Get free scan and check if your device is infected.
Remove it nowTo use full-featured product, you have to purchase a license for Combo Cleaner. Seven days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
What kind of malware is PondRAT?
PondRAT is a malicious software targeting Mac OSes. It is classed as a Remote Access Trojan (RAT). These trojans tend to be versatile, and their purpose is to allow remote access/control over infected devices.
Code similarities with malware (e.g., POOLRAT) used by Gleaming Pisces (aka Citrine Sleet) have led to the speculation that this threat actor group is behind PondRAT. Gleaming Pisces has North Korean affiliations.
This RAT has been observed being distributed via virulent Python software packages through PyPI (Python Package Index). Based on previous attacks, it is likely that the goal is to gain access to supply chain vendors via developers in order to infect the former's customers.
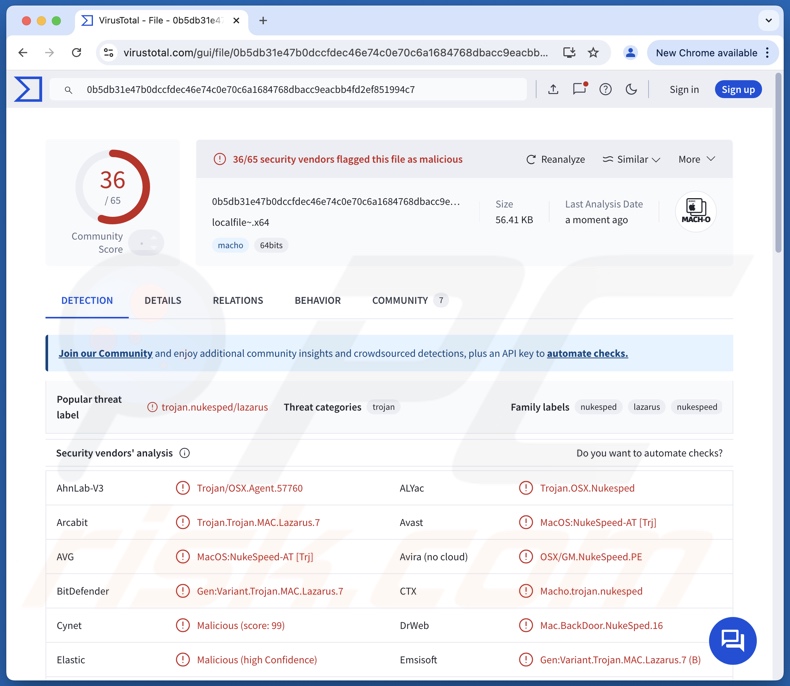
PondRAT malware overview
PondRAT is a RAT (Remote Access Trojan). Malware of this kind is designed to establish remote access and control over compromised machines. RATs tend to be versatile, yet PondRAT's functionalities are more streamlined.
This malicious program has anti-detection capabilities. It can execute commands on infiltrated devices, most importantly – downloading and uploading files. The former means that PondRAT can steal victims' system and personal files. The scope of the threat posed by this depends on the sensitivity of the information within the exfiltrated files.
As PondRAT can upload files onto systems, it could be used to cause chain infections. In other words, this RAT might introduce additional malware or malicious components into victims' machines. Common malware types include trojans, ransomware, and cryptocurrency miners.
While theoretically programs like PondRAT can cause just about any type of infection; in practice – they tend to operate within certain specifications and limitations.
It is pertinent to mention that malware developers often improve upon their software and methodologies. Therefore, potential future iterations of PondRAT could have additional/different capabilities and features.
To summarize, the presence of software like PondRAT on devices can result in multiple system infections, severe privacy issues, financial losses, and identity theft.
| Name | PondRAT virus |
| Threat Type | Mac malware, Mac virus, Remote Access Trojan, Remote Administration Tool, RAT |
| Detection Names | Avast (MacOS:NukeSpeed-AT [Trj]), Combo Cleaner (Gen:Variant.Trojan.MAC.Lazarus.7), ESET-NOD32 (A Variant Of OSX/NukeSped.K), Kaspersky (HEUR:Backdoor.OSX.Nukesped.j), Full List Of Detections (VirusTotal) |
| Symptoms | Trojans are designed to stealthily infiltrate the victim's computer and remain silent, and thus no particular symptoms are clearly visible on an infected machine. |
| Distribution Methods | Trojanized software, infected email attachments, malicious online advertisements, social engineering, program 'cracks'. |
| Damage | Stolen passwords and banking information, identity theft, the victim's computer added to a botnet. |
| Malware Removal (Windows) |
To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. Download Combo CleanerTo use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com. |
Mac-targeting remote access trojan examples
We have investigated countless malware samples; HZ RAT, Bella, XAgentOSX, and NetWeirdRC are merely a few of our articles on Mac-specific RATs.
As previously mentioned, these trojans tend to be incredibly multi-functional. However, regardless of how a piece of malicious software operates – its presence endangers device integrity and user safety. Hence, all threats must be eliminated immediately upon detection.
How did PondRAT infiltrate my computer?
PondRAT has been observed being spread via infected Python packages. They were uploaded to the Python Package Index (PyPI) – official third-party repository for Python software. At the time of research, the known PondRAT-laced packages had been removed from PyPI.
It is noteworthy that this RAT could be distributed by relying on other techniques. Malware is primarily proliferated using phishing and social engineering tactics. It is typically disguised as or bundled with regular content.
The most widespread malware distribution methods include: backdoor/loader-type trojans, drive-by (stealthy/deceptive) downloads, malicious attachments/links in spam mail (e.g., emails, DMs/PMs, SMSes, etc.), malvertising, online scams, dubious download sources (e.g., freeware and free file-hosting websites, P2P sharing networks, etc.), illegal software activation tools ("cracks"), pirated content, and fake updates.
Furthermore, some malicious programs can self-spread via local networks and removable storage devices (e.g., external hard drives, USB flash drives, etc.).
How to avoid installation of malware?
It is essential to be vigilant when browsing since the Internet is rife with deceptive and malicious content. All downloads must be made from official and verified sources. We recommend activating and updating programs using legitimate functions/tools, as those acquired from third-parties can contain malware.
Another recommendation is to exercise caution with incoming emails, PMs/DMs, SMSes, and other messages. We advise against opening attachments or links present in suspicious/irrelevant mail, as they can be harmful or infectious.
It is paramount for device/user safety to have a reputable anti-virus installed and kept updated. Security software must be used to perform regular system scans and to remove detected threats and issues. If you believe that your computer is already infected, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Quick menu:
Potentially unwanted applications removal:
Remove potentially unwanted applications from your "Applications" folder:
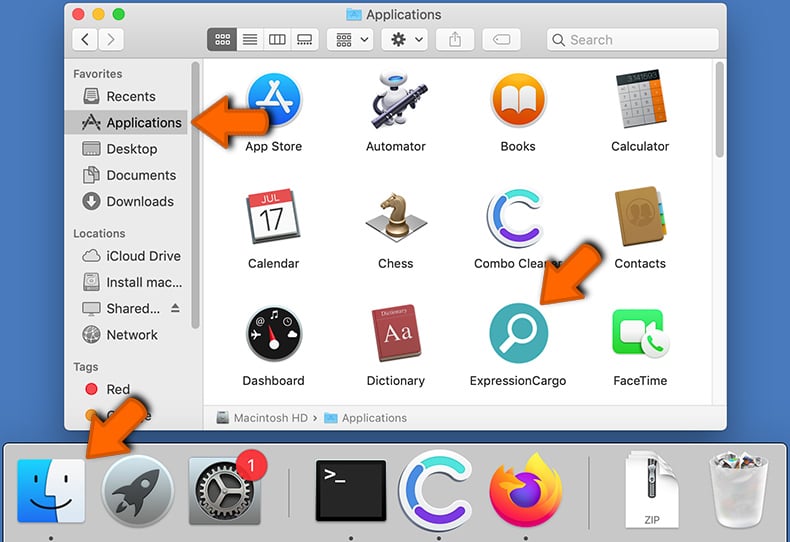
Click the Finder icon. In the Finder window, select "Applications". In the applications folder, look for "MPlayerX","NicePlayer", or other suspicious applications and drag them to the Trash. After removing the potentially unwanted application(s) that cause online ads, scan your Mac for any remaining unwanted components.
DOWNLOAD remover for malware infections
Combo Cleaner checks if your computer is infected with malware. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by RCS LT, the parent company of PCRisk.com.
Remove adware-related files and folders
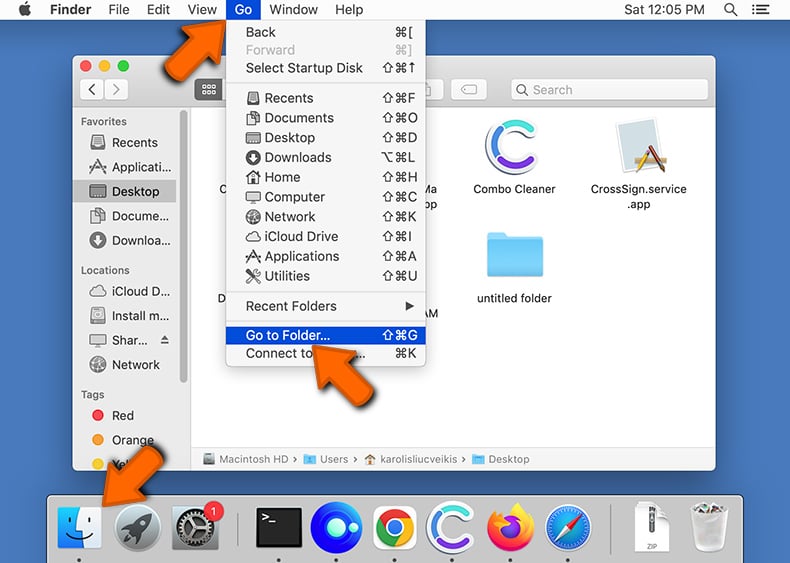
Click the Finder icon, from the menu bar. Choose Go, and click Go to Folder...
 Check for adware generated files in the /Library/LaunchAgents/ folder:
Check for adware generated files in the /Library/LaunchAgents/ folder:
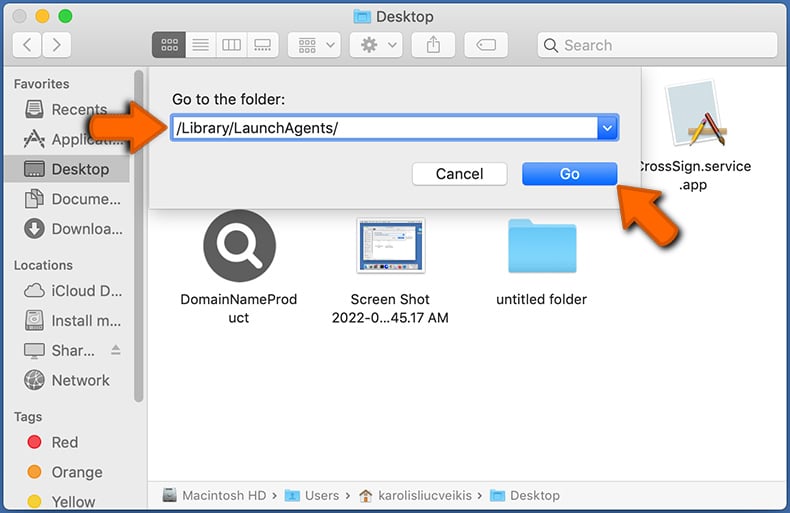
In the Go to Folder... bar, type: /Library/LaunchAgents/
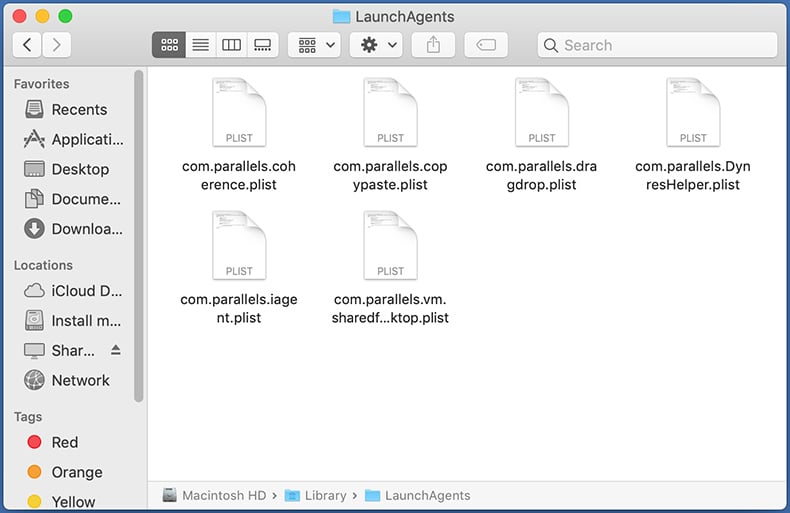
In the "LaunchAgents" folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - "installmac.AppRemoval.plist", "myppes.download.plist", "mykotlerino.ltvbit.plist", "kuklorest.update.plist", etc. Adware commonly installs several files with the exact same string.
 Check for adware generated files in the ~/Library/Application Support/ folder:
Check for adware generated files in the ~/Library/Application Support/ folder:
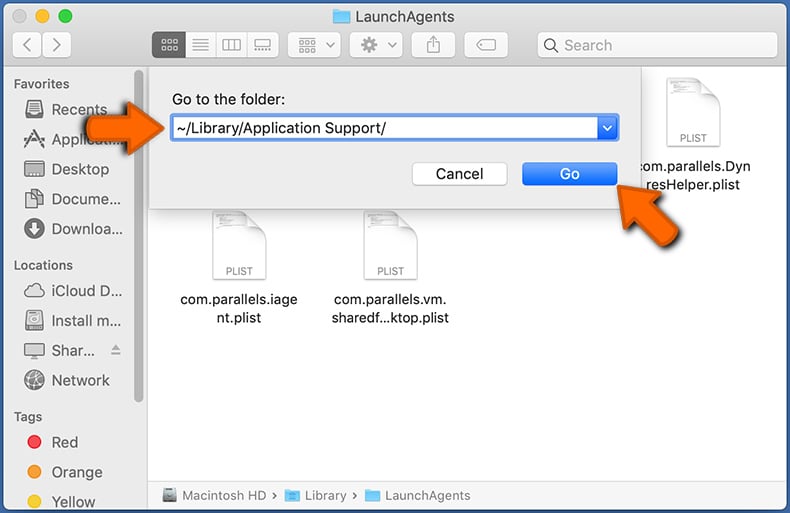
In the Go to Folder... bar, type: ~/Library/Application Support/
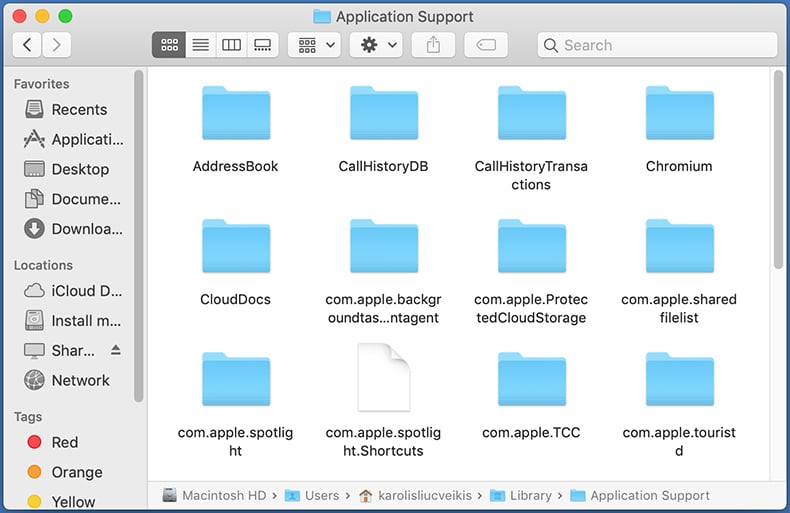
In the "Application Support" folder, look for any recently-added suspicious folders. For example, "MplayerX" or "NicePlayer", and move these folders to the Trash.
 Check for adware generated files in the ~/Library/LaunchAgents/ folder:
Check for adware generated files in the ~/Library/LaunchAgents/ folder:
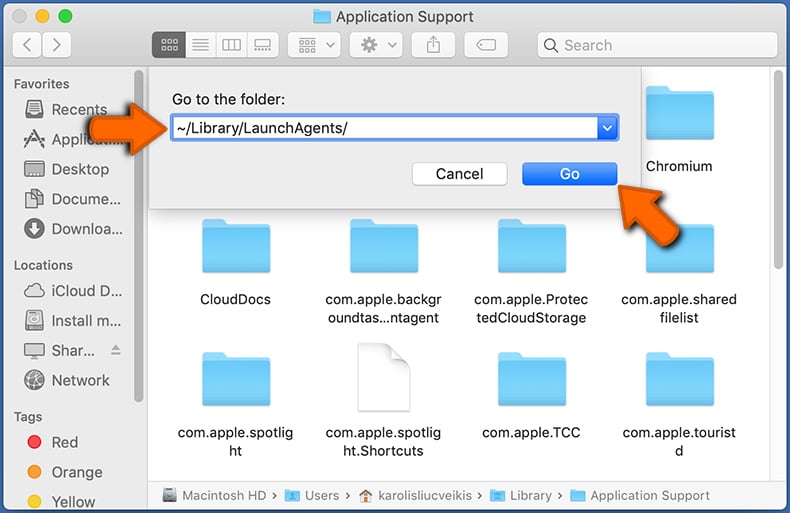
In the Go to Folder... bar, type: ~/Library/LaunchAgents/
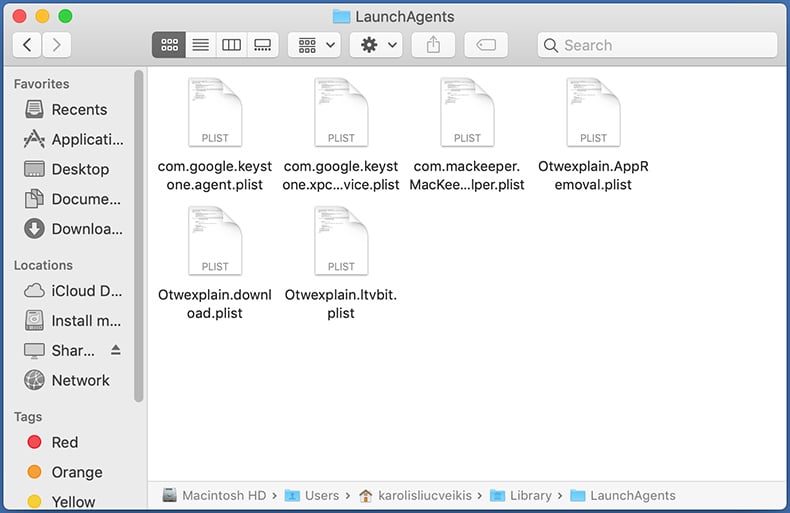
In the "LaunchAgents" folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - "installmac.AppRemoval.plist", "myppes.download.plist", "mykotlerino.ltvbit.plist", "kuklorest.update.plist", etc. Adware commonly installs several files with the exact same string.
 Check for adware generated files in the /Library/LaunchDaemons/ folder:
Check for adware generated files in the /Library/LaunchDaemons/ folder:
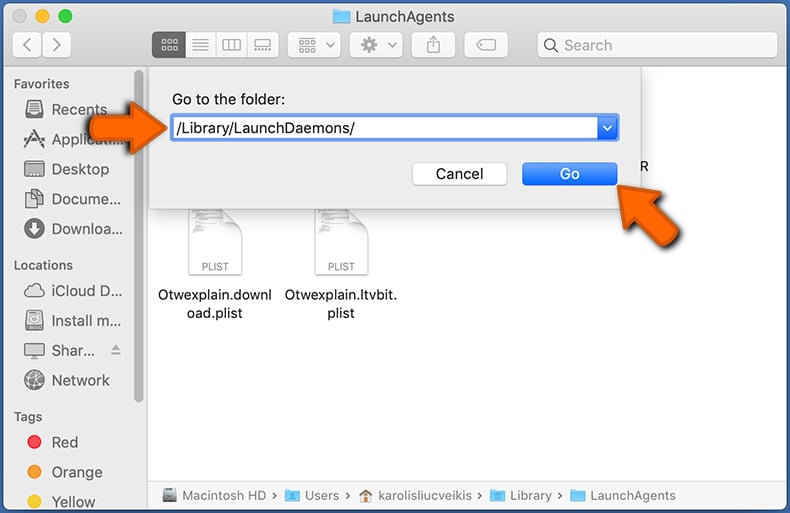
In the "Go to Folder..." bar, type: /Library/LaunchDaemons/
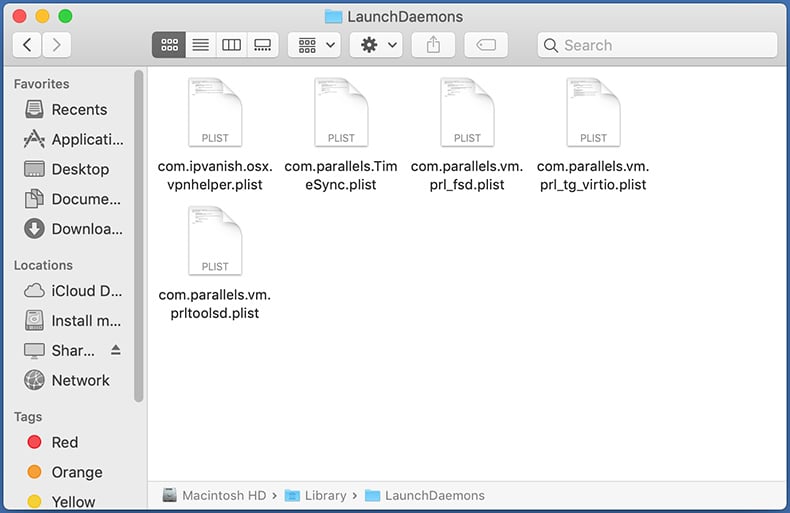
In the "LaunchDaemons" folder, look for recently-added suspicious files. For example "com.aoudad.net-preferences.plist", "com.myppes.net-preferences.plist", "com.kuklorest.net-preferences.plist", "com.avickUpd.plist", etc., and move them to the Trash.
 Scan your Mac with Combo Cleaner:
Scan your Mac with Combo Cleaner:
If you have followed all the steps correctly, your Mac should be clean of infections. To ensure your system is not infected, run a scan with Combo Cleaner Antivirus. Download it HERE. After downloading the file, double click combocleaner.dmg installer. In the opened window, drag and drop the Combo Cleaner icon on top of the Applications icon. Now open your launchpad and click on the Combo Cleaner icon. Wait until Combo Cleaner updates its virus definition database and click the "Start Combo Scan" button.
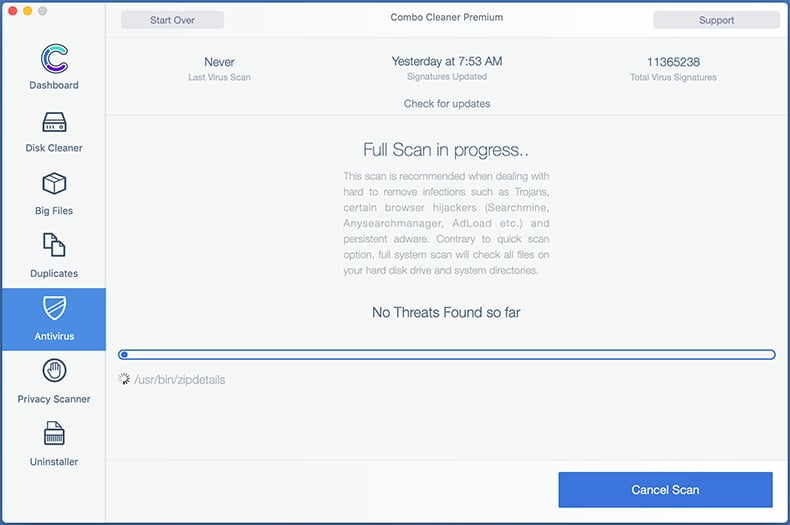
Combo Cleaner will scan your Mac for malware infections. If the antivirus scan displays "no threats found" - this means that you can continue with the removal guide; otherwise, it's recommended to remove any found infections before continuing.
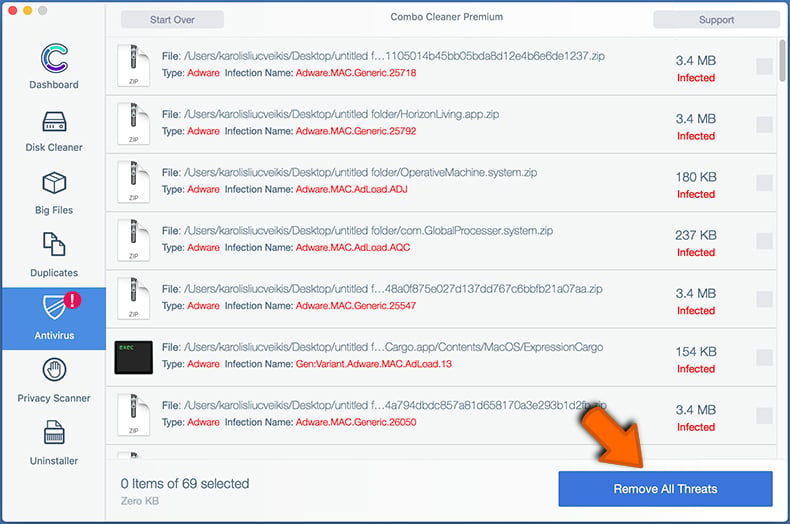
After removing files and folders generated by the adware, continue to remove rogue extensions from your Internet browsers.
Remove malicious extensions from Internet browsers
 Remove malicious Safari extensions:
Remove malicious Safari extensions:
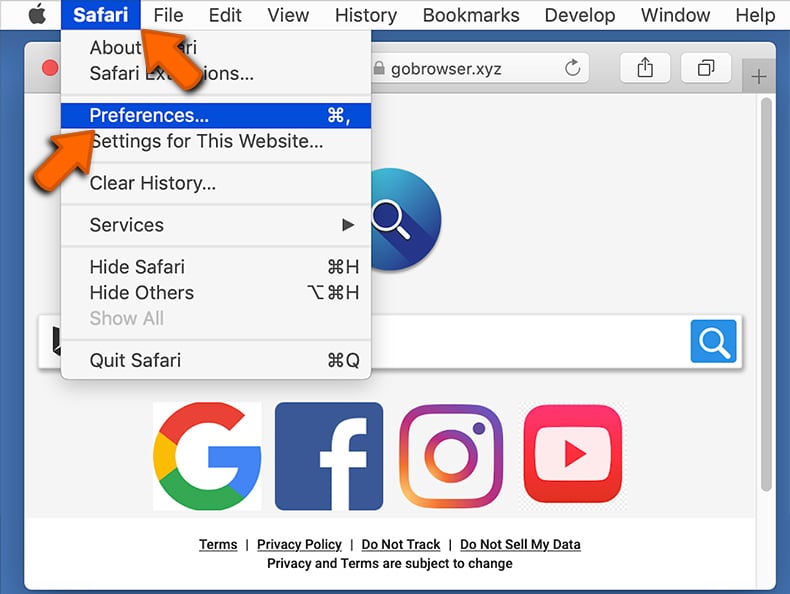
Open the Safari browser, from the menu bar, select "Safari" and click "Preferences...".
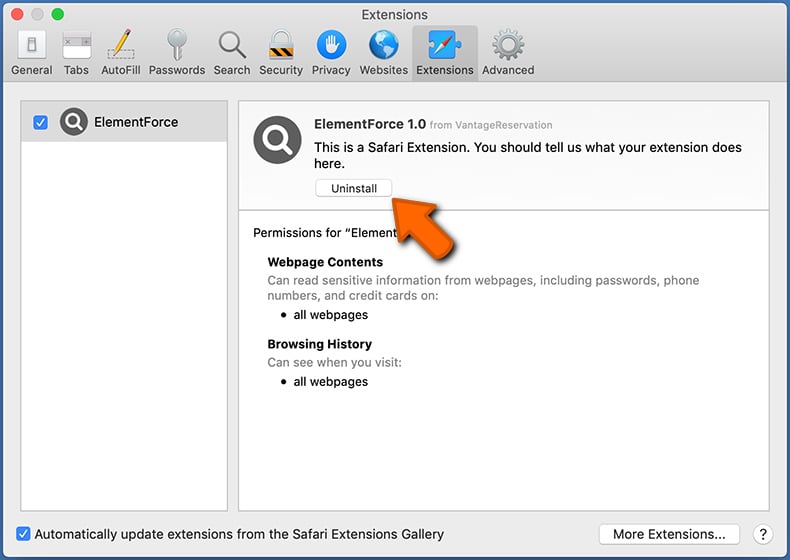
In the preferences window, select "Extensions" and look for any recently-installed suspicious extensions. When located, click the "Uninstall" button next to it/them. Note that you can safely uninstall all extensions from your Safari browser - none are crucial for regular browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Safari.
 Remove malicious extensions from Google Chrome:
Remove malicious extensions from Google Chrome:
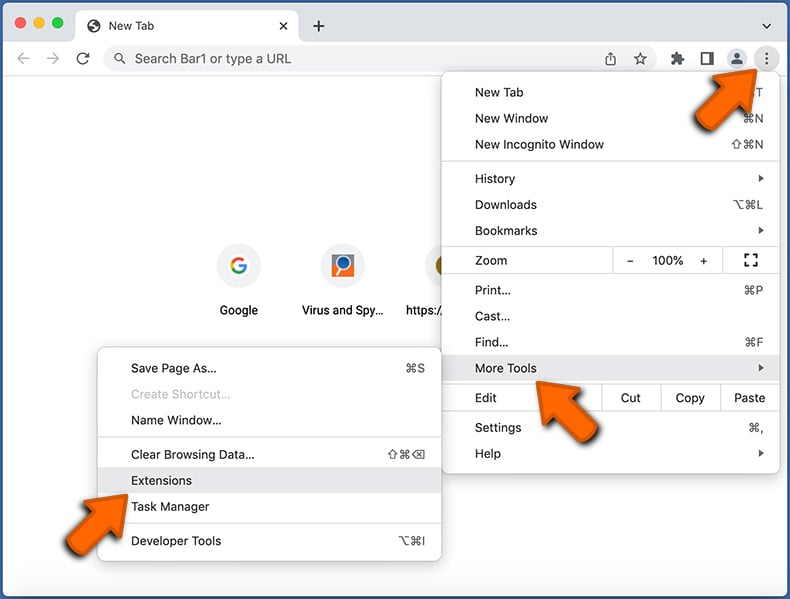
Click the Chrome menu icon ![]() (at the top right corner of Google Chrome), select "More Tools" and click "Extensions". Locate all recently-installed suspicious extensions, select these entries and click "Remove".
(at the top right corner of Google Chrome), select "More Tools" and click "Extensions". Locate all recently-installed suspicious extensions, select these entries and click "Remove".
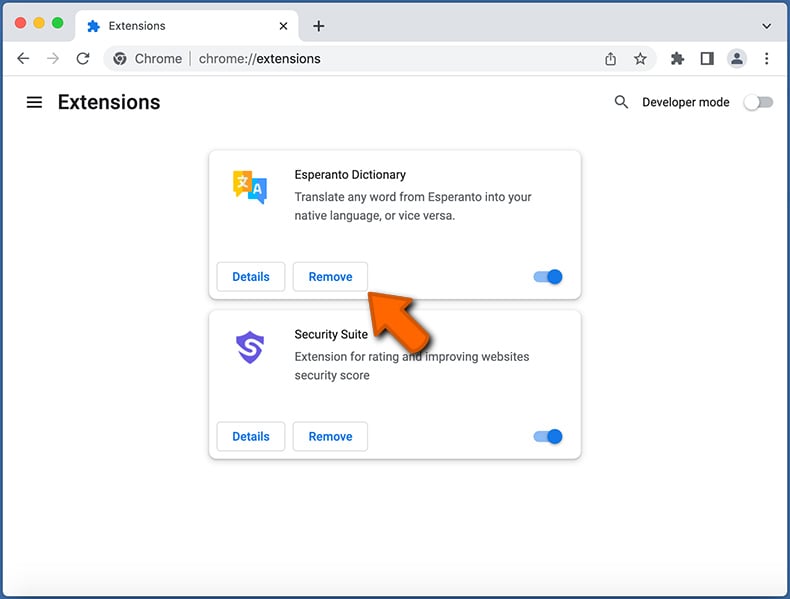
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Google Chrome.
 Remove malicious extensions from Mozilla Firefox:
Remove malicious extensions from Mozilla Firefox:
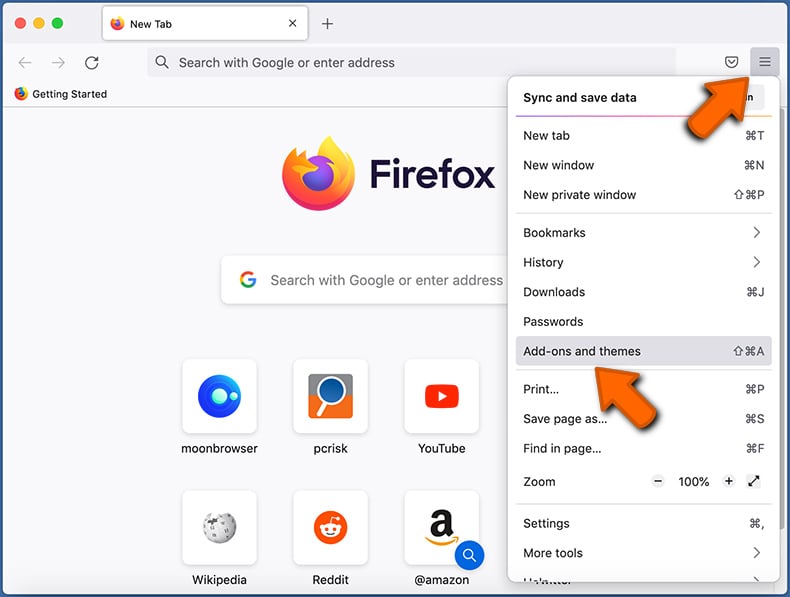
Click the Firefox menu ![]() (at the top right corner of the main window) and select "Add-ons and themes". Click "Extensions", in the opened window locate all recently-installed suspicious extensions, click on the three dots and then click "Remove".
(at the top right corner of the main window) and select "Add-ons and themes". Click "Extensions", in the opened window locate all recently-installed suspicious extensions, click on the three dots and then click "Remove".
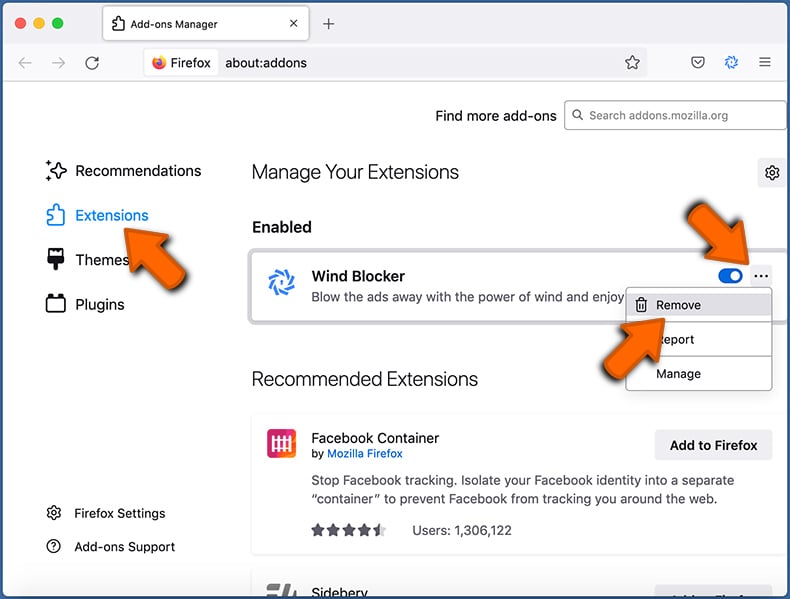
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Mozilla Firefox.
Frequently Asked Questions (FAQ)
My computer is infected with PondRAT malware, should I format my storage device to get rid of it?
Malware removal rarely necessitates formatting.
What are the biggest issues that PondRAT malware can cause?
The threats posed by an infection depend on the program's capabilities and the cyber criminals' modus operandi. PondRAT is a RAT that allows remote control over devices. It can steal files and upload them onto victims' machines; the latter means that it could be used to cause chain infections. Hence, the presence of this trojan may lead to multiple system infections, severe privacy issues, financial losses, and identity theft.
What is the purpose of PondRAT malware?
Most malware infections are motivated by profit. It is speculated that PondRAT is linked to Gleaming Pisces – a financially-motivated threat actor affiliated with North Korea. The affiliation suggests geopolitical motivations, which are not uncommon in malware attacks. Other reasons for infections include cyber criminals seeking amusement or to realize personal vendettas, process disruption (e.g., sites, services, companies, etc.), and hacktivism.
How did PondRAT malware infiltrate my computer?
PondRAT has been noted being spread through infected Python packages uploaded to PyPI. Other distribution methods are not unlikely. Generally, malware is primarily proliferated via trojans, drive-by downloads, spam mail, malvertising, online scams, suspect download channels (e.g., freeware and third-party sites, P2P sharing networks, etc.), illegal software activation tools ("cracks"), and fake updates. Some malicious programs can even self-proliferate through local networks and removable storage devices.
Will Combo Cleaner protect me from malware?
Yes, Combo Cleaner is designed to scan devices and remove all manner of threats. It is capable of detecting and eliminating most of the known malware infections. Remember that sophisticated malicious programs tend to hide deep within systems – therefore, running a complete system scan is crucial.
Share:

Tomas Meskauskas
Expert security researcher, professional malware analyst
I am passionate about computer security and technology. I have an experience of over 10 years working in various companies related to computer technical issue solving and Internet security. I have been working as an author and editor for pcrisk.com since 2010. Follow me on Twitter and LinkedIn to stay informed about the latest online security threats.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion