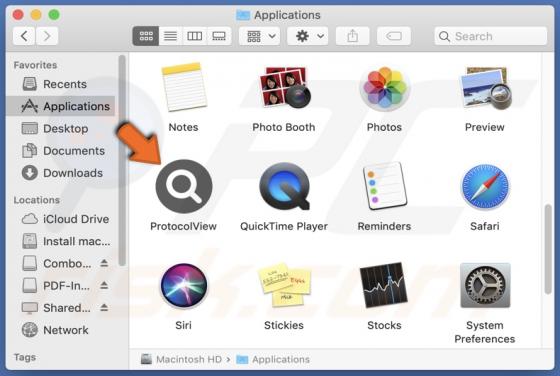
ProtocolView Adware (Mac)
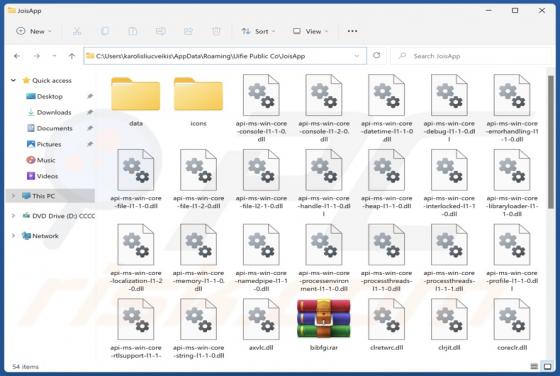
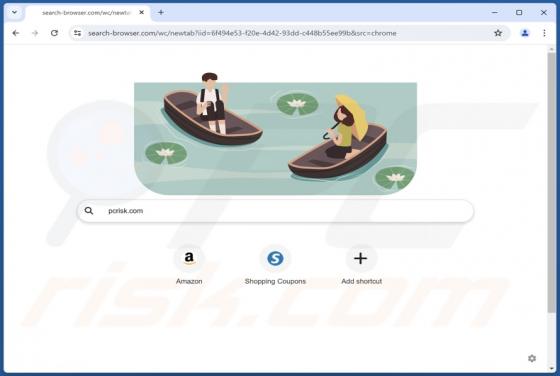
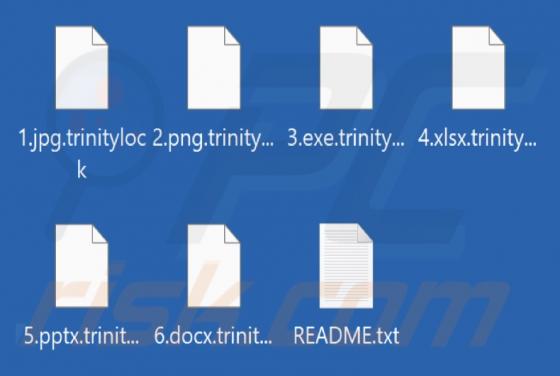
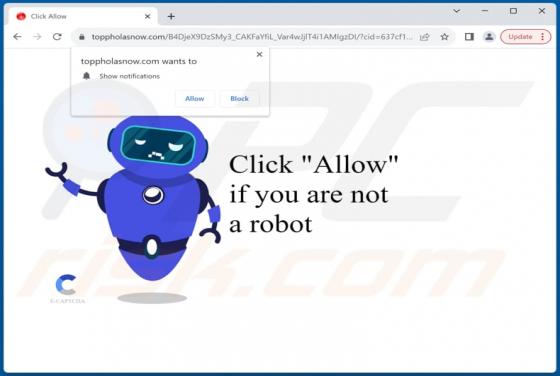
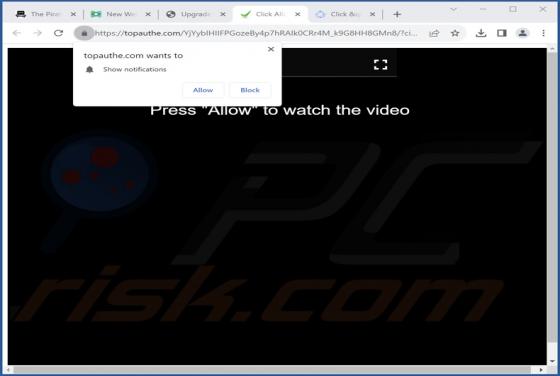
Our research team found ProtocolView while reviewing file submissions to the VirusTotal platform. Upon inspection, we determined that this app is advertising-supported software (adware). ProtocolView is part of the AdLoad malware group. Adware is designed to generate revenue for its deve