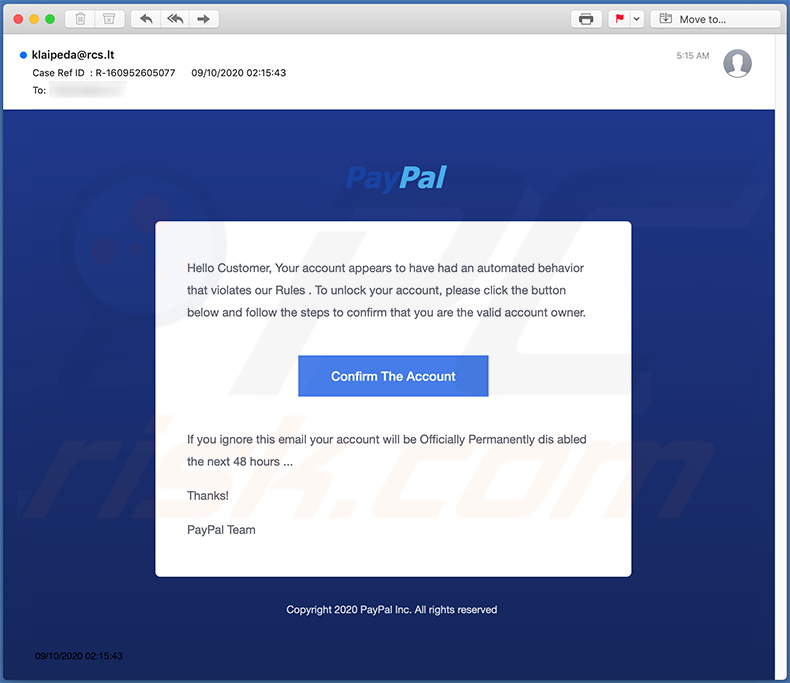
Text presented within:
Subject: Case Ref ID : R-160952605077
PayPal
Hello Customer, Your account appears to have had an automated behavior that violates our Rules . To unlock your account, please click the button below and follow the steps to confirm that you are the valid account owner.Confirm The Account
If you ignore this email your account will be Officially Permanently dis abled the next 48 hours ...Thanks!
PayPal Team
Copyright 2020 PayPal Inc. All rights reserved
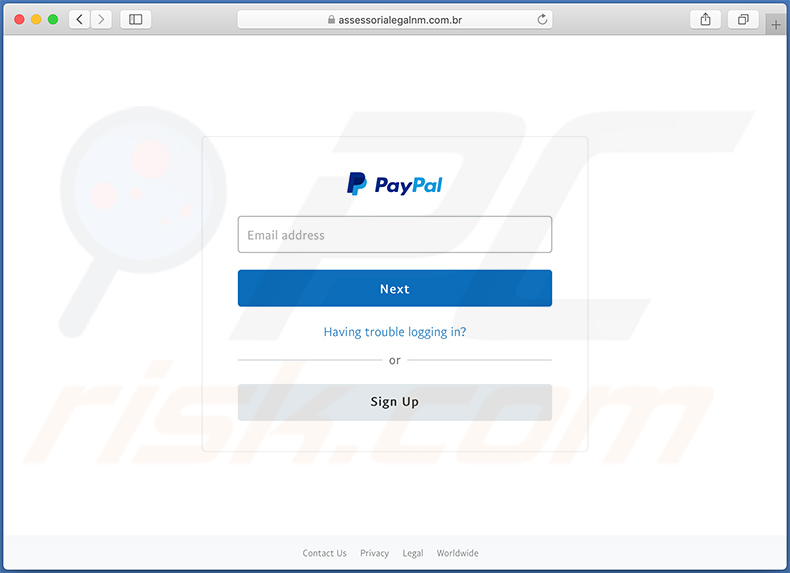
Screenshot of a website promoted using this email:
Yet another PayPal-themed spam emails used to promote a dubious sites:
Example 1:
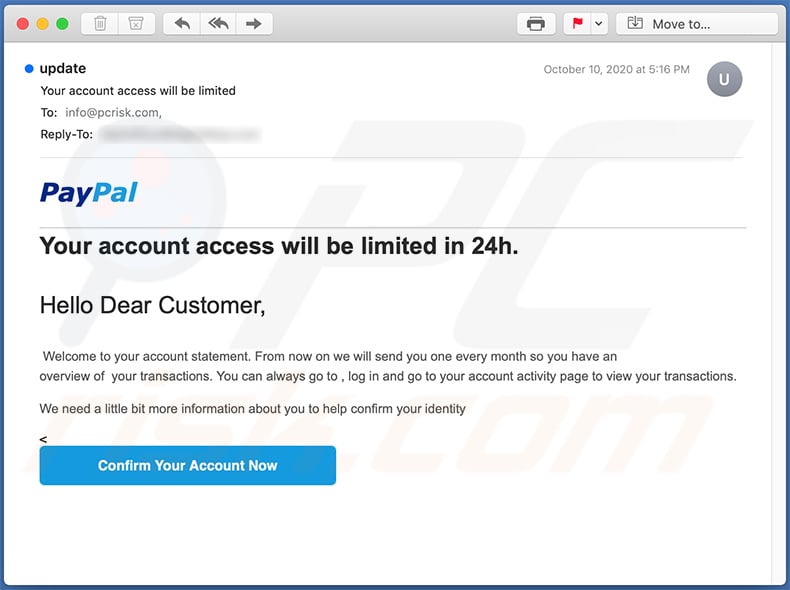
Text presented within:
Subject: Your account access will be limited
PayPal
Your account access will be limited in 24h.
Hello Dear Customer,
Welcome to your account statement. From now on we will send you one every month so you have an overview of your transactions. You can always go to , log in and go to your account activity page to view your transactions.
We need a little bit more information about you to help confirm your identity
<
Confirm Your Account Now
Example 2:
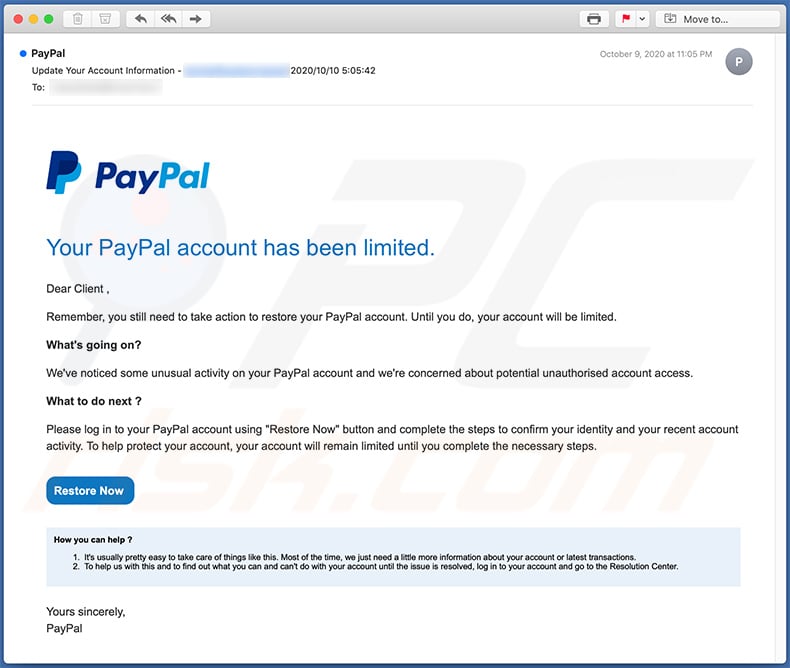
Text presented within:
Subject: Update Your Account Information - 2020/10/10 5:05:42
Your PayPal account has been limited.
Dear Client ,
Remember, you still need to take action to restore your PayPal account. Until you do, your account will be limited.What's going on?
We've noticed some unusual activity on your PayPal account and we're concerned about potential unauthorised account access.
What to do next ?
Please log in to your PayPal account using "Restore Now" button and complete the steps to confirm your identity and your recent account activity. To help protect your account, your account will remain limited until you complete the necessary steps.
Restore Now
How you can help ?It's usually pretty easy to take care of things like this. Most of the time, we just need a little more information about your account or latest transactions.
To help us with this and to find out what you can and can't do with your account until the issue is resolved, log in to your account and go to the Resolution Center.Yours sincerely,
PayPal
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is PayPal spam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
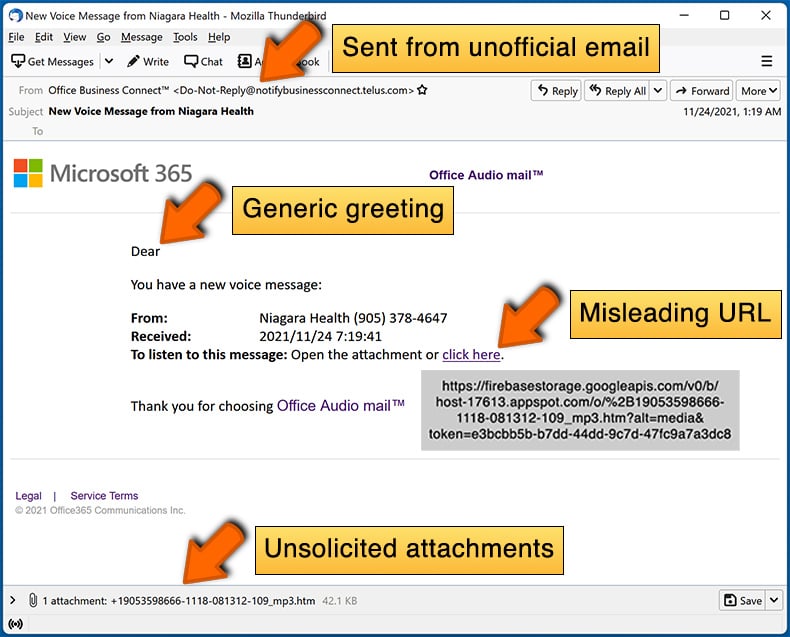
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion