Cuckoo Malware (Mac)
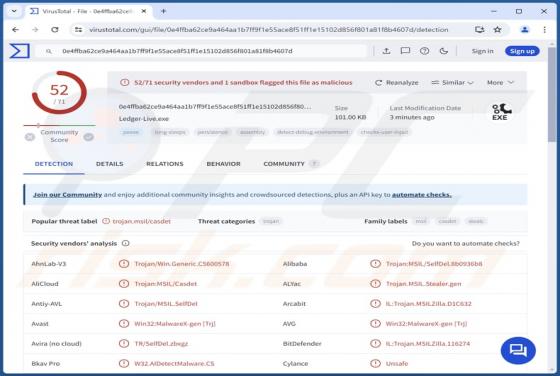
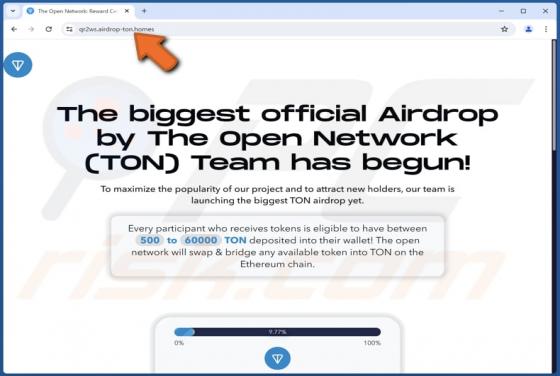
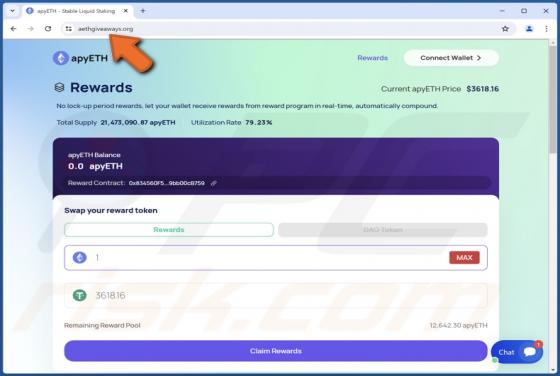
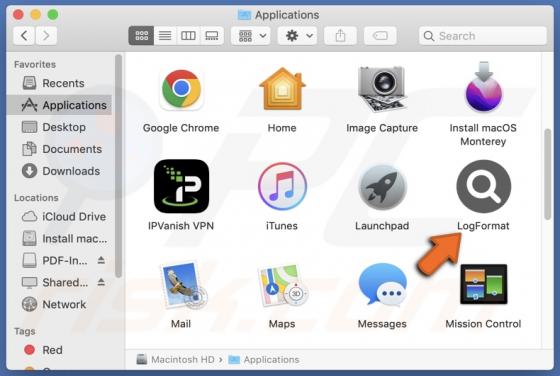
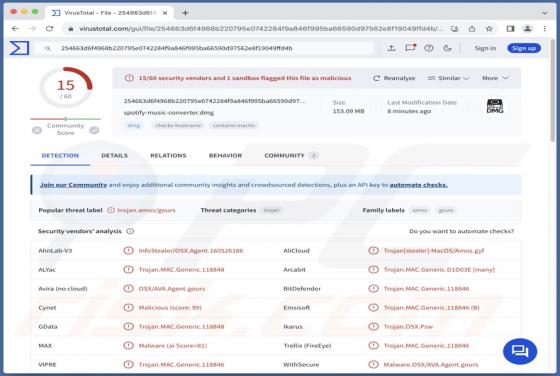
Cuckoo is a Mac-specific malware that operates as spyware and an information-stealer. It can record information and extract data from various browsers, cryptocurrency wallets, FTP clients, messengers, and other apps. The Cuckoo malicious program has been around since at least the spring of 2024