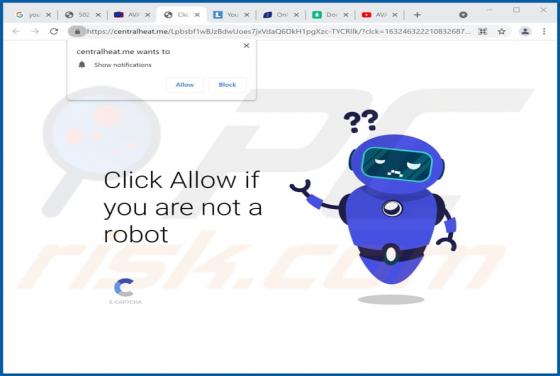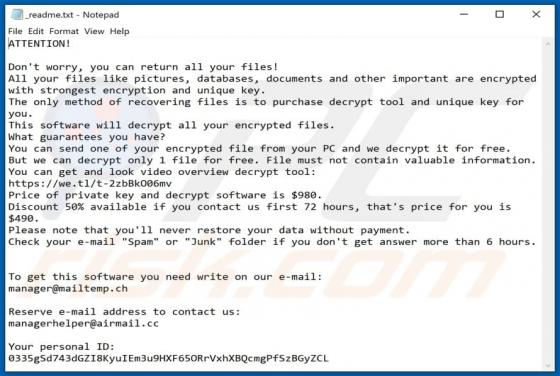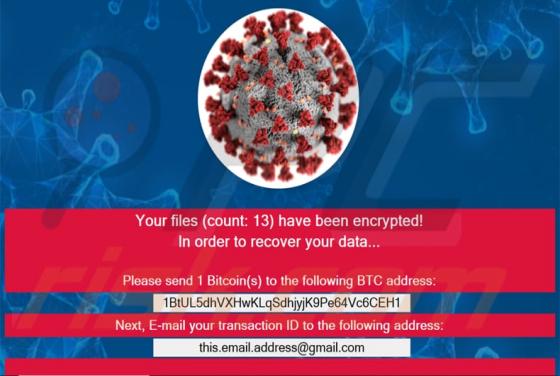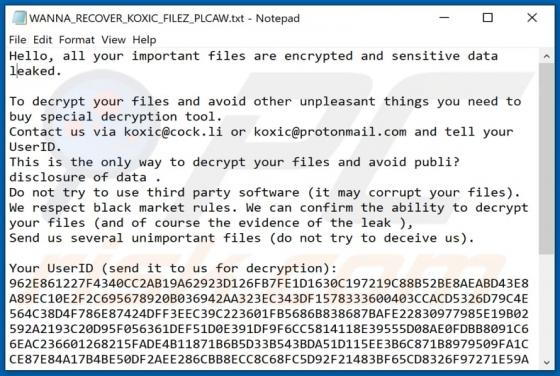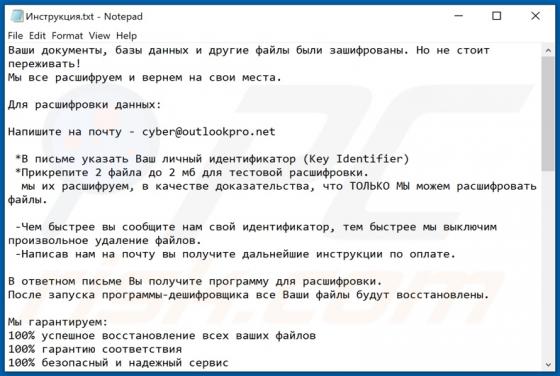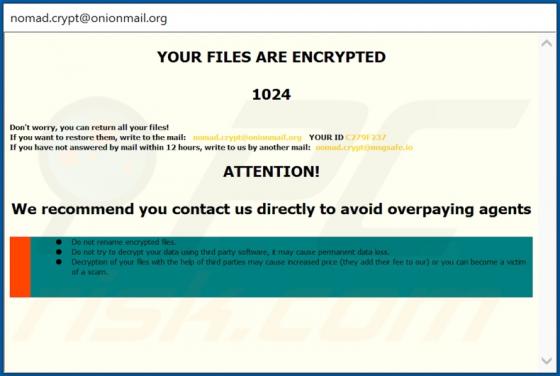
Nomad Ransomware
Nomad is a malicious program that belongs to the Dharma ransomware family. It is designed to encrypt data (render files inaccessible) and demand ransoms for the decryption. Affected files are renamed following this pattern: initial filename, unique ID assigned to the victim, cyber criminals' emai