How to remove Power App from web browsers
Browser HijackerAlso Known As: searchpowerapp.com redirect
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What is Power App?
Power App is a browser hijacker, identical to Genius App. This rogue application is advertised as enhancing web searches. It is supposedly capable of fast searches, providing accurate search results, etc., however, it operates by changing browser settings to promote a fake search engine (searchpowerapp.com).
Power App also monitors users' browsing habits and is categorized as a PUA (Potentially Unwanted Application), since users tend to install it onto devices inadvertently.

Google Chrome, Mozilla Firefox, Internet Explorer, and other popular browsers are common targets for browser hijackers. These applications operate by assigning their fake search engine addresses as the browser homepage, default search engines, and new tab/window URL.
Power App promotes searchpowerapp.com in this fashion. Therefore, each new tab/widow opened and each search via the URL bar redirects to searchpowerapp.com. Most fake search tools are unable to generate unique results, and therefore simply redirect to (or cause redirection chains ending with) a legitimate search engine.
As searchpowerapp.com is likewise unable to provide unique results, it enables users to choose which legitimate search engine it will redirect to (Google, Bing, Yahoo, or other). This renders Power App and searchpowerapp.com redundant, since users can of course access legitimate search engines without the interference of third parties.
While changes made by browser hijackers may seem insignificant and relatively easy to undo, this is not the case. Access to browser settings can be limited or denied, and any permissible changes made, simply reset. Therefore, the hijacking application must be removed to recover the affected browser.
As mentioned, Power App also tracks data. By monitoring browsing activity (URLs visited, pages viewed, search queries, etc.), it can gather users' personal information (IP addresses, geolocations, and private details). This collected data is then shared with third parties (potentially, cyber criminals) intent on misusing it for financial gain.
In summary, PUAs can cause browser and system infiltration/infections and lead to serious privacy issues (even identity theft). To ensure device and user safety, all suspicious applications and browser extensions/plug-ins must be removed immediately.
| Name | Power App. |
| Threat Type | Browser Hijacker, Redirect, Search Hijacker, Toolbar, Unwanted New Tab. |
| Browser Extension(s) | Power App. |
| Supposed Functionality | Enhanced web search experience. |
| Promoted URL | searchpowerapp.com |
| Serving IP Address (searchpowerapp.com) | 104.27.160.32 |
| Affected Browser Settings | Homepage, new tab URL, default search engine. |
| Symptoms | Manipulated Internet browser settings (homepage, default Internet search engine, new tab settings). Users are forced to visit the hijacker's website and search the internet using their search engines. |
| Distribution methods | Deceptive pop-up ads, free software installers (bundling), fake flash player installers. |
| Damage | Internet browser tracking (potential privacy issues), display of unwanted ads, redirects to dubious websites. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Online News Now, Current Weather App, GetFlightUpdates, MyImageConverter are a few examples of browser hijackers such as Power App. Nearly all PUAs share certain traits.
Most appear highly legitimate and offer various "useful" and "beneficial" features, however, the only purpose of all unwanted content is to generate revenue for its developers; therefore, all advertised features tend to be nonfunctional.
Rather than delivering any real value, PUAs hijack browsers, cause redirects to untrustworthy and malicious websites, run intrusive advertisement campaigns (pop-ups, surveys, banners, coupons, etc.) and track vulnerable data.
How did Power App install on my computer?
Some PUAs have "official" websites, on which they are often endorsed as "free" software. When time Power App was researched, it was available to download from the official Chrome Web Store, however, unwanted applications can also be installed together with other programs.
This deceptive marketing tactic (packing regular software with unwanted or malicious content) is called "bundling". By rushing through the download/installation processes (ignoring terms, skipping steps, using pre-set options, etc.), many users endanger devices with potential system infections.
Intrusive advertisements are also known to proliferate PUAs. Once clicked, they can execute scripts designed to initiate downloads/installs of these apps.
How to avoid installation of potentially unwanted applications
Verify the legitimacy of software and content, before downloading/installing. Use only trustworthy and official sources for downloading. Peer-to-Peer sharing networks, free file-hosting websites, third party downloaders and similar channels are dangerous, and thus should not be used.
Download and installation processes should be approached with caution. Read the terms, explore possible options, use "Custom/Advanced" settings, and opt-out of downloading/installing any additional software (e.g. apps, tools, features, etc.).
Intrusive advertisements typically seem normal and harmless, however, they often redirect to suspicious websites (e.g. gambling, pornography, adult-dating, and similar). If you experience ads/redirects of this type, inspect the device and remove all dubious applications and/or browser extensions/plug-ins.
If your computer is already infected with Power App, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate this browser hijacker.
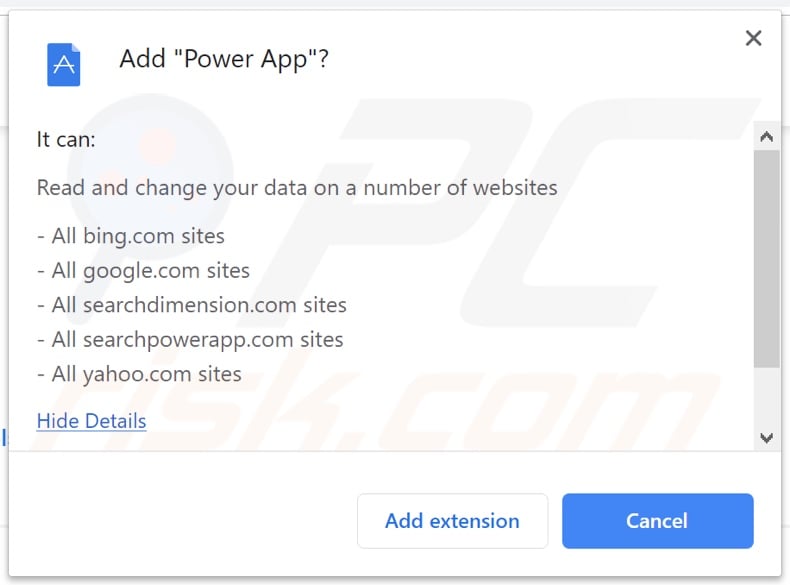
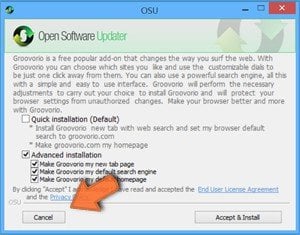
Power App browser hijacker asking for various permissions:
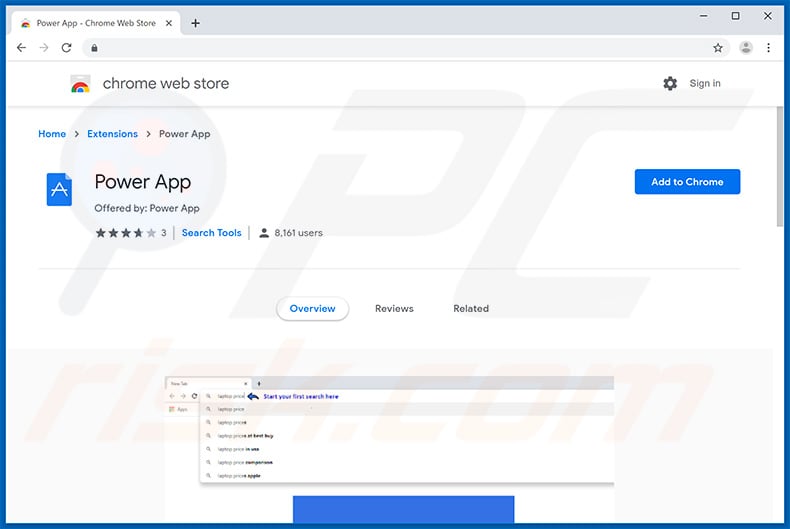
Power App browser hijacker on Chrome Web Store:
Searchdimension.com website promoting Power App browser hijacker:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
- What is Power App?
- STEP 1. Uninstall Power App application using Control Panel.
- STEP 2. Remove searchpowerapp.com redirect from Internet Explorer.
- STEP 3. Remove Power App browser hijacker from Google Chrome.
- STEP 4. Remove searchpowerapp.com homepage and default search engine from Mozilla Firefox.
- STEP 5. Remove searchpowerapp.com redirect from Safari.
- STEP 6. Remove rogue plug-ins from Microsoft Edge.
Power App browser hijacker removal:
Windows 11 users:
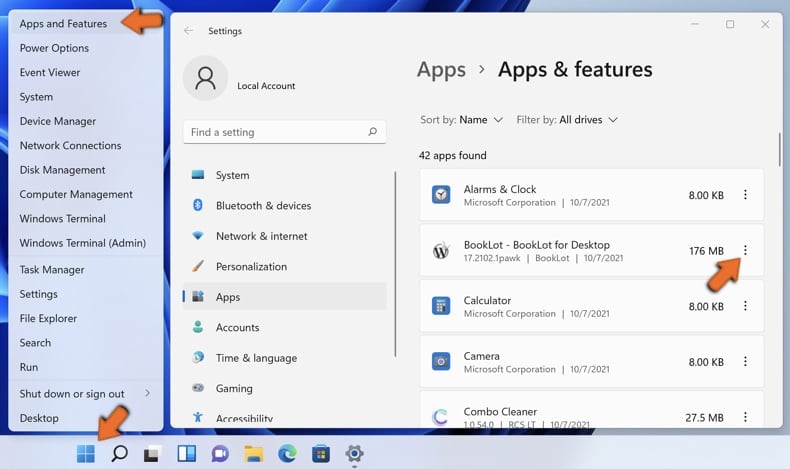
Right-click on the Start icon, select Apps and Features. In the opened window search for the application you want to uninstall, after locating it, click on the three vertical dots and select Uninstall.
Windows 10 users:
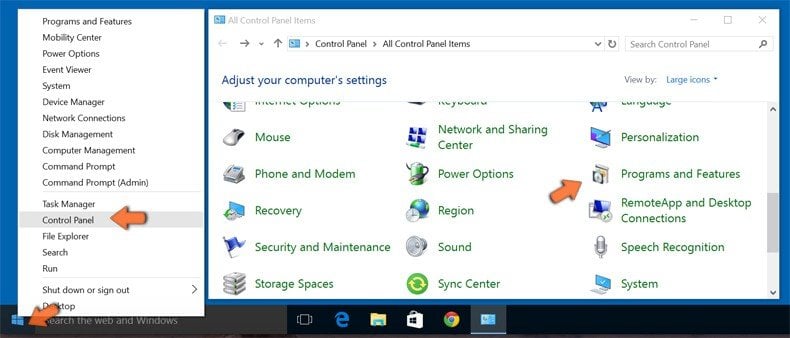
Right-click in the lower left corner of the screen, in the Quick Access Menu select Control Panel. In the opened window choose Programs and Features.
Windows 7 users:
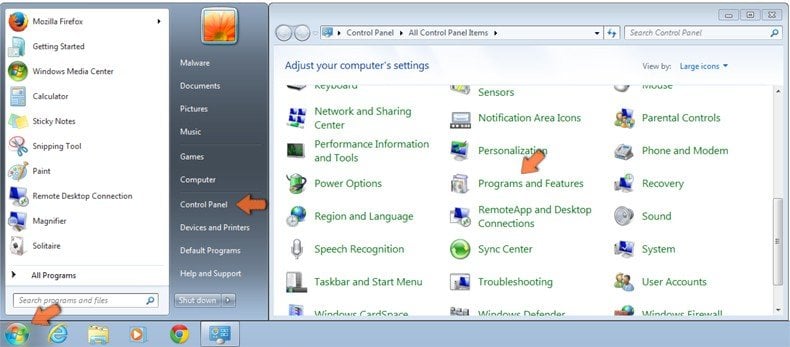
Click Start (Windows Logo at the bottom left corner of your desktop), choose Control Panel. Locate Programs and click Uninstall a program.
macOS (OSX) users:

Click Finder, in the opened screen select Applications. Drag the app from the Applications folder to the Trash (located in your Dock), then right click the Trash icon and select Empty Trash.
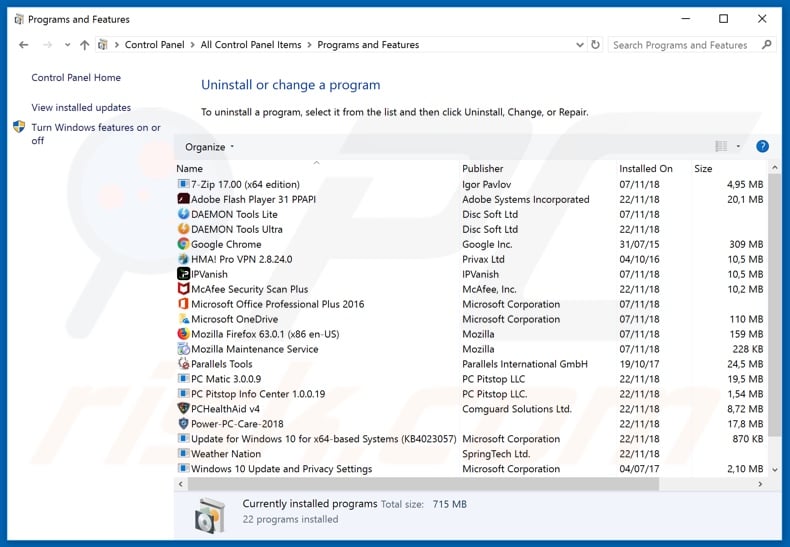
In the uninstall programs window: look for any recently installed suspicious applications (for example, "Power App"), select these entries and click "Uninstall" or "Remove".
After uninstalling the potentially unwanted applications that cause browser redirects to the searchpowerapp.com website, scan your computer for any remaining unwanted components. To scan your computer, use recommended malware removal software.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Power App browser hijacker removal from Internet browsers:
Video showing how to remove browser redirects:
 Remove malicious add-ons from Internet Explorer:
Remove malicious add-ons from Internet Explorer:
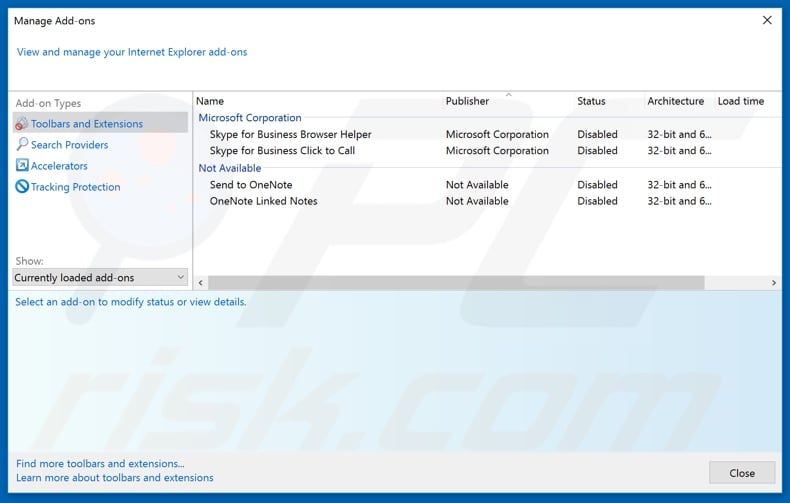
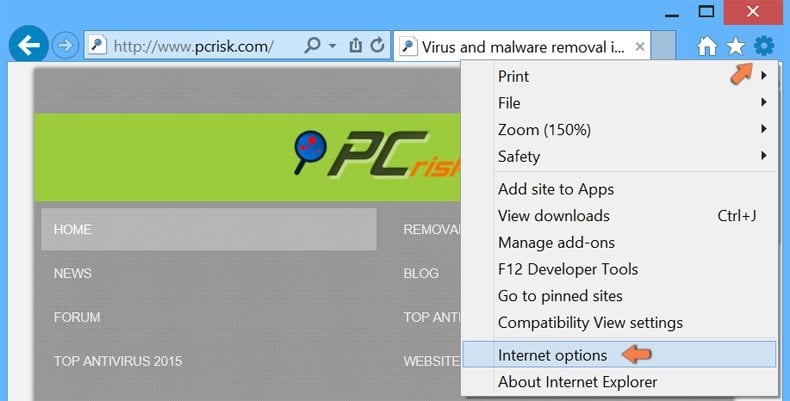
Click the "gear" icon ![]() (at the top right corner of Internet Explorer), select "Manage Add-ons". Look for any recently installed suspicious extensions, select these entries and click "Remove".
(at the top right corner of Internet Explorer), select "Manage Add-ons". Look for any recently installed suspicious extensions, select these entries and click "Remove".
Change your homepage:
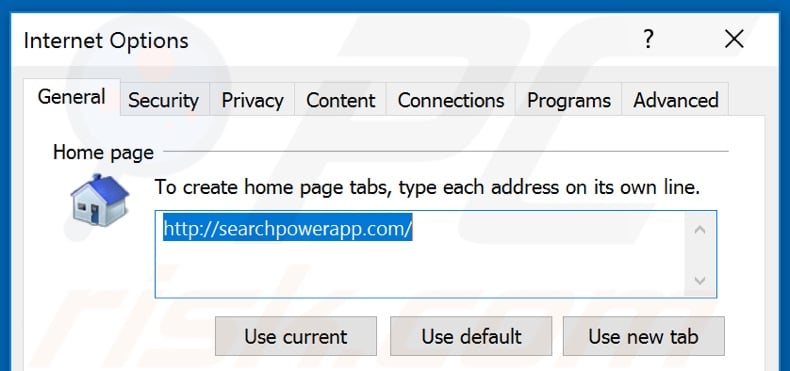
Click the "gear" icon ![]() (at the top right corner of Internet Explorer), select "Internet Options", in the opened window, remove hxxp://searchpowerapp.com and enter your preferred domain, which will open each time you launch Internet Explorer. You can also enter about: blank to open a blank page when you start Internet Explorer.
(at the top right corner of Internet Explorer), select "Internet Options", in the opened window, remove hxxp://searchpowerapp.com and enter your preferred domain, which will open each time you launch Internet Explorer. You can also enter about: blank to open a blank page when you start Internet Explorer.
Change your default search engine:
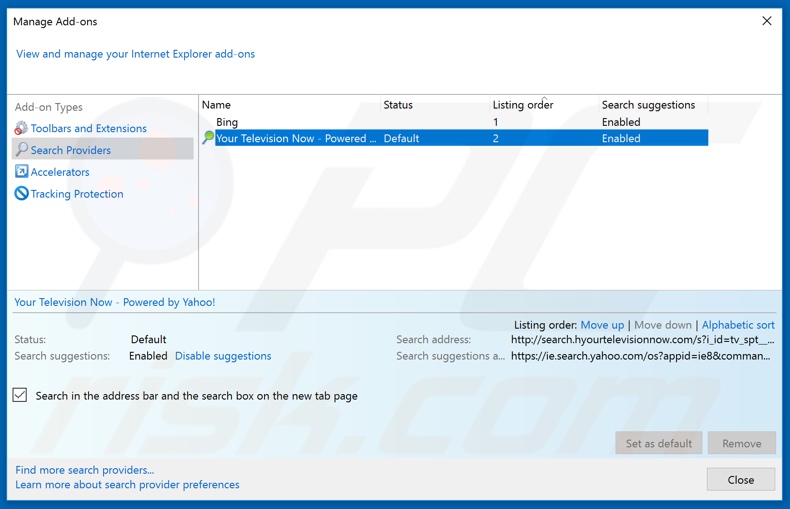
Click the "gear" icon ![]() (at the top right corner of Internet Explorer), select "Manage Add-ons". In the opened window, select "Search Providers", set "Google", "Bing", or any other preferred search engine as your default and then remove "Power App".
(at the top right corner of Internet Explorer), select "Manage Add-ons". In the opened window, select "Search Providers", set "Google", "Bing", or any other preferred search engine as your default and then remove "Power App".
Optional method:
If you continue to have problems with removal of the searchpowerapp.com redirect, reset your Internet Explorer settings to default.
Windows XP users: Click Start, click Run, in the opened window type inetcpl.cpl In the opened window click the Advanced tab, then click Reset.
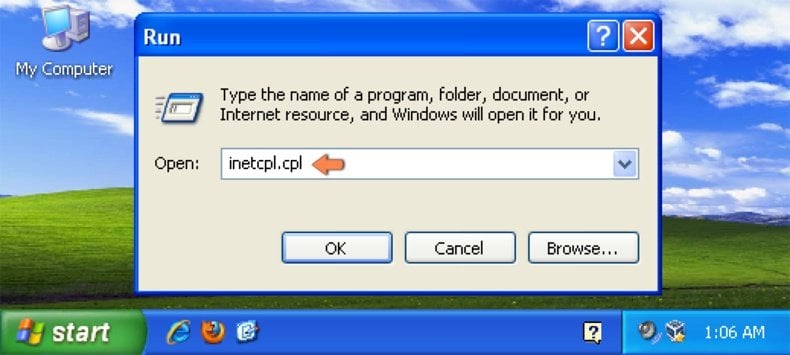
Windows Vista and Windows 7 users: Click the Windows logo, in the start search box type inetcpl.cpl and click enter. In the opened window click the Advanced tab, then click Reset.
Windows 8 users: Open Internet Explorer and click the gear icon. Select Internet Options.
In the opened window, select the Advanced tab.
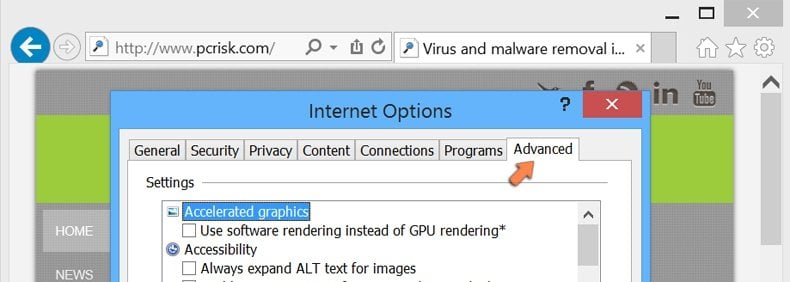
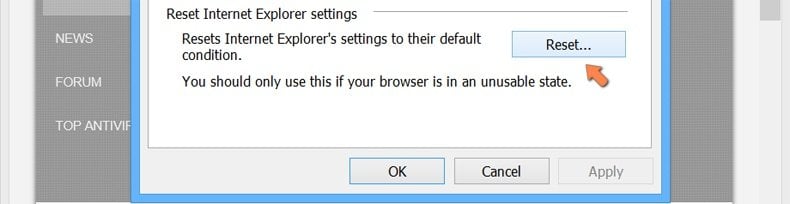
Click the Reset button.
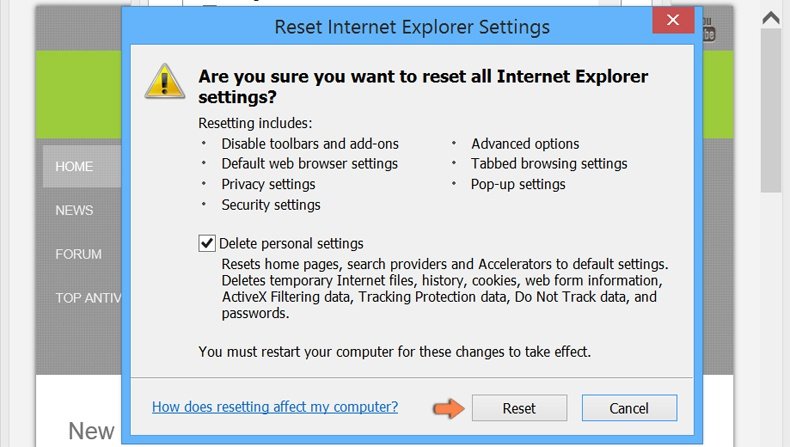
Confirm that you wish to reset Internet Explorer settings to default by clicking the Reset button.
 Remove malicious extensions from Google Chrome:
Remove malicious extensions from Google Chrome:
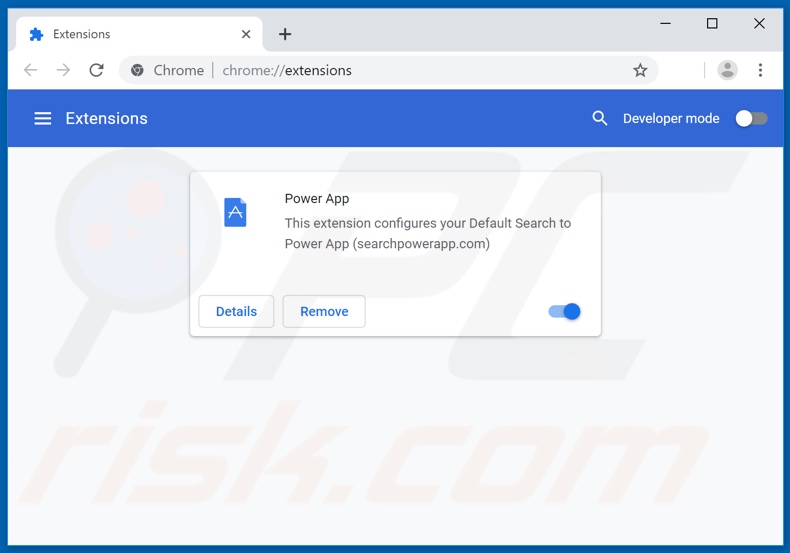
Click the Chrome menu icon ![]() (at the top right corner of Google Chrome), select "More tools" and click "Extensions". Locate "Power App" and other recently-installed suspicious browser add-ons, and remove them.
(at the top right corner of Google Chrome), select "More tools" and click "Extensions". Locate "Power App" and other recently-installed suspicious browser add-ons, and remove them.
Change your homepage:
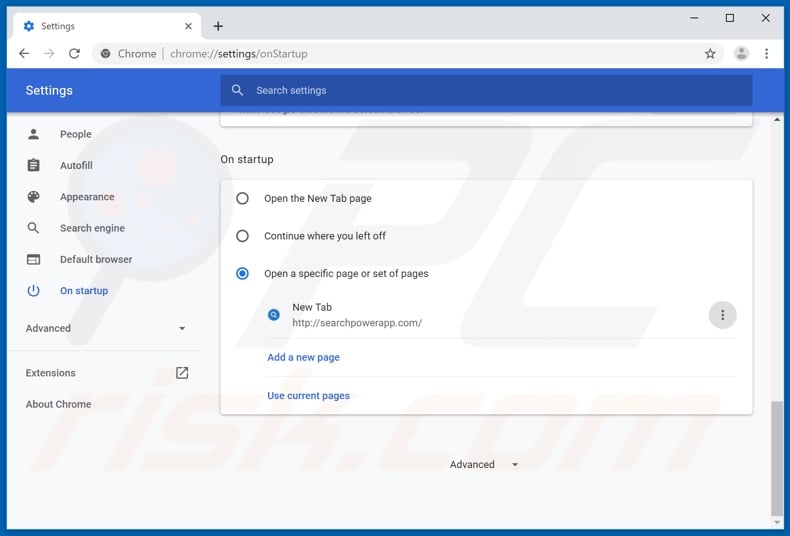
Click the Chrome menu icon ![]() (at the top right corner of Google Chrome), select "Settings". In the "On startup" section, disable "Power App", look for a browser hijacker URL (hxxp://www.searchpowerapp.com) below the “Open a specific or set of pages” option. If present, click on the three vertical dots icon and select “Remove”.
(at the top right corner of Google Chrome), select "Settings". In the "On startup" section, disable "Power App", look for a browser hijacker URL (hxxp://www.searchpowerapp.com) below the “Open a specific or set of pages” option. If present, click on the three vertical dots icon and select “Remove”.
Change your default search engine:
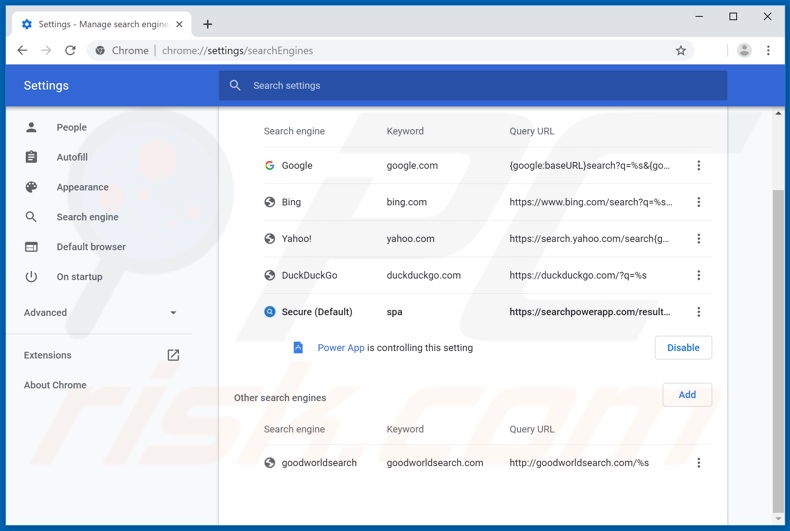
To change your default search engine in Google Chrome: Click the Chrome menu icon ![]() (at the top right corner of Google Chrome), select "Settings", in the "Search engine" section, click "Manage search engines...", in the opened list, look for "searchpowerapp.com", and when located, click the three vertical dots near this URL and select "Remove from list".
(at the top right corner of Google Chrome), select "Settings", in the "Search engine" section, click "Manage search engines...", in the opened list, look for "searchpowerapp.com", and when located, click the three vertical dots near this URL and select "Remove from list".
Optional method:
If you continue to have problems with removal of the searchpowerapp.com redirect, reset your Google Chrome browser settings. Click the Chrome menu icon ![]() (at the top right corner of Google Chrome) and select Settings. Scroll down to the bottom of the screen. Click the Advanced… link.
(at the top right corner of Google Chrome) and select Settings. Scroll down to the bottom of the screen. Click the Advanced… link.
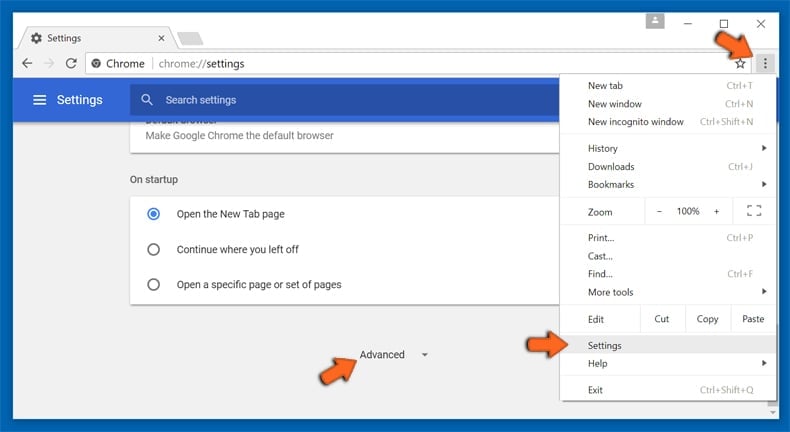
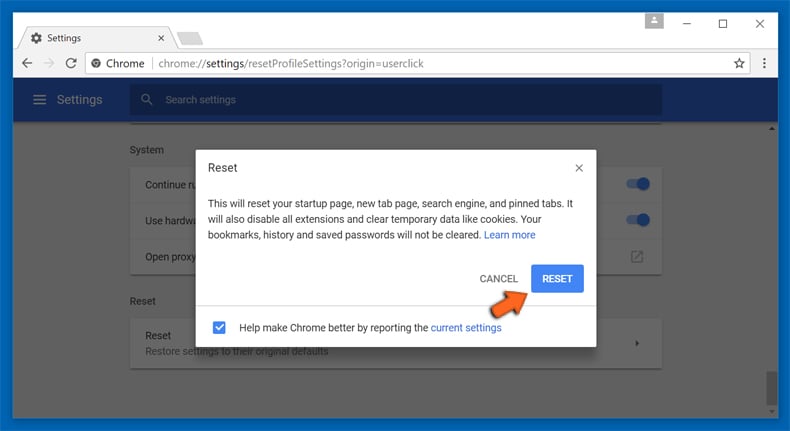
After scrolling to the bottom of the screen, click the Reset (Restore settings to their original defaults) button.
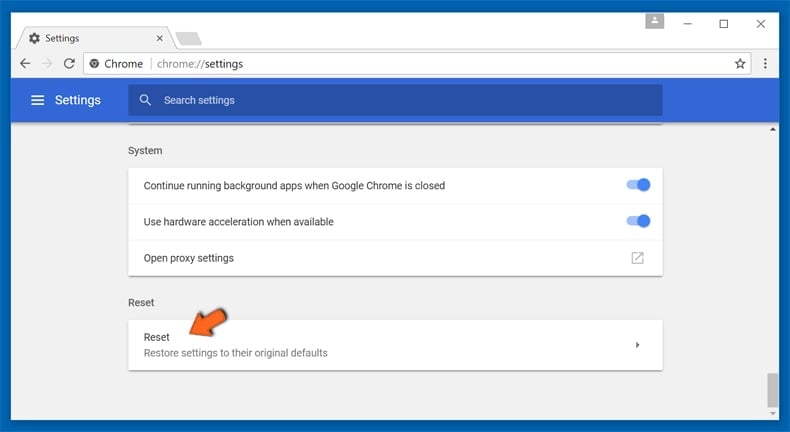
In the opened window, confirm that you wish to reset Google Chrome settings to default by clicking the Reset button.
 Remove malicious plug-ins from Mozilla Firefox:
Remove malicious plug-ins from Mozilla Firefox:
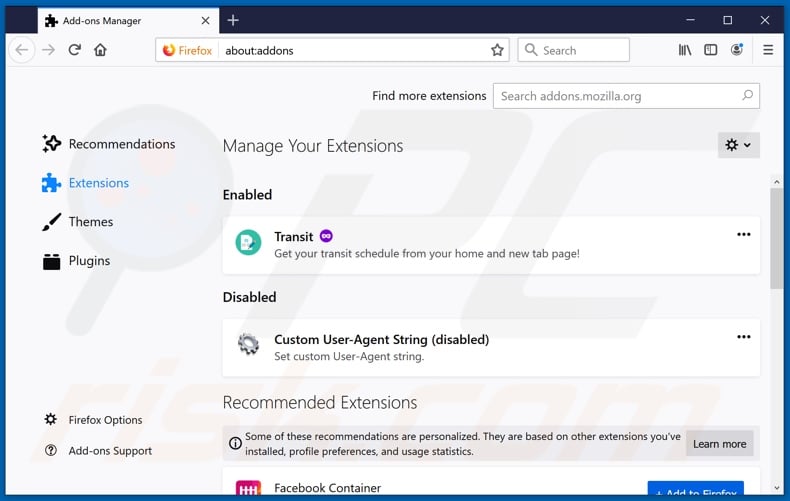
Click the Firefox menu ![]() (at the top right corner of the main window), select "Add-ons". Click on "Extensions" and remove "Power App", as well as all other recently installed browser plug-ins.
(at the top right corner of the main window), select "Add-ons". Click on "Extensions" and remove "Power App", as well as all other recently installed browser plug-ins.
Change your homepage:
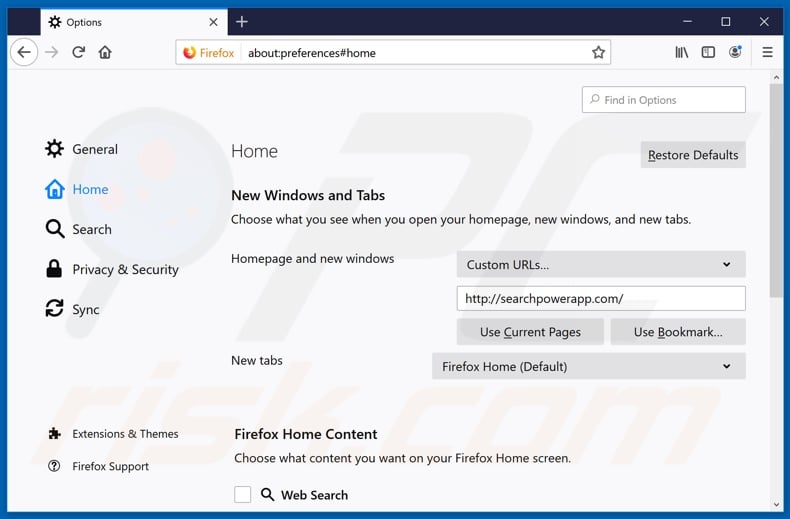
To reset your homepage, click the Firefox menu ![]() (at the top right corner of the main window), then select "Options", in the opened window, disable "Power App", remove hxxp://searchpowerapp.com and enter your preferred domain, which will open each time you start Mozilla Firefox.
(at the top right corner of the main window), then select "Options", in the opened window, disable "Power App", remove hxxp://searchpowerapp.com and enter your preferred domain, which will open each time you start Mozilla Firefox.
Change your default search engine:
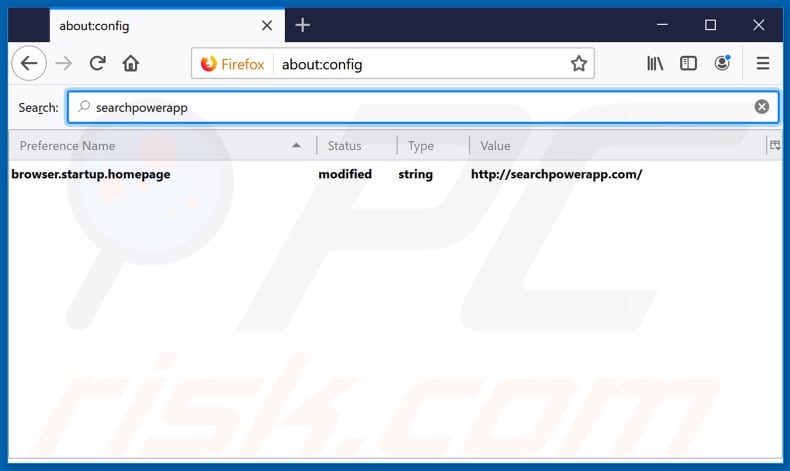
In the URL address bar, type about:config and press Enter.
Click "I'll be careful, I promise!".
In the search filter at the top, type: "moz-extension"
Right-click on the found preferences and select "Reset" to restore default values.
Optional method:
Computer users who have problems with searchpowerapp.com redirect removal can reset their Mozilla Firefox settings.
Open Mozilla Firefox, at the top right corner of the main window, click the Firefox menu, ![]() in the opened menu, click Help.
in the opened menu, click Help.
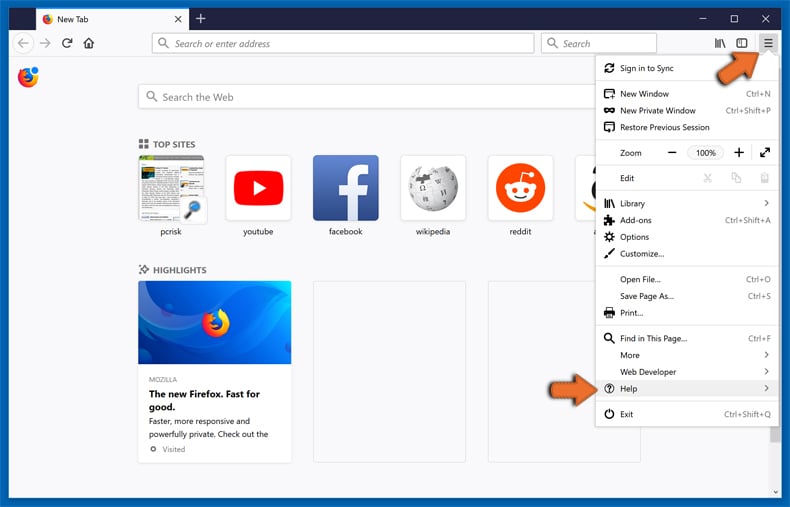
Select Troubleshooting Information.
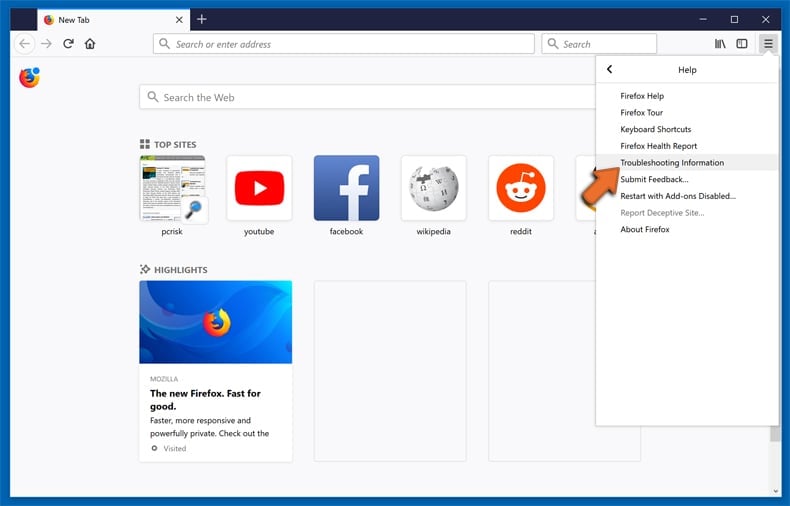
In the opened window, click the Refresh Firefox button.
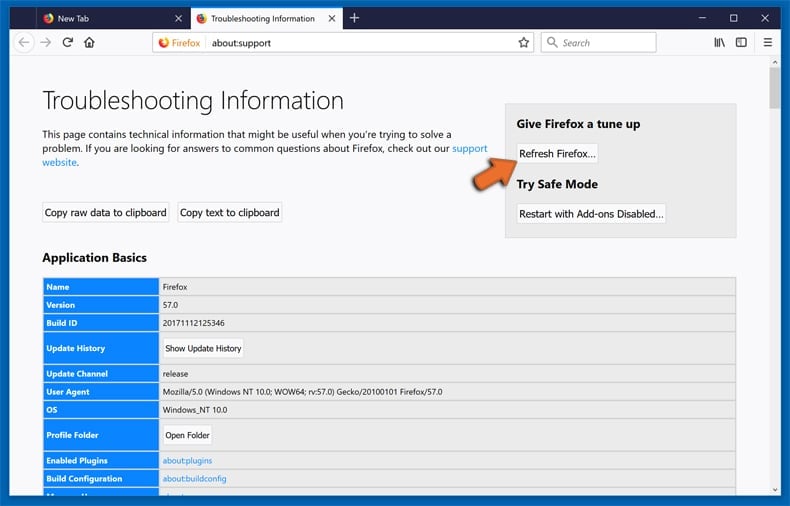
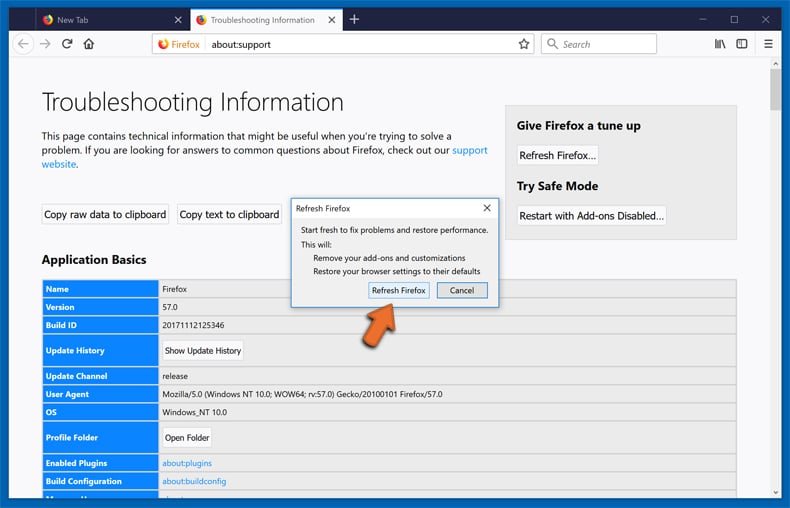
In the opened window, confirm that you wish to reset Mozilla Firefox settings to default by clicking the Refresh Firefox button.
 Remove malicious extensions from Safari:
Remove malicious extensions from Safari:
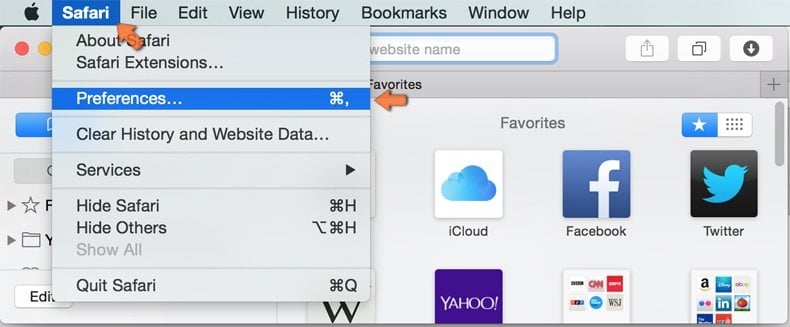
Make sure your Safari browser is active and click Safari menu, then select Preferences...
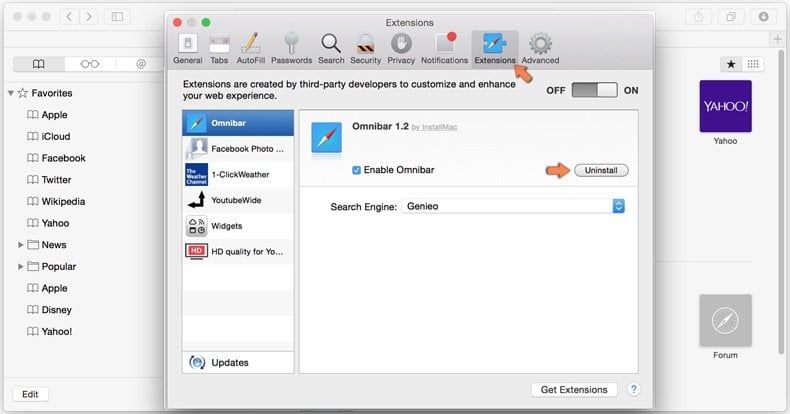
In the preferences window select the Extensions tab. Look for any recently installed suspicious extensions and uninstall them.
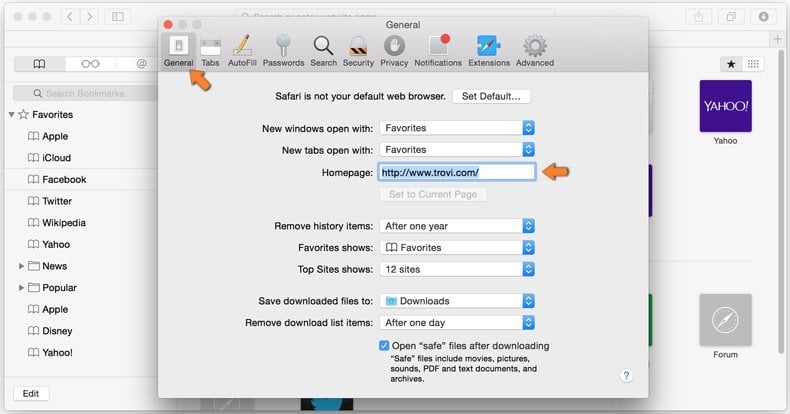
In the preferences window select General tab and make sure that your homepage is set to a preferred URL, if its altered by a browser hijacker - change it.
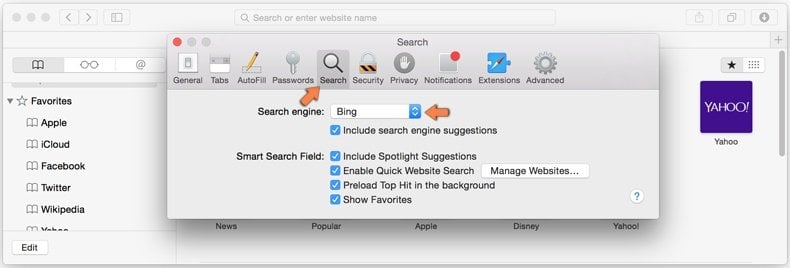
In the preferences window select Search tab and make sure that your preferred Internet search engine is selected.
Optional method:
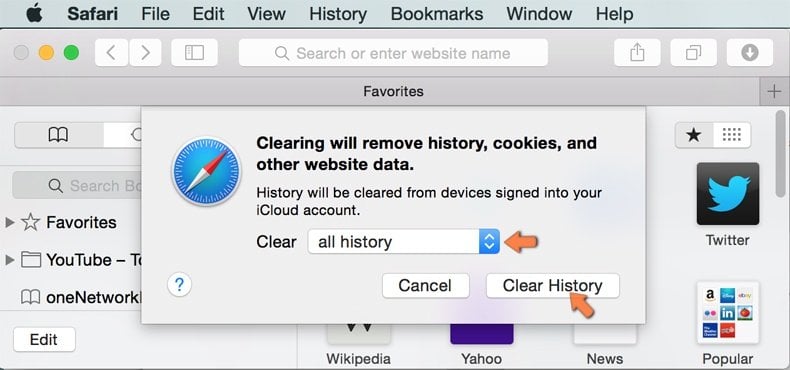
Make sure your Safari browser is active and click on Safari menu. From the drop down menu select Clear History and Website Data...
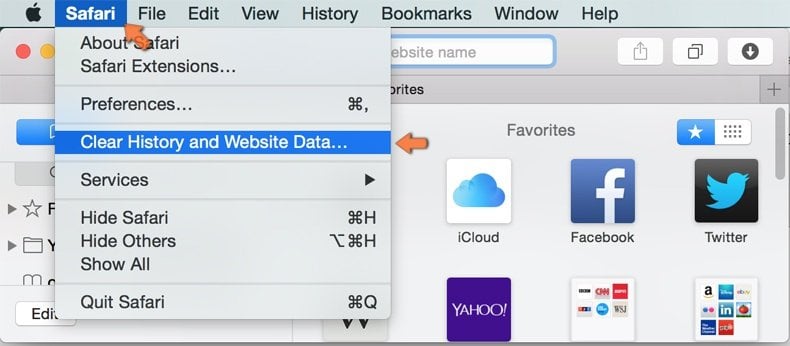
In the opened window select all history and click the Clear History button.
 Remove malicious extensions from Microsoft Edge:
Remove malicious extensions from Microsoft Edge:
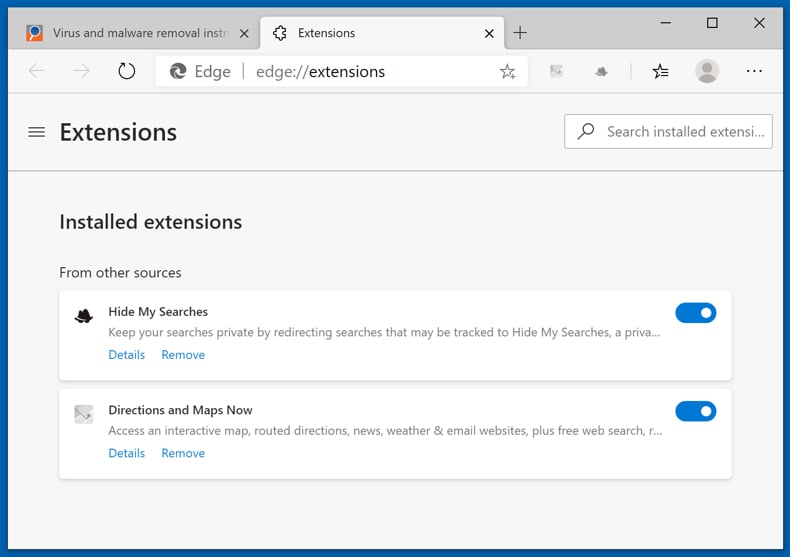
Click the Edge menu icon ![]() (at the top right corner of Microsoft Edge), select "Extensions". Locate any recently-installed suspicious browser add-ons, and remove them.
(at the top right corner of Microsoft Edge), select "Extensions". Locate any recently-installed suspicious browser add-ons, and remove them.
Change your homepage and new tab settings:
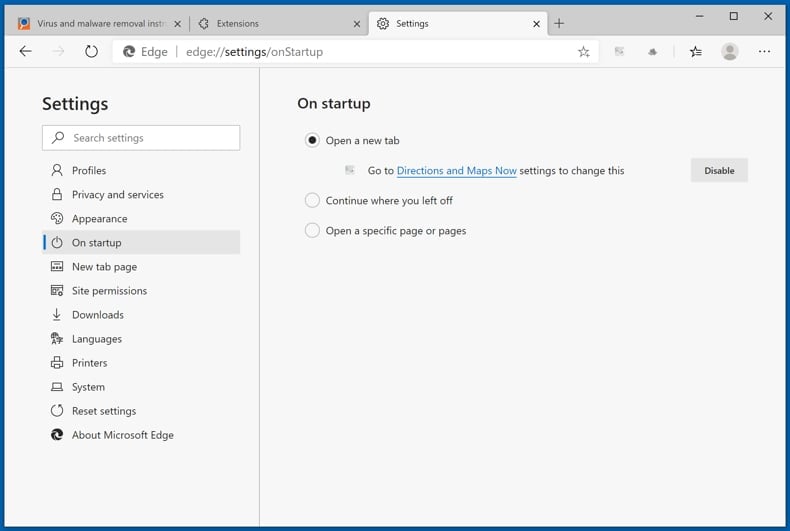
Click the Edge menu icon ![]() (at the top right corner of Microsoft Edge), select "Settings". In the "On startup" section look for the name of the browser hijacker and click "Disable".
(at the top right corner of Microsoft Edge), select "Settings". In the "On startup" section look for the name of the browser hijacker and click "Disable".
Change your default Internet search engine:
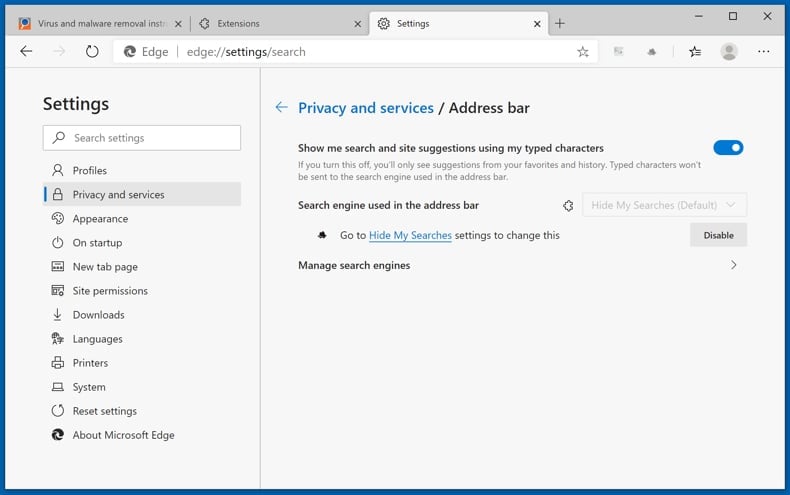
To change your default search engine in Microsoft Edge: Click the Edge menu icon ![]() (at the top right corner of Microsoft Edge), select "Privacy and services", scroll to bottom of the page and select "Address bar". In the "Search engines used in address bar" section look for the name of the unwanted Internet search engine, when located click the "Disable" button near it. Alternatively you can click on "Manage search engines", in the opened menu look for unwanted Internet search engine. Click on the puzzle icon
(at the top right corner of Microsoft Edge), select "Privacy and services", scroll to bottom of the page and select "Address bar". In the "Search engines used in address bar" section look for the name of the unwanted Internet search engine, when located click the "Disable" button near it. Alternatively you can click on "Manage search engines", in the opened menu look for unwanted Internet search engine. Click on the puzzle icon ![]() near it and select "Disable".
near it and select "Disable".
Optional method:
If you continue to have problems with removal of the searchpowerapp.com redirect, reset your Microsoft Edge browser settings. Click the Edge menu icon ![]() (at the top right corner of Microsoft Edge) and select Settings.
(at the top right corner of Microsoft Edge) and select Settings.
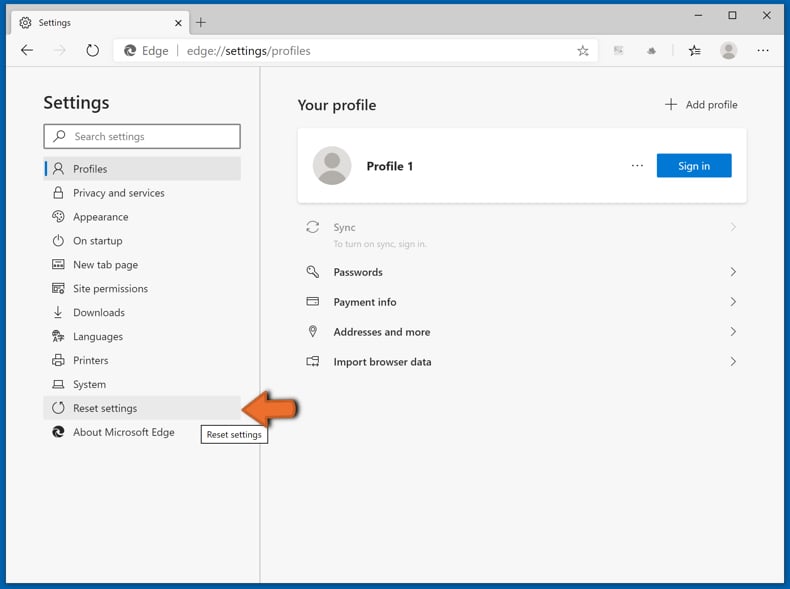
In the opened settings menu select Reset settings.
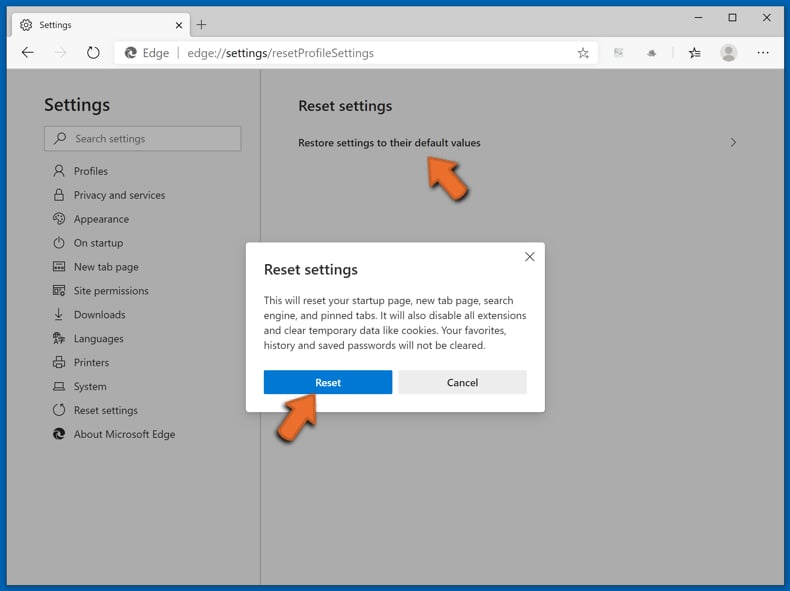
Select Restore settings to their default values. In the opened window, confirm that you wish to reset Microsoft Edge settings to default by clicking the Reset button.
- If this did not help, follow these alternative instructions explaining how to reset the Microsoft Edge browser.
Summary:
 A browser hijacker is a type of adware infection that modifies Internet browser settings by assigning the homepage and default Internet search engine settings to some other (unwanted) website URL. Commonly, this type of adware infiltrates operating systems through free software downloads. If your download is managed by a download client, ensure that you decline offers to install advertised toolbars or applications that seek to change your homepage and default Internet search engine settings.
A browser hijacker is a type of adware infection that modifies Internet browser settings by assigning the homepage and default Internet search engine settings to some other (unwanted) website URL. Commonly, this type of adware infiltrates operating systems through free software downloads. If your download is managed by a download client, ensure that you decline offers to install advertised toolbars or applications that seek to change your homepage and default Internet search engine settings.
Post a comment:
If you have additional information on searchpowerapp.com redirect or it's removal please share your knowledge in the comments section below.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion