How to remove the fake Google Drive browser extension
Browser HijackerAlso Known As: Illegitimate Google Drive browser extension
Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What kind of software is fake Google Drive extension?
While investigating dubious websites, our research team found a deceptive page promoting an installer containing this fake Google Drive browser extension. This piece of malicious software has data-stealing capabilities, and it can display spam browser notifications.
It must be emphasized that this extension is fake, and it is in no way associated with the actual Google Drive file storage and synchronization service or its developer – Google.
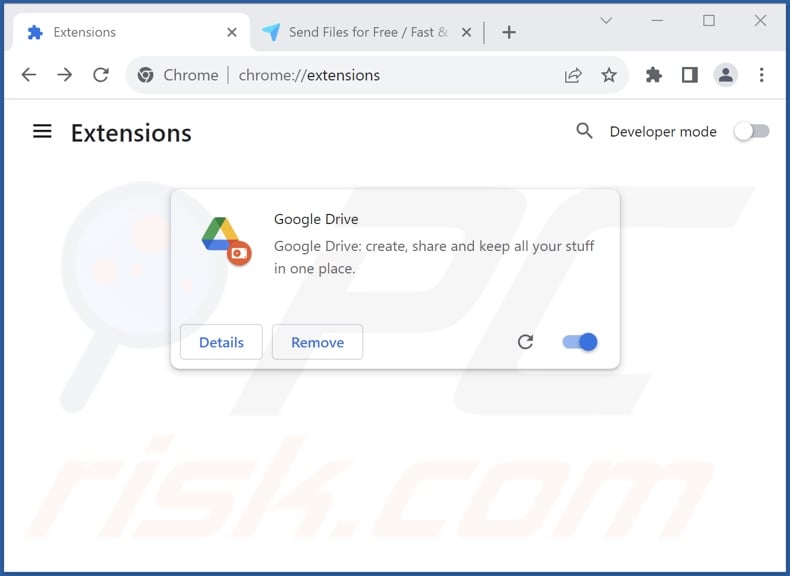
Fake Google Drive extension overview
After launching an installation setup containing this fake Google Drive extension, we found that it was not installed onto the Google Chrome browser. Rather, the installer dropped the extension's folder – named "Default" – into the "C:\Users\[username]\AppData\Local folder.
Thus, creating a persistence mechanism, as deleting the extension through Chrome will not eliminate it; the fake Google Drive extension will simply reappear once the browser is relaunched.
Furthermore, the Chrome browser's shortcut had its target modified by appending --load-extension="C:\Users\[username]\AppData\Local\Default". Removal steps for this malicious extension can be found below.
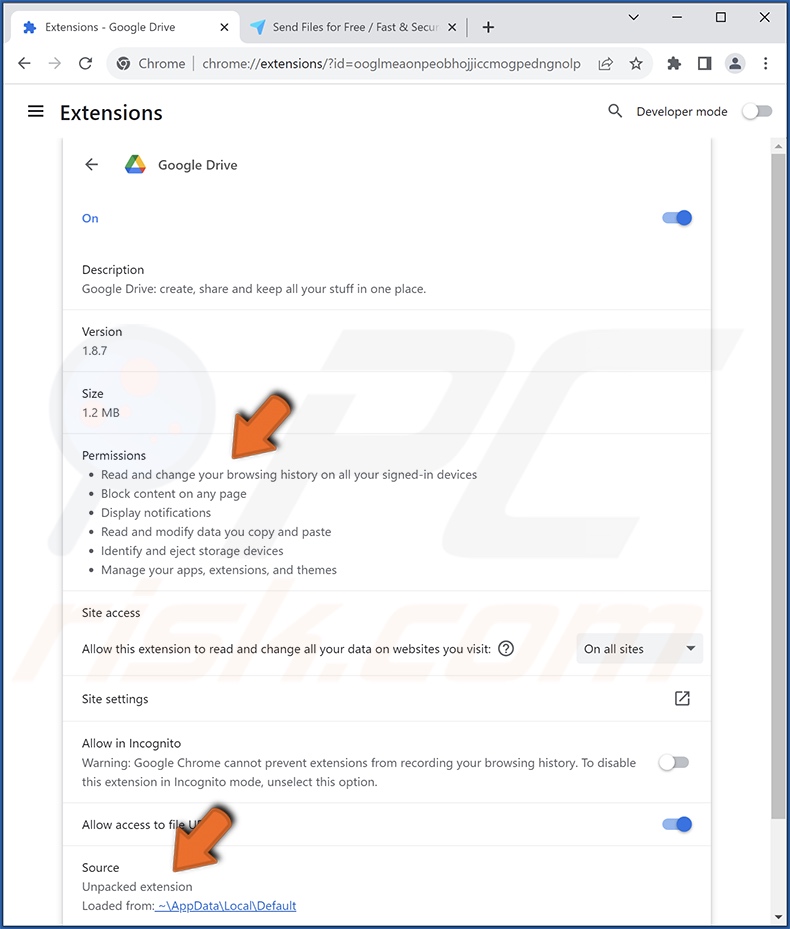
The fake Google Drive extension obtains various permissions following installation. It can spam users with browser notifications. These ads (when delivered by dubious extensions or sites) typically promote online scams, untrustworthy/harmful software, and even malware.
Additionally, this fake extension can obtain the browsing histories from all connected devices. In most cases, malicious software also targets the following data from browsers: Internet cookies, stored log-in credentials (usernames/passwords), personally identifiable details, saved credit card numbers, etc. The collected information can then be sold to third-parties or otherwise abused for profit.
Since the fake Google Drive extension can manage content installed onto browsers, it may be capable of obtaining data from various password managers, cryptocurrency-related extensions, and so on.
This malicious extension can likewise read and alter data copy-pasted on browsers. This feature could be used as a clipper – a type of software that detects when a cryptowallet address is copied and pastes that of a wallet belonging to cyber criminals, thereby rerouting outgoing transfers.
To summarize, the presence of software like this fake Google Drive extension on devices may lead to system infections, serious privacy issues, financial losses, and identity theft.
| Name | Fake Google Drive extension |
| Threat Type | Malicious browser extension, browser hijacker |
| Browser Extension(s) | Google Drive |
| Detection Names (installer) | N/A (VirusTotal) |
| Detection Names (Default folder) | Avast (Other:Malware-gen [Trj]), Combo Cleaner (JS:Trojan.Cryxos.13013), ClamAV (Js.Infostealer.Rilide-10007388-0), Emsisoft (JS:Trojan.Cryxos.13013 (B)), GData (JS:Trojan.Cryxos.13013 (2x)), Full List Of Detections (VirusTotal) |
| Symptoms | Manipulated Internet browser settings, spam notifications (ads). |
| Distribution methods | Deceptive pop-up ads, free software installers (bundling). |
| Damage | Internet browser tracking (potential privacy issues), display of unwanted ads, redirects to dubious websites. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Rogue browser extension examples
We have analyzed thousands of rogue browser extensions. The majority boast adware or browser hijacker capabilities, and practically all have some manner of data-tracking functionalities. Users are often lured into downloading/installing such software by promises of "handy" features, which are rarely operational.
In some cases, developers of malicious extensions use the names of legitimate products/services or outright spoof them. For example, "Chrome", "Google Translate", "Google Docs" – are a few examples of extensions disguised as Google products, and "AdBlock — best ad blocker", "Coinbase Wallet", "Avg Antivirus" – are a couple of miscellaneous ones using genuine names.
How did fake Google Drive extension install on my computer?
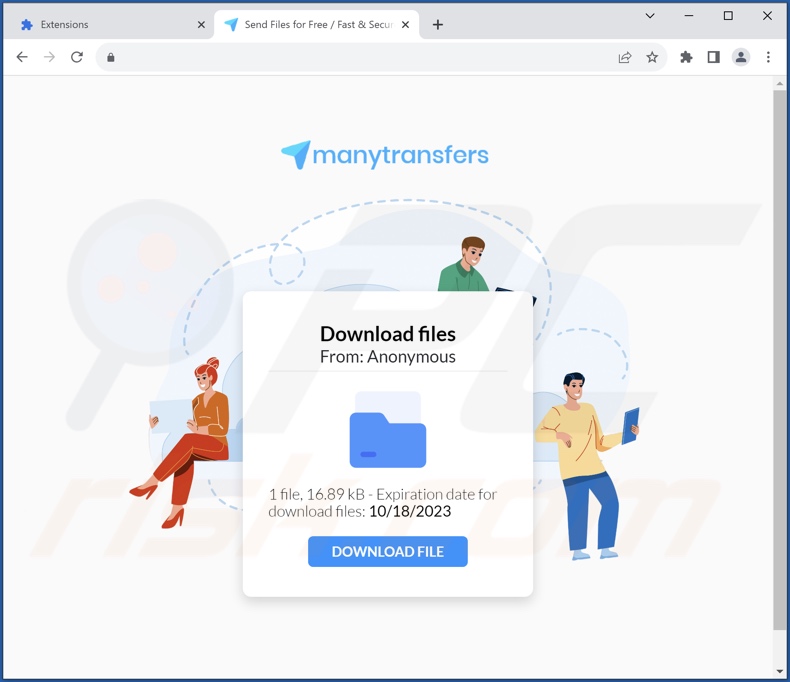
We downloaded a setup containing the fake Google Drive extension from a deceptive webpage. Various scam sites are used to proliferate rogue software, e.g., barebone pages instructing visitors to download content, alerting of present device infections, urging software updates, etc.
However, legitimate-looking "official" promotional webpages are used as well. Most users access these pages via redirects generated by mistyped URLs, websites utilizing rogue advertising networks, spam browser notifications, intrusive ads, or installed adware.
Another widespread distribution technique is "bundling" – packing ordinary program installers with unwanted/malicious additions.
The risk of allowing bundled content into the system is increased by downloading from untrustworthy channels (e.g., freeware and third-party sites, P2P sharing networks, etc.) and by rushing through installation processes (e.g., ignoring terms, skipping steps, using "Easy/Quick" settings, etc.).
Intrusive advertisements are used in software proliferation as well. Some of these adverts can be triggered (i.e., by being clicked) to execute scripts that perform stealthy downloads/installations.
How to avoid installation of rogue browser extensions?
It is essential to research software and download it only from official/verified sources. When installing, we recommend reading terms, inspecting possible options, using the "Custom/Advanced" settings, and opting out of all additional apps, extensions, tools, features, etc.
We also advise being vigilant when browsing since fraudulent and dangerous online content typically appears legitimate and innocuous. For example, while intrusive ads may look harmless – they redirect to highly questionable websites (e.g., gambling, scam-promoting, adult dating, pornography, etc.).
In case of continuous encounters with such adverts/redirects, check the system and immediately remove all suspect applications and browser extensions/plug-ins. If your computer is already infected with fake Google Drive extension, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate this software.
Deceptive website promoting this fake Google Drive extension:
Fake Google Drive extension's detailed information (including permissions):
Removal steps for this fake Google Drive extension:
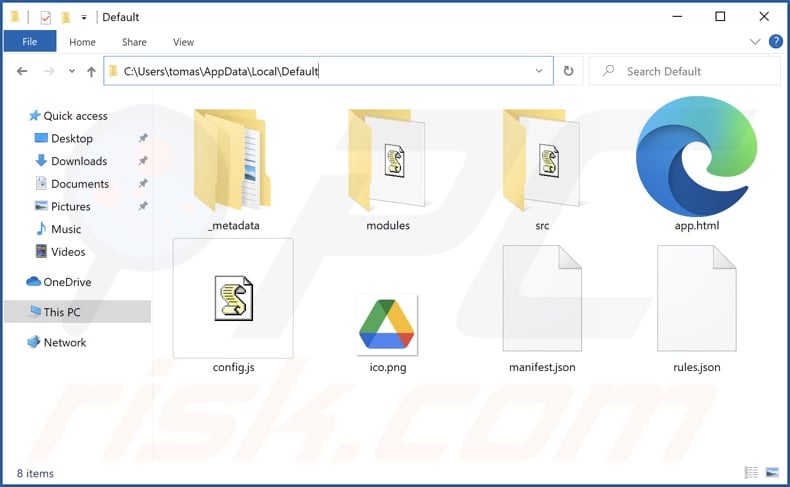
Delete the installation folder of the fake Google Drive extension – titled "Default" – from the AppData\Local folder (i.e., delete C:\Users\[username]\AppData\Local\Default).
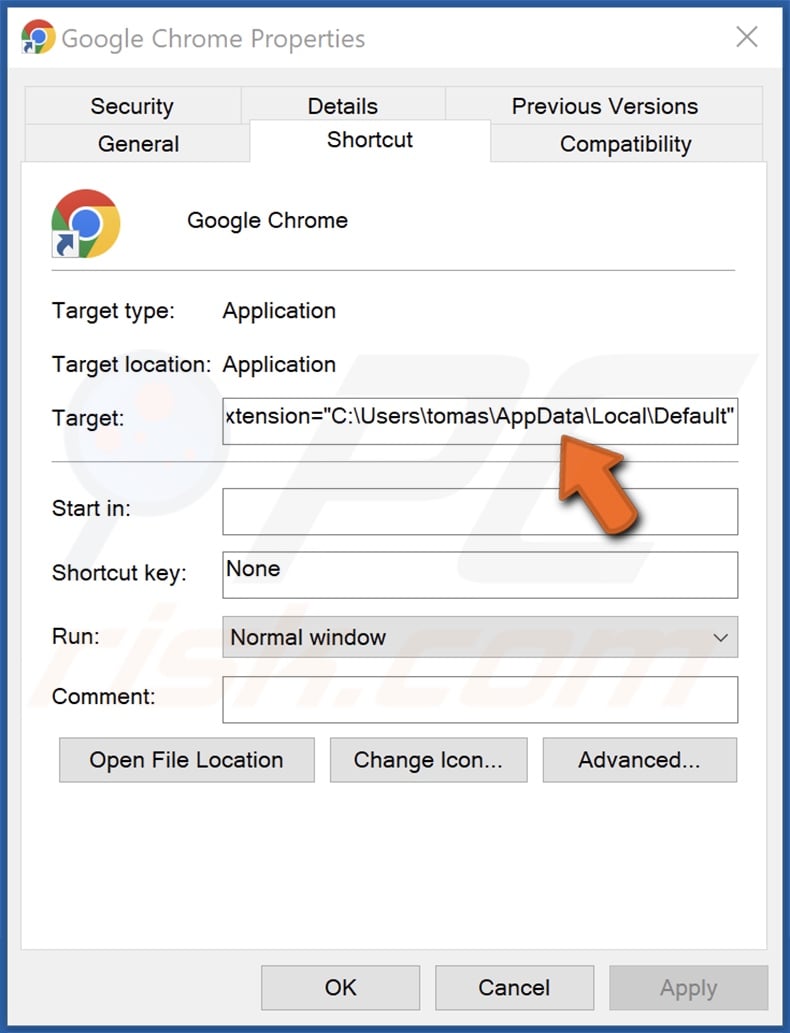
Delete the appendix – --load-extension="C:\Users\[username]\AppData\Local\Default – from the target of Chrome browser's shortcut.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
Video showing how to remove fake Google Drive extension using Combo Cleaner:
Frequently Asked Questions (FAQ)
What harm can rogue extensions cause?
The threats associated with any piece of harmful software depend on its capabilities. Rogue browser extensions commonly have adware or browser hijacker functionalities. This fake Google Drive extension can display spam browser notifications (oftentimes used to promote scams and unreliable/malicious software), and it collects private user data. Generally, software of this kind can cause system infections, severe privacy issues, financial losses, and identity theft.
How do rogue extension developers generate revenue?
Typically, developers of rogue browser extensions profit by selling/abusing sensitive information and/or by promoting content (e.g., websites, products, software, etc.). The fake Google Drive extension has data-stealing abilities; thus, it generates revenue primarily by following the former model.
How did a fake Google Drive extension infiltrate my computer?
We downloaded a fake Google Drive extension in an installer promoted by a deceptive webpage. In addition to such sites, rogue browser extensions are commonly distributed through online scams, bundled installation setups, freeware and free file-hosting websites, P2P sharing networks, spam browser notifications, and intrusive advertisements.
Will Combo Cleaner remove rogue extensions?
Yes, Combo Cleaner is designed to detect and eliminate all manner of threats. It is pertinent to mention that manual removal (unaided by security tools) might be ineffective. In some cases, after the rogue software has been manually removed – various file leftovers remain hidden within the system. Furthermore, the components may continue to run and cause problems. Hence, it is paramount to eliminate software thoroughly.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion